What is an ISMS (Information Security Management System)?
In this Article
What is an ISMS?
An Information Security Management System (ISMS) comprises a collection of policies and procedures designed to manage an organization’s sensitive data systematically. The primary objective of an ISMS is to reduce risk and maintain business continuity by proactively minimizing the effects of a security breach.

An ISMS generally focuses on the behavior of employees and processes, in addition to data and technology. It may be tailored to specific types of data, like customer information, or applied broadly in a manner that integrates into the company’s culture.
How does an ISMS work?
An ISMS offers a structured method for overseeing an organization’s information security. This encompasses various overarching policies designed to regulate and control security risk levels throughout the organization.
ISO/IEC 27001 is the global standard for information security and the establishment of an ISMS. It is jointly issued by the International Organization for Standardization and the International Electrotechnical Commission. While the standard does not prescribe specific measures, it recommends practices such as documentation, internal audits, continuous improvement, and both corrective and preventive actions. To achieve ISO 27001 certification, an organization must have an ISMS that identifies its organizational assets and provides the following assessments:
- The risks facing the information assets;
- The measures implemented to safeguard these assets;
- A response plan for potential security breaches;
- The identification of individuals accountable for each phase of the information security process.
The aim of an ISMS is not solely to maximize information security but to achieve the specific level of security that an organization deems necessary. The degree of control required can differ based on industry-specific needs. For instance, in the heavily regulated healthcare sector, organizations may implement systems designed to ensure that sensitive patient information is thoroughly secured.
ISMS Benefits

An ISMS adopts a comprehensive approach to managing information systems within an organization, yielding multiple advantages as outlined below.
- Secures sensitive data: An ISMS safeguards various types of proprietary information assets, whether paper-based, digital, or cloud-based. This includes personal data, intellectual property, financial records, customer information, and data shared with third parties.
- Ensures regulatory compliance: By implementing an ISMS, organizations can fulfill all relevant regulatory and contractual requirements and enhance their understanding of legal issues related to information systems. This is particularly critical in sectors like finance and healthcare, where legal non-compliance can result in substantial fines.
- Supports business continuity: Investing in an ISMS boosts an organization’s defenses against threats, reducing the incidence of security breaches like cyber attacks. This minimizes disruptions and downtime, crucial for maintaining continuous business operations.
- Cuts costs: An ISMS conducts thorough risk assessments, allowing organizations to focus resources on high-risk assets rather than unnecessary defenses. This targeted approach, combined with reduced downtime from fewer security incidents, significantly lowers overall expenditures.
- Strengthens company culture: An ISMS fosters a culture of security and asset management that extends beyond IT security, encouraging all employees to recognize risks associated with information assets and to integrate security best practices into their daily activities.
- Responds to evolving threats: As security threats continually evolve, an ISMS equips organizations to anticipate and adapt to new challenges and the dynamic demands of the security landscape.
ISMS best Practices

The ISO 27001 and ISO 27002 standards provide a framework of best practices for establishing an ISMS. Here is a checklist of best practices to consider when implementing an ISMS:
Understand business needs: Before deploying an ISMS, it is crucial for organizations to thoroughly understand their business operations, tools, and current information security measures. This overview helps in aligning the ISMS with specific business and security requirements. Familiarizing oneself with how the ISO 27001 framework can aid in data protection and identifying the key personnel responsible for managing the ISMS are also important steps.
Establish an information security policy: Setting up an information security policy prior to implementing an ISMS is advantageous. This initial step allows an organization to identify potential vulnerabilities within their current security framework. The policy should offer a comprehensive outline of the existing security measures in place within the organization.
Conduct security awareness training: It is essential for all employees to participate in regular security awareness training. Such training should educate participants about the ever-changing threat landscape, common vulnerabilities in information systems, and effective techniques for mitigating and preventing data breaches.
Secure devices: All organizational devices should be safeguarded against physical damage and unauthorized access. Implementing security measures to deter hacking attempts is critical. Tools like Google Workspace and Office 365, which provide built-in device security features, should be installed across all devices to enhance protection.
Encrypt data: Encryption is a critical defense mechanism against unauthorized access and is vital for securing sensitive information. All organizational data should be encrypted as a preparatory step before implementing an ISMS to safeguard against unauthorized access or tampering.
Back up data: Data backups are crucial for preventing data loss and should be integrated into the organization’s security policies before establishing an ISMS. Planning the location and frequency of backups is important, and measures should be in place to secure backup data, applicable to both on-premises and cloud storage.
Conduct an internal security audit: Prior to implementing an ISMS, conducting an internal security audit is advisable. These audits allow organizations to examine their security infrastructure, software, and devices thoroughly, helping to identify and rectify security vulnerabilities. This proactive step ensures a more secure environment before the ISMS goes live.
