CyberManager Standard
ISMS+PIMS
Optimal Security and Privacy Management for Progressive Organizations
Overview: CyberManager Standard offers a robust Information Security Management System (ISMS) and Privacy Information Management System (PIMS), crucial for organizations seeking compliance with ISO27001, NEN7510, BIO, SOC2, ISAE3402, and GDPR standards.
Key Features:
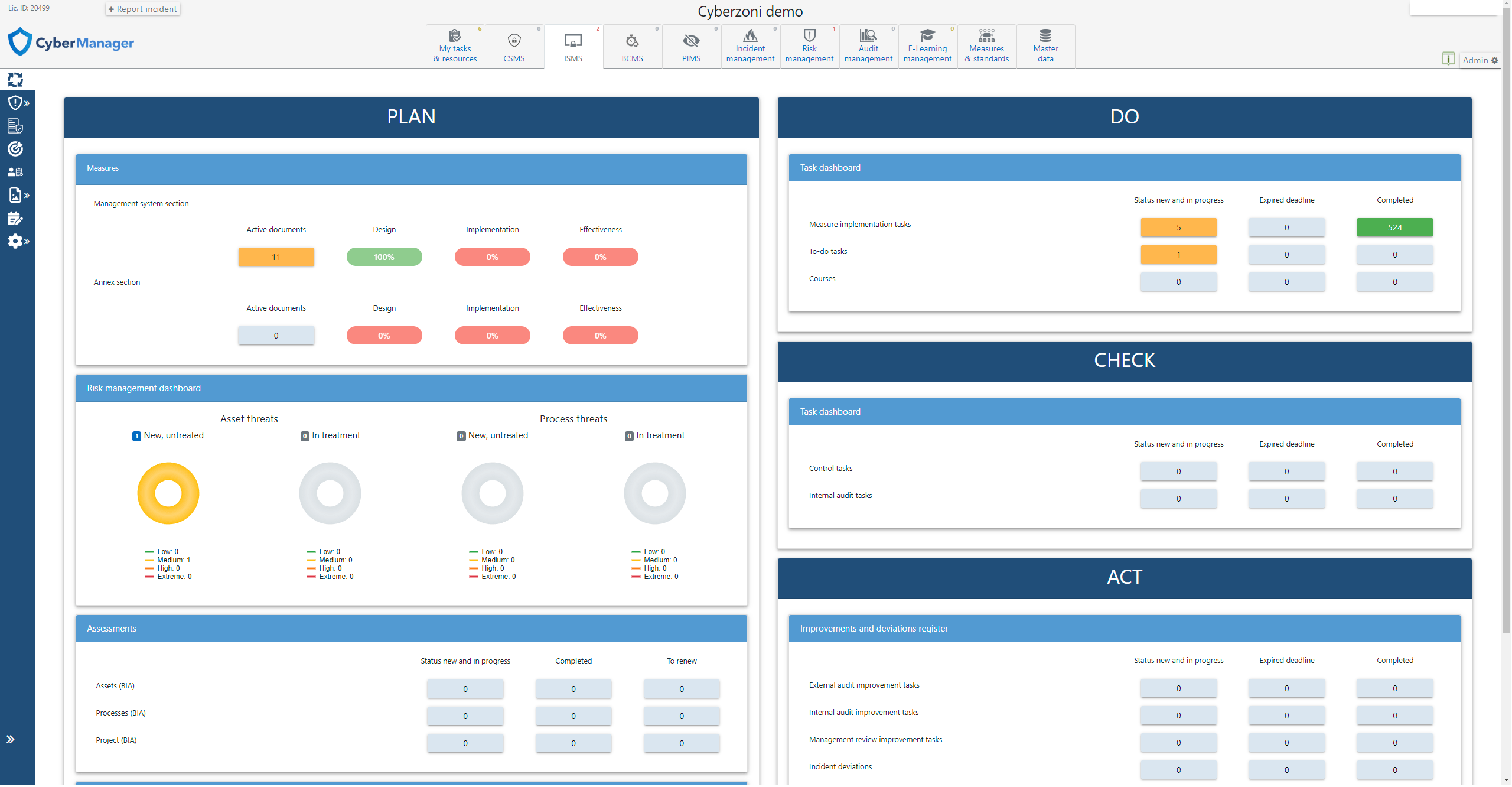
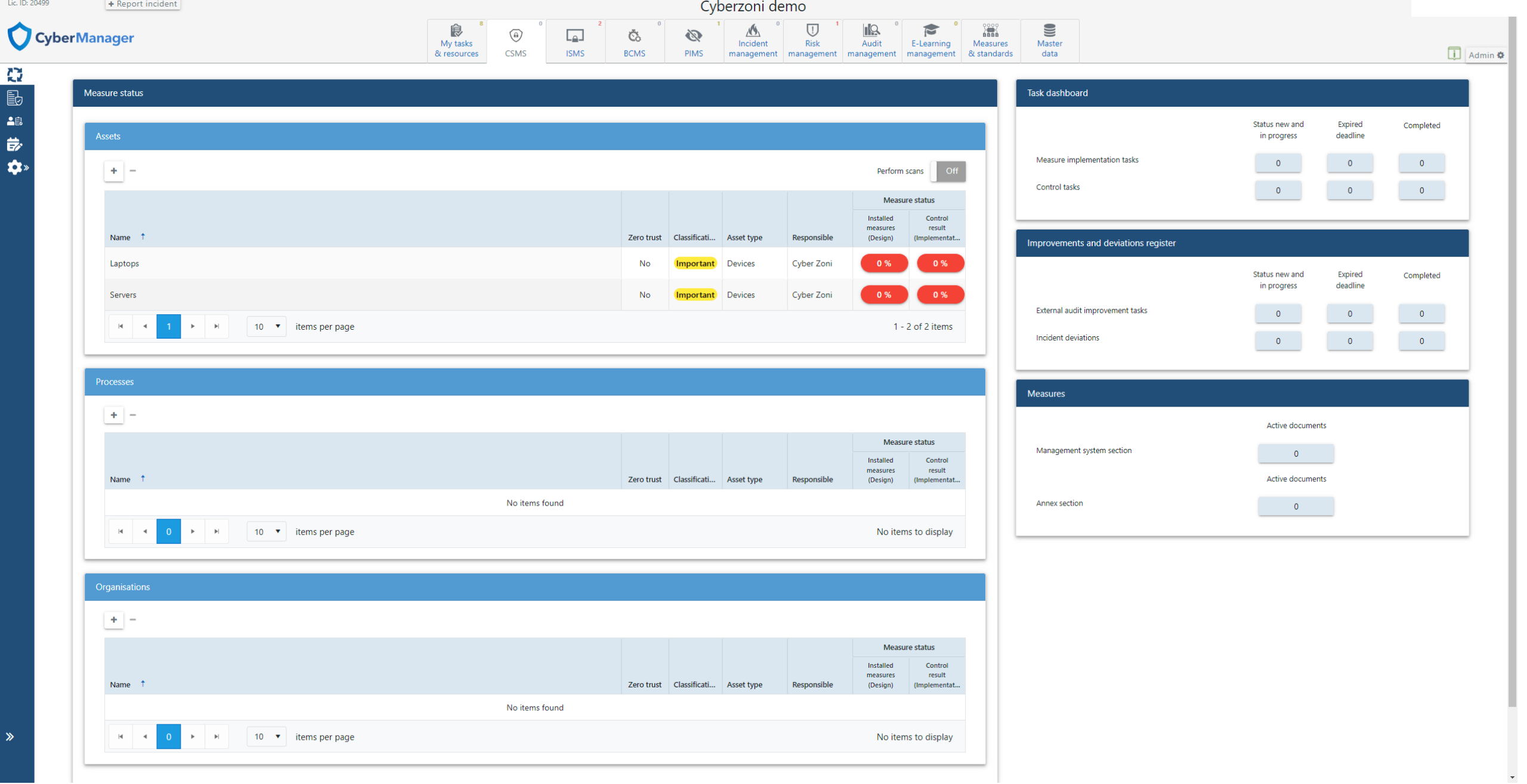
Information Security Management System (ISMS):
- Comprehensive Compliance: Aligns with major standards like ISO 27001, ensuring your organization meets global security benchmarks.
