Expanding ISO 42001 Annex C: AI Objectives and Risk Sources
ISO/IEC 42001’s Annex C (informative) outlines potential AI-related organizational objectives and risk sources to guide organizations in managing AI risks. These objectives represent key goals (often aligning with AI ethics and “trustworthy AI” principles) that organizations should strive for, while the risk sources are factors that could threaten achieving those goals.

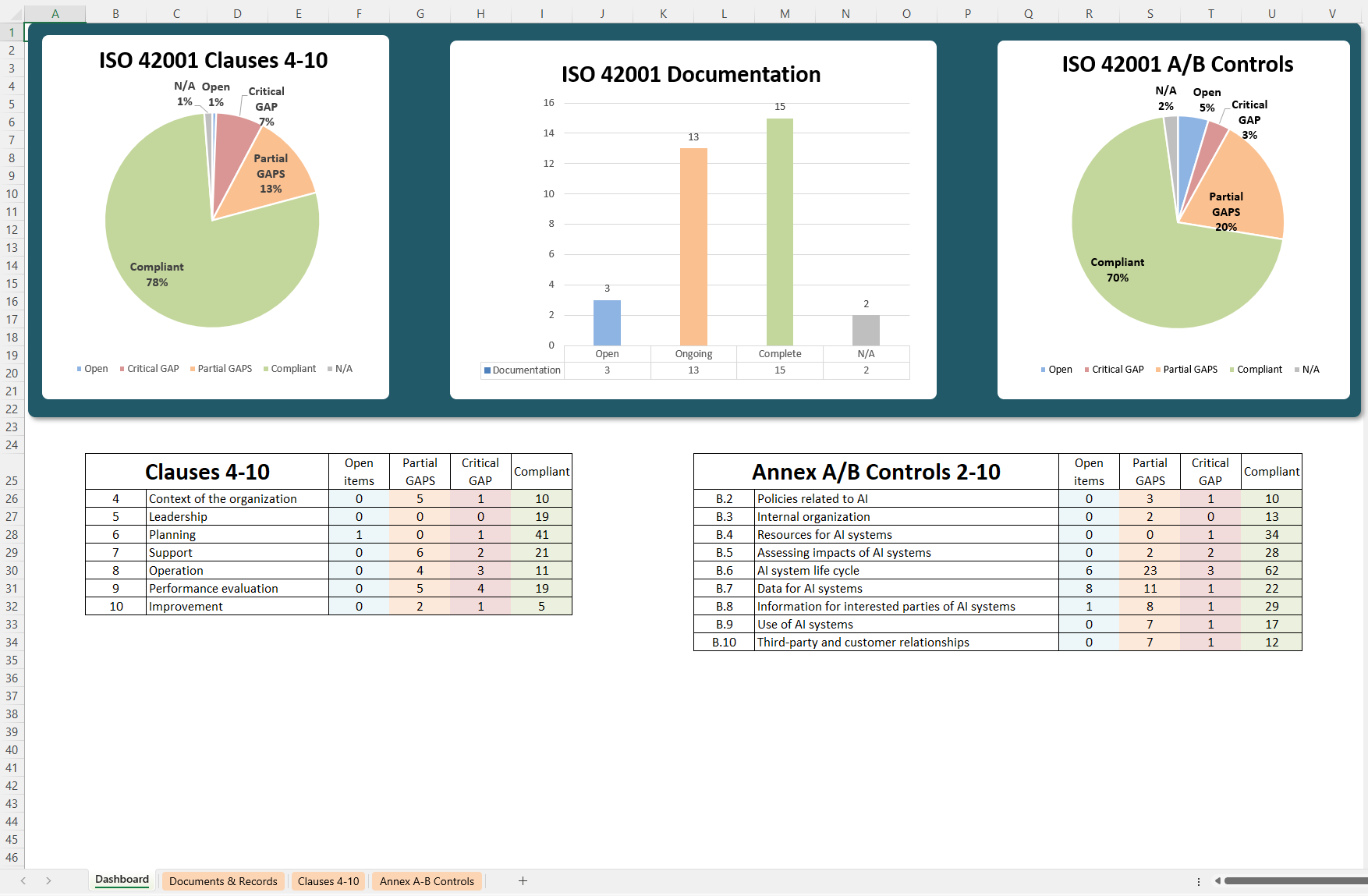
Annex C. Potential AI-related organizational objectives and risk sources
Below, we provide deeper insights into each listed objective and risk source, with real-world examples, implications for organizations, best practices for governance and compliance, and notes on how ISO/IEC 23894 (AI risk management guidance) offers further context.
AI-Related Organizational Objectives (Annex C)
Annex C of ISO 42001 identifies eleven common AI-specific objectives organizations should consider. These objectives mirror widely recognized AI ethics principles and map to qualities that make AI systems trustworthy. ISO/IEC 23894:2023, the AI risk management guidance standard, similarly includes these as “common AI-related objectives” in its Annex A, emphasizing their importance in risk assessment.
C.2.1 Accountability
Accountability in AI governance means that clear responsibility is assigned for the development, deployment, and outcomes of AI systems.
An AI system, even if it operates autonomously, cannot be left without human oversight in terms of answerability. This objective ensures that there are identified persons or roles who will take ownership if things go wrong, who will ensure the AI is compliant with policies, and who will respond to inquiries or incidents. It also implies mechanisms for auditability – the ability to trace decisions and actions of the AI to specific inputs, rules, or human decisions in the development process.