Implementation of an ISMS
Setting up an ISMS can be approached in several ways. Many organizations adopt the plan-do-check-act methodology or adhere to the ISO 27001 international security standard, which provides detailed guidelines for establishing an ISMS.
Here are the key steps to implement an ISMS effectively:
Define the scope and objectives: Start by determining which assets require protection and the reasons for protecting them. Consider what clients, stakeholders, and trustees expect to be secured. Management should establish specific objectives concerning the application areas and boundaries of the ISMS.
Identify assets: Pinpoint the assets that need safeguarding. This involves compiling an inventory of critical business assets, such as hardware, software, services, information, databases, and physical sites, using a business process map.
Assess the risks: Once assets are cataloged, analyze and score their associated risks by considering legal and compliance obligations. Evaluate the potential impacts of risk scenarios, such as the consequences of a breach in confidentiality, availability, or integrity of the information assets, and the likelihood of such breaches. The objective is to decide which risks are tolerable and which must be addressed urgently to prevent significant damage.
Plan risk mitigation: A robust ISMS identifies risks and also devises effective strategies to mitigate them. Mitigation strategies should include clear plans to either completely avoid certain risks or reduce them to an acceptable level. For instance, to prevent the risk of data loss from stolen laptops, enforce policies that prohibit storing sensitive customer data on portable devices. If you need assistance with implementing said mitigation/controls consider using an iso 27002 implementation guide.
Continuous improvement: Regularly monitor, audit, and review the effectiveness of the ISMS. If this monitoring uncovers any shortcomings or new risk factors, the ISMS process should be reevaluated and restarted from the beginning. This continual refinement allows the ISMS to adapt swiftly to changes and enhances the organization’s ability to manage information security risks effectively.
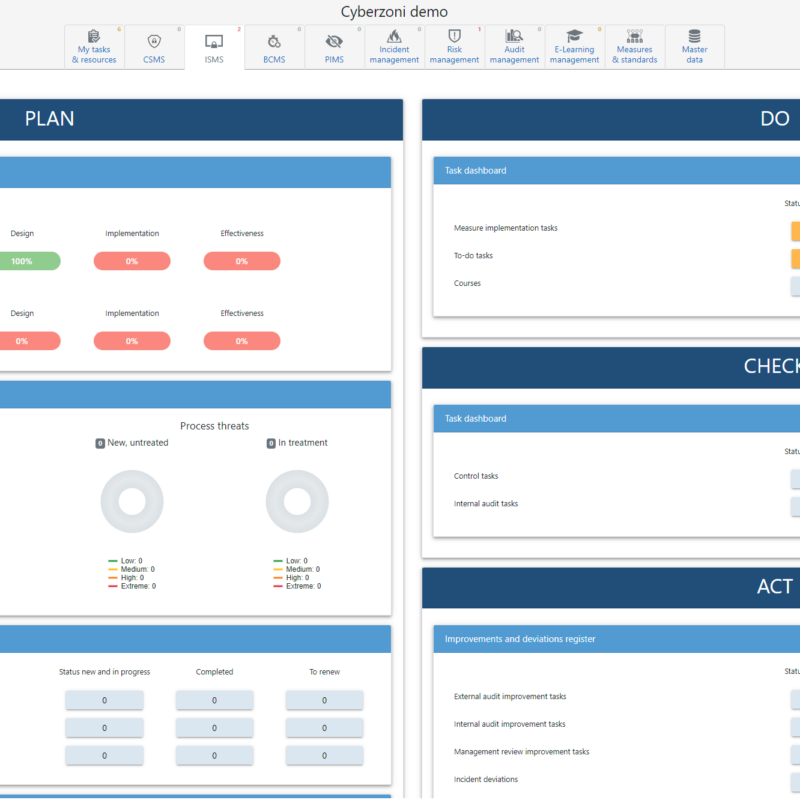
CyberManager: The ISMS Solution
CyberManager offers advanced Information Security Management System (ISMS) and Privacy Information Management System (PIMS) capabilities, making it an essential tool for organizations aiming to comply with standards like ISO27001, GDPR, and more. It features a real-time dashboard for security monitoring, efficient task management through a Plan-Do-Check-Act framework, and robust audit readiness, preparing organizations for both internal and external evaluations. With GDPR alignment and effective data breach management, it seamlessly integrates security and privacy management, supported by an intuitive user interface and single sign-on integration. Whether enhancing security protocols or ensuring business continuity, CyberManager provides a scalable solution tailored to meet stringent regulatory needs and manage risks effectively.
