Create an Audit-Ready ISMS with ISO 27001 Policy Templates
For many organizations developing policies from scratch can be a time-consuming task. This is where ISO 27001 Templates and ISO 27001 Policy Templates can help you alot.
Time-Saving
Drafting policies from scratch is resource-intensive. Templates provide a pre-defined structure that can be quickly customized, reducing the workload and enabling faster implementation.
- Pre-written Structure
- Quick Customization
- Faster Implementation
- Reduced Workload
- Efficiency in Compliance
Consistency
Pre-written templates ensure that all policies follow a consistent format and cover the required elements, helping you maintain a unified approach to security management across your organization
- Uniform Format
- Comprehensive Coverage
- Consistency Across Teams
- Unified Security Approach
- Easier Audits and Reviews
Discover our ISO 27001 Policy Templates
Our ISO 27001:2022 Policy Templates offer a quick, efficient way to meet the certification requirements without compromising on quality.
ISO 27001 Core Documents Bundle
ISO 27001 Toolkit
The ISO 27001 Core Documents Bundle contains all the essential Tools, Policies, Procedures, and Records needed to establish and maintain compliance with the standard. These ISO 27001 templates help you meet the mandatory requirements and streamline the process of managing your ISMS by providing clear, customizable structures for key documents.
ISMS Scope Document Template
ISO 27001 Clause 4.3
This ISMS Scope Document Template defines the boundaries and scope of the ISMS in alignment with Clause 4.3, ensuring that all relevant aspects of the organization are clearly identified by specifying which departments, systems, and processes fall under the ISO 27001 ISMS framework.
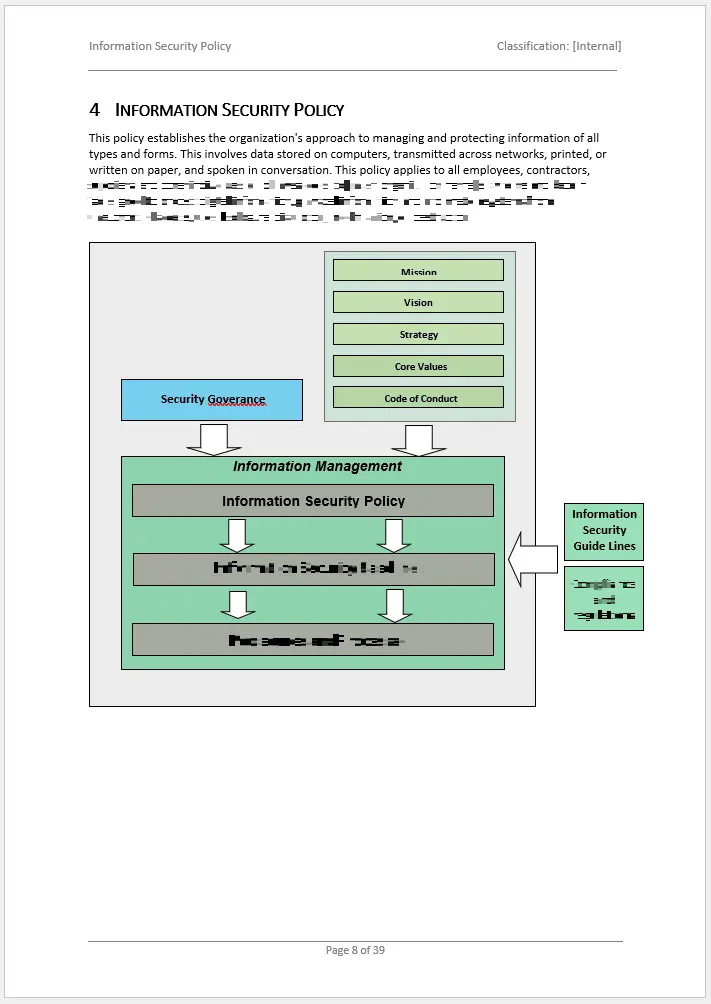
Information Security Policy
ISO 27001 Clause 5.2
A high-level policy outlining the organization’s commitment to maintaining information security, this Information Security Policy Template aligns with Clause 5.2 and establishes clear security objectives, responsibilities, and principles to be followed by all employees. It serves as the cornerstone of the organization’s ISMS, providing a framework.
Risk Management Policy Template
ISO 27001 Clauses 6.1
The Risk Management Policy Template outlines the methodology for managing risks within the organization, aligning with Clause 6.1, which focuses on actions to address risks and opportunities. It provides a structured approach to identifying threats and vulnerabilities, evaluating their potential impact, and selecting appropriate risk mitigation strategies.