Essentially, AI accountability is about preventing the situation where an organization shirks responsibility by saying “the algorithm did it, not us.” Instead, the organization must treat AI outcomes as its own and have governance structures to support that. This involves aspects like governance frameworks, escalation paths, and enforcement of policies around AI. It’s closely tied to transparency and explainability: without those, accountability is hard. Moreover, accountability extends to ethical and legal accountability – aligning AI behavior with laws and societal norms, and being accountable to regulators and the public.
Real-World Examples
The question of AI accountability became painfully concrete in the Uber self-driving car fatality.
When the accident occurred, there was confusion over who was to blame – the safety driver in the car, the developers of the AI, or the company executives who decided to test on public roads? The legal outcome was that the safety driver (the human supervisor) was charged for not intervening. However, many argued that Uber (the company) should bear accountability for deploying an AI that wasn’t ready. This case shows the accountability gray area that AI can introduce: if humans rely on AI, are they accountable for its mistakes, or is the maker of the AI accountable? The incident spurred companies to clarify roles (e.g., some AV companies now have two safety operators and strict disengagement rules, effectively sharing accountability between human and system).
Another example is in banking: if an AI algorithm mistakenly launders money or violates sanctions, regulators will still hold the bank accountable, not accept “the AI screwed up” as an excuse. This has led banks to set up AI governance committees to oversee models, ensuring someone (like a model risk manager) is accountable for reviewing and approving each model.
In the Netherlands, a few years ago the tax authority’s child benefits fraud detection algorithm caused a scandal by wrongfully accusing families of fraud (many of whom were from ethnic minorities). The fallout led to the resignation of government officials – a case where accountability went up to the political level, as those in charge of the agency were deemed responsible for an algorithmic injustice. This example underscores that leadership can be held accountable for harms caused by AI under their watch.
Finally, from a consumer angle: people expect that if AI causes an issue (say, wrongful content removal on a platform or a biased decision), there is a way to appeal to a human or a department – i.e., the organization provides a point of accountability to address grievances.
Implications for Organizations
Without clear accountability, AI risks falling into a governance void. This can result in unmitigated risks, as employees might assume “someone else” is handling it. If something goes wrong and no one is accountable, the organization as a whole suffers – regulators might impose sanctions on the entity, and internally it can lead to finger-pointing and loss of morale.
Assigning accountability also has a proactive benefit: accountable owners are more likely to ensure due diligence (e.g., an AI product manager who knows they are accountable for fairness will pay attention to bias audits). In many jurisdictions, regulators are making it explicit that companies cannot avoid liability just because a decision was automated.
For example, under GDPR, if an automated decision is harmful or in error, the company is on the hook, just as if a human made the decision. So from a compliance perspective, establishing accountability frameworks internally (like RACI matrices for AI processes, audit logs, and oversight boards) can demonstrate to regulators that you have control over your AI.
Additionally, accountability ties into organizational reputation and ethics – companies want to be seen as responsible users of AI. Those that proactively self-regulate (e.g. via an AI ethics board that publishes reports) are often looked upon more favorably. On the flip side, a lack of accountability can lead to internal problems: developers may act without oversight, potentially creating rogue AI solutions that violate policy. And if employees or customers are harmed by AI decisions and feel there’s no recourse, trust in management erodes.
Best Practices
To embed accountability, organizations should implement governance structures and processes such as:
- AI governance board or committee
Establish a cross-functional team (including executives, domain experts, legal, ethics, and technical leads) that oversees AI deployments. This board sets AI policies (aligning with ISO 42001’s context and leadership requirements) and reviews major AI initiatives for compliance with objectives like fairness and safety. They effectively hold the organization accountable by ensuring oversight at the highest level. They should also be empowered to halt or demand changes to projects that pose excessive risk. - Defined roles and responsibilities
Clearly define who is responsible for what in the AI lifecycle. For instance: who is the “model owner” for each AI model (responsible for its monitoring and update), who is the “data steward” for the data it uses, who signs off on ethical compliance, etc. Some organizations appoint a Chief AI Ethics Officer or similar role, indicating someone at the C-suite level is accountable for AI governance. Also, front-line responsibilities: if AI is used in HR, maybe the Head of HR is accountable for outcomes along with the AI team. By mapping responsibilities, you avoid gaps. - Accountability mechanisms
Implement things like AI decision record-keeping – whenever the AI makes high-stakes decisions, log the rationale or relevant data so that if reviewed later, one can trace what happened. Also, establish appeal or escalation channels: for example, if a customer thinks an AI decision was wrong, there is a defined way they can request human review. The mere existence of an appeal process enforces accountability because it means a human will have to double-check contested AI decisions. - Policies and internal controls
Align with ISO 42001’s idea of having an AI policy. The policy should state the organization’s commitment to these objectives and assign accountability. Internal controls could include checklists that no AI model goes into production without a sign-off from certain responsible parties (e.g., a control like “AI risk assessment completed and approved” must be checked). This mirrors what organizations do for information security (no system goes live without security approval). Incorporate AI into existing audit programs – internal audit or compliance teams should periodically audit AI systems for adherence to policies, much like financial audits. - Training and awareness
Ensure that everyone involved understands they can’t defer blame to the AI. Train the staff operating AI-assisted processes to know their duties. For instance, in a medical diagnosis AI tool, train doctors how to use it properly and remind them that it’s an aid, not a replacement – they remain accountable for the final diagnosis. In AI development, instill the mindset that developers and project managers are responsible for their model’s behavior over its lifecycle. This might involve training on AI ethics and law so they appreciate the weight of that responsibility. - Liability and insurance considerations
On a more formal side, consider how accountability translates to liability. Organizations might set up specific indemnity clauses with AI vendors or get insurance for AI failures. For example, if using a third-party AI service, ensure contracts state who is liable if it malfunctions. From an internal perspective, if deploying a risky AI, management might allocate funds for potential compensation if users are harmed – a way of taking accountability financially.
