Chinese Domain Name Scams
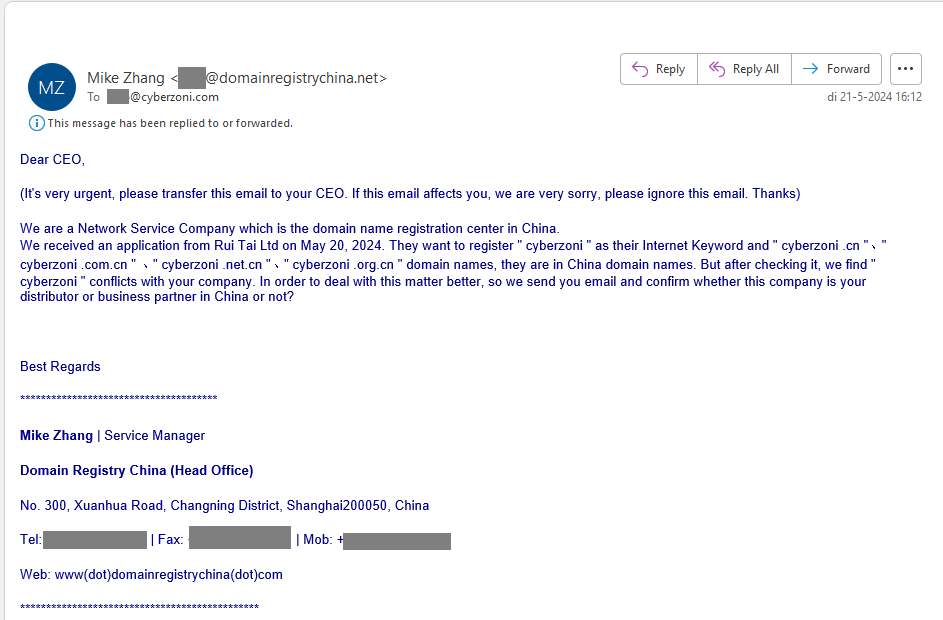
Chinese domain name registration scam, we responded so you don’t have to.
This scam is designed to invoke panic and prompt hasty financial decisions.
Our investigation into these deceitful practices provides a detailed look at how such scams unfold and the tactics used to exploit unsuspecting businesses.
Chinese Domain Name Scams Read More »