What is ISMS? Understanding ISMS Meaning and ISO 27001 Framework
In this Article
ISMS Meaning and Its Role in Modern Cybersecurity
Securing invaluable information is a prime goal for any organization, regardless of the industry. In an era where businesses heavily rely on information systems to streamline operations and make informed decisions, understanding the ISMS meaning becomes crucial. ISMS stands for Information Security Management System, a strategic framework designed to manage, monitor, and mitigate risks associated with data security. The reliance on these systems brings inherent risks such as data breaches and confidentiality loss. This is where an Information Security Management System (ISMS) emerges as a strategic investment to reinforce your organization’s cybersecurity.
What is an ISMS?
An Information Security Management System (ISMS) is a systematic approach designed to manage sensitive information and keep it secure. ISMS is built on a framework of policies, procedures, and processes that collectively help an organization defend against threats and vulnerabilities. Its primary goals are to maintain the confidentiality, integrity, and availability of data—three cornerstones of cybersecurity.
Key Components of an ISMS
An effective ISMS consists of multiple elements that work together to secure information assets. Key components include:
- Risk Assessment: Identifying, evaluating, and managing risks to prioritize security actions.
- Incident Management: Preparing for, responding to, and recovering from security incidents.
- Continuous Improvement: Regular updates and assessments to address new threats and improve system effectiveness.
The Importance of ISMS in Cybersecurity
With cyber threats on the rise, the ISMS framework ensures that businesses can defend against digital attacks while staying compliant with regulatory standards. Implementing an ISMS isn’t just about meeting requirements; it’s a strategic approach to building a security-first culture and protecting the trust of clients and partners.
An ISMS also helps organizations manage and minimize risks in a structured, predictable way. By defining processes and responsibilities, an ISMS makes sure everyone in the organization knows their role in maintaining security.
Benefits of ISMS Implementation
Establishing an ISMS can offer several key benefits:
- Enhanced Data Protection: Centralized security policies safeguard sensitive information.
- Regulatory Compliance: Many industries have stringent regulations for data security, which an ISMS can help meet.
- Increased Client Confidence: A well-managed ISMS demonstrates a commitment to protecting client data.
- Structured Risk Management: An ISMS provides a consistent framework for identifying and managing risks.
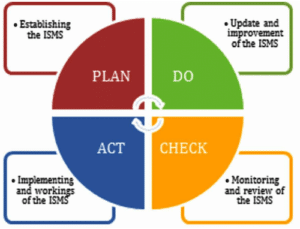
Incorporating the PDCA Approach in ISMS
ISMS effectively adopts the Plan-Do-Check-Act (PDCA) cycle, a continuous improvement framework, to ensure its efficacy.
Plan: Define your security objectives, identify potential threats and vulnerabilities, and establish a robust policy and a set of controls to address the risks.
Do: Implement the policies and controls outlined in the planning stage.
Check: Monitor and review the effectiveness of the ISMS and its controls, and report the results to management for review.
Act: Take corrective and preventive actions based on the results of the review, and make improvements to the ISMS where necessary.
This continuous loop allows your organization to adapt to evolving threats and changes in your business environment, ensuring ongoing improvement and resilience.
What is the goal of information security management system ISMS
Understanding “What is the Goal of Information Security Management System ISMS?” involves recognizing its fundamental purpose: to safeguard an organization’s sensitive information. This system, policies, procedures, and technological measures, is designed to protect data from threats like cyber-attacks, data breaches, and internal vulnerabilities.
By implementing ISMS, organizations aim to minimize risk and ensure business continuity by proactively identifying and mitigating potential security risks.
The Business Benefits of ISMS
- Risk Management: ISMS helps organizations understand and manage their information risks, implement controls to mitigate these risks, and ensure the organization can continue to operate even if a security incident occurs.
- Regulatory Compliance: An ISMS that is compliant with international standards like ISO 27001 helps ensure that your organization is following best practices for information security, and meeting legal, contractual, and regulatory requirements.
- Improved Customer Confidence: With data breaches increasingly hitting the headlines, businesses that can demonstrate they have robust security measures in place can gain a significant advantage in the eyes of customers and partners.
- Operational Efficiency: By providing a structured framework for managing information risks, an ISMS can help reduce duplication of effort and ensure that security resources are used efficiently.
