Vendor Security Assessment - Questionnaire (.xls)
- Vendor Security Assessment Template
- Excel-based template
- List with Sample Questions
- Align with ISO 27001 (eg. Control 5.19)
Vendor Security Assessment Template
Instead of wading through endless details, a good template gives you a straightforward framework to assess your vendors’ security practices. It’s like having a checklist that ensures you don’t miss anything critical.
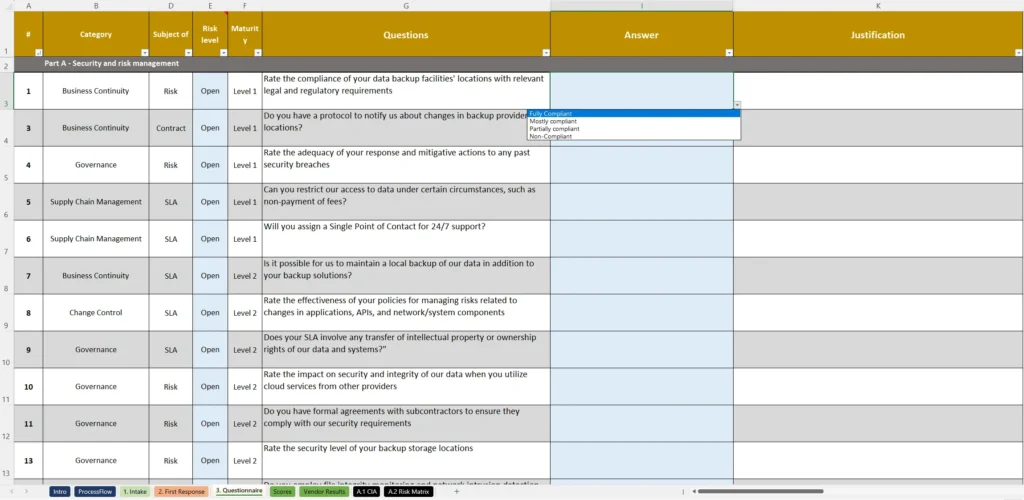
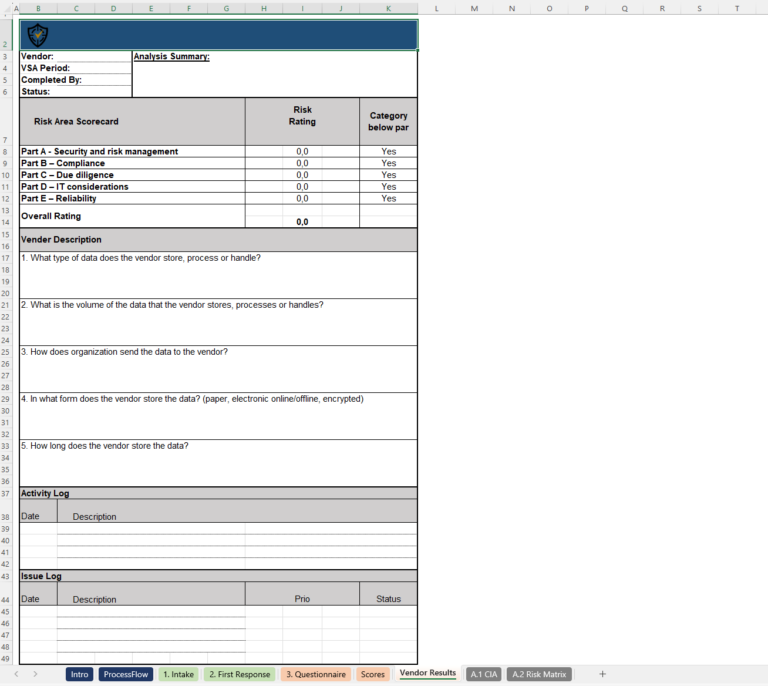
A strong vendor security assessment template covers some key areas, like:
- Organizational Security Policies: Does the vendor have a solid security foundation? This part checks their overall security governance.