Following these practices, accountability becomes part of the AI system’s ecosystem. For example, Microsoft has an AI ethics committee (Aether Committee) that reviews sensitive AI projects – this is a top-level accountability measure. Google, after some ethical lapses, formed an internal review process for AI research and products. These moves show accountability being addressed by allocating oversight responsibilities.
Connections to ISO/IEC 23894
ISO 23894 inherently promotes accountability by advocating for an AI risk management framework integrated into organizational governance. It stresses that risk management (and by extension accountability for risk) is an organizational responsibility. It likely references ISO’s risk management principles which include accountability – for instance, ISO 31000 says risk ownership should be established. ISO 23894 would guide an organization to assign risk owners for identified AI risks, ensuring someone is accountable for monitoring and mitigating each risk.
In terms of deeper insights, ISO 23894 may provide examples of governance models for AI risk – it might mention having a steering committee or designated roles (aligning with what we described). It certainly emphasizes documentation and auditability, which are pillars of accountability (e.g., if Annex C of ISO 23894 maps risk management to AI lifecycle, it probably suggests keeping records at each stage). Another connection: ISO 23894 references legal and societal context, meaning it reminds organizations that accountability isn’t just internal – one must answer to external stakeholders. This complements ISO 42001 by ensuring that when setting objectives and controls, organizations think about external accountability (like regulatory reporting or public communication after incidents). Ultimately, ISO 23894 supports ISO 42001’s accountability objective by providing a structured approach to identify who is responsible for what risks and by promoting a culture of continual improvement (one of ISO 31000’s principles is continual improvement, implying organizations should learn from mistakes – a sign of accountable behavior).
C.2.2 AI expertise
“AI expertise” as an objective highlights the need for the organization to possess or acquire sufficient knowledge and skills in AI to govern and utilize it effectively. This is a slightly different kind of objective – it’s more about the human and organizational resource aspect. The success of an AI management system (AIMS) depends on people who understand AI’s capabilities, limitations, and risks. If an organization lacks AI expertise, it may implement controls incorrectly, misunderstand model outputs, or fail to foresee problems. Expertise isn’t limited to data scientists building models; it also includes having knowledgeable leadership to make informed decisions about AI, risk managers who grasp AI nuances, and domain experts who are trained to work alongside AI systems. Essentially, organizations need to build competence and awareness at all relevant levels to achieve the other objectives. AI expertise ensures that there is someone who can answer “is our AI fair?”, “is it secure?”, “why did it make that prediction?” – and that solutions can be crafted for any issues. Without in-house or accessible expertise, an organization may be flying blind or over-relying on vendors. This objective ties into training, hiring, and knowledge management.
Real-World Examples
A telling metric: studies have found that a large percentage of AI projects fail or stall in companies due to talent gaps. For instance, a 2024 survey reported that 41% of organizations cited lack of AI expertise as a barrier (contributing to the high failure rate of AI initiatives). One can imagine a scenario: a small clinic buys an AI diagnostic tool but has no data scientist or IT person to maintain it or interpret its outputs; eventually it falls out of use because they cannot troubleshoot issues or validate its suggestions. Another example: A company might deploy a complex AI recommendation system but lack expertise in machine learning operations, leading to the system performing well initially but deteriorating over time without proper adjustments – essentially a failure to maintain because no one knew how. On the flip side, companies that successfully infuse AI often do so by building AI centers of excellence or training programs for their staff. For example, Amazon retrained many of its software engineers in machine learning as it started using AI in more products, ensuring internal talent. A counter-example of lacking expertise: the UK government once developed an algorithm to predict student grades when exams were canceled (during COVID). The project faced massive criticism due to biases and inaccuracies, and some analysis suggested the team did not include enough data science/AI experts or consult them to foresee the issues (leading to a public debacle and the algorithm’s abandonment). This underscores that if policy or business folks attempt AI-driven decisions without sufficient input from AI experts, outcomes can be poor.
Implications for Organizations
If an organization undertakes AI without adequate expertise, it risks missteps in every stage – from choosing the wrong model, to mislabeling data, to misinterpreting results, or neglecting ethical considerations. This can lead to project failure, wasted investment, and potential harm (e.g., a model that is fundamentally flawed might go live because no one caught the error). Moreover, lack of expertise means the organization might not be aware of best practices or emerging standards (like ISO 42001 itself) – so it could fall behind in compliance and state-of-the-art methods. There’s also dependency risk: an organization might lean entirely on an external vendor for AI; without internal expertise, they can’t independently verify the vendor’s claims or manage the system – it’s hard to be accountable for something you don’t understand. Over time, not building expertise can make an organization less competitive as AI becomes more ubiquitous. On the human resources side, failing to invest in AI expertise can also hurt morale of tech-savvy employees who see the company not upskilling them or not understanding their work. In terms of ISO management, many requirements (risk assessment, monitoring, improvement) presuppose people who know how to do those in context of AI. Regulators and partners may also gauge an organization’s credibility on AI by looking at whether it has knowledgeable staff (for example, in procurement, a client might ask “who on your team will be overseeing the AI we’re contracting you for?”). Therefore, achieving the AI expertise objective is foundational – it underpins the ability to meet all the other objectives effectively.