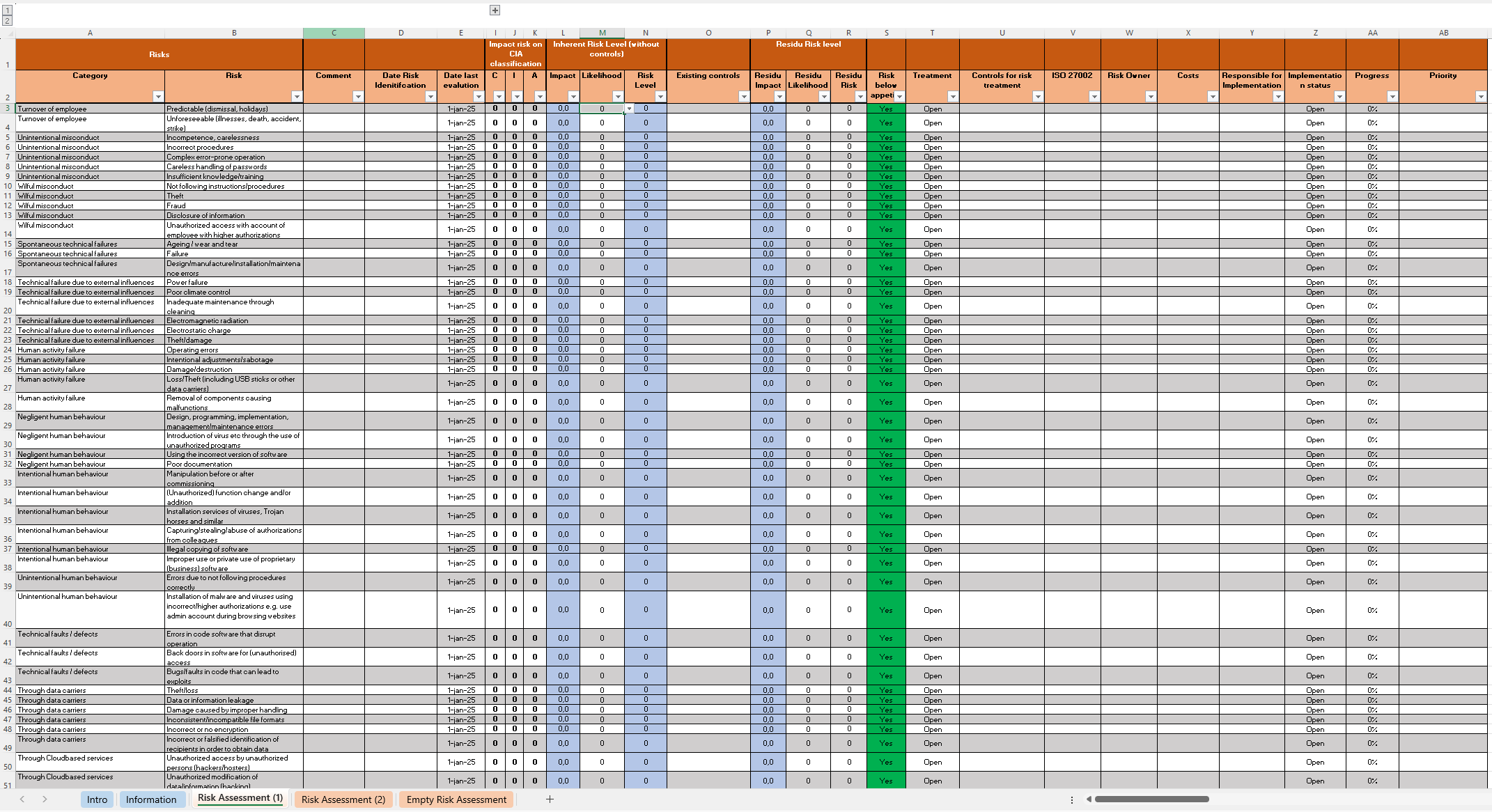
Risk Assessment Template
ISO 27001 Clauses 8.2, and 8.3
The ISO 27001 Risk Assessment Template is a tool used to document and evaluate risks, aligning with Clause 8.2 and Clause 8.3. It helps in systematically identifying specific threats and vulnerabilities related to the organization’s operations. This Excel template allows you to calculate the potential impact, and rank them based on severity and likelihood.
