A Complete Guide to ISO 27001 Controls
In simple terms, ISO 27001 controls are the set of security measures and activities that your organization implements to protect its information and manage the associated risks. These controls are meant to address the vulnerabilities and threats identified during the risk assessment process, ensuring that your organization's information security practices meet the required standards and regulations.
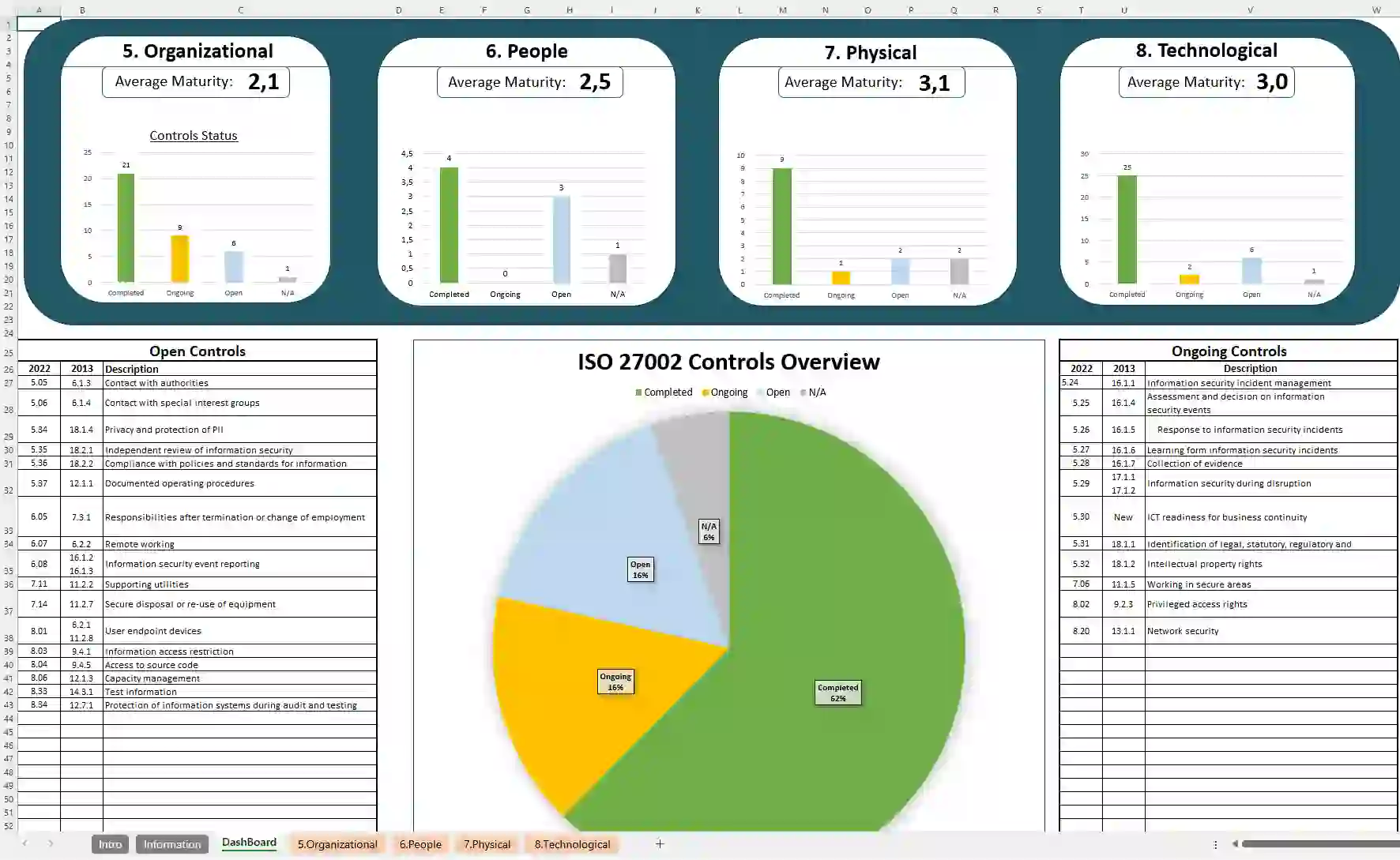
5. Organizational Controls(37)
Controls establish the framework, leadership, and operating procedures necessary to oversee information security across the organization.
6. People Controls(8)
Focusing on the human aspect of security, these controls guide staff training, awareness programs, and role-based responsibilities.
7. Physical Controls(14)
Designed to safeguard physical environments, these controls protect buildings, hardware, and other tangible assets.
8. Technological Controls(34)
These controls leverage technical measures such as access restrictions, encryption, and monitoring systems to defend information assets.
What are the ISO 27001 Controls
ISO 27001 controls are a fundamental part of the ISO 27001 standard, which outlines requirements for creating, implementing, maintaining, and continually improving an Information Security Management System (ISMS). These controls are designed to help organizations safeguard their information assets and manage security risks systematically. Essentially, ISO 27001 controls are actions, policies, and measures that your organization adopts to protect data and ensure the confidentiality, integrity, and availability of your systems and information.
What is the main purpose of ISO 27001 Annex A controls?
The primary purpose of ISO 27001 controls is to provide a structured approach to managing information security risks. These controls ensure your organization has adequate safeguards in place to prevent unauthorized access, minimize security threats, and ensure compliance with relevant regulations. They address potential vulnerabilities in the system, ranging from administrative processes to technical protections.