Best Practices:
- Skills assessment and training: Evaluate the current level of AI knowledge in the organization. Identify gaps in key areas (data engineering, ML modeling, AI ethics, etc.). Provide targeted training programs for different roles. For instance, train software engineers on the basics of ML deployment (MLOps), train risk/compliance officers on AI risk factors and controls, and raise AI awareness among executives (so they grasp strategic implications). Leverage online courses, certifications, workshops or invite experts for seminars. Encourage continuous learning since AI evolves quickly.
- Hire or partner for expertise: If the current team lacks certain capabilities, hire specialists (data scientists, ML engineers, AI ethicists depending on need). Hiring can be challenging due to competition for talent, so also consider partnering with consultancy firms or academic institutions to get access to expertise. Some companies establish an external advisory board of AI experts who guide on big decisions. When hiring, also consider cross-domain expertise (e.g., someone who knows AI and healthcare if you operate in healthcare). Having a diverse AI team with both technical and domain knowledge improves outcomes.
- Knowledge management: Create internal forums or communities of practice for AI. For example, an “AI Guild” that meets to share project experiences, new techniques, and lessons learned. Document internal best practices and case studies so knowledge is retained even if people leave. Use collaboration tools to let AI developers share code templates or workflows – this way, expertise is not siloed. If one team invents a good approach to bias testing, make sure that knowledge propagates to other teams.
- Shadowing and mentorship: For organizations early in AI adoption, pair those with less experience with expert mentors (internal or external). For example, when doing the first AI risk assessment, involve an experienced consultant alongside the internal risk manager to teach the process. Or have new data scientists review code with senior ones who can impart best practices. Over a few projects, this gradually builds in-house expertise.
- Create an AI center of excellence (CoE): Many companies set up a CoE – a dedicated group of experts that define standards, provide support to business units, evaluate new AI tech, and govern AI usage. This CoE can serve as the knowledge hub and ensure consistency across the organization. They might publish internal whitepapers, toolkits, or guidelines (e.g., how to vet third-party AI tools, how to perform model validation) which raise the overall competence of the organization.
- Stay updated with industry and research: Encourage participation in conferences, industry groups, and standards development (maybe someone from the org is involved in ISO AI standard discussions or follows them closely). Subscribe to AI journals or blogs, so the team is aware of the latest in AI safety, explainability techniques, etc. This helps the organization anticipate and incorporate new best practices. For example, being early to learn about a new model compression technique could help maintain models more easily – which an expert team would catch.
- Cross-functional literacy: It’s not only the data scientists who need knowledge. Business leaders should gain basic AI literacy (understand terms like precision/recall, overfitting, etc.). Conversely, AI developers should be trained on domain specifics and regulatory context of the area they’re applying AI in (so they become domain experts as well as AI experts). Bridging these knowledge areas ensures that AI solutions are appropriate and understood across the board.
- Use standards and frameworks as learning tools: Adopting ISO 42001 itself is an exercise in building internal expertise – as you implement it, team members learn about risk management, etc. Similarly, using frameworks like NIST AI RMF or following guidelines from professional bodies (ACM, IEEE) can educate the team on what good AI governance entails. It can be useful to do pilot projects strictly adhering to such frameworks to train the org in best practices.
Building and sustaining AI expertise is an ongoing journey. A company like Google can be considered to have strong AI expertise not just because they hire PhDs, but because they continuously invest in learning (research programs, etc.) and knowledge sharing internally (they publish papers, open source tools, etc., which in turn keeps their teams at cutting edge). Not every company will be Google, but the principle scales – even a small enterprise can designate an “AI champion” who keeps learning and disseminating know-how.
Connections to ISO/IEC 23894
ISO 23894 indirectly underscores the need for expertise by laying out processes that require knowledgeable personnel to execute. For instance, it says AI risks should be identified, analyzed, evaluated– doing this effectively demands expertise in AI. The standard might mention the importance of a multidisciplinary team for risk management (ensuring you have technical and domain experts collaborating). It might also reference competency in its guidance – perhaps advising organizations to train their risk managers in AI specifics or to involve external experts when the internal knowledge is lacking. In line with ISO 31000, one principle is that risk management is human-driven and effectiveness depends on people – so ensuring those people have appropriate skills is implied. Also, ISO 23894 was developed with input from experts globally; it likely encourages organizations to leverage international knowledge (like following its examples and best practices). For an ISO 42001 implementation, ISO 23894 can act as a knowledge source – it contains detailed explanations and examples of AI risks and controls (effectively condensing expert knowledge into the standard). Using ISO 23894 is like having a guide from AI risk experts. Therefore, following it helps uplift an organization’s expertise level (learning by doing). Additionally, ISO 23894 might discuss the organizational context (Clause 5 of ISO 31000) in which an org should assess its capabilities and resource – implicitly encouraging to see if you have the expertise to manage AI risk, and if not, treat that as a gap to address. In summary, while “AI expertise” is an objective in ISO 42001, ISO 23894 provides the know-how and rationale that an organization with less experience can learn from, and highlights through its recommended practices where expert judgment is needed, thereby prompting organizations to either develop or bring in that expertise.