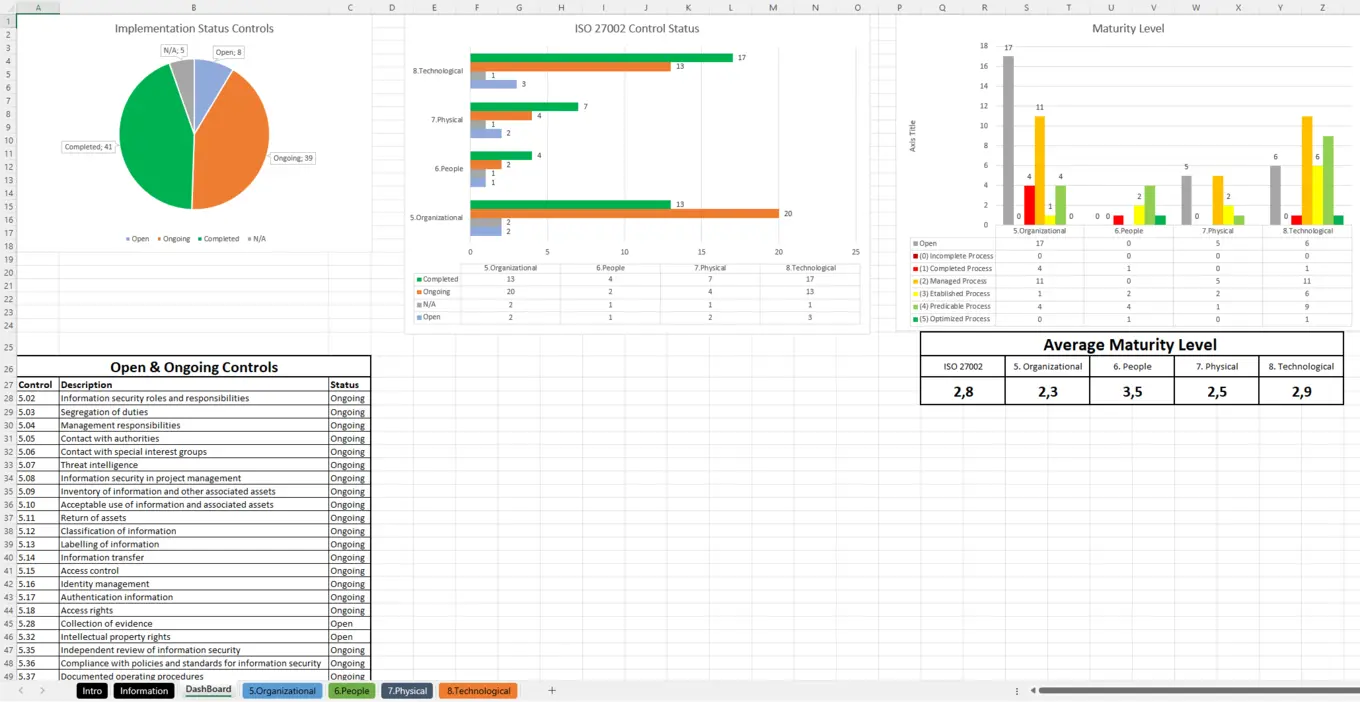
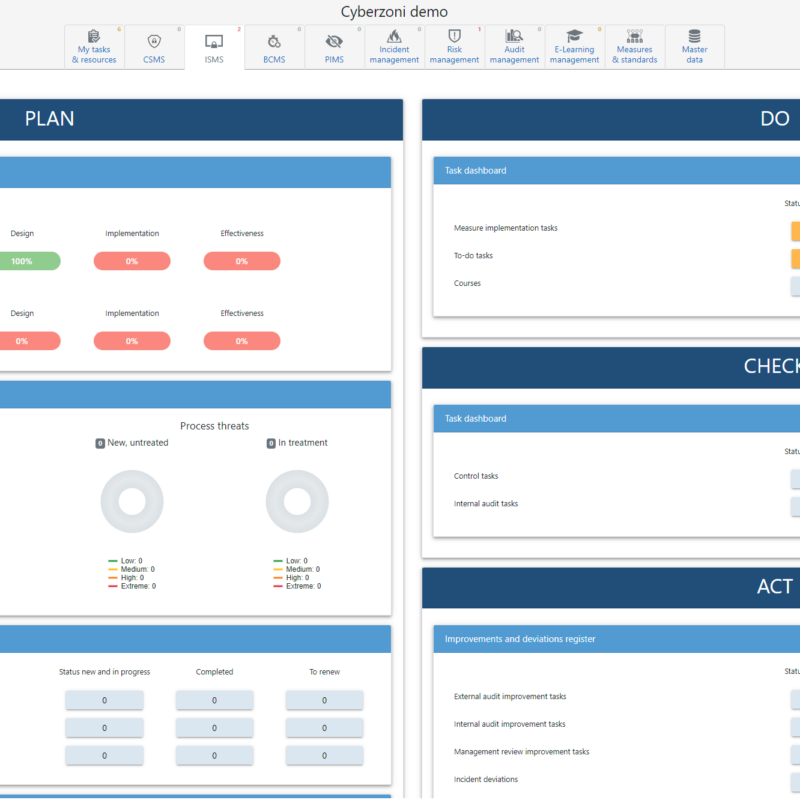
- Real-Time Dashboard: Offers a dynamic ISMS dashboard, presenting a holistic view of your security posture, implementation status, and control measures.
- Efficient Task Management: Utilizes a Plan-Do-Check-Act framework, enabling streamlined management of security tasks and responsibilities.
- Risk and Incident Management: Advanced risk management features, including a detailed risk register and efficient incident response capabilities.
- Audit Readiness: Features an audit management system, preparing your organization for both internal and external audits.
Privacy Information Management System (PIMS):
- GDPR Alignment: Fully equipped to manage GDPR requirements with a comprehensive processing register and DPIA management tools.
- Data Breach Management: Efficiently manage and report data breaches, ensuring compliance and minimizing impact.
- Seamless Integration: Integrates with ISMS, allowing for a unified approach to managing security and privacy risks.
General Functionalities:
- Customizable email notifications, multilingual support, secure document storage, and robust 2FA security.
- An intuitive user interface with audit logs, customizable fields, and advanced user group management.
- Single Sign-On Integration:
- Effortless Access Control: Offers integration with ADFS, AzureAD, and Okta, streamlining user access management.
- Enhanced Security and Convenience: Ensures secure and convenient access across multiple environments.
Why Choose CyberManager Standard?
- It provides a solid foundation for organizations embarking on their information security and privacy journey. With its user-friendly interface, comprehensive feature set, and adherence to global standards, CyberManager Standard is the ideal choice for businesses seeking to enhance their security posture and ensure regulatory compliance.
CyberManager Advanced
ISMS+PIMS+CSMS
Advanced Security Solution for Comprehensive Risk Management
Overview: Building upon the Standard package, the Advanced version introduces the Cyber Security Management System (CSMS), offering an enriched suite for organizations needing a more sophisticated security approach.
Enhanced Features:
- Cyber Security Management System (CSMS):
- One-Click Cyber Risk Insights: Get instant visibility into your cyber risks and vulnerabilities directly from the CSMS dashboard.
- Comprehensive Standards Management: Manage and align with key cyber security standards such as NIST-CSF and IEC 62443.
- Integrated Vulnerability Scanning: Proactively identify and address vulnerabilities with integrated scanning and improvement activities.
Why Choose CyberManager Advanced?
- For organizations that require an all-encompassing view of their security landscape, including cyber risks, the Advanced package is unmatched. It not only provides foundational security and privacy management but also introduces advanced cyber security capabilities, making it ideal for businesses facing complex security challenges in a dynamic environment.