How many ISO 27001 Controls are there
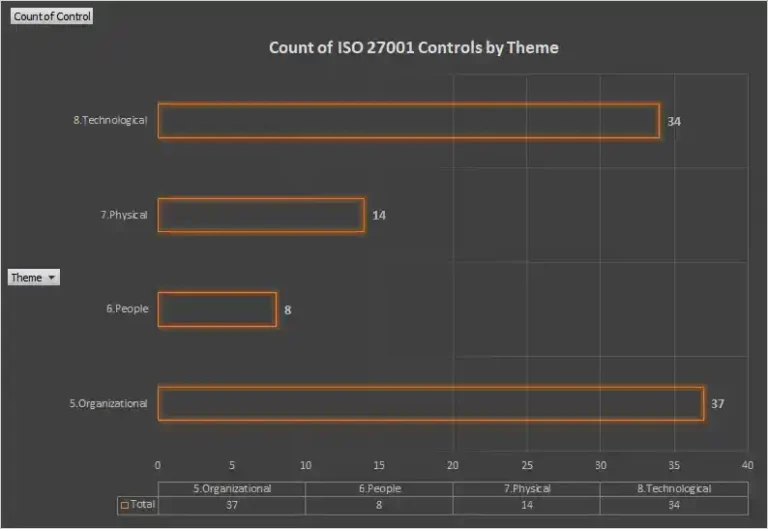
In total, ISO 27001:2022 contains 93 individual controls. These controls are grouped into 4 Themes (Main Clauses), each addressing a specific aspect of information security. The themes cover everything from high-level management practices to technical security measures and personnel responsibilities.
The controls in Annex A are structured into four themes:
- Organizational Controls (37): Focused on policies, procedures, and management activities.
- People Controls (8): Targeting the human factor—staff training, roles, and responsibilities.
- Physical Controls (14): Protecting physical assets, facilities, and hardware.
- Technological Controls (34): Addressing technical security measures like encryption, network security, and malware protection.
Breakdown of ISO 27001 Controls
Clause/Theme 5: Organizational Controls
This theme focuses on the management and governance of information security at an organizational level. The controls address roles, responsibilities, policies, governance structures, and procedures to ensure that information security is managed effectively across the organization. Areas covered:
- Governance and Accountability: Establishing a governance structure for information security.
- Information Security Policy: Developing and maintaining an information security policy.
- Information Security Roles and Responsibilities: Defining roles and responsibilities related to information security.
- Risk Management and Treatment: Ensuring systematic identification, assessment, and treatment of information security risks.
- Supplier Relationships and Third-Party Security: Addressing security within third-party agreements and managing supplier-related risks.
Some example controls in this theme:
- A.5.2: Information security roles and responsibilities.
- A.5.23: Manage information security for cloud services
- A.5.31: Identification of legal, statutory, regulatory and contractual requirements
Clause/Theme 6: People Controls
The People Controls theme centers on the human element of information security, addressing the role that employees, contractors, and other stakeholders play in securing your organization’s information assets. Main areas covered:
- Human Resource Security: Addressing information security during recruitment, employment, and after employment.
- Security Awareness and Training: Ensuring staff members are educated and trained on security risks and responsibilities.
- Disciplinary Processes: Establishing a disciplinary framework for handling information security breaches or non-compliance.
Some example controls in this theme:
- A.6.1: Screening and vetting of staff.
- A.6.3: Information security training and awareness programs.
- A.6.6: Confidentiality agreements and obligations.
Clause/Theme 7: Physical Controls
This theme deals with the physical aspects of security, such as protecting organizational premises, physical assets, and infrastructure from unauthorized access or damage. Key areas covered:
- Physical Security perimeters: Defining secure areas within the organization’s physical environment.
- Access Control to Facilities: Limiting physical access to sensitive areas, especially those where critical infrastructure and information are stored.
- Environmental Security: Addressing protection from environmental threats like fire, floods, and power failures.
Some example controls in this theme:
Clause/Theme 8: Technological Controls
The Technological Controls theme focuses on the protection of digital systems, networks, and data through technical measures such as encryption, monitoring, and access management. Key areas covered:
- Access Control and Authentication: Ensuring that only authorized users can access systems, networks, and data.
- Cryptography and Data Protection: Using encryption and other techniques to protect the confidentiality and integrity of information.
- Network and System Security: Protecting systems, networks, and communications from unauthorized access and attacks.
- Incident Management: Responding to and recovering from security incidents that threaten the organization’s information systems.
Some example controls in this theme:
How to Select and Apply ISO 27001 Controls
ISO 27001 provides a set of controls to help organizations protect their information assets. However, not every control will be relevant to every organization. The process of selecting the right controls depends on your organization’s risk profile, the specific threats you face, and the operational requirements of your business.
We’ll walk you through the process of selecting and implementing the right ISO 27001 controls for your organization. We’ll also explain the role of the Statement of Applicability (SoA) in this process, and explore the specific requirements outlined in Clause 6.1.3(d) for creating the SoA.
Step 1: Conduct a Risk Assessment
Before selecting ISO 27001 controls, it’s important to identify the risks that your organization faces. A risk assessment acts as the foundation for recognizing threats, vulnerabilities, and their potential impact. During the assessment, you will evaluate the likelihood and consequences of various security threats and their potential effect on your organization’s operations, assets, and reputation.
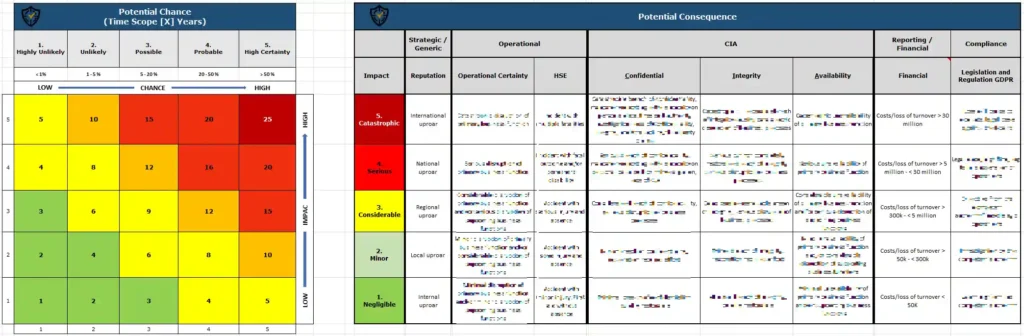
The findings from the risk assessment will guide the selection of relevant controls. For example, if your organization handles highly sensitive customer data, you may need to prioritize controls related to access management, data encryption, and employee training to address these specific risks. For conducting a risk assessment, you can use our ISO 27001 Risk Assessment Template.
