BLOG
Welcome to the CyberZoni Blog – a destination for the latest in cybersecurity. Here, we cut through the complexity of cybersecurity with clear, insightful analysis and practical advice.
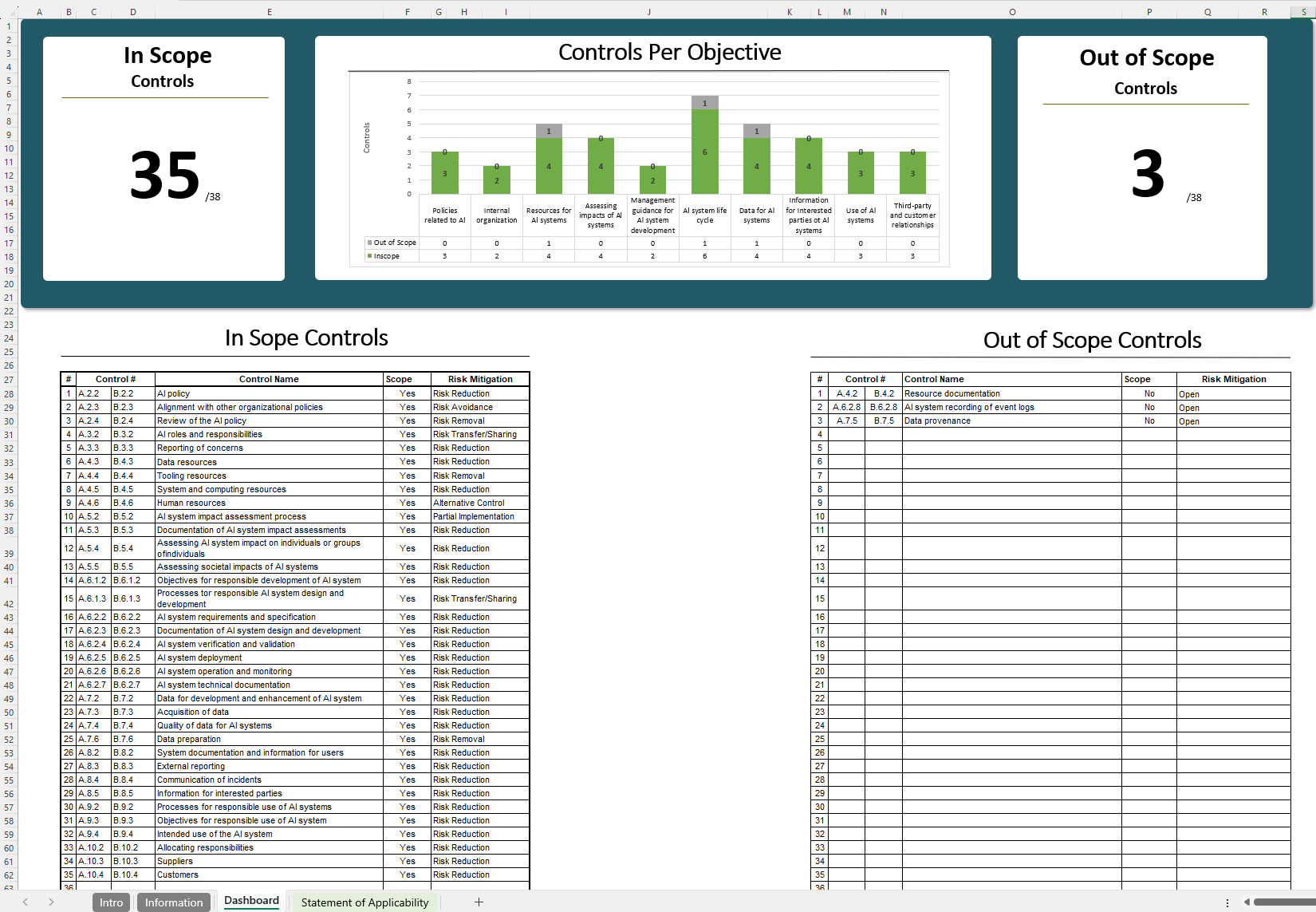
ISO 42001 Statement of Applicability (SoA)
In ISO 42001, the Statement of Applicability (SoA) outlines the specific Annex A controls your organization has chosen to implement (or omit) based on its AI risk assessment, along with reasons for those decisions. This document is crucial for ISO 42001 certification, as it demonstrates your organization’s commitment to ethical and compliant AI management by addressing key AI risks (e.g. bias, privacy, transparency) with appropriate controls.