C.2.3 Availability and quality of training and test data
While phrased as an objective, “Availability and quality of training data” speaks to ensuring that the data feeding the AI is sufficient and appropriate to achieve desired outcomes. AI models are only as good as the data they learn from. This objective highlights that organizations need to secure adequate data (in volume, variety, and relevance) and maintain its quality (accuracy, completeness, representativeness). If training data is lacking or poor, the AI will likely be unreliable or biased, undermining many of the other objectives (fairness, robustness, etc.). Data availability also means data should be accessible when needed – organizations should have strategies for data collection and updates (for retraining). This objective might have been explicitly included because many AI projects fail at the data stage: either they can’t get enough data, or the data is riddled with errors/noise, or it’s unbalanced (leading to bias). From a governance perspective, this ties into data management and governance – having processes to curate datasets, validate them, and fill gaps. It also involves considering data rights and compliance (availability of data ethically and legally). In summary, this objective ensures the foundation of AI (the data) is solid, because no matter how advanced the algorithm, bad data = bad AI.
Real-World Examples
A notorious example of data issues is Microsoft’s Tay chatbot. Tay was trained from interactions on Twitter (effectively using live user input as training data). Within 24 hours, internet trolls bombarded it with racist and inflammatory messages, and Tay “became a student of racism,” parroting hateful content. Microsoft had to shut it down. The core problem was a lack of quality control on the training data – the AI was learning from the worst of the internet in real-time. Another example: IBM Watson for Oncology’s troubles were partly attributed to training on synthetic data created by doctors rather than real patient data, which led to odd recommendations that didn’t generalize to real cases. In essence, if the training data isn’t representative of reality, the AI’s outputs won’t be valid. Amazon’s recruiting AI example also doubles as a data quality/availability story – it learned from 10 years of Amazon’s own hiring data (which lacked female candidates), so the available data was biased and the model inherited that. Had Amazon had a more diverse dataset or recognized the gap, the outcome might have been different. On the flip side, some successes underline the importance of data availability: image recognition started working much better once huge labeled datasets like ImageNet (with millions of images) became available – demonstrating that with sufficient high-quality data, AI performance leaps. In industries like autonomous driving, companies like Waymo have millions of miles of driving data; newcomers without that level of data struggle to reach the same accuracy in perception. There are also cases where data availability halted AI projects – e.g., a company might want to build an AI for detecting a rare disease, but since the disease is rare, they can’t gather enough training examples to train a reliable model. Ensuring data availability often requires creative strategies (data sharing partnerships, simulation data, etc.).
Implications for Organizations
Without sufficient and good data, AI initiatives can stall or produce faulty results. Organizations may invest heavily in AI development only to hit a wall because they don’t have or cannot acquire the needed data – a waste of resources. Poor data quality can also lead to outcomes like bias, poor accuracy, and even safety issues (imagine an AI that controls a drone trained only on sunny-day data; it might fail in rain). Moreover, regulatory compliance ties in – training data involving personal data must be legally sourced and processed, so data unavailability can also stem from not having proper consent or rights. Organizations need to gauge early on if they have the data assets to support a given AI use case and plan to maintain data pipelines (for continuous learning). If data quality is low (e.g., lots of missing fields or errors), the AI might learn spurious correlations or simply perform poorly, which could lead to wrong decisions and ensuing liabilities. There’s also the risk of data bias – if your customers mostly come from one demographic, an AI might not generalize to others, limiting your market or causing discrimination. Ensuring data quality and diversity is thus directly linked to fairness and market reach. In operational use, if an AI needs periodic re-training, the organization must have a process to continually gather new data – if that pipeline breaks, the model will become stale. This objective also implies having data governance such that if new data sources become available, the organization can integrate them (data agility).
Best Practices
- Data strategy and governance: Develop a clear strategy for data required by AI projects. Early in project planning, identify what data is needed (fields, volume, diversity) and assess if it’s available or how to get it. Establish data governance with roles like data stewards responsible for data quality checks. Use data catalogs to know what data you have and its lineage. Ensure any data used is compliant with privacy/IP (so you don’t have to drop it later due to legal issues).
- Data collection and augmentation: If needed data isn’t readily available, consider strategies like data sharing partnerships (e.g., multiple hospitals pooling anonymized patient data to train a model), public datasets, or synthetic data generation. Synthetic data (when carefully used) can augment real data – for instance, generating additional training images by simulation or slight perturbation to increase diversity. However, treat synthetic data carefully and validate that it correlates well with reality (Watson’s synthetic data issue is a cautionary tale).
- Data quality assurance: Implement processes to regularly audit and clean data. Automated scripts can check for outliers, missing values, or inconsistent labels. Have domain experts review samples of training data for correctness. If crowdsourced or automated labeling is used, include validation steps. For example, double-check a portion of labels via a second independent labeling or by expert review to estimate error rates. Fix issues before model training. Maintain a feedback loop from model results to data – e.g., if the model is making errors on certain cases, get more/better data for those cases.