Step 2: Review Annex A Controls
Once you understand the risks your organization faces, you can begin reviewing the ISO 27001 Annex A controls. Annex A contains a list of 93 controls, categorized under four main themes—Organizational, People, Physical, and Technological controls. You can also refer to our ISO 27002 2022 Controls Spreadsheet for an easy-to-use breakdown of these controls.
When selecting which controls to apply, consider the following:
- Choose controls that directly address the risks identified in your risk assessment.
- Ensure the controls align with your business goals, regulatory obligations, and contractual commitments.
- Evaluate any existing security measures in place and determine whether they are adequate or require improvement.
Step 3: Create the Statement of Applicability (SoA)
The Statement of Applicability (SoA) provides a list of all the controls from Annex A, indicating which are applicable and which are not. The SoA also serves to justify why certain controls were either selected or excluded based on your organization’s specific risks and needs.
Steps to Create the SoA:
- Document the controls: List all the controls from Annex A and indicate whether they are applicable to your organization.
- Justify inclusion or exclusion: For each control, explain why it is relevant or not, based on the findings from your risk assessment.
- Identify legal and regulatory requirements: Some controls may be mandatory due to external regulations, regardless of the risk assessment outcome.
- Review and update the SoA regularly: As your organization’s risks evolve, the SoA should be reviewed and updated to ensure the selected controls are still effective.
Clause 6.1.3(d) – The Creation of the Statement of Applicability
Clause 6.1.3(d) of ISO 27001 specifically addresses the development of the Statement of Applicability (SoA) within the context of the Risk Treatment Plan. The SoA functions as a transparent document that justifies control selection. You can use our ISO 27001 2022 SoA Template to help document your selected controls and exclusions.
Clause 6.1.3(d) requires that organizations:
- Create the SoA after the risk assessment: The SoA must reflect the risks identified and the relevant controls needed to manage those risks.
- Provide justification for each control: For each control, you must explain why it was either included or excluded, in line with your organization’s risk treatment plan.
- Review and update the SoA regularly: The SoA should be periodically updated to remain aligned with the current risk landscape and security needs.
Step 4: Implement the Selected Controls
After selecting the appropriate controls and documenting them in the SoA, the next step is to apply them throughout your organization. This process involves integrating necessary processes, tools, and resources to mitigate the identified risks.
The process of applying ISO 27001 controls includes:
Developing Policies and Procedures: Write clear security policies that reflect the selected controls, and ensure employees understand their roles in implementing them.
Allocating Resources: Ensure the necessary resources, such as personnel, technology, and budget, are available for effective control implementation.
Integrating Controls into Operations: Information security should be embedded into daily business activities, from IT system access control to employee training and physical security measures.
Training Employees: Provide ongoing training and awareness programs to ensure that all employees understand their responsibilities and know how to follow the implemented controls.
Monitoring and Measuring Effectiveness: Continuously assess the effectiveness of the controls through regular audits, security assessments, and incident reporting to ensure they’re functioning as intended.
Step 5: Document and Maintain Evidence
ISO 27001 requires organizations to maintain proper documentation and evidence of control implementation to demonstrate compliance. This documentation should include:
- The SoA, which details the controls that have been applied.
- Risk assessment reports, showing the rationale behind the selection of controls.
- Procedures, guidelines, and training materials supporting the controls.
- Incident logs, audit reports, and other records that demonstrate the effectiveness of the controls.
For an overview of the policies required for your ISMS, check out our full list of ISO 27001 Policy Templates.
What are the Controls in ISO 27001 designed to do?
The controls in ISO 27001 are designed to protect the confidentiality, integrity, and availability of an organization’s information. These three principles form the backbone of information security management and are critical in preventing unauthorized access, data breaches, and other security threats. Each control is suited to address specific risks and vulnerabilities within an organization’s information systems, supporting that information security is systematically managed.
ISO 27001 controls offer a structured approach to mitigating security risks by establishing a set of security measures that can be applied across different areas of the organization. Let’s dive into the main goals and purposes these controls are designed to achieve.
Protecting Confidentiality
Confidentiality is about ensuring that sensitive information is accessible only to those who are authorized to access it. ISO 27001 controls are designed to prevent unauthorized access, sharing, or disclosure of information.
- Access Control: One of the core functions of ISO 27001 controls is to manage who has access to what information. Controls related to user access management (like requiring strong authentication, assigning least privilege access, and implementing role-based access controls) help ensure that sensitive data is only accessible by authorized individuals.
- Encryption and Data Protection: Controls such as data encryption ensure that even if information is intercepted during transmission or at rest, it remains unreadable without the appropriate decryption key, safeguarding its confidentiality.
- Physical Security: Measures like secure areas and equipment protection ensure that physical access to critical systems and information is restricted to authorized personnel only, preventing unauthorized physical access to sensitive data.
Ensuring Integrity
Integrity refers to the accuracy, consistency, and trustworthiness of information over its lifecycle. ISO 27001 controls are aimed at preventing unauthorized modification, alteration, or corruption of data.
- Data Validation and Integrity Checks: Controls that require data validation help ensure that information is entered correctly and remains consistent over time. Audit logs and hashing techniques are commonly used to detect and correct unauthorized changes to data.
- Malware Protection: Implementing controls like anti-malware systems helps detect and prevent malicious software from compromising the integrity of information. If an attacker introduces malware to manipulate data, these controls ensure that threats are identified and mitigated promptly.
- Backup and Recovery: The integrity of data is also maintained through regular backups. Backup controls ensure that, in case of data corruption or loss, your organization can restore information from a known good state.
Ensuring Availability
Availability means that information is accessible and usable when needed by authorized users. ISO 27001 controls are designed to ensure that systems and data are consistently available for legitimate business needs, even in the face of unexpected events or disasters.
- Business Continuity: ISO 27001 controls related to business continuity help ensure that critical information systems remain operational in the event of disruptions. This includes regular testing and updating of disaster recovery and continuity plans to account for emerging risks and scenarios.
- Redundancy and Failover Systems: Implementing redundant systems (such as backup power supplies and data centers) ensures that if one part of the infrastructure fails, another can take its place, minimizing downtime and ensuring continued availability of critical data.
- Access Control in Systems: Controls ensuring that access is properly managed prevent unauthorized users from interfering with or shutting down systems, which could compromise availability.