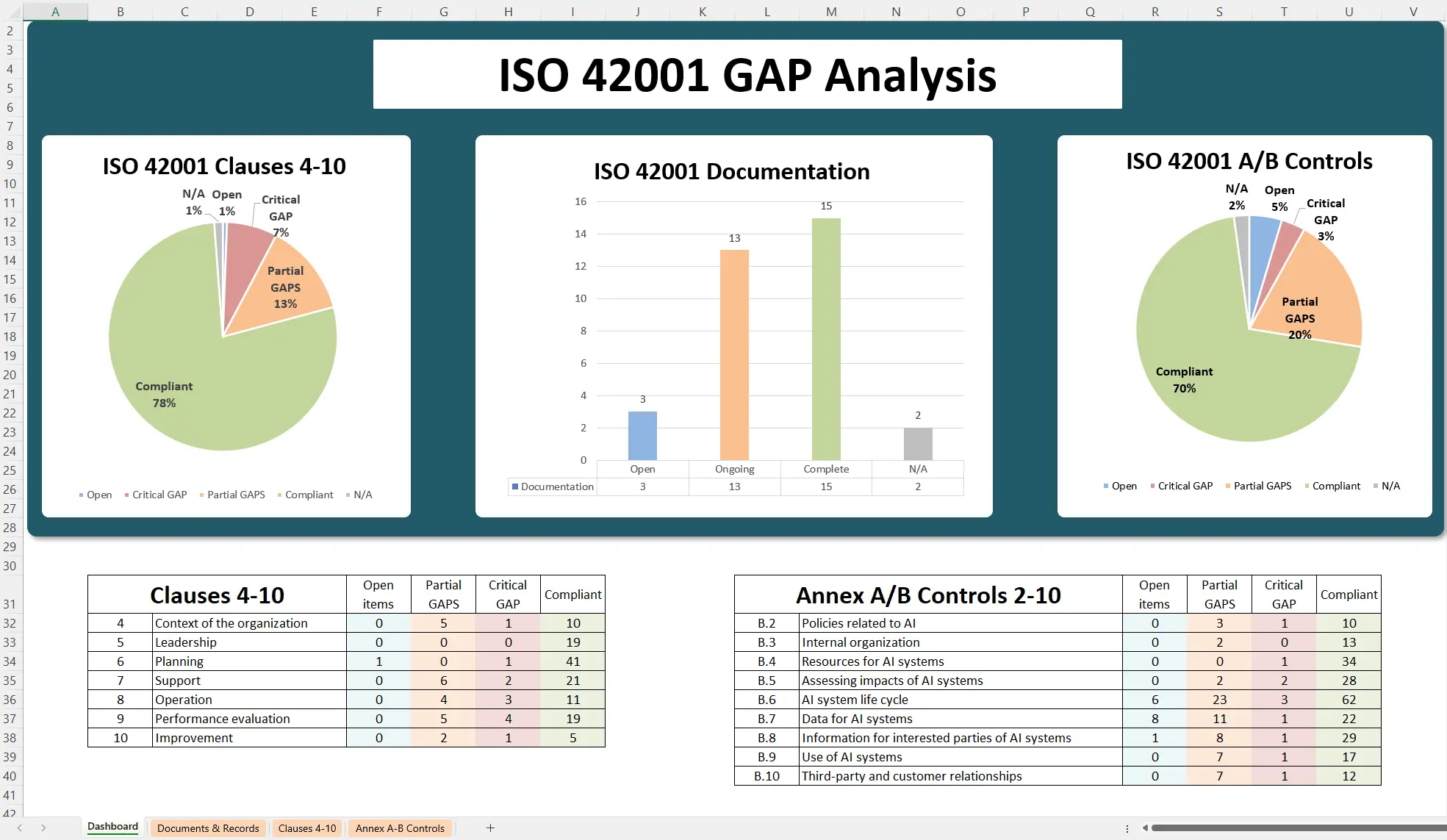
ISO 42001 Gap Analysis
Conducting an ISO 42001 GAP analysis is a critical first step toward trustworthy and compliant AI systems. With thoroughly examining your organization’s AI governance against the standard’s requirements, you gain clear insight into where you stand and what needs improvement. This process, when done with a structured approach and the right tools, demystifies the path to ISO 42001 compliance.

