Managed Security Service Provider
We specialize in providing cybersecurity solutions custom to the unique needs of your business. With over 10 years of experience as a Managed Security Service Provider (MSSP) and expertise in healthcare, DoD contractors and operational technology (OT) protection, we offer a wide range of services. From ISO 27001 templates and audit checklists to full CISO support, our services are purposeful made to offer you the best assistance to your organization.
Templates and Tools
Get structured documents that bring clarity to your security goals, making compliance a manageable and efficient process for your team.
Framework Guidance
Not sure how to handle all those frameworks and standards? Our guidance gives you the clarity and tools you need to tackle compliance with confidence—step by step.
CISO Service
Our tiered CISO support services—from basic guidance to full security leadership—equip your organization with the strategic oversight it needs.
Cyber Security Managed Services

We provide reliable and proactive Cyber Security Managed Services to protect and advice your business from cyber risks. Our dedicated team has deep industry expertise to stay ahead of cybercriminals.
Expertise and Specialization
Our team consists of industry leaders equipped with the latest knowledge on cyber threats and defensive technologies.
Cost Efficiency
We provide a cost-efficient solution by minimizing the expenses involved in staffing, training, and maintaining security operations






Latest Products
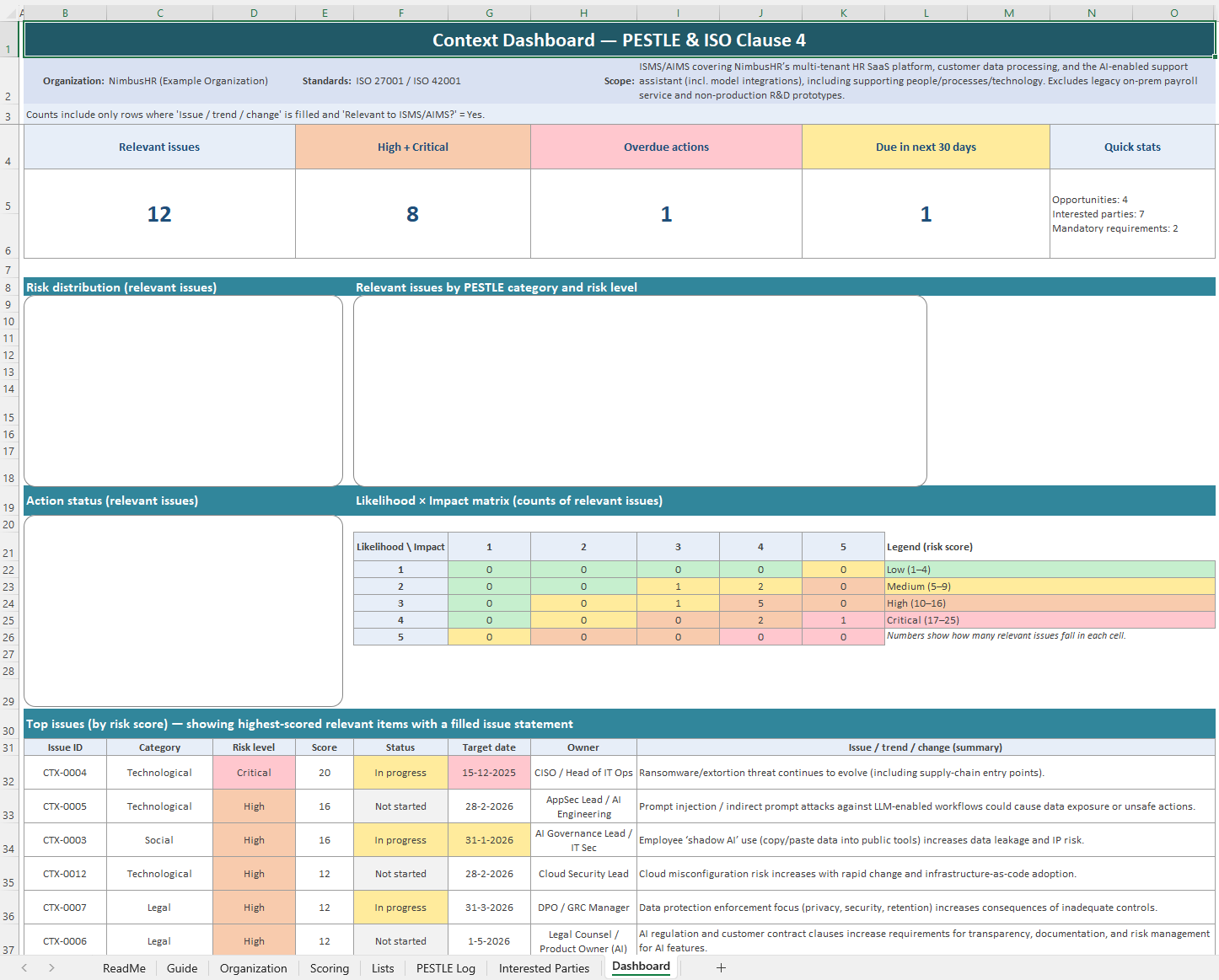
PESTLE Analysis Template (ISO 27001 & ISO 42001)
- Excel workbook (XLSX) — pestle analysis template
- Built for pestle analysis ISO 27001/42001 Clause 4
- PESTEL framework template: log external/internal issues
- Likelihood/impact scoring + 5×5 risk matrix
- Executive dashboard with KPIs, charts, heatmap
- Interested parties register for Clause 4.2 requirement
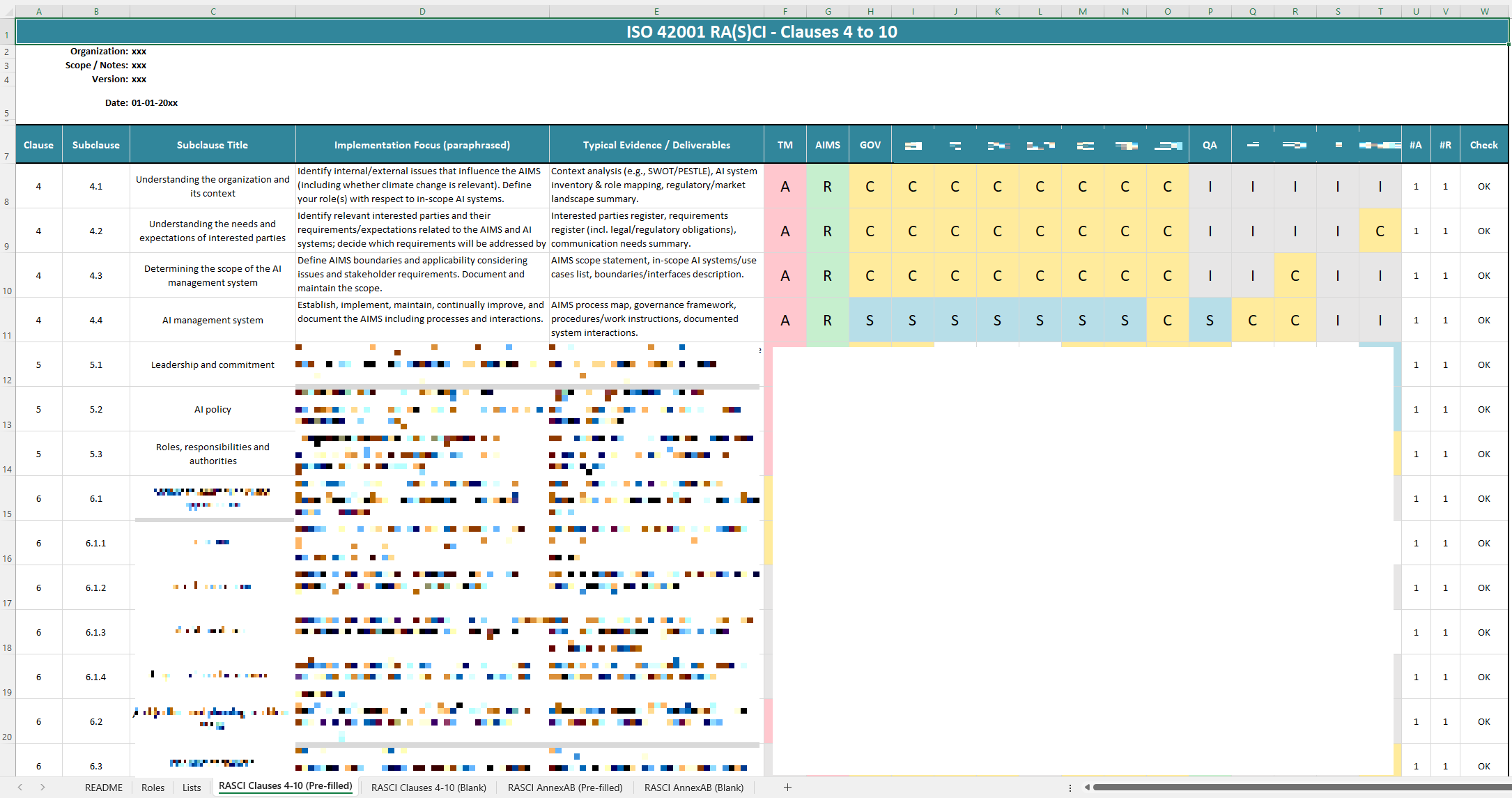
ISO 42001 RACI Matrix Template
- Covers ISO 42001 Clauses 4–10 + subclauses
- Includes Annex A controls RA(S)CI + Annex B guidance reference fields
- Role library for alignment with business structure
- Dropdown RA(S)CI selections for consistent assignment