The five Attributes Associated With ISO 27001 Controls
Controls are not a one-size-fits-all solution but can be viewed through various perspectives or attributes to help organizations better understand how to apply them effectively. The five key attributes associated with ISO 27001 controls include Control Type, Information Security Properties, Cybersecurity Concepts, Operational Capabilities, and Security Domains. Each attribute provides a unique lens through which to assess and apply the controls to address specific organizational needs and security objectives.
a) Control Type
Control Type is an attribute that allows organizations to view controls from the perspective of how and when the control addresses the occurrence of an incident. Essentially, it helps categorize controls based on their function in either preventing, detecting, or correcting incidents.
Preventive controls are designed to stop information security incidents before they happen. These controls aim to eliminate vulnerabilities or reduce the likelihood of an event that could compromise information security. For example, firewalls and access control policies prevent unauthorized access to systems.
Detective controls come into play when an incident occurs. Their primary function is to identify that a security incident has taken place. These controls do not prevent incidents but act as an early warning system. Examples include intrusion detection systems (IDS) or continuous monitoring tools that flag unusual behavior.
Corrective controls are applied after an incident has occurred. They aim to minimize the damage or restore systems to their original state. This includes measures like backup and recovery systems, incident response procedures, and data restoration protocols.
b) Information Security Properties
Information Security Properties refer to the core characteristics of information that the control aims to protect. The main attributes here are Confidentiality, Integrity, and Availability—commonly known as the CIA triad. These properties are fundamental to information security and define how controls are applied based on the nature of the information being protected.
Confidentiality ensures that information is only accessible to those who are authorized to view it. Controls that support confidentiality typically involve encryption, access controls, and secure storage systems.
Integrity guarantees that information remains accurate, complete, and trustworthy throughout its lifecycle. Integrity is often maintained through hashing, version control, and integrity checks, ensuring that data is not tampered with or altered without authorization.
Availability refers to ensuring that information and systems are accessible when needed. Availability controls include disaster recovery plans, redundancy in systems, and ensuring systems remain functional and accessible during critical times.
c) Cybersecurity Concepts
Cybersecurity Concepts offers a framework for understanding controls based on the cybersecurity lifecycle outlined in ISO/IEC TS 27110. These concepts are aligned with the traditional cybersecurity approach, which can be viewed in terms of the stages of threat and risk management. The five concepts in this attribute include Identify, Protect, Detect, Respond, and Recover.
Identify refers to understanding and managing the organization’s cybersecurity risk, including asset management and risk assessment.
Protect focuses on implementing safeguards to prevent cyberattacks and unauthorized access. This includes measures like firewalls, encryption, and access control systems.
Detect involves continuous monitoring and detection systems that help identify security breaches or vulnerabilities early. Examples include intrusion detection systems (IDS) and network monitoring tools.
Respond is concerned with how the organization reacts when an incident occurs, including incident response plans, communication, and coordination to contain and mitigate damage.
Recover focuses on restoring operations after a security incident and includes business continuity plans, disaster recovery, and data recovery processes.
d) Operational Capabilities
Operational Capabilities is an attribute that categorizes controls based on specific information security capabilities that organizations need to manage and protect their assets. These capabilities span a range of operational areas from governance to human resource security, and network protection.
Key operational capabilities include:
Governance: Establishing clear security governance frameworks to manage policies, responsibilities, and decision-making processes related to information security.
Asset Management: Ensuring that organizational assets, including hardware, software, and intellectual property, are properly protected and managed.
Information Protection: Safeguarding sensitive information through measures such as encryption, access controls, and secure storage.
Human Resource Security: Addressing security during recruitment, training, and termination processes to ensure staff members are aware of their security responsibilities.
Physical Security: Securing physical premises and equipment to prevent unauthorized access or damage.
System and Network Security: Implementing measures to protect systems and networks, such as firewalls, intrusion detection systems, and secure configuration.
Application Security: Ensuring the security of software and applications throughout their lifecycle, including secure coding practices, patch management, and vulnerability assessments.
Secure Configuration: Applying appropriate configuration standards and security settings to minimize vulnerabilities in systems and applications.
Identity and Access Management: Managing user identities, roles, and access permissions to ensure only authorized individuals have access to sensitive information.
Threat and Vulnerability Management: Identifying and mitigating threats and vulnerabilities to prevent potential security breaches.
Continuity: Ensuring the availability of critical systems and services in case of disruptions through business continuity planning and disaster recovery measures.
Supplier Relationships Security: Managing risks associated with third-party vendors and ensuring they adhere to security standards.
Legal and Compliance: Ensuring that all security practices align with legal and regulatory requirements.
Information Security Event Management: Detecting and responding to security events promptly to minimize their impact.
Information Security Assurance: Ensuring the overall effectiveness of the ISMS through regular audits, assessments, and reviews.
e) Security Domains
Security Domains represent different areas within the broader framework of information security, and controls are applied to these domains based on the specific security needs. The domains are divided into four categories: Governance and Ecosystem, Protection, Defence, and Resilience.
Governance and Ecosystem: This domain involves managing security governance, risk management, and ecosystem cybersecurity, including working with internal and external stakeholders.
Protection: Covers measures like IT security architecture, identity and access management, physical and environmental security, and secure systems administration.
Defence: Focuses on detection mechanisms (such as intrusion detection systems) and response capabilities to protect against ongoing cyber threats or incidents.
Resilience: Ensures business continuity and crisis management processes are in place to recover from security incidents and disasters.
Control layout
The control layout in ISO 27001 is structured to provide clear, consistent, and actionable information for each control. This layout helps organizations understand the control’s purpose, how to implement it. Each control in the ISO 27001 standard follows a specific format that ensures all necessary details are provided in an organized manner.