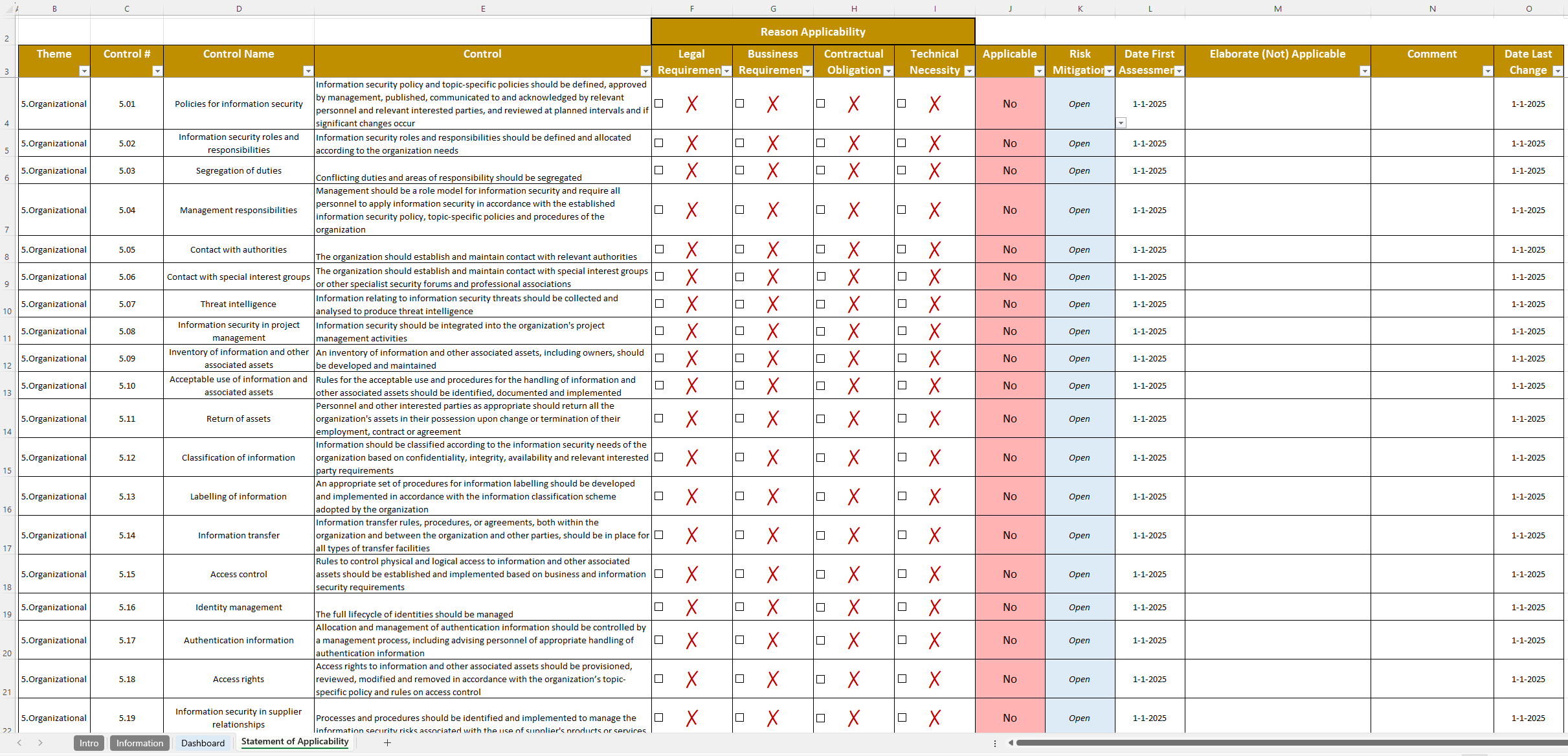
Statement of Applicability Template
ISO 27001 Clause 6.1.3
A comprehensive ISO 27001:2022 SoA Template that lists all Annex A controls, aligning with Clause 6.1.3, which focuses on information security risk treatment, including the requirement to produce a Statement of Applicability. This template indicates whether the controls are applicable to the organization and how they are being implemented.
Asset Management Policy Template
ISO 27001 Annex A Control 5.9
The Asset Management Policy Template outlines how information assets are identified, classified, and managed throughout their lifecycle, aligning with Control 5.9 of ISO 27001 to ensure the protection of sensitive data and equipment.
Asset Register Template
ISO 27001 Annex A Control 5.9
An organized inventory sheet that tracks all information assets, ensuring they are properly recorded, classified, and managed.
Acceptable use Policy Template
ISO 27001 Annex A Control 5.10
This policy defines how employees are permitted to use the organization’s assets, including IT equipment and data, ensuring proper security practices are followed.