- Access Controls: How well does the vendor protect access to sensitive systems and data? You want to make sure they’re not leaving any doors open.
- Data Protection Measures: Are they encrypting data? How do they handle sensitive information? This section is all about making sure their data practices meet your standards.
- Incident Response Plans: Are they prepared for a breach? Knowing their response strategy can be crucial for your own peace of mind.
- Compliance and Certifications: Do they meet industry standards and regulations? This is where you confirm they’re up to scratch on legal and compliance fronts.
Using a template you’re able to evaluate each one on the same playing field, making sure no security detail slips through the cracks.
Here’s a tip: make sure your vendor security assessment template aligns with recognized standards, like ISO 27001 Control 5.19. This specific control is all about managing information security risks when working with suppliers. Basically, it encourages you to set up processes and procedures that tackle any risks associated with using third-party products or services.
Incorporating a standard like ISO 27001 Control 5.19 in your template is a smart move. It makes sure your vendor evaluations meet industry best practices, giving you that added layer of protection for your organization. Plus, it reinforces trust and transparency with your vendors, which, let’s be honest, is a big win for everyone involved.
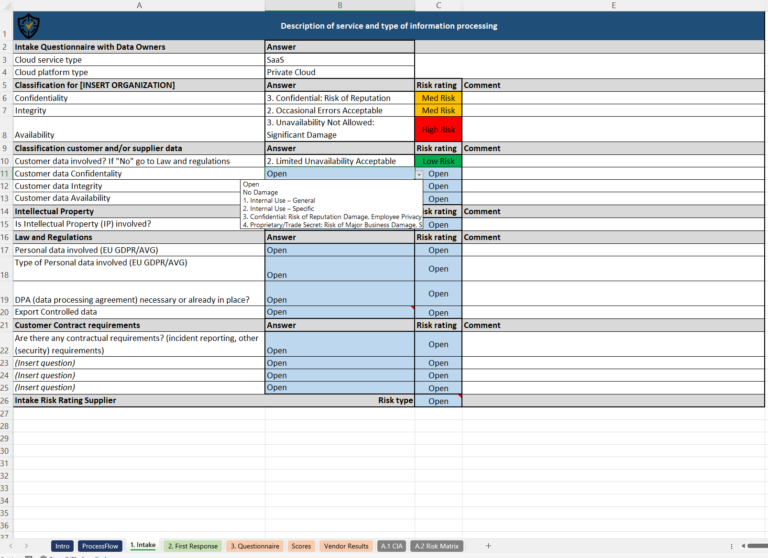
Vendor Security Assessment Questionnaire
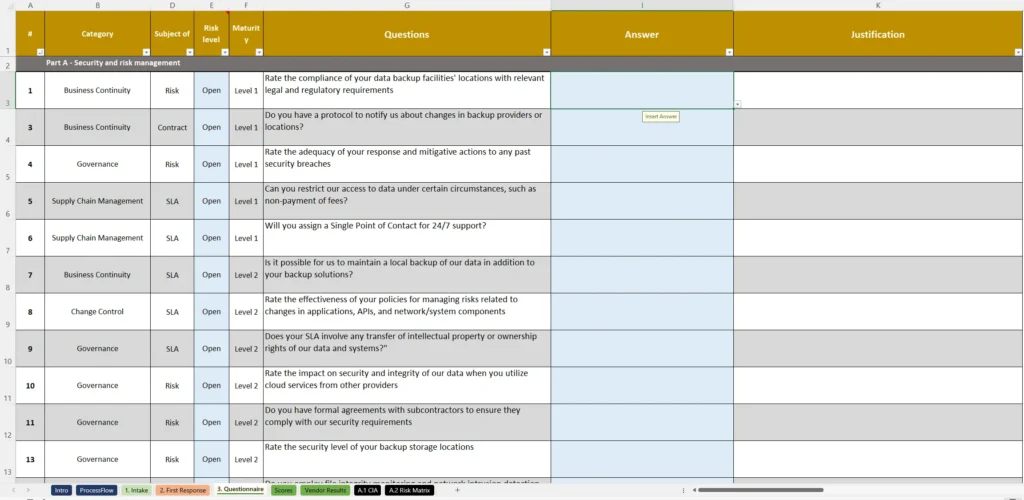
When it comes to collecting information about a vendor’s security practices, a well-designed vendor security assessment questionnaire is your best ally. This questionnaire is typically a structured set of questions that cover key areas of cybersecurity, such as access control, data encryption, and incident response. By using a vendor security assessment questionnaire, you can get a snapshot of your vendor’s security posture without needing to dig into their systems firsthand.