- Incident Management: Having an ISMS in place can also help your organization respond effectively to the inevitable security incidents, reducing their impact and preventing them from reoccurring.
Do I need an ISMS
Adopting an ISMS brings advantages such as stronger cybersecurity, greater efficiency, regulatory compliance, and increased customer trust. Understanding the ISMS meaning — Information Security Management System — reveals why investing in an ISMS isn’t just an expenditure, but a strategic move towards continuous business growth. For ISMS implementation guidance or cybersecurity-related queries, our specialist team is always available to help.
If you’re contemplating enhancing your organization’s cybersecurity with an ISMS, or have any queries, our team is ready to assist. Feel free to reach out for additional information, pricing details, or to schedule a consultation with one of our specialists.
How to Implement an ISMS in Your Organization
Implementing an ISMS can seem daunting, but following a step-by-step approach can simplify the process.
-
Assess Current Security Posture: Start with a comprehensive review of your existing security measures. Identify any vulnerabilities, sensitive data assets, and areas needing enhanced protection.
-
Define Scope and Objectives: Determine which aspects of your business the ISMS will cover. This scope helps set achievable security objectives and prioritizes resources.
-
Develop Policies and Procedures: Draft clear policies that detail how your organization manages and mitigates risks. Policies should include access control, data handling, and incident response protocols.
-
Train Employees: Security is a shared responsibility, so training is essential. Regular training sessions help ensure all employees understand and follow ISMS protocols.
-
Continuous Monitoring and Improvement: A successful ISMS adapts to the evolving industry. Perform regular evaluations and update policies as needed to address new security challenges.
Real-World Applications of ISMS
Many organizations, especially in finance, healthcare, and government sectors, rely on ISMS to protect critical data and ensure compliance with legal requirements. For example, banks use ISMS to secure client data and transaction details, while healthcare providers safeguard patient records and comply with healthcare data protection laws.
Adopting an ISMS isn’t limited to large corporations. Small and medium-sized businesses increasingly see the value of ISMS in building a culture of security that scales with business growth.
Challenges in ISMS Implementation
While the benefits of ISMS are clear, implementing one can present challenges. Here are some common hurdles:
- Resource Constraints: Establishing an ISMS can be resource-intensive, requiring dedicated personnel, time, and budget.
- Complex Documentation: ISMS implementation involves creating and maintaining extensive documentation, which can be time-consuming.
- Employee Buy-In: Changing processes and implementing security measures may meet resistance from staff who need to adapt to new protocols.
To overcome these challenges, organizations can begin with a limited ISMS scope, gradually expanding as they gain experience and resources. Regular communication about the ISMS’s value can also increase employee engagement.
Future of ISMS in Cybersecurity
The role of an ISMS in cybersecurity will likely expand. New technologies, such as artificial intelligence and machine learning, offer exciting opportunities to improve ISMS effectiveness through predictive analysis and real-time threat detection. Additionally, the rise of remote work means that organizations must adapt their ISMS strategies to address the unique challenges of decentralized networks.
For companies looking to stay ahead in cybersecurity, an agile, well-implemented ISMS will be essential. By focusing on continuous improvement and staying informed of industry trends, organizations can assure their ISMS remains relevant in the face of cybersecurity challenges.
FAQ
Where does ISMS stand for?
ISMS stands for Information Security Management System. It refers to a framework of policies and procedures that includes all legal, physical, and technical controls involved in an organization’s information risk management processes.
How does an ISMS Protect Company Data?
An ISMS protects a company’s data by systematically managing risks to the security of its information. It involves identifying potential risks and implementing specific security measures to mitigate them, thereby ensuring the safety and integrity of the data.
What are the Key Components of an ISMS?
The key components of an ISMS include risk assessment and management procedures, security policies, physical and technical controls, incident management protocols, and continuous improvement processes to adapt to the changing cybersecurity field.
Is ISMS Certification Important for Businesses?
Yes, ISMS certification, such as ISO 27001, is important as it demonstrates a business’s commitment to maintaining high standards of information security, enhancing trust with clients and stakeholders, and ensuring compliance with regulatory requirements.
Can Small Businesses Benefit from Implementing an ISMS?
Absolutely, small businesses can significantly benefit from implementing an ISMS. It helps in protecting sensitive data, building customer trust, and providing a structured approach to managing information security risks, which is vital regardless of business size.