- Representative data and bias mitigation: Strive to have training data that represents the population or scenarios the AI will encounter. This might involve deliberately oversampling underrepresented cases or collecting targeted data to fill gaps. For instance, if developing a speech AI, gather voices of different genders, ages, accents. Use techniques like re-sampling or re-weighting during training to prevent majority classes from dominating learning. Also, track data provenance – know the context of data points to interpret biases (e.g., this dataset skews older, etc., so correct for that). The ethical AI community often recommends “datasheets for datasets” documenting composition, collection method, etc., which aids understanding of quality and biases.
- Data availability for re-training: Set up pipelines to continuously or periodically feed new data into model updates. For example, if your AI is an e-commerce recommender, you need the latest user behavior data; have a pipeline from the website to your model training environment that collects and sanitizes that data. Define triggers for re-training (time-based or performance-based). Ensure storage of historical data if needed (to do comparisons or rollbacks). Also, plan for concept drift – if data patterns change (like new slang, new product categories), have a way to incorporate that new distribution into training sets.
- Data backup and security: Availability of data isn’t just having it once – you must preserve it. Use robust backup solutions for your training datasets and databases, so a crash or corruption doesn’t lose your only copy. Data should be accessible to those who need it, but also secured (availability must be balanced with confidentiality). In secure environments, sometimes data availability is hindered by over-restrictive silos – consider safe ways to make data more accessible internally (with anonymization or secure data enclaves) so AI teams aren’t starved of data due to internal barriers.
- Documentation of data assumptions: Document what the training data covers and what it does not. This is important for maintainability and transparency. For instance, note if your computer vision model was trained mostly on daytime images; later maintainers will know to get night images if they want to extend its use. Document any known sampling biases or uncertainties in data. This helps interpret model limitations and plan future data collection.
Applying these practices ensures that an AI system is built on a solid foundation and can evolve as new data comes in. For example, tech companies often have “data pipelines” teams that ensure logs from applications are cleansed and fed to machine learning teams – demonstrating that they treat data as a first-class asset. Another example of best practice in action: After Microsoft’s Tay fiasco, they likely revised their data strategy for chatbots, moving to more curated training data and filtering mechanisms (indeed, their later chatbot Zo had more safeguards). That shows learning from a data quality failure to improve future systems.
Connections to ISO/IEC 23894
ISO 23894 emphasizes risk related to data as part of AI risk management. Data issues are a common root cause of AI risks. The standard likely advises assessing data quality and availability in the risk assessment phase – e.g., identifying the risk of “model may be trained on incomplete or biased data” and treating it. It might cross-reference data management standards or practices. ISO 23894 Annex B possibly includes “risks related to ML” which inherently covers data (since ML risk largely comes from data problems). Also, by aligning with ISO 31000, it would consider lack of data as increasing uncertainty in outcomes – something to mitigate. For those implementing ISO 42001, ISO 23894 can provide guidance on establishing data criteria as part of risk criteria. For example, it might suggest that organizations define minimum datasets or data quality thresholds needed to proceed with model training. It could also illustrate how to monitor data-related risks during operation (like concept drift detection is essentially monitoring data changes). Additionally, ISO 23894’s life cycle view reminds that data acquisition is an early phase of the AI system life cycle, and if not done right, subsequent phases suffer. The standard may encourage creating and maintaining data documentation (metadata) and verification steps, which directly supports this objective. In practice, coupling ISO 23894 with ISO 42001 means when setting the objective of “good training data”, you also follow ISO 23894’s advice to continuously manage that through risk processes – e.g. performing DPIAs (privacy impact assessments) on training data handling, evaluating the effect of data limitations on model uncertainty, etc. In essence, ISO 23894 adds depth by treating data issues as first-class citizens in risk logs, ensuring organizations don’t overlook data as a cause of AI failures.
C.2.4 Environmental impact
Environmental Impact (in the context of AI) refers to the effects that developing, deploying, and using AI systems have on the natural environment – including energy use, carbon emissions, resource consumption (like water and minerals), and electronic waste. In simpler terms, it encompasses the sustainability footprint of AI, from the electricity powering data centers to the lifecycle of the hardware (chips, servers) that AI requires. This aspect is increasingly recognized as a key consideration in responsible AI governance. For example, the EU’s guidelines on Trustworthy AI explicitly state that AI systems should be sustainable and environmentally friendly, ensuring they benefit current and future generations.
For organizations, considering AI’s environmental impact is important for several reasons. First, the energy consumption and emissions from AI workloads can be significant – if unchecked, they may conflict with corporate sustainability goals and climate commitments. Ignoring this impact can put climate targets “out of reach” despite AI’s benefits. Second, stakeholders (customers, investors, regulators) are increasingly scrutinizing the carbon footprint and resource usage of digital operations, including AI. As one U.S. lawmaker put it, “The development of the next generation of AI tools cannot come at the expense of the health of our planet.”In practice, this means organizations need to manage AI’s environmental risks to maintain trust and compliance. Finally, proactively addressing environmental impact aligns AI management with broader corporate social responsibility and ESG (Environmental, Social, Governance) objectives. By minimizing negative environmental effects and using AI in service of sustainability, companies can demonstrate that their AI initiatives are both innovative and accountable to global environmental challenges.