Here’s an overview of the components typically included in the control layout:
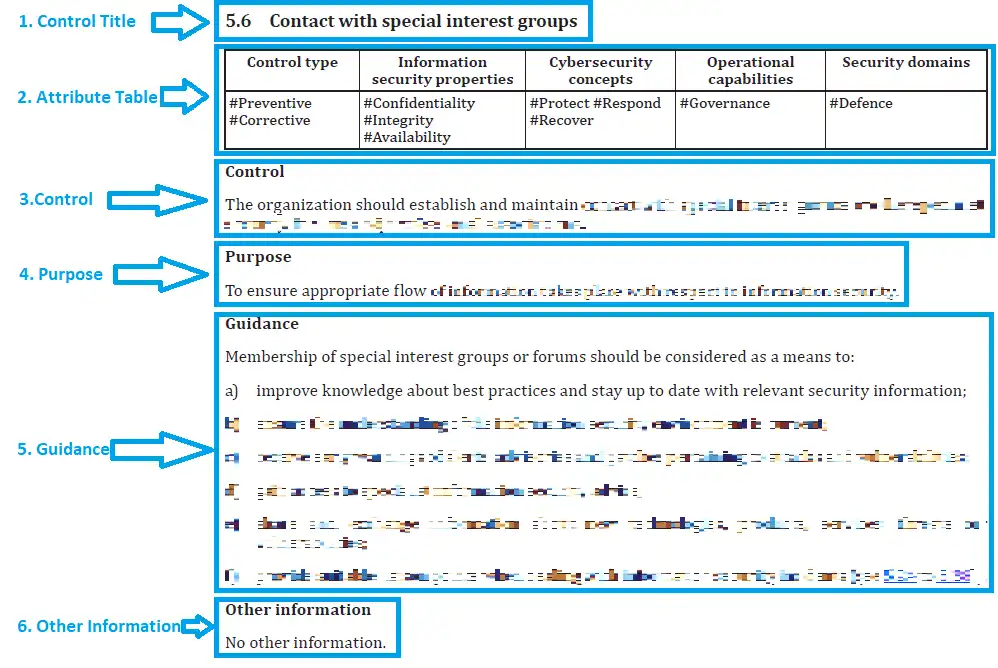
1. Control Title
Each control in ISO 27001 has a control title, which serves as a concise, descriptive name for the control. This title is usually short, making it easy for users to quickly identify the focus of the control. The title acts as a label that summarizes the purpose of the control, often reflecting the core function it addresses (e.g., “Access Control” or “Incident Response”).
2. Attribute Table
The attribute table provides a detailed view of the control’s characteristics, including its value(s) for each of the attributes assigned to it. The table typically includes the following attributes:
- Control Type: Indicates whether the control is Preventive, Detective, or Corrective.
- Information Security Properties: Specifies whether the control contributes to Confidentiality, Integrity, and/or Availability.
- Cybersecurity Concepts: Identifies how the control aligns with cybersecurity lifecycle stages such as Identify, Protect, Detect, Respond, and Recover.
- Operational Capabilities: Lists the relevant operational capabilities that the control addresses, such as Governance, Asset Management, or Information Protection.
- Security Domains: Specifies which security domain the control belongs to (e.g., Governance and Ecosystem, Protection, Defence, or Resilience).
This table provides a quick, structured reference for understanding how the control fits within the broader security framework.
3. Control
The control section describes what the control is and its core functionality. This section explains the specific action or measure that is implemented to mitigate a particular risk. The description is typically brief but clear, detailing the required security measure. For example, a control might involve implementing two-factor authentication to prevent unauthorized access or setting up firewalls to protect the network perimeter.
4. Purpose
The purpose section provides the rationale for implementing the control. It explains why the control is necessary and how it contributes to the overall information security objectives. This section helps organizations understand the importance of the control in mitigating security risks. For example, the purpose of an access control policy might be to ensure that only authorized individuals can access sensitive information, thereby reducing the risk of data breaches.
5. Guidance
The guidance section outlines how the control should be implemented. This part provides practical advice and recommendations on applying the control within the organization. The guidance can include step-by-step instructions, technical specifications, or procedural recommendations, depending on the control’s nature.
If the guidance is extensive or addresses multiple topics, subheadings are used to break the text into more manageable sections. These subheadings help readers navigate through the content, making it easier to find specific information.
Examples of guidance might include:
- How to configure systems or devices to comply with a specific control.
- Best practices for implementing policies and procedures.
- Steps for testing and validating the effectiveness of a control.
Not all controls require lengthy guidance. Some controls are straightforward and may only need a brief explanation of their implementation.
6. Other Information
The other information section provides any additional details or references that can support the control’s implementation. This might include:
- Explanatory text: Additional context to clarify complex concepts or considerations.
- References to related documents: Links or references to other relevant ISO standards, guidelines, or internal documents that provide further insight or detail. For example, a control related to encryption might refer to specific cryptographic standards or government regulations.
This section is especially useful for providing more detailed explanations or offering insight into related compliance or regulatory requirements.
Control Layout in Action
By maintaining a consistent control layout, ISO 27001 ensures that each control is clearly defined and easy to understand. The structured layout allows organizations to quickly identify key details, making it easier to implement and manage their ISMS.
For instance, an Access Control control might look like this:
- Control Title: Access Control
- Attribute Table:
- Control Type: Preventive
- Information Security Properties: Confidentiality, Integrity
- Cybersecurity Concepts: Protect
- Operational Capabilities: Identity and Access Management
- Security Domains: Protection
- Control: Implement user authentication measures to restrict access to sensitive information.
- Purpose: To ensure that only authorized individuals can access sensitive information, thus preventing unauthorized access and protecting data privacy.
- Guidance:
- Implement multi-factor authentication for all systems storing sensitive data.
- Regularly review and update user access rights based on job roles.
- Other Information: Refer to organizational policy on Access Control for additional guidance. See ISO 27002 for specific technical configurations.
This layout helps maintain clarity and consistency in the application of ISO 27001 controls across an organization.
Best Practices for Implementating ISO 27001 Controls
While the framework provides clear guidelines, successful implementation requires careful planning, coordination, and ongoing effort. We’ll explore how to implement ISO 27001 controls effectively, common mistakes to avoid, how to integrate controls into daily operations.
How to Implement ISO 27001 Controls Effectively
The successful implementation of ISO 27001 controls involves a series of steps that ensure the controls are applied appropriately and align with the organization’s security goals. Follow these best practices to implement controls effectively:
Conduct a Thorough Risk Assessment: The first step in applying ISO 27001 controls is conducting a detailed risk assessment. This assessment will help identify the potential threats, vulnerabilities, and risks your organization faces. The results of the risk assessment will guide the selection and implementation of controls, ensuring that they address your organization’s unique security needs.
