ISO 27002 Implementation Guide
- Excel-based Implementation Guide.
- Guidance for deploying ISO 27002 2022 controls.
- Comparative of 27001:2013 and 27001:2022 controls.
- Additional details on controls.
- Guidelines for conducting internal audits.
- Document and assess security controls.
What is the ISO 27002 implementation guide?
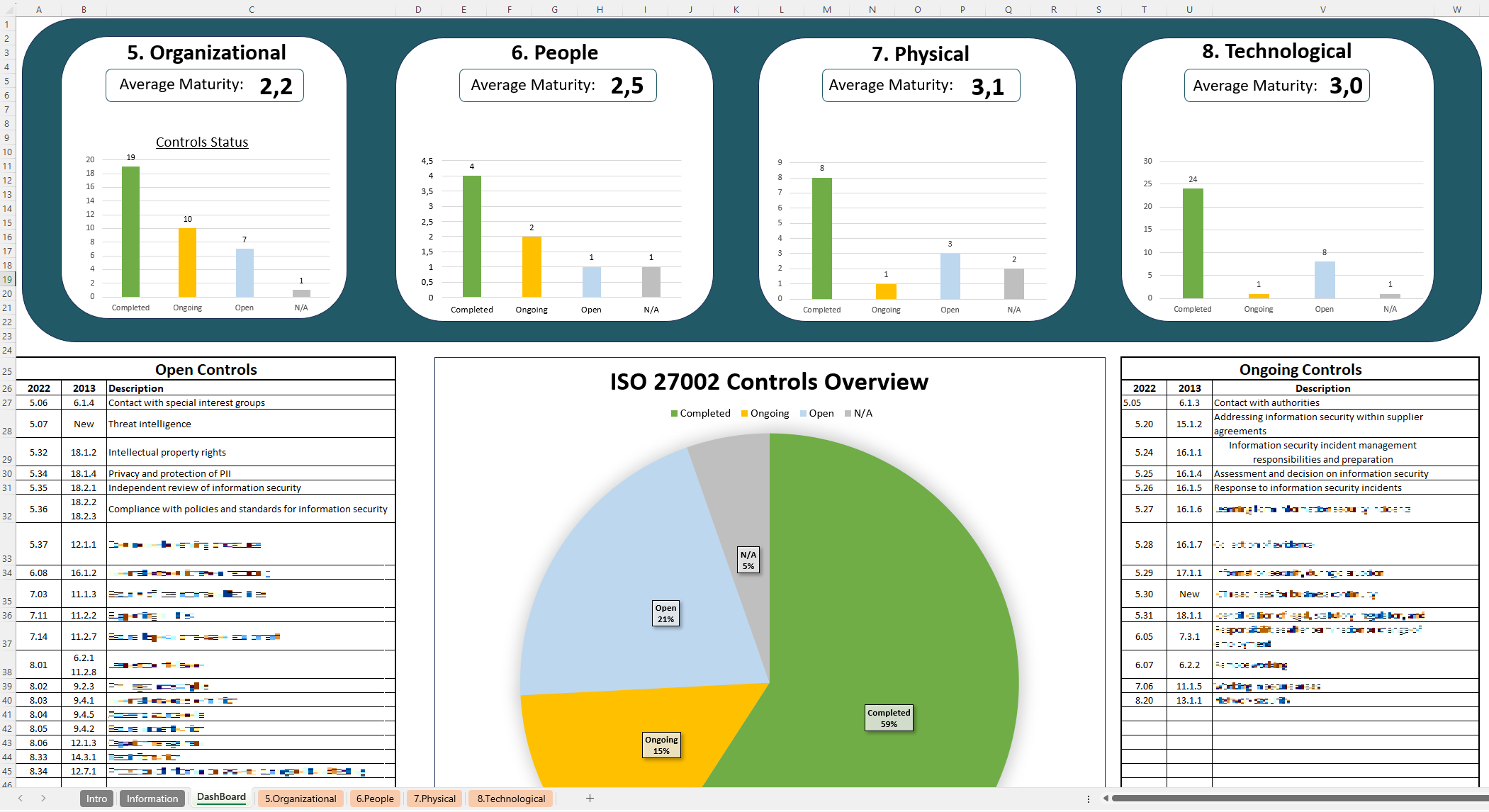
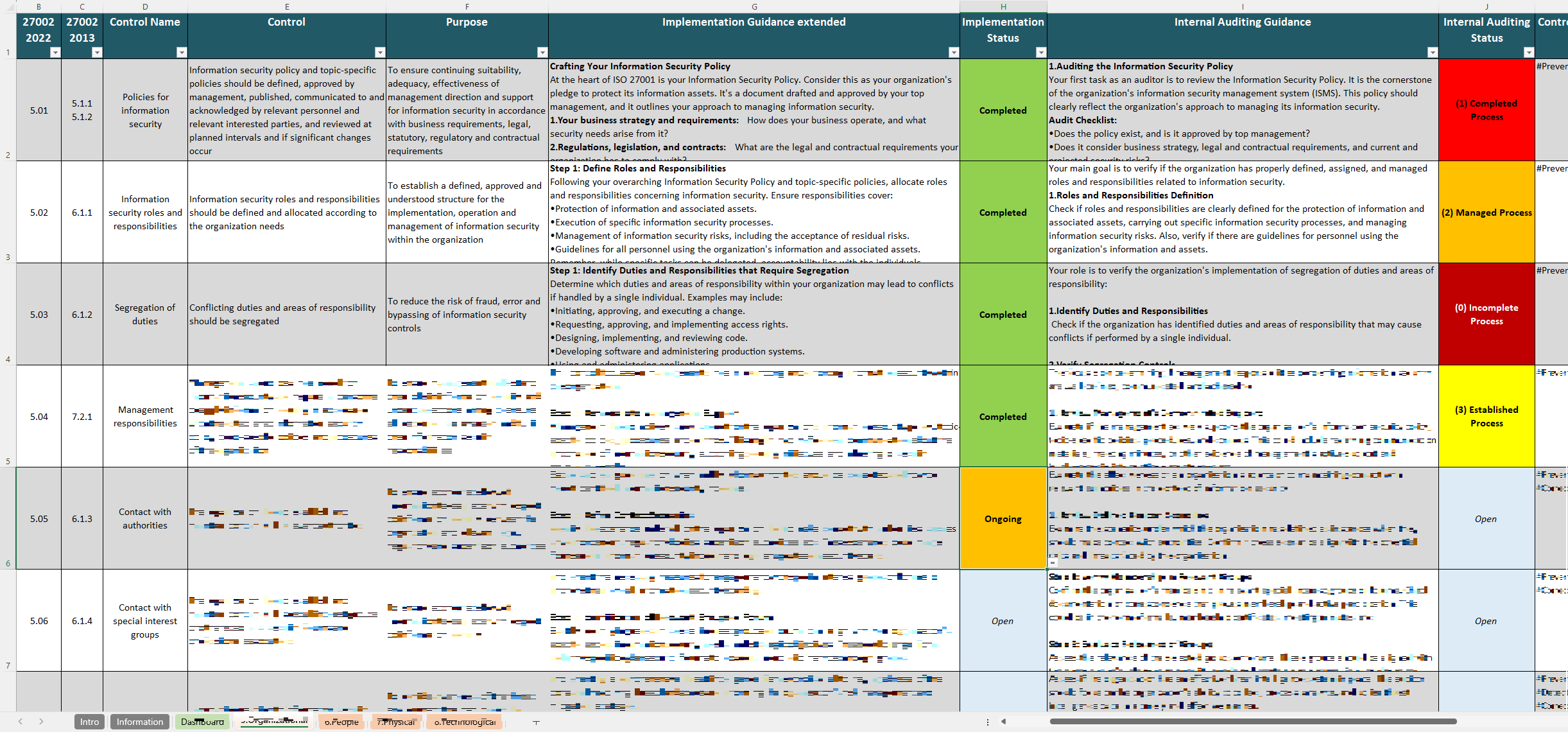
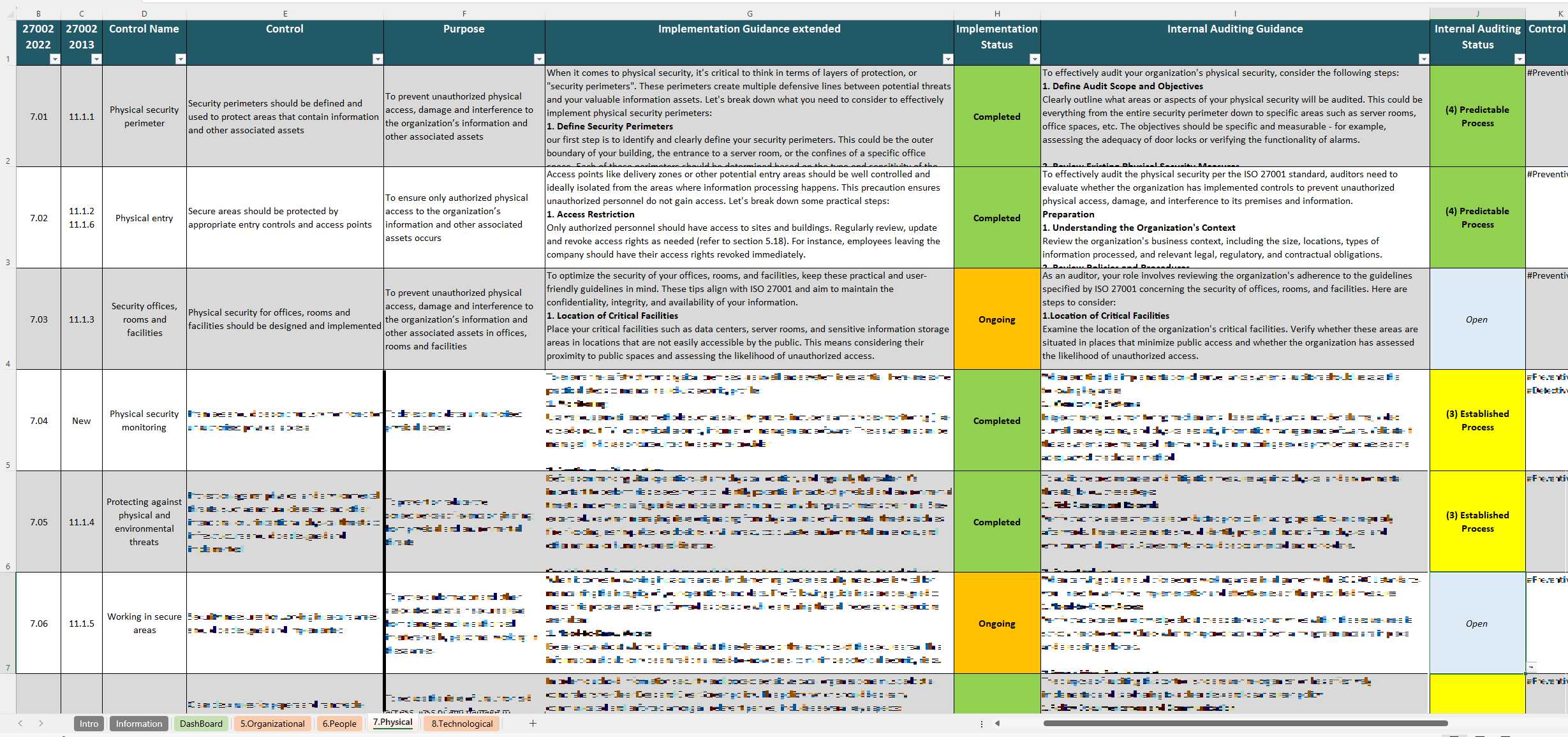
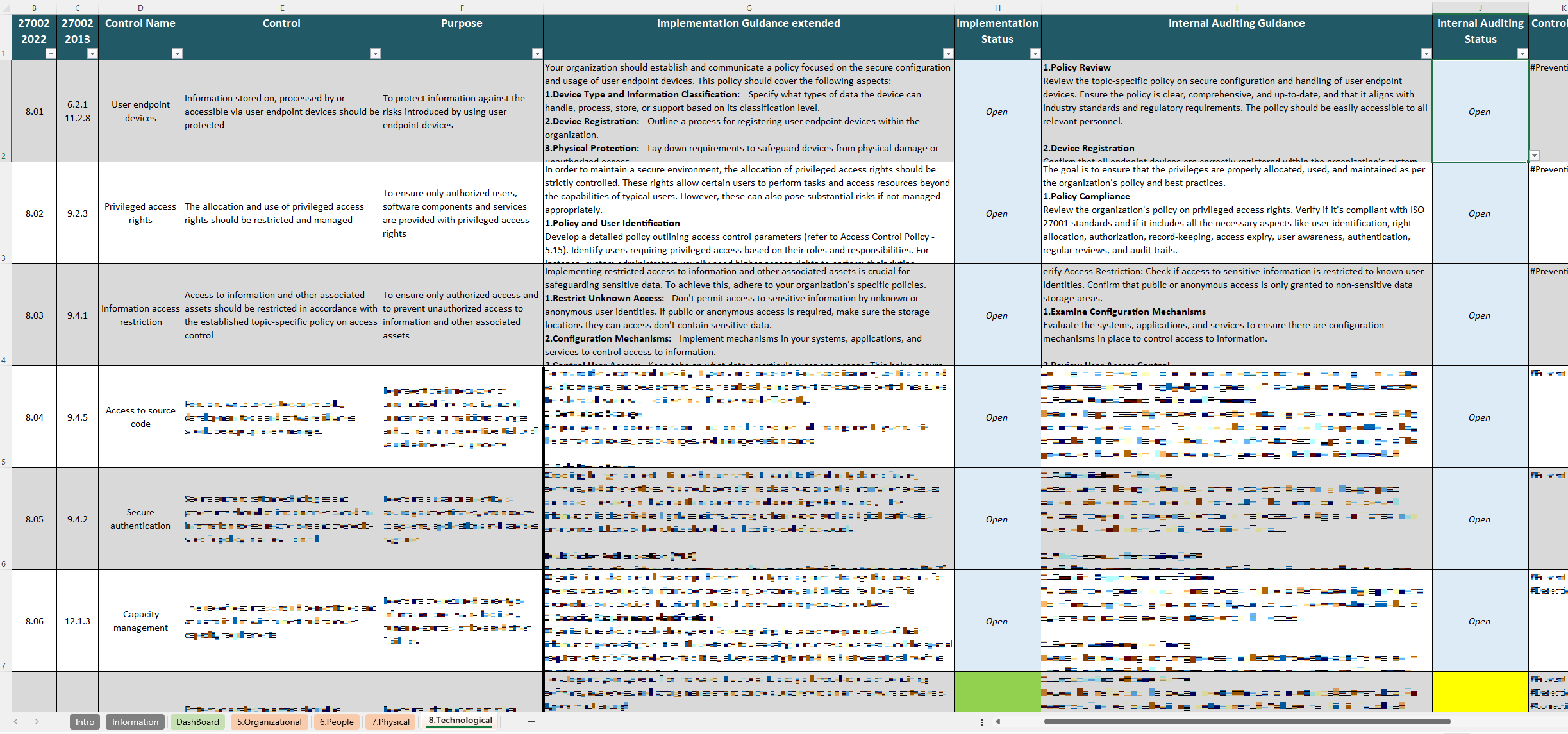
With a user-friendly format, the ISO 27002 Implementation Guide breaks down the recently updated 93 ISO 27002 controls into four categories: Organizational, People, Physical, and Technological. Each control is presented with space for documentation and tracking, enabling users to map responsibilities, assign tasks, and record audit findings with ease. This resource is valuable for organizations seeking ISO 27001 certification or looking to align their security practices with global standards, offering a clear method to organize and demonstrate compliance.