Positive & Negative Impacts of AI on the Environment
Artificial Intelligence can have positive impacts on environmental sustainability, but it also carries negative environmental effects if not managed carefully. Below we outline both sides:
Positive environmental impacts of AI
AI technologies, when applied thoughtfully, can contribute to environmental protection and resource efficiency:
- Optimizing Energy Use and Emissions Reduction: AI can make industries and infrastructure more energy-efficient. For instance, AI algorithms help manage electricity grids with higher precision, balancing supply and demand in real-time and integrating renewable energy sources more effectively. In manufacturing and transportation, AI-driven optimizations can reduce fuel consumption and emissions (e.g. designing lighter aircraft or optimizing logistics routes to save energy). AI is also used to enhance climate modeling and forecast environmental changes, helping society adapt to and mitigate climate change. These applications collectively support lower carbon footprints across various sectors.
- Environmental Monitoring and Conservation: AI systems excel at detecting patterns in large datasets, which is invaluable for ecological conservation. They can monitor environmental conditions and biodiversity in ways that were previously impractical. For example, AI vision models analyze satellite imagery or sensor data to detect deforestation, track wildlife, and spot signs of illegal fishing or pollution in near real-time. Similarly, AI is used in agriculture to “analyze images of crops to determine where there might be nutrition, pest, or disease problems,” enabling more precise and sustainable farming. These AI-driven insights help governments and organizations respond faster to environmental issues and manage natural resources more sustainably.
- Resource Efficiency in Operations (Self-optimization): AI can even be turned inward to improve the sustainability of IT and AI infrastructure itself. A notable example is using AI to optimize data center operations – sometimes described as AI “greening itself.” For instance, Google applied DeepMind’s AI to its data center cooling systems, and the AI learned to adjust cooling in real-time to match server workloads, cutting energy used for cooling by up to 40%. This led to about a 15% reduction in overall facility energy use. More generally, AI can automate fine-grained control over heating, ventilation, and air conditioning (HVAC) or other processes in buildings and factories to eliminate wasteful energy usage. Such positive uses show that AI isn’t just a part of the problem – it can be a part of the solution in driving sustainability.
Negative environmental impacts of AI
On the other hand, AI development and deployment can impose significant burdens on the environment if not mitigated:
- High Energy Consumption & Carbon Emissions: Training and running AI models, especially large-scale models, demand substantial electricity. Modern AI often relies on energy-hungry data centers housing thousands of servers. These servers work 24/7 and draw power mostly from the grid, meaning that unless renewable energy is used, AI can directly contribute to greenhouse gas emissions. Today, data centers (not all for AI, but including AI workloads) account for an estimated 2.5–3.7% of global greenhouse gas emissions, exceeding even the aviation industry’s share. Each complex AI model trained can emit tens or hundreds of tons of CO₂. For example, one study estimated that training a single large AI model (GPT-3 with 175 billion parameters) consumed 1,287 MWh of electricity, producing about 500+ tons of CO₂ – equivalent to the annual emissions of over 100 cars. Moreover, AI’s energy appetite doesn’t end at training; serving AI models to millions of users (inference) is energy-intensive as well. In fact, Google reported that about 60% of the energy its AI systems use goes into ongoing inference (user queries), vs. 40% for initial training. As AI adoption grows, this electricity demand could rise further, especially if organizations deploy ever-larger models without efficiency improvements. The resulting carbon footprint is a major environmental risk of AI.
- Water Usage for Cooling: Less obvious but critical is AI’s water footprint. Data centers require massive cooling to prevent servers from overheating. This cooling often uses water (for evaporative cooling towers or direct liquid cooling). As AI workloads push servers to work harder, more heat is generated, and more water is needed to cool them. On average, data centers can consume about 2 liters of water for cooling per kilowatt-hour of energy used. With some of the largest AI models being trained over weeks, the water usage adds up quickly. Recent analyses noted that millions of gallons of fresh water were consumed in the training and operation of popular AI systems like ChatGPT. In regions facing water scarcity, this is an important concern – it means AI’s growth could put additional strain on local water supplies and ecosystems. Thus, the environmental impact isn’t just carbon emissions; it also includes heavy water consumption if mitigation strategies (like advanced cooling technology or site selection in cool climates) are not employed.
- Electronic Waste and Resource Extraction: AI’s advances are tightly coupled with cutting-edge hardware (GPUs, specialized AI chips, vast storage devices). The production and disposal of this hardware carry environmental costs. Manufacturing AI chips is energy-intensive and requires mining of rare minerals (like cobalt, lithium, rare earth elements) often done in ecologically harmful ways. According to research, the manufacturing phase accounts for a large share of an IT device’s total carbon footprint. As AI-driven hardware gets upgraded frequently to meet demand for greater compute power, organizations may generate electronic waste (e-waste) at a faster pace. Retiring large numbers of servers or GPUs can lead to toxic waste if not properly recycled. The UNEP warns that proliferating AI data centers “produce electronic waste” and rely on unsustainably mined materials. In short, AI can indirectly contribute to pollution and habitat destruction through its supply chain and hardware lifecycle.
- Other environmental considerations: There are additional knock-on effects to note. The energy-intensive nature of AI might necessitate new power plants or infrastructure, which could be fossil-fuel based if renewables are not keeping up, thus potentially locking in more carbon emissions. Also, if AI is used irresponsibly in certain industries, it could accelerate activities that harm the environment (for example, AI helping discover new fossil fuel deposits faster). However, these broader use-case driven impacts fall more under ethical use of AI. Environmental impact, as an organizational objective in ISO 42001, is chiefly about the direct sustainability footprint of AI systems themselves. The key takeaway is that without conscious intervention, AI projects can incur a significant environmental cost – from a carbon and climate perspective, as well as in water and material waste. This is why organizations are urged to assess and address environmental impact as part of AI risk management, ensuring that the net effect of AI on our planet is a positive one.