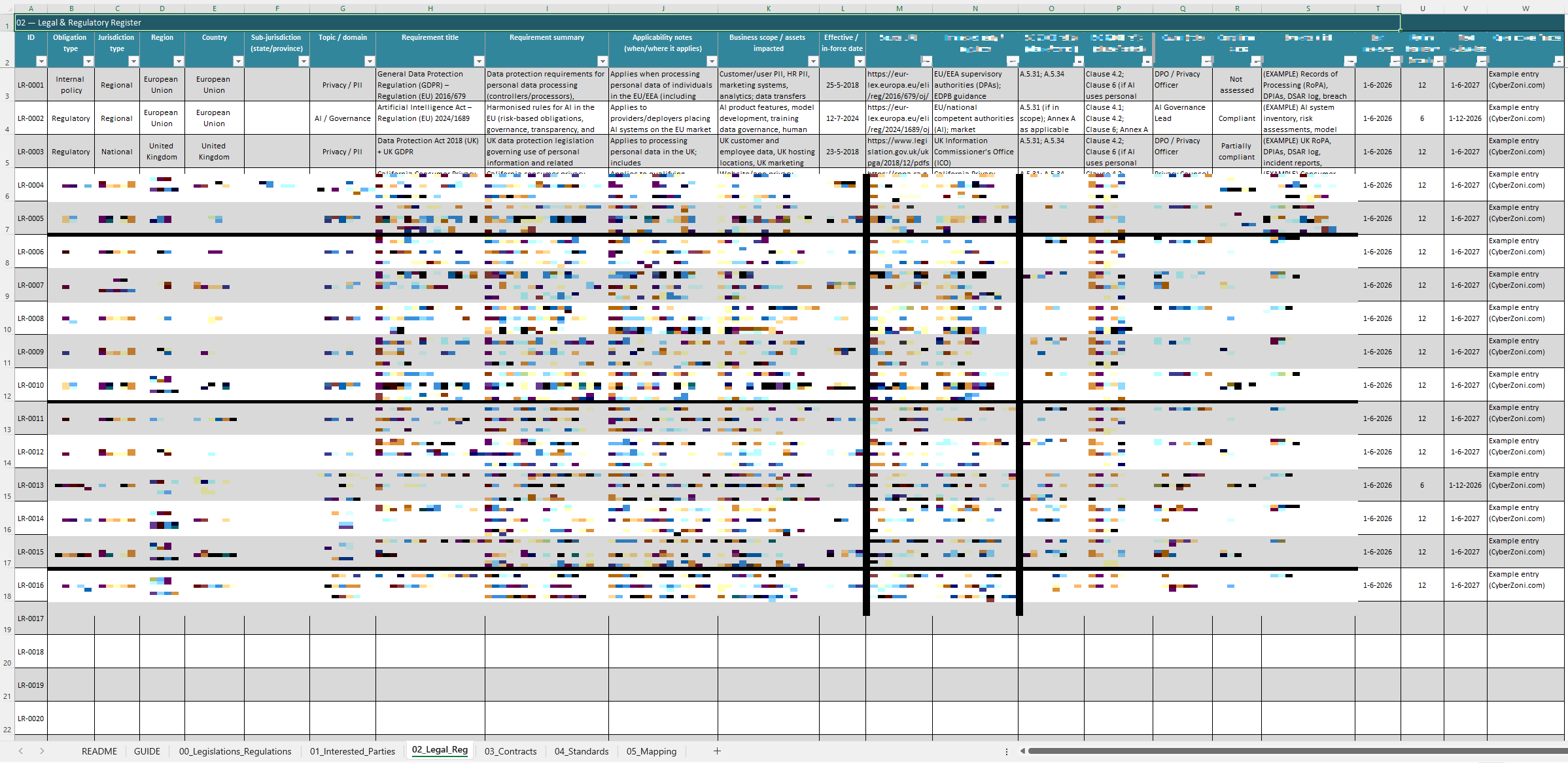
Legal Register Template
ISO 27001 Annex A 5.31
A register to keep track of all applicable legal and regulatory requirements, ensuring that the organization remains compliant with laws and regulations concerning information security.
Security Operating Procedures
ISO 27001 Annex A 5.37
Provides detailed procedures for managing IT operations securely, including configurations, access controls, and regular system monitoring.