- Built-in checks for missing Accountable/Responsible
- Instant download, ready to customize
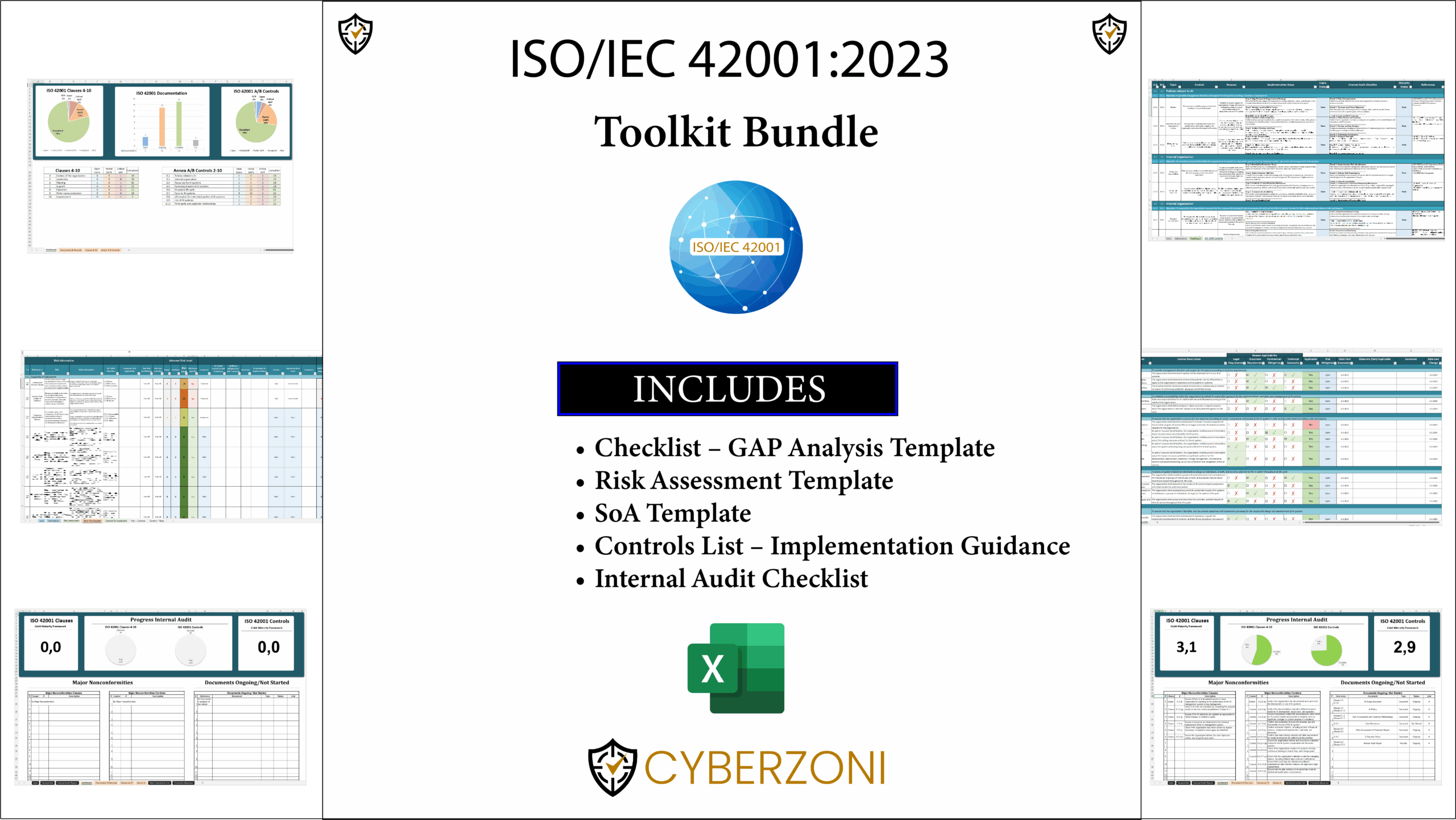
ISO 42001 Toolkit Bundle
The ISO 42001 Toolkit contains the following Excel templates:
- ISO 42001 Checklist – GAP Analysis Template
- ISO 42001 Risk Assessment Template
- ISO 42001 SoA Template – Statement of Applicability
- ISO 42001 Controls List – Implementation Guidance
- ISO 42001 Internal Audit Checklist
- ISO 42001 RACI Matrix Template
- PESTLE Analysis Template
Mature Your Compliance Process
Take the guesswork out of compliance with our streamlined tools. From our ISO 27001 Gap Analysis Template to our ISO 27001 Core Documents Bundle, these resources provide everything you need to manage compliance with ease, helping your team stay focused on protecting critical assets.
Identify and Mitigate Risks Efficiently
Provide your team with our ISO 27001 Risk Assessment Template to proactively identify and manage risks. Made to simplify the risk management process, this template helps with a well-prepared security posture to address vulnerabilities and increase your maturity.
Vendor and Supplier Security
Protect your business by securing your supply chain. Our Procurement Supplier Risk Assessment Template is made to help you assess and mitigate third-party risks, to make sure that all partners meet your security requirements.
Prepare for ISO 27001 Audits
Our ISO 27001 Audit Checklist leaves no compliance point unchecked, helping your team confidently prepare for audits and strengthen your organization’s security framework.

Managed Cyber Security
Stay a step ahead of cyber threats with our expert-managed services. Our custom approach covers all aspects of cybersecurity, protecting your data and applications. Gain cost-effective security and operational efficiency, letting you focus on business growth while we ensure your defenses are strong.
Pen-testing and vulnerability Scanning
Stay ahead of vulnerabilities with our Vulnerability Scanning service. Proactively detect and address potential security gaps, this service equips your business with the insights needed. Gain protection against threats, ensuring the safety and integrity of your data and systems.