CyberManager PRO
ISMS+PIMS+CSMS+BCMS
The Pinnacle of Integrated Security and Business Continuity Management
Overview: CyberManager PRO is the ultimate package, adding Business Continuity Management System (BCMS) to the robust features of the Advanced version. It’s designed for organizations demanding the highest level of resilience and risk management.
Exclusive Features:
- Business Continuity Management System (BCMS):
- Comprehensive Business Continuity Planning: Offers tools for thorough business continuity assessments and planning.
- ISO 22301 Compliance: Fully aligned with the ISO 22301 Standard for business continuity.
- Seamless Integration: Integrates with ISMS and CSMS, ensuring a holistic approach to organizational resilience.
Why Choose CyberManager PRO?
- CyberManager PRO is the definitive choice for enterprises seeking to protect against threats and also to ensure continuity in the face of disruptions.
Quality Management System (QMS) Module
Enhancing Operational Excellence and Customer Satisfaction
Overview: The QMS module is an essential addition for organizations focusing on quality assurance, customer satisfaction, and compliance with quality standards such as ISO 9001. This module integrates seamlessly with the CyberManager suite, enhancing the overall risk management capabilities with a focus on quality control.
Key Features:
- Customer Satisfaction Module:
- Survey and Feedback Collection: Facilitate customer satisfaction surveys with ease, using customizable templates and mailing lists.
- Insightful Analytics: Analyze feedback through various dashboards, helping you understand and improve customer satisfaction levels.
- Complaint Registration & Management:
- Efficient Tracking: Register and manage customer complaints efficiently, ensuring prompt resolution and follow-up.
- Comprehensive Reporting: Dashboard views provide insights into complaint sources, progress, and resolution outcomes.
- ISO 9001 Management System Integration:
- Unified Control System: Integrates with the CyberManager’s Plan-Do-Check-Act system, streamlining complaint handling, incident management, and control tasks.
- Continuous Improvement: Supports continuous improvement practices, with tools for internal and external audits, documentation, and management reviews.
Benefits of QMS Module:
- Aligns quality management processes with overall organizational objectives.
- Enhances customer trust and satisfaction, leading to better client retention and brand reputation.
- Ensures compliance with international quality standards, providing a competitive edge in the market.
Financial Risk Management System (FRMS) Module
Robust Protection Against Financial Threats and Fraud
Overview: The FRMS module is designed for organizations looking to fortify their financial operations against fraud, including CEO Fraud, phishing, and other cyber threats. This module complements the CyberManager suite by adding a focused layer of financial risk management.
Key Features:
- Proactive Control Measures:
- Risk Analysis & Control Implementation: Perform detailed risk analyses and implement control measures tailored to financial processes.
- Implementation Status & Effectiveness Monitoring: Monitor the implementation and effectiveness of controls, enhancing financial security.
- Integrated Awareness Program:
- Customized Training: Tailored awareness programs addressing risks like CEO fraud, phishing, and ransomware.
- Preventive Measures: Emphasize on prevention, equipping employees with knowledge and tools to recognize and respond to threats.
- Compliance with Financial Frameworks:
- Support for Own and Standard Frameworks: Compatible with custom and standard frameworks like ITGC.
- Visibility into Risk Awareness: Provides insights into employee risk awareness, aiding in informed decision-making.
Benefits of FRMS Module:
- Significantly reduces the risk of financial fraud, safeguarding your organization’s assets and reputation.
- Empowers employees with the knowledge to identify and react to financial threats.
- Ensures compliance with financial regulations and standards, reinforcing investor and stakeholder confidence.
Flexible User Options for All Business Sizes
Overview: Our system is designed to cater to organizations of all sizes, offering a range of user types and instances to fit your specific needs. Whether you’re a small business or a large corporation, you can choose a plan that aligns with your operational scale and complexity.
User Types:
- Task User:
- Role: A Task User is someone who can complete specific tasks assigned to them. These tasks might include actions like carrying out a deployment, conducting an audit, or completing a to-do item.
- Focus: Their role is more focused and task-oriented.
- Management User:
- Role: A Management User has broader responsibilities. They can deploy tasks, manage processes, and access all other management functionalities of the system.