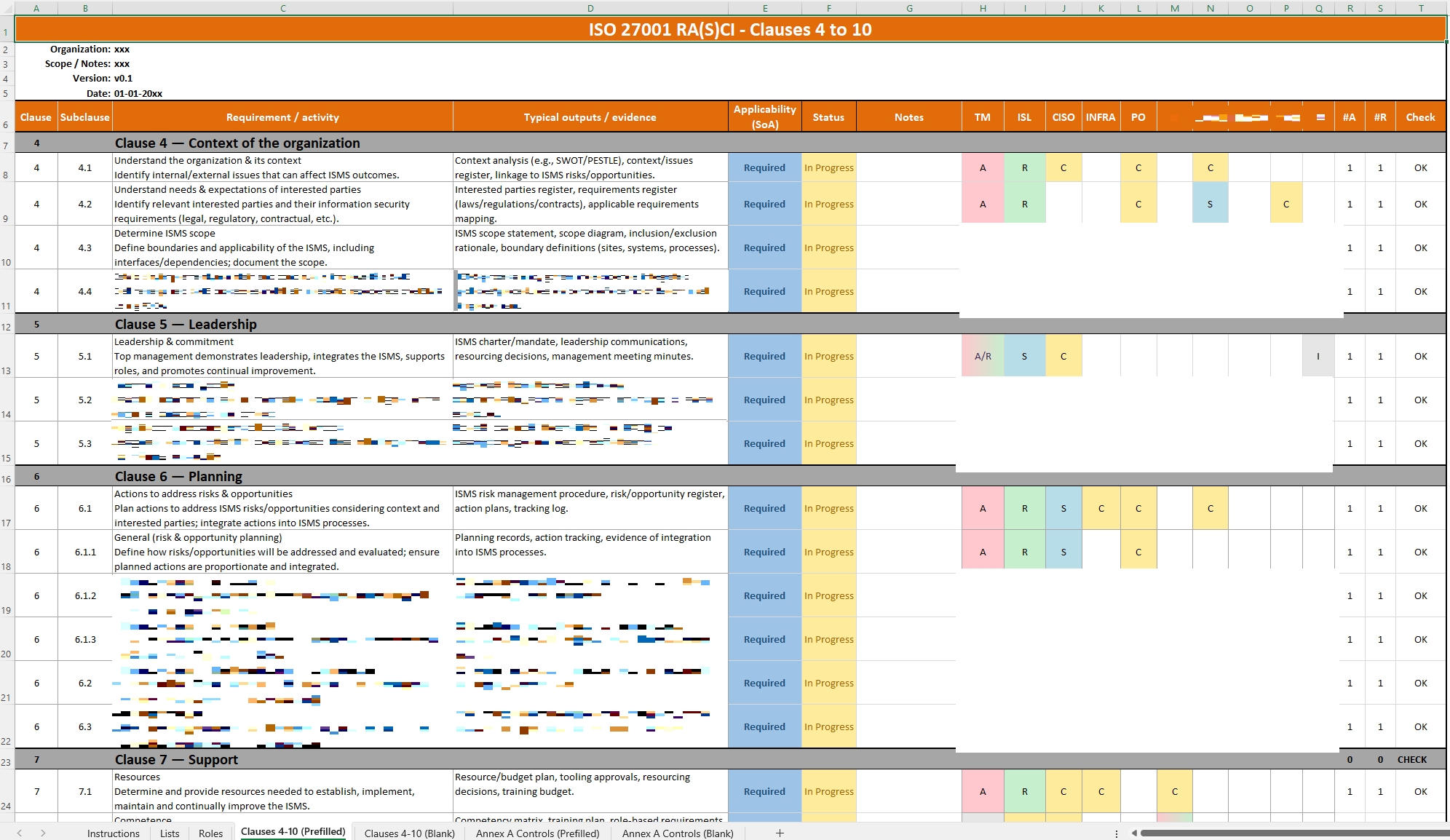
Raci Matrix Template
ISO 27001 Annex A 6.2, A 6.6
A RACI matrix is a tool that assigns responsibilities for security activities by specifying who is Responsible, Accountable, Consulted, and Informed.
Configuration Management Policy
ISO 27001 Annex A 8.9
Clearly outlines the roles and responsibilities for information security across the organization, ensuring accountability for specific tasks and controls.