What is ISO 27002?
ISO 27002 is a globally recognized standard that provides a framework for implementing information security controls. It offers detailed guidance on selecting and applying the most appropriate controls to mitigate information security risks. By emphasizing practical measures, ISO 27002 helps organizations protect their critical assets.
The standard was updated in 2022, streamlining its control structure by reducing the total number of controls from 114 to 93 and grouping them into four main categories: Organizational, People, Physical, and Technological.
Differentiating ISO 27001 and ISO 27002 in the ISO 27000 Family
ISO 27001 and ISO 27002 are closely related standards in the ISO 27000 family, both centered on information security. However, each plays a distinct role in forming and maintaining an Information Security Management System (ISMS). ISO 27001 establishes the overall requirements for an ISMS, including the processes for risk assessment and treatment, while ISO 27002 provides detailed guidance on selecting and implementing specific security controls.
ISO 27001: ISMS Framework
ISO 27001 is the core standard for creating, implementing, maintaining, and continuously refining an ISMS. It adopts a risk-based approach, requiring organizations to identify, assess, and manage potential threats in a systematic way to protect their information assets. The standard also mandates regular internal audits and management reviews to ensure ongoing compliance and adaptation to emerging risks. Achieving formal ISO 27001 certification further demonstrates an organization’s commitment to robust security practices, earning trust from clients, partners, and regulators alike.
ISO 27002: Guide to Implementing Security Controls
While ISO 27001 defines the “what” of information security—establishing goals and principles—ISO 27002 covers the “how” by offering detailed guidance on applying specific security controls. These controls address areas such as access management, cryptography, and incident response, supporting the objectives outlined in ISO 27001’s Annex A. Unlike ISO 27001, ISO 27002 is not certifiable; it functions as a flexible, best-practice framework that organizations can tailor to their unique requirements.
In 2022, ISO 27002 underwent a significant update, consolidating the total number of controls from 114 to 93 and arranging them into four primary categories: Organizational, People, Physical, and Technological. This organized structure simplifies the process of selecting and implementing controls, helping organizations maintain compliance and adapt effectively to evolving security threats.
Integrating ISO 27002 Controls
The controls in ISO 27002 form the backbone of the standard, outlining the specific security practices organizations can use to safeguard their information assets and reinforce their ISMS. The ISO 27002 Implementation Guide is an excellent resource for tracking and managing these controls, enabling a systematic approach to implementing each measure as part of a broader security strategy.
In its 2022 revision, ISO 27002 streamlined the previous 114 controls into 93, categorizing them into four groups: Organizational, People, Physical, and Technological. This updated structure addresses evolving security challenges such as cloud security and threat intelligence, helping organizations stay resilient in an constantly changing cybersecurity landscape.
Four Categories of ISO 27002 Controls
- Organizational Controls
These controls center on governance, policy development, and procedural frameworks, covering areas such as risk management, supplier relationships, and defined roles and responsibilities. With addressing these foundational elements, organizations can establish a clear structure for their security programs and ensure alignment with overarching business objectives. - People Controls
Focused on human interactions and behavior, these controls include training initiatives, security awareness programs, and background checks. With utilizing tools like the ISO 27002 Implementation Guide, organizations can systematically monitor compliance and reduce the risk of human error, ultimately fostering a security-conscious culture. - Physical Controls
Aimed at safeguarding tangible assets, these measures address facility security, access restrictions, and other protective practices. Implementing physical controls helps prevent unauthorized entry to critical areas, supporting the overall integrity of an organization’s infrastructure and data. - Technological Controls
Spanning technical safeguards like cryptography, network protection, and system access management, these controls form the backbone of an organization’s digital defense strategy. With the ISO 27002 Implementation guide, teams can track and coordinate the implementation of these measures across various departments, ensuring comprehensive coverage and oversight.