- Capabilities: They are equipped to handle more complex and administrative aspects of the system.
Available Plans:
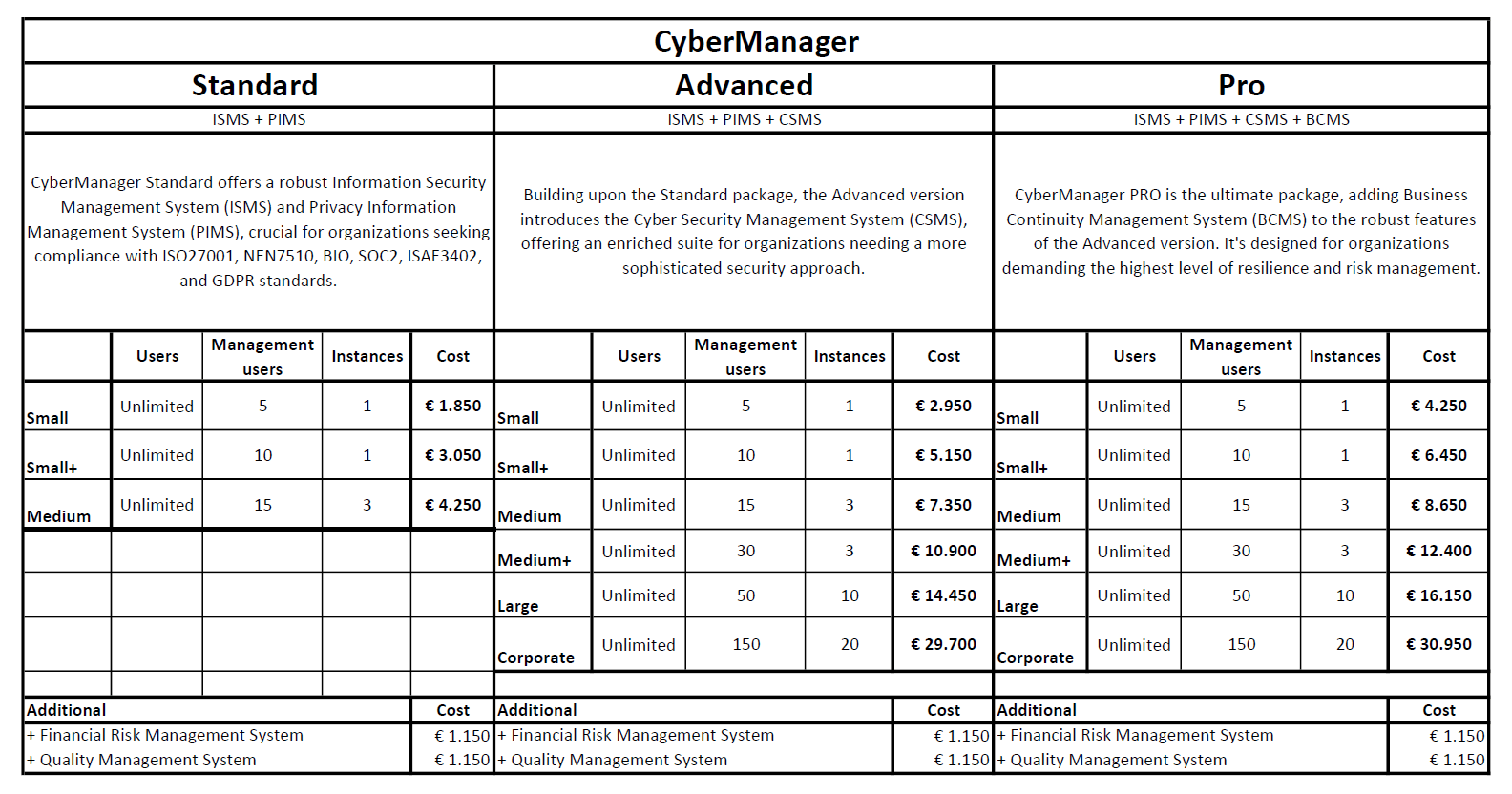
- Small:
- Management Users: 5
- Instances: 1 (single operational instance)
- Ideal for: Small businesses or startups with limited management needs.