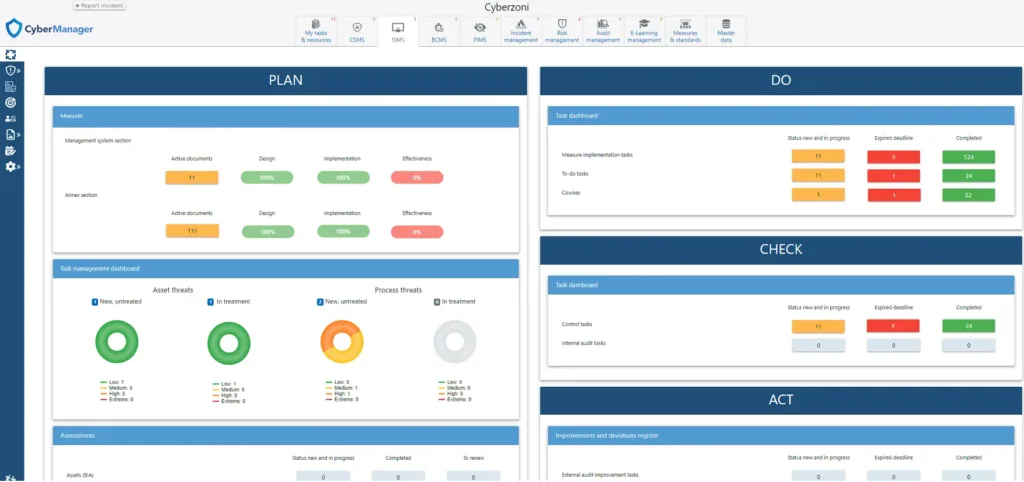
Cybermanager
CyberManager is your go-to solution for Information Security Management (ISMS). Simplify compliance, increase cybersecurity maturity, and reduce risks effectively. With CyberManager, you gain a powerful tool to manage information security.
Latest Articles
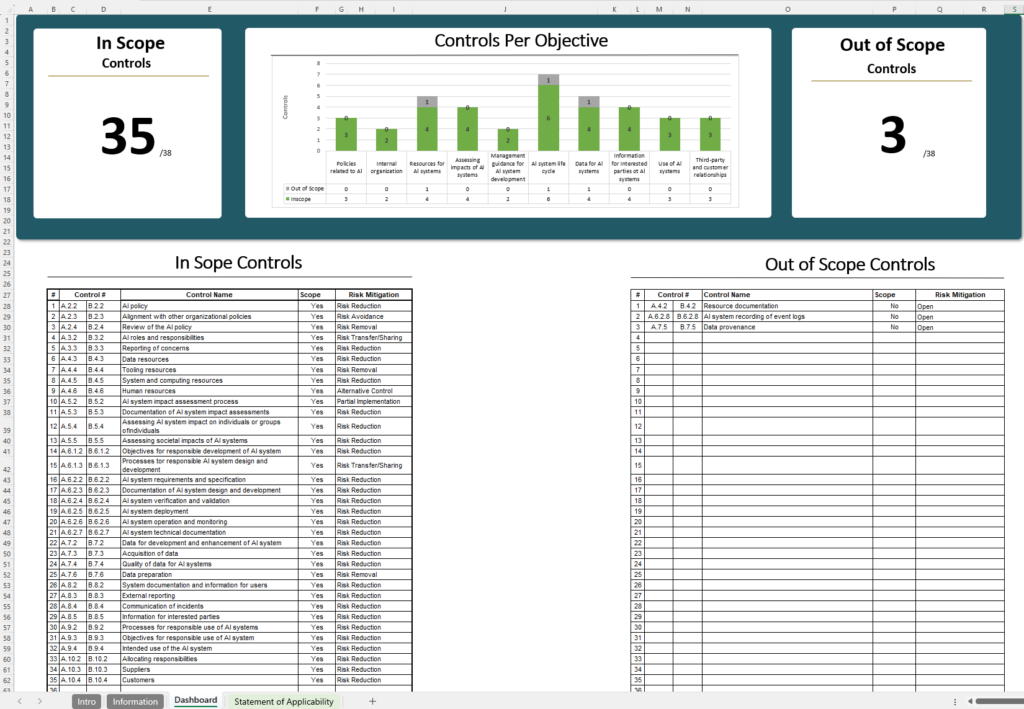
ISO 42001 Statement of Applicability (SoA)
In ISO 42001, the Statement of Applicability (SoA) outlines the specific Annex A controls your organization has chosen to implement (or omit) based on its AI risk assessment, along with reasons for those decisions. This document is crucial for ISO 42001 certification, as it demonstrates your organization’s commitment to ethical and compliant AI management by addressing key AI risks (e.g. bias, privacy, transparency) with appropriate controls.
