ISO 42001 Statement of Applicability (SoA)
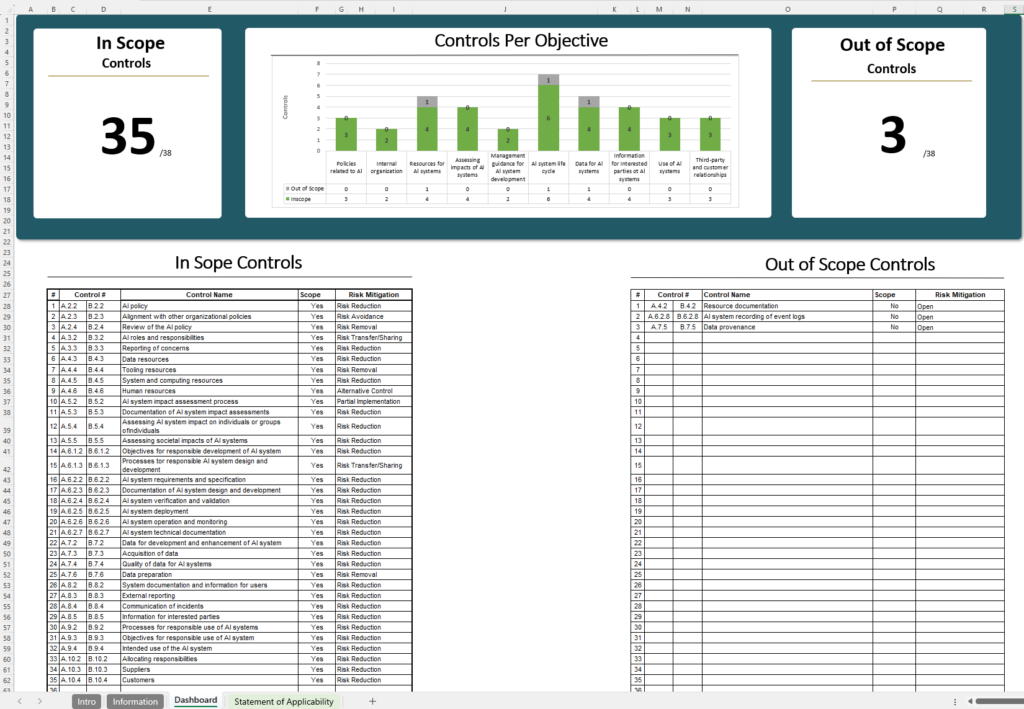
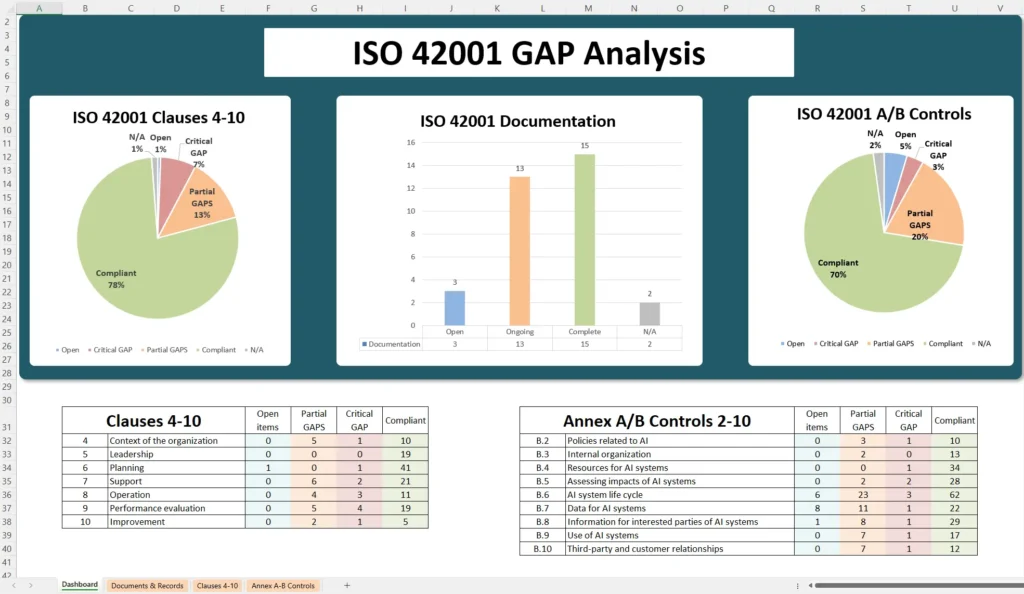
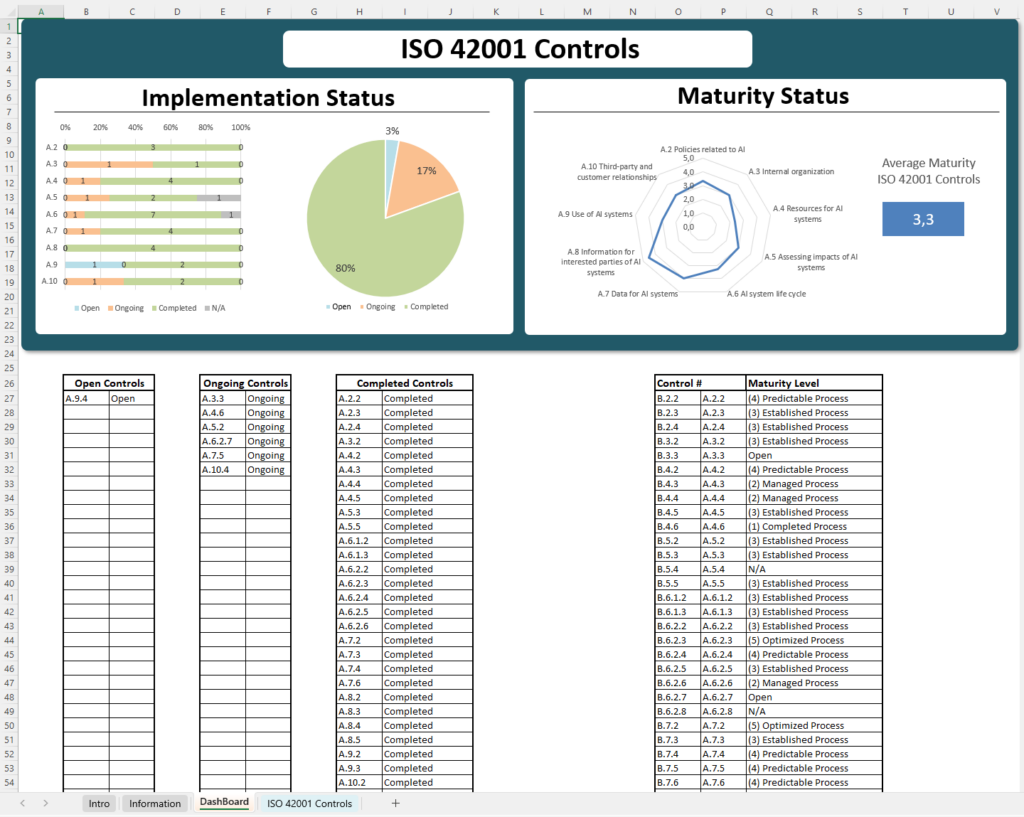
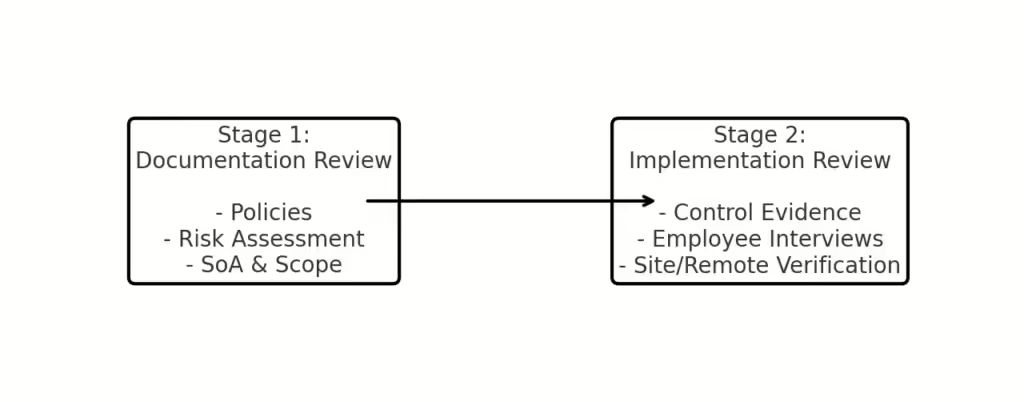
In ISO 42001, the Statement of Applicability (SoA) outlines the specific Annex A controls your organization has chosen to implement (or omit) based on its AI risk assessment, along with reasons for those decisions. This document is crucial for ISO 42001 certification, as it demonstrates your organization’s commitment to ethical and compliant AI management by addressing key AI risks (e.g. bias, privacy, transparency) with appropriate controls.
ISO 42001 Statement of Applicability (SoA) Read More »