Develop a Detailed Implementation Plan: Once the controls are selected, it’s essential to create an implementation plan. This plan should outline:
- The specific controls to be implemented.
- The roles and responsibilities of individuals involved in the implementation process.
- A timeline for implementing each control.
- Resources needed, such as personnel, tools, and budget.
- The steps to monitor and evaluate the effectiveness of the controls.
Engage Stakeholders: Ensure that key stakeholders across the organization are involved in the implementation process. This includes top management, IT teams, human resources, legal departments, and other relevant personnel. Engaging stakeholders early on ensures that controls are properly understood and supported, and that they align with broader organizational goals.
Provide Training and Awareness: Employee awareness and training are critical to the successful implementation of ISO 27001 controls. All employees should be educated about the importance of information security, their roles in maintaining it, and the specific controls that apply to them. Regular training sessions, along with clear documentation, will help employees understand the controls and follow best practices for their implementation.
Monitor and Review Progress: As you implement the controls, continuously monitor progress and gather feedback. Regular audits and assessments will help you identify any gaps or weaknesses in the controls, ensuring that they are functioning as intended. Schedule periodic reviews to assess whether the controls are still effective and relevant to the evolving security landscape.
Common Mistakes When Applying Controls
While ISO 27001 provides a structured approach to information security, there are common mistakes organizations can make when implementing controls. Avoid these pitfalls for a smoother and more effective implementation:
Lack of a Clear Risk Assessment: One of the most common mistakes is not conducting a comprehensive risk assessment. Without a clear understanding of the specific risks your organization faces, it’s difficult to select the right controls. Ensure the risk assessment is thorough, regularly updated, and aligned with organizational priorities.
Overlooking Stakeholder Engagement: Failing to involve key stakeholders in the process can lead to poor implementation and lack of buy-in. Ensure that management, staff, and departments across the organization understand the importance of the controls and are actively engaged in the implementation process.
Ineffective Communication: Miscommunication or lack of communication regarding the controls can create confusion and lead to inconsistent application. It’s important to have clear, open lines of communication, especially when it comes to roles, responsibilities, and expectations for implementing controls.
Inadequate Training and Awareness: Controls are only effective if employees understand them and apply them correctly. Insufficient training can lead to security gaps. Make sure everyone in the organization receives regular training and has access to resources that help them follow security best practices.
Failure to Monitor and Adapt: ISO 27001 controls should not be seen as a one-time task but as part of an ongoing process. Failing to regularly monitor and review the effectiveness of controls can result in vulnerabilities. Continuous improvement is at the heart of ISO 27001, so ongoing monitoring and feedback are crucial.
Integrating Controls into Daily Business Operations
To confirm that ISO 27001 controls are effective, they must be integrated into your organization’s daily operations. Best practices for embedding controls into your routine workflows:
Embed Security into Business Processes: Information security should be part of the fabric of your organization’s business operations. This means incorporating security measures into every part of the business process, from HR policies and physical security measures to IT systems and data handling. For example, access control measures should be embedded into the organization’s IT infrastructure and business systems to limit unauthorized access from day one.
Align Controls with Existing Policies and Procedures: ISO 27001 controls should not operate in isolation. They must align with your organization’s existing policies and procedures. For example, your information security policy should be closely aligned with HR policies, data protection procedures, and risk management frameworks. Ensuring this alignment will help streamline the implementation and ongoing management of controls.
Automate Where Possible: Many ISO 27001 controls, particularly in the areas of monitoring, incident detection, and access management, can be automated to reduce human error and improve efficiency. Automation can help monitor user activity, flag unusual behavior, and even enforce security policies like password complexity or multi-factor authentication.
Make Information Security Part of the Organizational Culture: Information security should be ingrained into the culture of your organization. This means leadership must demonstrate a commitment to security, and employees must be motivated to follow security procedures. Encourage a security-first mindset by integrating security into employee performance reviews, recognition programs, and team goals.
Tools and Technologies to Support Control Implementation
There are many tools and technologies available that can help your organization implement and manage ISO 27001 controls more effectively. Some tools include:
Governance, Risk, and Compliance (GRC) Tools: GRC platforms can help organizations manage risk assessments, track control implementation, and ensure compliance with security standards like ISO 27001. These tools provide centralized dashboards, documentation management, and reporting capabilities to streamline compliance efforts.
Security Information and Event Management (SIEM) Systems: SIEM systems help monitor, detect, and respond to security incidents by collecting and analyzing security event data. These tools can assist in detecting anomalies and breaches in real-time, supporting detective controls.
Identity and Access Management (IAM) Solutions: IAM solutions help organizations enforce access controls, ensuring that only authorized individuals can access sensitive data. These solutions can help with user authentication, role-based access control, and audit logging.
Data Loss Prevention (DLP) Software: DLP tools help prevent data breaches by monitoring and controlling the movement of sensitive data across systems, networks, and endpoints. These tools can block unauthorized sharing of data, enforce encryption, and generate alerts when risky behaviors are detected.
Backup and Recovery Solutions: Effective backup and disaster recovery solutions are essential for implementing corrective controls. These tools ensure that critical business data is regularly backed up and can be recovered quickly in the event of a breach or disaster.
Security Awareness Training Platforms: Security training platforms can help provide regular, engaging training sessions for employees, ensuring they are aware of security policies, best practices, and the role they play in maintaining a secure environment.
Tools and Templates for Implementing ISO 27001 Controls
Implementing ISO 27001 controls can be a complex and time-consuming task, but there are various tools and templates available that can help streamline the process, ensure compliance, and improve the overall effectiveness of your ISMS. These tools and templates can assist in everything from risk assessments and control selection to documentation and monitoring.
1. GAP Analysis Template
An ISO 27001 GAP Analysis Template is used to identify the differences between the current state of your information security practices and the desired state defined by ISO 27001. This template helps you assess where your organization is in relation to compliance with the standard and where improvements are needed.