5 Whys in Cybersecurity Audits
The 5 Whys methodology, when applied with care, can significantly enhance internal audits and compliance efforts in cybersecurity. It aligns perfectly with the continuous improvement ethos of standards like ISO and NIST – turning every audit finding or incident into a chance to strengthen the system. With digging down to root causes your organization can avoid superficial fixes and instead implement changes that are more effective and permanent.
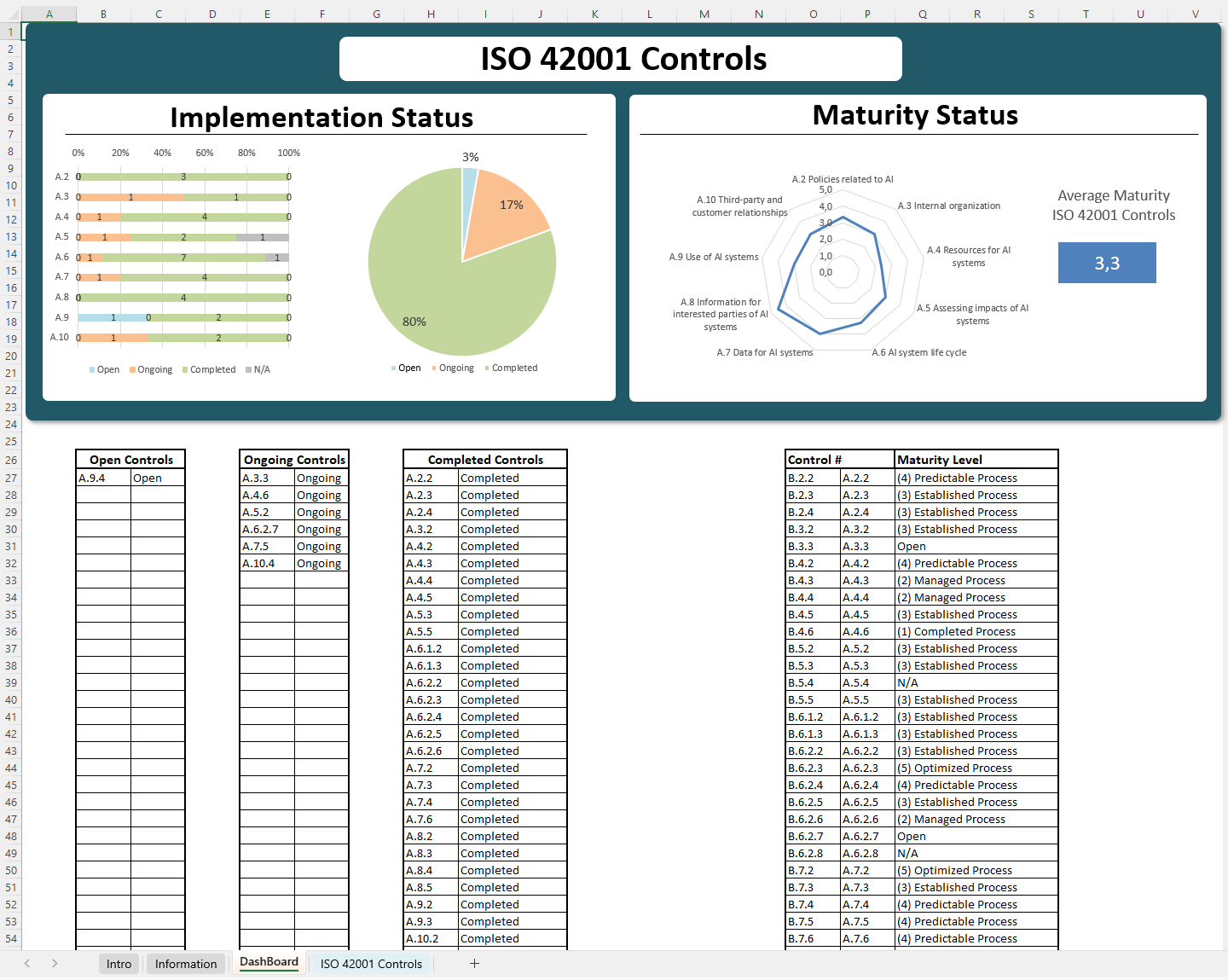
Deploying AIMS Controls
ISO/IEC 42001:2023 is the first international standard for Artificial Intelligence Management Systems (AIMS), published in December 2023. It provides a structured framework for governing AI development, deployment, and use in an ethical and risk-managed way. Much like ISO 27001 for information security, ISO 42001 uses a plan–do–check–act (PDCA) model and includes defined clauses and an annex of controls to ensure AI systems are trustworthy (transparent, accountable, fair, safe, and reliable).