-
CyberManager
Software € 1.850,00 – € 33.250,00 Select options This product has multiple variants. The options may be chosen on the product page
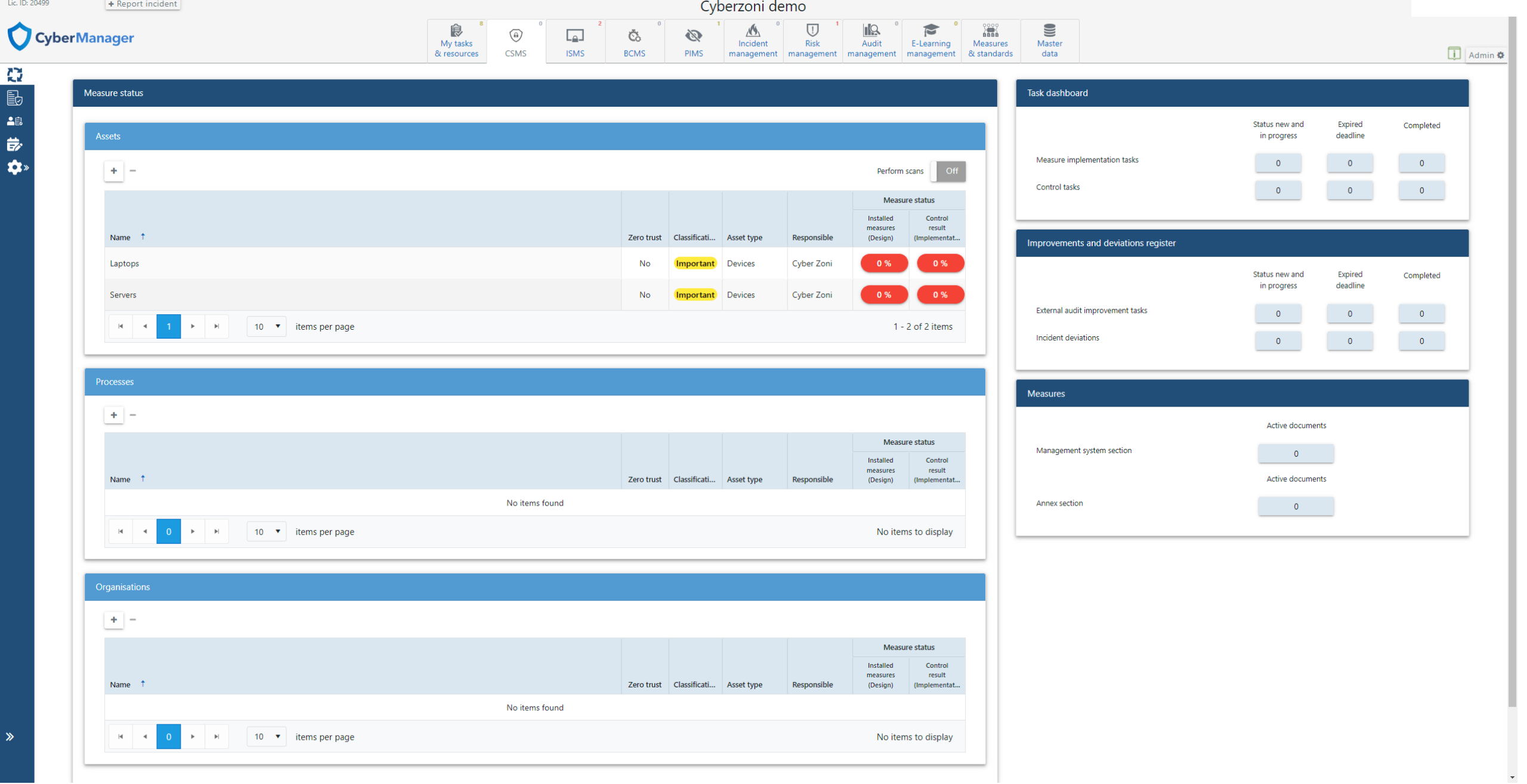
Cyber Security Management System (CSMS) Overview
The Cyber Security Management System (CSMS) within CyberManager offers a suite of tools designed to increase your organization’s cybersecurity defenses. Key features include:
- One-Click Cyber Risk Insights: Gain immediate access to an overview of your cybersecurity risks and vulnerabilities through the CSMS dashboard, enabling quick assessments and decisions.
- Comprehensive Standards Management: Align your security practices with critical cybersecurity standards such as NIST-CSF and IEC 62443, ensuring comprehensive compliance and oversight.
- Integrated Vulnerability Scanning: Actively detect and address security weaknesses with integrated scanning tools that highlight and suggest improvements for vulnerabilities, helping prevent potential breaches and strengthen security measures.
These features make CSMS an invaluable tool for any organization seeking to fortify its cybersecurity posture and maintain high standards of risk management.