The GAP analysis process typically includes:
- Current State Assessment: A review of your existing information security policies, processes, and controls to assess their effectiveness.
- Desired State Definition: A description of the security requirements outlined by ISO 27001 and the specific controls that need to be implemented.
- GAP Identification: Identifying the gaps between the current state and the desired state, which may include missing controls, incomplete processes, or non-compliance with ISO 27001 standards.
- Action Plan: Developing an action plan to close these gaps, including the implementation of new controls, policies, and procedures, along with timelines and responsible parties.
2. ISO 27001 Risk Assessment Template
A risk assessment template is an essential tool for identifying, evaluating, and managing the risks your organization faces. The risk assessment is the first step in the risk treatment process, and it lays the foundation for selecting the appropriate controls. A well-structured template helps ensure that all necessary risks are identified and assessed consistently.
Key benefits of using a risk assessment template include:
- Standardization: Ensures a consistent approach to identifying and evaluating risks across the organization.
- Efficiency: Saves time by providing predefined sections for documenting risk scenarios, likelihood, impact, and control effectiveness.
- Clear Documentation: Helps create clear records of the risk assessment process, which is necessary for auditing and compliance purposes.
3. ISO 27002 2022 Controls Spreadsheet
The ISO 27002 2022 Controls Spreadsheet is a valuable resource for organizations implementing ISO 27001 controls. This spreadsheet contains all the controls listed in ISO 27002:2022, the companion standard to ISO 27001 that provides guidance on the implementation of information security controls.
This tool is useful for:
- Control Mapping: Helping you map each control from ISO 27002 to your organization’s specific risk profile.
- Tracking Implementation: Assisting in tracking the status of each control’s implementation, from planning to completion.
- Customization: Allowing for easy customization of the controls to fit the specific needs of your organization.
With the controls spreadsheet, you can quickly identify which controls are relevant to your organization, track their progress, and ensure all necessary actions are taken to meet ISO 27001 requirements.
4. Statement of Applicability (SoA) Template
The Statement of Applicability (SoA) is one of the most important documents in the ISO 27001 implementation process. It provides a list of all the controls from Annex A of ISO 27001, indicating which are applicable to your organization and justifying their inclusion or exclusion based on your risk assessment.
Using an SoA template helps streamline the creation of this essential document. The template typically includes:
- A table of Annex A controls with space to mark whether each control is applicable.
- Rationale for exclusions: An area for justifying why certain controls were excluded from the ISMS, based on the organization’s risk profile.
- Reference to related policies: A section for referencing existing policies or documents that are aligned with the controls.
5. ISO 27001 Policy Templates
ISO 27001 requires the implementation of various security policies that align with the standard’s controls. Having ISO 27001 policy templates on hand can simplify the process of creating these documents. The templates are designed to help you create comprehensive and compliant policies that address the necessary aspects of information security.
Common ISO 27001 policy templates include:
- Information Security Policy: Outlines the organization’s commitment to protecting information and defines the scope and objectives of the ISMS.
- Access Control Policy: Details the rules and guidelines for granting and managing access to information systems.
- Incident Response Policy: Describes the procedures to follow when a security incident occurs, including detection, reporting, response, and recovery.
- Data Protection Policy: Ensures that sensitive data is handled in compliance with data protection regulations (e.g., GDPR).
6. Control Implementation and Monitoring Tools
In addition to templates, several tools can help monitor and manage the implementation of ISO 27001 controls:
Governance, Risk, and Compliance (GRC) Tools: GRC tools allow you to track the implementation of controls, manage risks, and ensure compliance with ISO 27001. They provide a central repository for all risk assessments, control documentation, and audit results, making it easier to manage your ISMS.
Security Information and Event Management (SIEM) Systems: SIEM systems help monitor security events and incidents in real time. They provide alerts for unusual activity and can automatically correlate events to help identify potential threats.
Identity and Access Management (IAM) Solutions: IAM tools can help enforce access control policies, manage user permissions, and track access events, ensuring that only authorized individuals have access to sensitive information.
Malware Protection Tools: Anti-malware software helps to protect against malicious threats, ensuring that controls aimed at detecting and preventing malware are functioning effectively.
Audit and Monitoring Software: These tools assist in regularly reviewing the effectiveness of controls, performing audits, and ensuring that security measures are continuously maintained.
7. Incident Management and Response Templates
Having incident management templates can be extremely helpful when addressing security incidents. These templates can assist in documenting and managing incidents, ensuring that your response is organized and in line with ISO 27001 requirements. Templates typically include sections for:
- Incident detection and reporting
- Investigation and analysis
- Corrective actions and root cause analysis
- Communication plans for informing relevant stakeholders
- Post-incident reviews
8. Internal Audit Template
An ISO 27001 Internal Audit Template is a checklist for ensuring that ISO 27001 controls are functioning correctly and that your organization remains in compliance with the standard. The internal audit process is essential for evaluating the effectiveness of your ISMS and identifying areas for improvement.
An internal audit check typically includes the following sections:
- Audit Scope: Defines the scope of the audit, including which controls, processes, or departments will be reviewed.
- Audit Checklist: A detailed list of questions or criteria to evaluate the compliance and effectiveness of ISO 27001 controls.
- Findings and Non-Conformities: A section to document any findings, discrepancies, or non-conformities identified during the audit.
- Recommendations for Improvement: Suggestions for corrective actions or improvements to address any issues uncovered during the audit.
- Follow-Up: A process for tracking the implementation of corrective actions based on audit findings.
FAQ
What are ISO 27001 controls?
ISO 27001 controls are a set of best-practice security measures outlined in Annex A of the ISO/IEC 27001 standard. They are designed to protect an organization’s information assets from a wide range of risks. Each control addresses a specific aspect of information security, such as access management, physical security, and incident response.
How many controls are there in ISO 27001?
In the 2022 revision of ISO/IEC 27001, there are 93 controls (reduced from the 114 in the older 2013 version). These controls are reorganized into four main themes (people, organizational, technological, and physical) for better clarity and alignment with modern security practices.
Are ISO 27001 Annex A controls mandatory?
