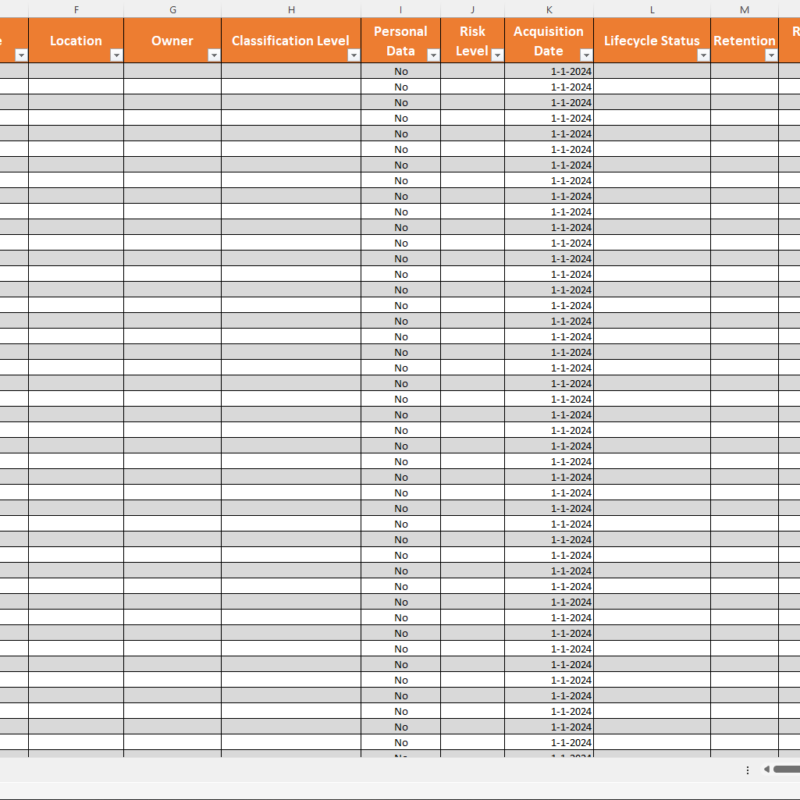
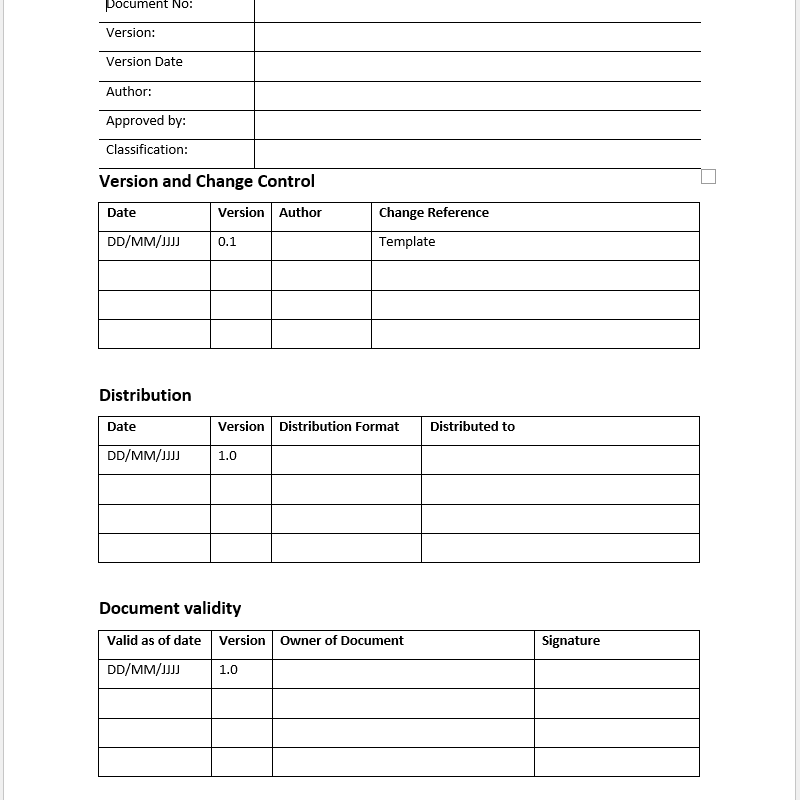
• Excel document.
• Guide for implementing ISO 27002 2022 controls.
• Instructions for an internal audit.
• Overview of 27001:2013 vs. 27001:2022 controls.
• Supplementary control information.
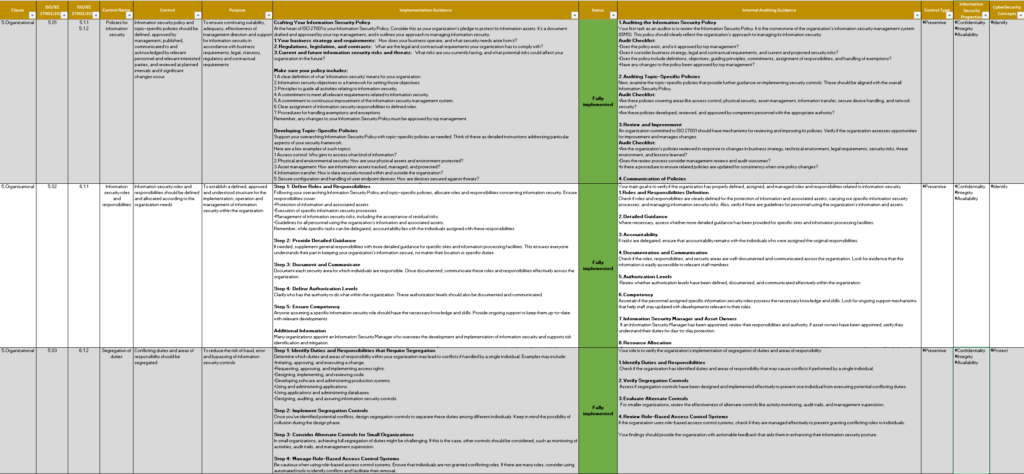
Streamline Your Security Efforts
Our Checklist ISO 27002 transforms complex guidelines into manageable actions. With this tool, you can:

Compliance Checklist ISO 27002
Our checklist is updated regularly to reflect any amendments in the standards, providing you with the confidence that your compliance efforts are always aligned with the latest requirements. It is a reliable resource for organizations of all sizes looking to increase their information security framework and achieve compliance with recognized global standards.
Should you require further details about the Checklist ISO 27002 or wish to discuss how it can be tailored to fit your organization’s needs, our team is available to assist you. Contact us today to learn how we can help you with your compliance process and secure your information assets more effectively.