ISMS Internal Audit
The ISMS Internal Audit Process is actually a structured journey to keep your Information ISMS aligned with the ISO/IEC 27001 standard. Think of it as a periodic health check for your organization’s security posture—one that identifies vulnerabilities, confirms compliance, and reveals opportunities to increase your organizations maturity.
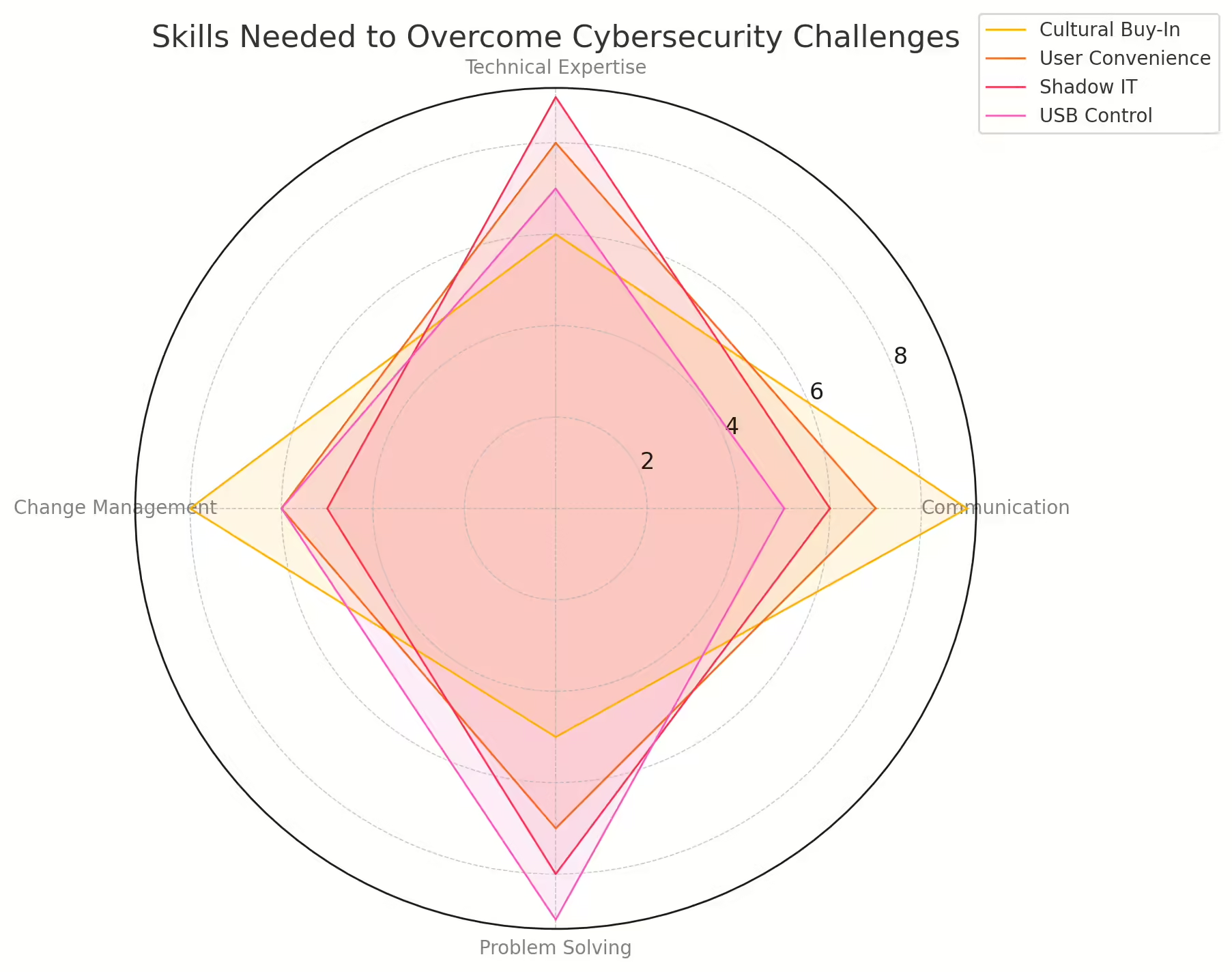
Tackling Cultural Resistance and Security Fatigue in 2024
Implementing security effectively remains challenging for cybersecurity professionals. They face a constant battle between enforcing strict policies and ensuring convenience for end-users.