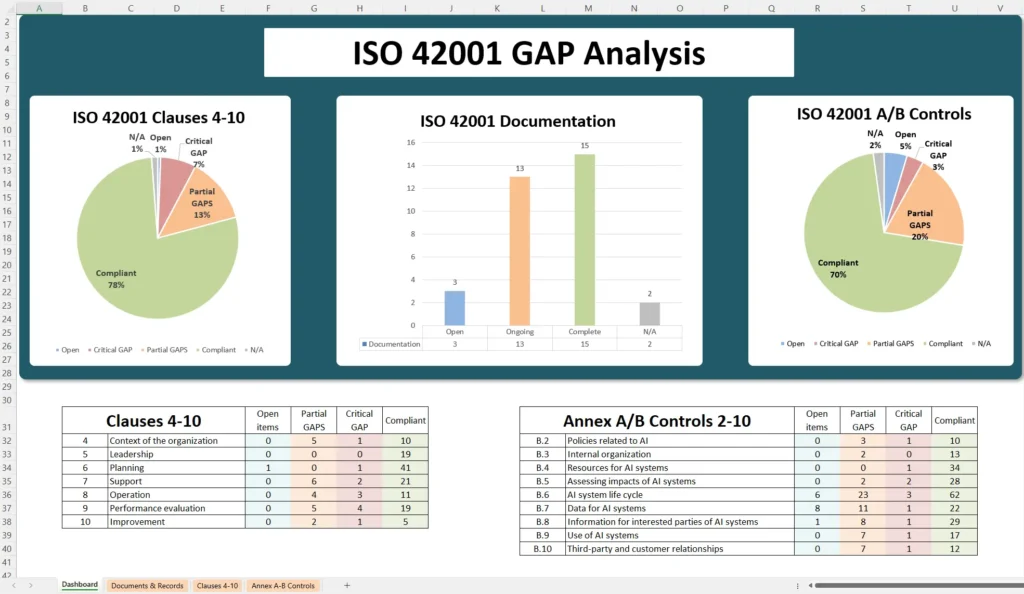
ISO 42001 Gap Analysis
Conducting an ISO 42001 GAP analysis is a critical first step toward trustworthy and compliant AI systems. With thoroughly examining your organization’s AI governance against the standard’s requirements, you gain clear insight into where you stand and what needs improvement. This process, when done with a structured approach and the right tools, demystifies the path to ISO 42001 compliance.

5 Whys in Cybersecurity Audits
The 5 Whys methodology, when applied with care, can significantly enhance internal audits and compliance efforts in cybersecurity. It aligns perfectly with the continuous improvement ethos of standards like ISO and NIST – turning every audit finding or incident into a chance to strengthen the system. With digging down to root causes your organization can avoid superficial fixes and instead implement changes that are more effective and permanent.
What Our Clients Say About Us
The CISO support provided by CyberZoni was a game changer for our team. Their expert guidance on management and security awareness helped us secure our business from potential threats. I highly recommend them for startups looking to implement cybersecurity the right way!
Alex M.
Head of IT Security
We needed a more mature cybersecurity strategy that could scale as we grew. CyberZoni’s CISO Support was exactly what we needed. Their incident response planning and management advice made a huge difference.
Jennifer R.
Information Security Manager
After experiencing a data breach, we partnered with CyberZoni for full CISO support. Their hands-on approach to security management, from penetration testing to vendor security management, helped us a great deal.
Michael P.
Security Operations Manager