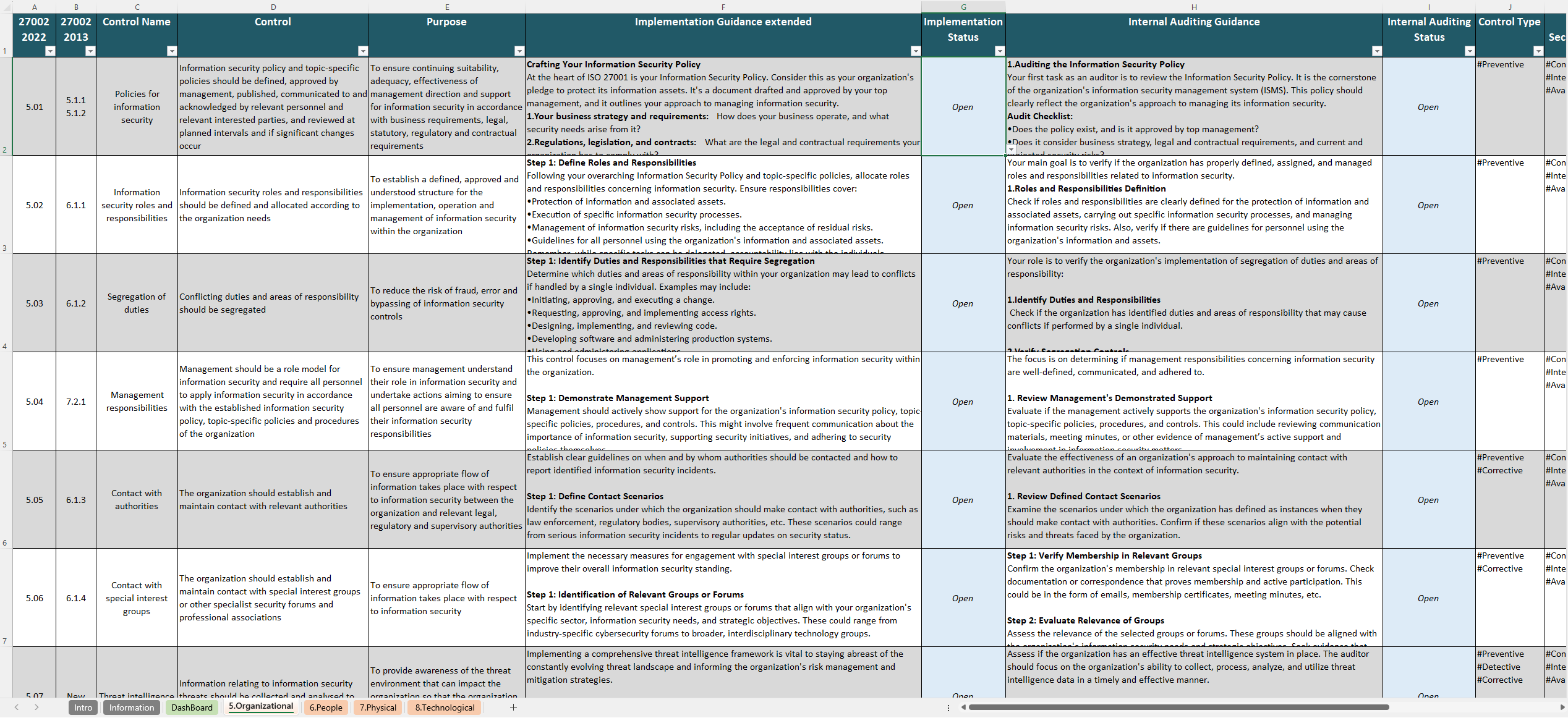
ISO 27002 2022 Controls Spreadsheet
ISO 27001 Annex A Controls
Our ISO 27002 2022 Controls Spreadsheet is a complete solution for Implementing and Managing ISO 27002 controls. The excel-based control list is broken down into the four theme tabs to make navigation and implementation straightforward.
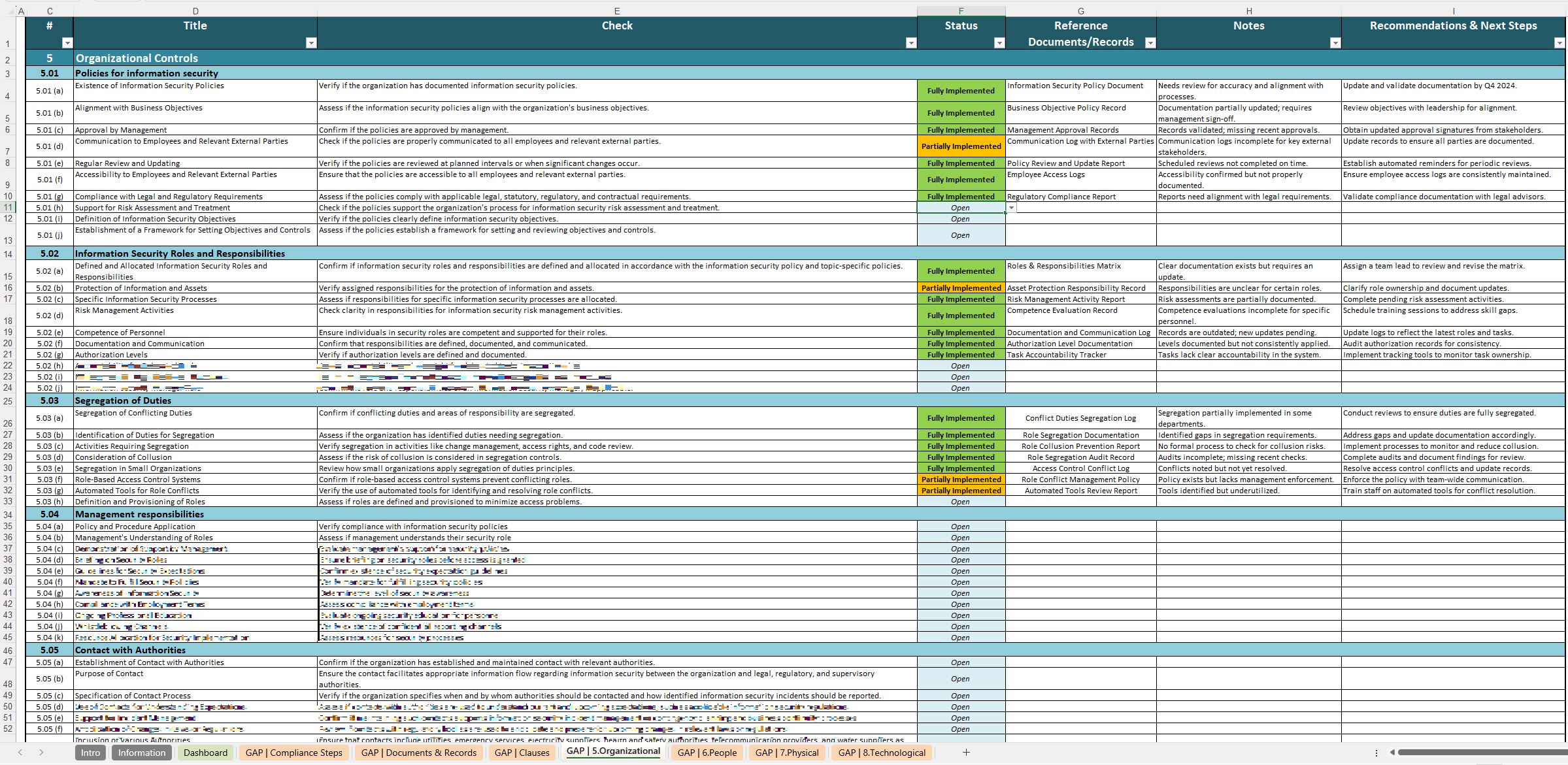
ISO 27001 Gap Analysis Template
All Clauses - Controls - Documents & Records
The ISO 27001 Gap Analysis Template will help you assess whether your current policies meet the requirements of the standard, pinpointing missing or incomplete areas.
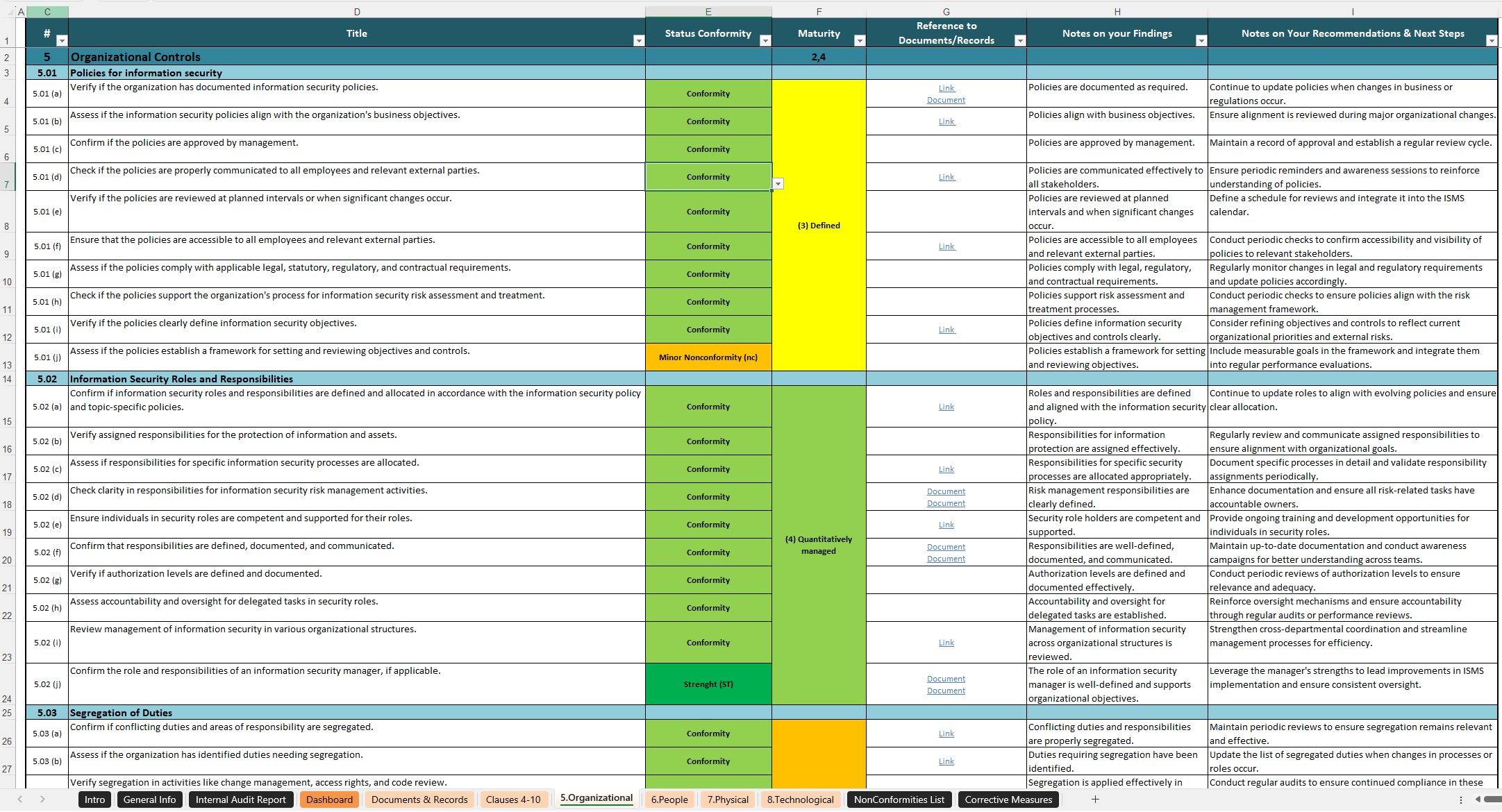
ISO 27001 Internal Audit Template
ISO 27001 Annex A Controls
Internal audits is a mandatory component, detailed in Clause 9.2 which is subdivided into Clause 9.2.1 & Clause 9.2.2 and in Control 5.35, of acquiring and maintaining ISO 27001 certification. These audits provide an objective evaluation of your ISMS, helping you identify non-conformities, areas for improvement, and the effectiveness of your security controls. Conducting regular internal audits ensures that your ISMS stays aligned with ISO 27001 requirements and also prepares you for external certification audits.
An effective internal audit process:
- Evaluates the effectiveness of your information security policies and procedures.
- Identifies gaps and non-conformities in your ISMS.