Benefits of Using an ISO 27002 Implementation guide
Security Control Management
The ISO 27002 Implementation Guide centralizes an organization’s information security controls into one unified resource, making the oversight process more efficient. By keeping all controls in a single, well-organized document, teams can assign responsibilities, track progress, and document updates with ease. This cohesive approach facilitates better interdepartmental collaboration and ensures that all stakeholders have real-time access to the most current security information.
Readiness with the ISO 27002 Implementation Guide
The ISO 27002 Implementation Guide is particularly helpful for organizations aiming to achieve ISO 27001 certification, as it closely aligns with the Annex A controls outlined in ISO 27001.With leveraging this guide, teams can thoroughly prepare for both internal and external audits and maintain clear documentation of their control implementations. This detailed record allows auditors to quickly assess compliance efforts and confirms an organization’s commitment to robust information security practices.
Efficient Control Management with the ISO 27002 Implementation Guide
Implementing and tracking ISO 27002 controls can be intricate and time-consuming without the proper tools. The ISO 27002 Implementation Guide simplifies this process by offering a ready-to-use framework, reducing the need for manual tracking. With less administrative overhead, security teams can concentrate on refining controls and addressing emerging risks, rather than being bogged down in extensive documentation.
Customization for flexibility
The ISO 27002 Implementation Guide is designed for easy customization, allowing organizations to modify controls according to different risk levels, industry standards, and internal policies. This flexibility ensures that every security measure remains both relevant and effective, ultimately strengthening the organization’s overall security framework.
Security and Risk Management
Beyond compliance, the ISO 27002 Implementation Guide reinforces an organization’s security posture by supporting systematic risk management. By regularly tracking and reviewing controls, teams can proactively identify potential gaps, assess risk levels, and initiate timely improvements. This well-organized approach contributes to a resilient ISMS, ensuring it remains agile and responsive to evolving security threats.
Why Choose This ISO 27002 Implementation Guide?
The ISO 27002 Implementation Guide is designed to simplify and enhance the management of ISO 27002 controls. Here’s why it stands out:
User-Friendly Structure
The guide presents controls in a clear, organized format, reducing complexity for security teams and saving valuable time.
Alignment with ISO 27001
By mirroring ISO 27001 Annex A, it provides a solid foundation for achieving or maintaining ISO 27001 certification.Customizable Controls
Easily modify controls to address unique security concerns, industry-specific requirements, and risk profiles, ensuring lasting relevance and practicality.Audit-Ready Documentation
All control details are maintained in a single location, streamlining audit preparations and facilitating quick, accurate compliance verification.
Protect Your Business with CyberZoni
- Virtual CISO
- Vulnerability Scanning
- Control Design and Implementation
FAQ
What is ISO 27002?
ISO 27002 is a globally recognized standard focusing on information security controls. It offers detailed guidance on selecting and applying the most appropriate measures to protect an organization’s information assets, covering aspects such as access management, cryptography, and incident response.
What changed in the 2022 update to ISO 27002?
In 2022, ISO 27002 streamlined its structure, reducing the number of controls from 114 to 93. These controls are now categorized into four main groups:
- Organizational
- People
- Physical
- Technological
What is the ISO 27002 Implementation Guide
It is a practical resource that consolidates all ISO 27002 controls into a single, user-friendly format. Organizations can use it to:
- Document each control, its purpose, and its implementation status.
- Manage roles and responsibilities for each control.
- Monitor and review control effectiveness over time.
Why is the ISO 27002 Implementation Guide valuable for ISO 27001 certification?
The guide aligns with ISO 27001 Annex A controls, making it an excellent foundation for organizations pursuing (or maintaining) ISO 27001 certification. With keeping a clear record of control implementation, you can more easily prepare for audits and demonstrate compliance to internal and external stakeholders.
How does the Implementation Guide support audit readiness?
All control documentation is maintained in one place, simplifying audit preparation. Auditors can quickly review the organization’s approach to each control, verify compliance, and provide feedback. This centralization also cuts down on the time and effort needed to gather documentation scattered across different systems.