Think of it as a roadmap. With a well-organized questionnaire, you’re not just ticking boxes; you’re uncovering the layers of your vendor’s cybersecurity practices. This makes it easier to spot potential vulnerabilities and determine if your vendor’s security measures align with your own standards.
Vendor Security Assessment Questionnaire xls
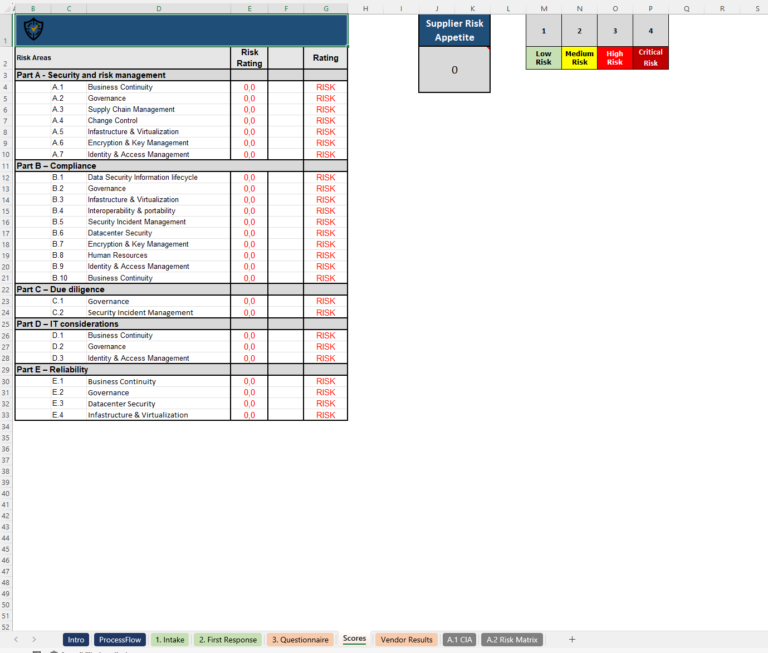
For those managing multiple vendors, an Excel (XLS) version of the vendor security assessment questionnaire can be a game-changer. The vendor security assessment questionnaire xls allows you to input, track, and compare responses in a standardized format, making it much simpler to manage large sets of data. In Excel, you can create custom fields, automate scoring, and even visualize results through graphs or charts.
An XLS format also enables easier collaboration across teams. When multiple stakeholders need to review the results, having a shared spreadsheet ensures everyone stays on the same page and can quickly spot any red flags.