- Small+:
- Management Users: 10
- Instances: 1
- Ideal for: Growing small businesses requiring more managerial oversight.
- Medium:
- Management Users: 15
- Instances: 3 (allowing for broader operational scope)
- Ideal for: Medium-sized businesses with multiple operational areas.
- Medium+:
- Management Users: 30
- Instances: 3
- Ideal for: Larger medium-sized businesses with extensive management requirements.
- Large:
- Management Users: 50
- Instances: 10 (suitable for large-scale operations)
- Ideal for: Large organizations needing substantial management capacity.
- Corporate:
- Management Users: 150
- Instances: 20 (extensive operational reach)
- Ideal for: Large corporations with complex, multi-faceted operations.
Choosing the Right Plan: Selecting the right plan depends on the size of your organization and the complexity of your operations.
Smaller businesses may benefit from plans with fewer management users and instances, while larger organizations will likely require more extensive options.
Wide Range of Supported Standards for Comprehensive Compliance
Our system provides extensive support for a variety of international and national standards, ensuring that your organization can achieve and maintain compliance across multiple areas, including information security, privacy, quality management, and more.
Supported Standards:
- ISO 27001: International standard for information security management systems (ISMS), focusing on protecting and securing data.
- AVG (GDPR): The General Data Protection Regulation, known as AVG in Dutch, sets guidelines for the collection and processing of personal information within the EU.
- ISO 27701: Provides guidance for privacy information management within the context of an ISMS, complementing GDPR requirements.
- ISO 22301: International standard for business continuity management systems, ensuring resilience and recovery in the event of disruptions.
- NEN 7510: Dutch standard for information security in healthcare, ensuring patient data is handled securely and privately.
- BIO (Baseline Information Security Government): Dutch government standard for information security, covering all levels of government.
- TISAX (Trusted Information Security Assessment Exchange): A standard for information security in the automotive industry, particularly in Germany.
- SOC2: Framework for managing data based on five “trust service principles” — security, availability, processing integrity, confidentiality, and privacy.
- ISAE 3402: International auditing standard for assurance reports on controls at service organizations.
- CSIR: Cybersecurity Information Sharing and Reporting, focusing on sharing information about cyber threats and vulnerabilities.
- NIST CSF (National Institute of Standards and Technology Cybersecurity Framework): Provides guidelines on how to prevent, detect, and respond to cyberattacks.
- IEC 62443: International standard for the security of industrial automation and control systems.
- NIS2 Directive: European directive focused on improving cybersecurity across the EU.
- PCI/DSS (Payment Card Industry Data Security Standard): Security standard for organizations that handle branded credit cards to ensure secure transactions.
- ISO 9001: International standard for quality management systems, focusing on meeting customer and regulatory requirements.
- CIS Controls: A set of actions for cyber defense that provide specific and actionable ways to stop today’s most pervasive and dangerous attacks.
- NTA 7516: Dutch standard for secure email and chat applications in the healthcare sector.
- AFM (Dutch Authority for the Financial Markets): Regulations for behavior and integrity in the financial markets.
- DigiD: Dutch digital identification system, ensuring secure access to government and healthcare services.
- NoreaPCF (Norea Privacy Control Framework): Dutch framework for privacy controls and assessments.
- ITGC (Information Technology General Controls): Controls that ensure the integrity of the data and information technology systems.
- ENSIA (Eenduidige Normatiek Single Information Audit): Dutch framework for information security in municipalities.
- ISO 14001: International standard for environmental management systems, focusing on environmental responsibilities.
- NBA (Netherlands Institute of Chartered Accountants): Standards and guidelines for accountancy in the Netherlands.
- And More!
Benefits of Supported Standards:
- Comprehensive Compliance: Our system supports a broad range of standards, ensuring your organization can meet diverse regulatory requirements.
- Streamlined Management: With support for these standards, you can manage multiple compliance requirements within a single, integrated system.
- Adaptability: Whether your focus is on information security, privacy, quality management, or financial regulation, our system adapts to your specific needs.