- Helps implement corrective actions to continuously improve your security posture.
- Ensures your organization is prepared for external audits and reduces the risk of non-compliance.
FAQ
What is ISO 27001 certification?
ISO 27001 is an international standard for managing information security. Certification to this standard demonstrates that an organization follows best practices to protect sensitive information by implementing an Information Security Management System (ISMS).
Do these ISO 27001 templates guarantee certification?
No, using templates alone doesn’t guarantee certification. While templates help structure your ISMS, successful certification also requires proper implementation, risk assessments, employee training, and passing an external audit.
How often should the policies be reviewed?
ISO 27001 policies should be reviewed at least annually or whenever there are significant changes in the organization, such as new technology, legal requirements, or incidents. This ensures policies stay relevant and effective.
Who is responsible for implementing ISO 27001 policies?
Typically, responsibility falls on senior management, information security officers, and control owners. However, all employees should be aware of and follow the policies relevant to their role.
What are the key components of ISO 27001 policies?
The key elements include a commitment to meeting information security requirements, continual improvement of the ISMS, and clear communication within the organization. Each policy should align with your organization’s specific objectives and risks.
Do the templates cover all ISO 27001 requirements?
Yes, ISO 27001 policy templates are typically designed to cover essential areas such as risk management, access control, incident response, and data protection. You can customize them based on your organization’s specific needs.
How long does it take to implement ISO 27001 policies?
This varies depending on your organization’s size and complexity. On average, it can take several months to properly implement, train employees, and prepare for certification.
Do we need external help to implement ISO 27001?
While it’s possible to implement ISO 27001 internally, many organizations benefit from external expertise to accelerate the process and ensure compliance, especially during audits.
What are Annex A controls?
Annex A in ISO 27001 lists 93 specific security controls that organizations must consider when implementing their ISMS. These range from access control to cryptography and incident management.
What is the difference between ISO 27001 and ISO 27002?
ISO 27001 is the standard for an ISMS, focusing on management and risk. ISO 27002 provides guidance on implementing the specific controls listed in ISO 27001 Annex A. For more information check out our ISO 27002 vs 27001 article.