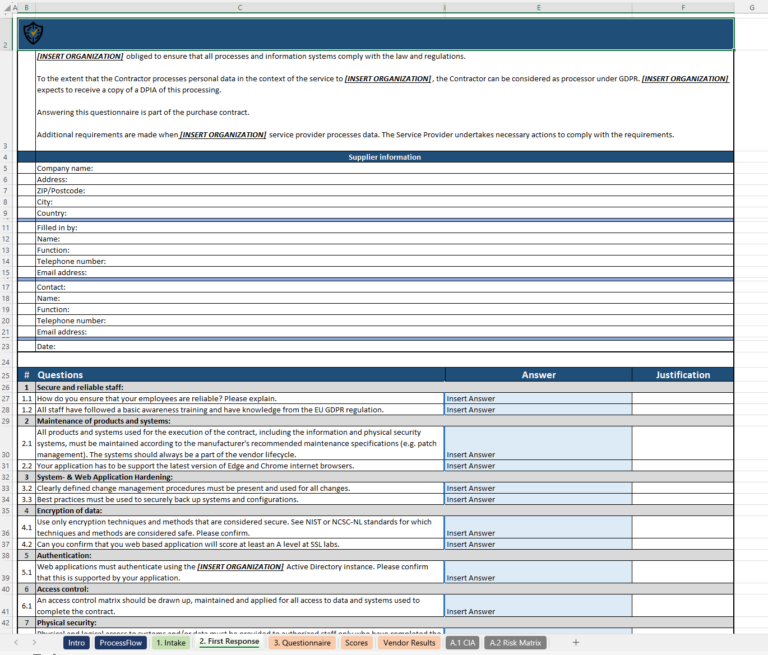
Vendor Security Questionnaire Template
A vendor security questionnaire template is a ready-to-go solution designed to simplify your risk assessment process. This template usually includes a list of questions covering essential areas like network security, data protection, compliance, and incident response. By using a pre-made vendor security questionnaire template, you save time on crafting questions from scratch, ensuring you cover all critical points.
For those who need a more specialized tool, the Procurement supplier risk assessment template offers a tailored approach to assessing suppliers. This template is adaptable, allowing you to customize it to match specific risks related to your industry or vendor type, whether you’re dealing with IT services, suppliers handling sensitive data, or subcontractors with access to your network.
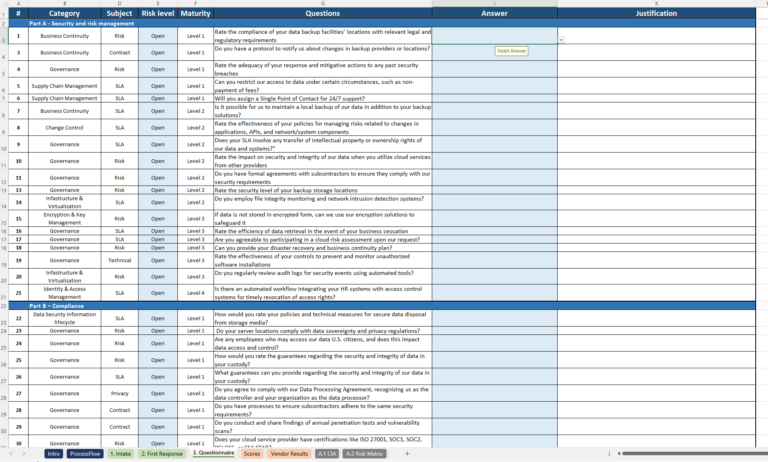
Vendor Security Assessment Questionnaire Sample
Looking for inspiration or clarity on what a vendor security assessment questionnaire should look like? A vendor security assessment questionnaire sample can provide a clear example of best practices. Samples are useful for understanding the types of questions you might ask and the depth of information you need. They often illustrate how questions can be phrased to get specific, actionable answers.
Samples also serve as a benchmark. By comparing your vendor’s responses to a questionnaire sample, you can evaluate their security readiness against established best practices. This ensures you’re setting a high standard for data protection and risk management, even before any formal partnership begins.
In summary, a comprehensive vendor security assessment—backed by a well-structured questionnaire, a versatile XLS format, and robust templates—can significantly reduce the risks associated with third-party vendors. These tools empower you to identify potential security gaps early, make informed decisions, and build a safer network of trusted vendors. After all, in cybersecurity, a proactive approach to vendor management can make all the difference in keeping your data secure.