Not all controls are automatically mandatory. Organizations must conduct a risk assessment to identify which controls are relevant to their specific risks and objectives. The chosen controls should be documented in a Statement of Applicability (SoA), explaining which controls are applied, which are excluded, and why.
How do I choose which ISO 27001 controls to implement?
The selection of controls is driven by your risk assessment. After identifying risks, you determine which controls will best mitigate or reduce those risks to acceptable levels. You should also consider legal, regulatory, and contractual requirements that might mandate certain controls.
Can ISO 27001 controls be customized?
Yes. While the standard provides a comprehensive list, you can adjust controls based on the nature, size, and requirements of your organization. Customization helps ensure the controls are practical, cost-effective, and relevant to your unique environment.
What is the relationship between ISO 27001 and ISO 27002?
ISO/IEC 27001 is the certifiable standard that outlines the requirements for an ISMS and includes a reference list of controls in Annex A. ISO/IEC 27002 provides detailed implementation guidance for these controls. You use ISO 27002 as a companion to better understand how to implement the controls recommended in ISO 27001.
How often should ISO 27001 controls be reviewed or updated?
Controls should be reviewed regularly—at least annually or whenever there is a significant change (e.g., new technology, organizational restructuring, or major shifts in risk landscape). Continuous monitoring and periodic internal audits help ensure the effectiveness and relevance of implemented controls.
What if my organization already has other security measures in place?
ISO 27001 is designed to integrate with existing security frameworks and measures. You can map your current controls to the relevant ISO 27001 controls, identifying any gaps or areas for improvement. This approach helps optimize your existing security processes rather than duplicating them.
How do ISO 27001 controls help with compliance requirements (e.g., GDPR, HIPAA, etc.)?
ISO 27001 controls provide a robust, internationally recognized framework for managing information security risks. Many of its practices align with regulatory requirements like GDPR, HIPAA, and others. By implementing ISO 27001 controls, you often address a broad spectrum of compliance obligations more efficiently.
Do I need a consultant to implement ISO 27001 controls?
While it’s possible to implement ISO 27001 internally, hiring a consultant or working with an experienced partner can streamline the process, particularly if your organization lacks in-house expertise. A consultant can guide risk assessments, control selection, documentation, and audit preparation.
How long does it take to implement ISO 27001 controls?
The timeframe varies based on the size and complexity of your organization, as well as your existing security posture. Some organizations can implement the controls in a few months, while others may need a year or more to fully integrate them into their processes and culture.
Why does Annex A start with 5 in ISO 27001?
Annex A in ISO/IEC 27001:2022 is structured such that the controls are consolidated under main clauses beginning with section 5. The sections prior to 5 (i.e., clauses 0–4 in the ISO standard) focus on the overarching requirements for setting up, implementing, maintaining, and continually improving an ISMS. Beginning the controls at clause 5 helps distinguish the “what” of an ISMS’s core requirements from the “how” of implementing those security controls.
What are the 4 domains under ISO 27001 list of controls?
In the 2022 version of ISO/IEC 27001, the 93 controls are grouped into four thematic domains to streamline their application:
- Organizational Controls – Focus on policies, processes, and governance measures.
- People Controls – Address the human factors in information security (e.g., training, awareness).
- Physical Controls – Cover the protection of physical environments and infrastructure.
- Technological Controls – Encompass technical measures such as encryption, access management, and system monitoring.
What are the benefits of implementing ISO 27001 controls?
- Risk mitigation: A systematic approach to identifying and managing security risks.
- Regulatory compliance: Strong alignment with various data protection and privacy regulations.
- Customer trust: Demonstrates your commitment to safeguarding information, fostering confidence in your services.
- Continuous improvement: Encourages regular review and enhancement of your information security posture.
What happens during an external audit of ISO 27001 controls?
During an ISO 27001 certification audit, an external auditor will examine your ISMS policies, procedures, and records to verify that you have effectively implemented and maintained the relevant controls. They may interview staff, review documentation, and conduct spot checks to ensure compliance and effectiveness.
Concluding: Why bother with ISO 27001 Controls
Annex A controls in ISO 27001 are the core actions, policies, and measures that organizations implement to secure their information systems and assets. These controls provide an approach to managing information security risks. The importance of Annex A controls lies in their ability to:
- Standardize Information Security Practices: They provide a clear set of controls that organizations can follow to ensure that all aspects of information security are addressed.
- Mitigate Risk: By addressing vulnerabilities and reducing the likelihood of security incidents, Annex A controls help minimize risks to business operations, finances, and reputation.
- Ensure Compliance: Many industries have regulatory requirements that demand robust information security practices. ISO 27001 controls help organizations comply with laws, industry standards, and best practices.
- Enable Continuous Improvement: ISO 27001 is based on a cycle of continuous improvement, and the controls ensure that organizations not only meet current security needs but also adapt to new vulnerabilities.
Final Tips for Implementing and Maintaining Controls
Successfully implementing and maintaining ISO 27001 controls requires a structured, ongoing approach. Here are some final tips to ensure your organization’s controls are effective:
Start with a Risk Assessment: The foundation of ISO 27001 is identifying and addressing risks. A thorough risk assessment is essential for selecting the right controls and ensuring that they address your organization’s specific vulnerabilities.
Ensure Top Management Support: The success of your ISMS depends on leadership buy-in. Ensure that top management is actively involved in setting the direction for information security and that they allocate the necessary resources for implementing and maintaining controls.
Integrate Controls into Daily Operations: Information security is not just the responsibility of the IT team. Ensure that security practices are embedded across all aspects of the organization, from HR policies to employee training and physical security measures.
Regularly Monitor and Review: Implementing controls is just the first step. Regular audits, assessments, and feedback loops are essential for ensuring that controls remain effective and aligned with evolving risks. Use monitoring tools and techniques to continuously assess the performance of your ISMS.
Stay Flexible and Adapt to Change: The threat landscape is constantly changing, so it’s important to regularly update and adapt your controls to new risks. Regularly review Annex A controls and adjust them as necessary to keep pace with emerging threats, changes in technology, and business requirements.
Ending thoughts
Cybersecurity resilience is about preventing attacks and making sure your organization can recover swiftly and remain operational in the face of disruptions. ISO 27001 controls help achieve this resilience.