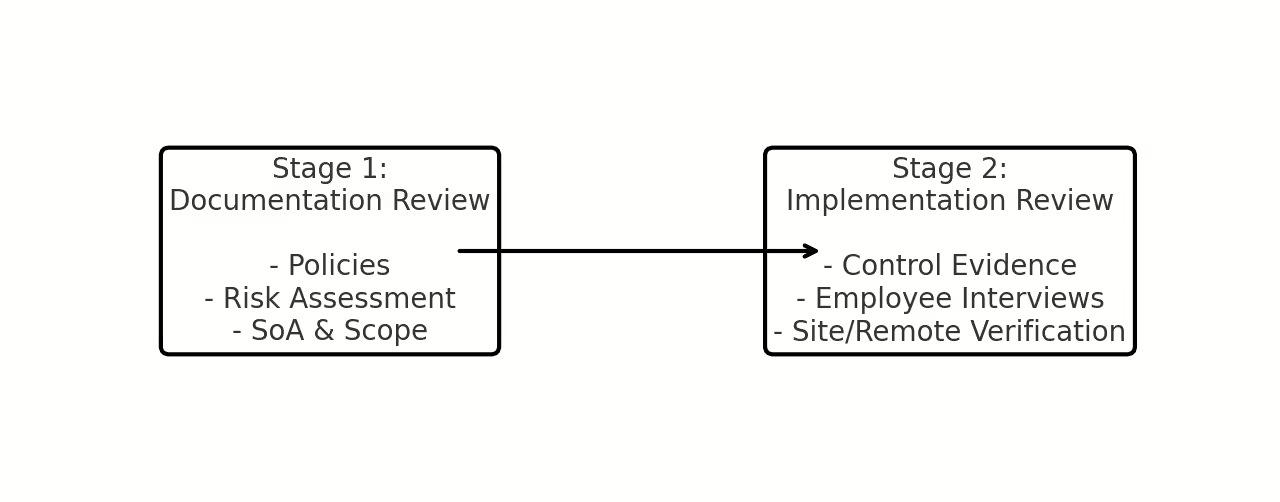
ISO 27001 Audit Process
This guide demystifies the certification audit journey, breaking it down into Stage 1: Documentation Review and Stage 2: Implementation Review. Learn what auditors examine at each stage—from ISMS policies and risk assessments in Stage 1 to real-world application checks like control sampling and employee interviews in Stage 2.
Data Security in Project Management
Early consideration of data security requirements for the product or service (e.g. at the planning and design stages), can lead to more effective and cost-efficient solutions for quality and data security.
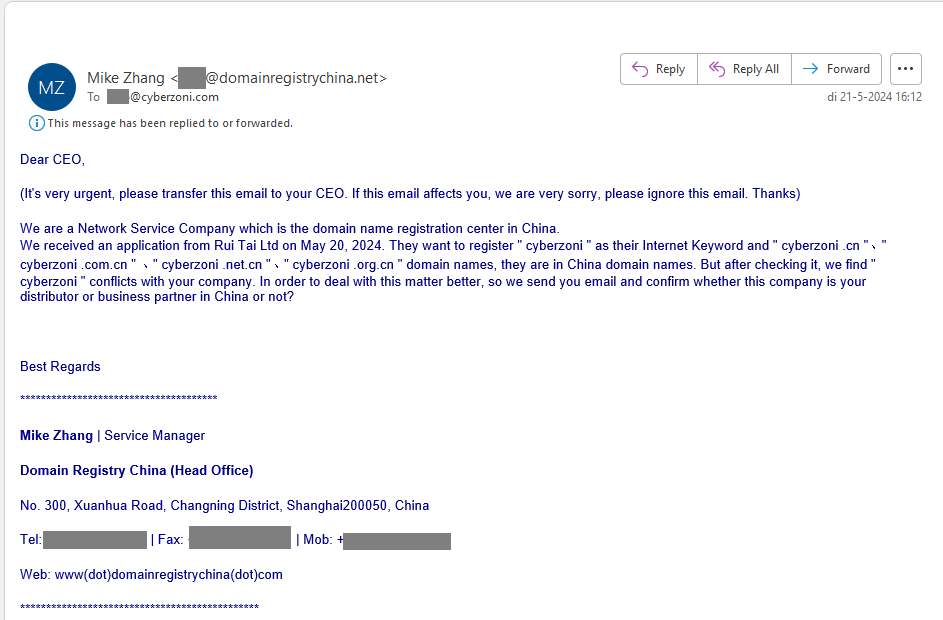
Chinese Domain Name Scams
Chinese domain name registration scam, we responded so you don’t have to.
This scam is designed to invoke panic and prompt hasty financial decisions.
Our investigation into these deceitful practices provides a detailed look at how such scams unfold and the tactics used to exploit unsuspecting businesses.

Cyber Security Advisor
Our advisors are skilled in evaluating security risks, devising strategies, and implementing effective security measures. They play a crucial role in developing security policies, training staff, and making sure your defenses and infrastructure are robust.
What is an ISMS
An Information Security Management System (ISMS) comprises a collection of policies and procedures designed to manage an organization’s sensitive data systematically. The primary objective of an ISMS is to reduce risk and maintain business continuity by proactively minimizing the effects of a security breach.

What is OT Cyber Security
OT Cyber security involves strategies and protections implemented to defend operational technology systems. These systems use specialized software to automate industrial processes and are susceptible to cyber security risks. The integration of information technology and operational technology increases overall security measures.

What is CyberSecurity?
Gain an understanding of cyber security, focusing on the techniques and strategies essential for protecting networks, devices, and data from cyber attacks. This article provides a detailed introduction to the threats that businesses and individuals face.
What is ISO 27001
Learn about ISO 27001 and its importance in establishing a secure information security management system. This overview explains the standard’s requirements and how it helps organizations protect critical information assets.

vCISO Meaning and why you absolutely need 1
The article on Cyberzoni about vCISO (Virtual Chief Information Security Officer) emphasizes its importance for businesses facing data breaches and cyber threats. It explains how a vCISO provides expert cybersecurity advice and strategic oversight without the costs and commitments of a full-time executive.
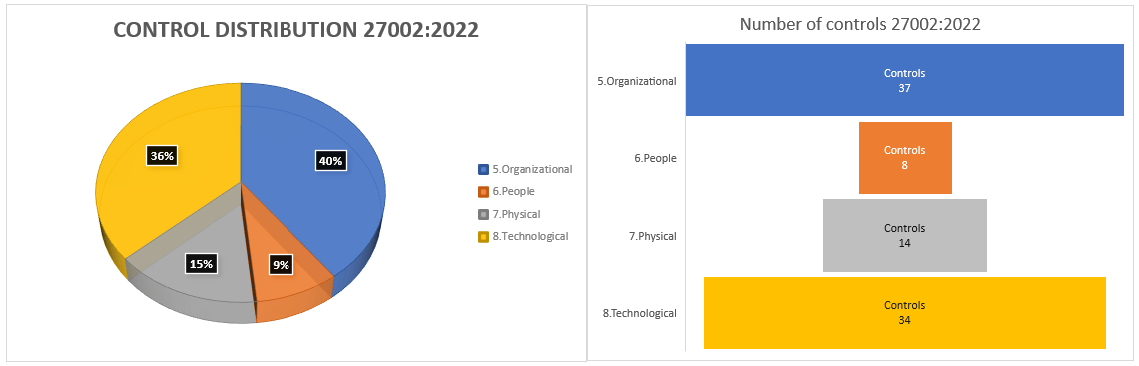
Annex A Document: ISO 27002 Expert Implementation Guide
ISO-27001 stands as a beacon of trust and reliability. With Cyberzoni’s guide, you’re not just getting a document; you’re getting a partner in your journey towards impeccable information security.

Baseline Assessment in Cybersecurity
A baseline assessment is an evaluation of a organization’s current cybersecurity posture. It’s like a health check-up but for your company’s digital defenses. By understanding where you currently stand, you can identify gaps, weaknesses, and areas of strength.

SMB in Cyber Security
SMBs are prime targets for sophisticated cyber threats. Consequently, it becomes essential for SMBs to prioritize cybersecurity and shield their digital assets from potential threats.
ISMS Meaning and Its Role in Modern Cybersecurity
ISMS stands for Information Security Management System, a strategic framework designed to manage, monitor, and mitigate risks associated with data security.