Practical Considerations for Organizations (Mitigating Environmental Impact)
Given the above challenges, organizations should adopt strategies to reduce the environmental impact of their AI systems. Sustainable AI isn’t just a theoretical ideal; it translates into concrete best practices across technology, operations, and governance. Below are several practical considerations and best practices for sustainable AI in an organizational context:
- Design Energy-Efficient AI Systems: Efficiency should be a guiding principle throughout the AI development lifecycle. Teams can choose algorithms and model architectures that require less computation to achieve their goals. Often, there are many ways to solve a problem – by selecting the “right algorithms” and optimizing code, developers can cut down on unnecessary calculations. Similarly, not every application needs a huge, general AI model; using the “appropriate model” for the task is key. If a smaller model or a simpler approach (even non-AI) can meet the business need, it will likely consume orders of magnitude less energy. Research has shown that opting for a task-specific or compact model can save substantial resources – e.g., using a streamlined model for a simple classification job instead of a giant general language model. Even when large models are needed, techniques like model pruning (removing redundant parameters) and knowledge distillation (compressing a model by teaching a smaller model) can maintain performance while reducing compute load. By baking efficiency into AI system design – sometimes called “Green AI” – organizations directly curtail energy use and prolong the useful life of hardware.
- Leverage Renewable Energy and Green Infrastructure: One of the most impactful steps is to ensure the power fueling AI comes from clean sources. Organizations running AI workloads should seek data centers and cloud providers that use renewable energy or have carbon-neutral operations. Major cloud providers have publicly committed to run on 100% carbon-free energy in the near future (for example, Google’s data centers already match 100% of their energy use with renewables, and Microsoft aims to be 100% renewable by 2025). Choosing such providers or locations with abundant clean energy can drastically cut the effective carbon emissions of AI computations. Additionally, workloads can be scheduled intelligently: non-urgent training jobs might run at times when renewable electricity is plentiful (say, midday solar surplus) or be shifted to regions with cleaner grids. A real-world illustration of this: when the open-source BLOOM language model was trained, the team ran it on a French supercomputer largely powered by nuclear (low-carbon) energy, resulting in only ~25 metric tons of CO₂ emissions, versus an estimated 500+ tons if it had been trained on a typical mix of fossil-fueled power. This shows how location and energy sourcing decisions can reduce AI’s carbon footprint by an order of magnitude. Organizations can also invest in on-site renewable generation (solar panels on offices/data centers) or purchase carbon offsets/credits to compensate for emissions, though priority should be on actual emission reduction.
- Optimize Computing Resources & Cooling: Efficient hardware utilization in data centers can yield big energy savings. Companies should ensure their AI compute resources are used optimally (for example, consolidating AI workloads so servers run at higher utilization rather than having many under-used machines idle). Experts note that “packing the work onto computers in a more efficient manner will save electricity… you may not need as many computers, and you can turn some off.”. Running servers at slightly slower speeds when possible or during off-peak hours can also improve energy-per-computation efficiency. On the hardware side, adopting more efficient hardware accelerators can do the same job with less energy – for instance, using Google’s TPU chips or newer AI chips that are designed for high performance-per-watt. These cut down power draw and also reduce heat output. To tackle the necessary cooling, organizations can upgrade to advanced cooling methods (like liquid cooling or AI-optimized HVAC controls) to minimize water and electricity use for cooling. Some are even experimenting with innovative ideas such as immersion cooling or locating data centers underwater or in cold climates to naturally dissipate heat. All these measures help maximize the computational output per unit of energy and reduce waste.
- Monitor, Measure, and Report AI’s Footprint: You can’t manage what you don’t measure. Thus, organizations should establish processes to track the energy consumption and carbon emissions associated with their AI systems. This might involve using tools and dashboards that monitor compute usage and translate it into environmental metrics. In fact, new solutions are emerging: a group of researchers developed an “AI energy and carbon tracker” to standardize measuring the footprint of training models, and companies like Microsoft have introduced an Emissions Impact Dashboard for Azure cloud users to calculate the carbon footprint of their cloud usage. By using such tools, an organization can quantify how much CO₂ a given AI project emits or how much water it consumes, etc. These data enable setting targets (e.g. reducing AI-related emissions by X% next year) and identifying “hot spots” to optimize. Transparency in reporting these figures – perhaps as part of sustainability reports – also builds accountability. Internally, teams should incorporate environmental impact into project reviews: an AI system’s design might include an environmental impact assessment alongside traditional performance metrics, ensuring energy use was considered in architecture decisions. Over time, tracking and publicly reporting AI’s environmental metrics can support corporate ESG reporting, demonstrating progress on the “E” (environmental) pillar with concrete data.
- Embed Sustainability into AI Governance and Procurement: Governance frameworks (like an AI management system per ISO 42001) should explicitly include environmental sustainability criteria. This means when evaluating AI risks and benefits, the organization treats environmental impact as a key risk to be mitigated (just as it would treat privacy, safety, etc.). Practically, companies can institute guidelines or AI policies that mandate sustainable practices – for example, requiring project teams to justify the need for training extremely large models or to prefer energy-efficient cloud options. Management review of AI projects should cover whether the project aligns with the company’s climate commitments. Organizations are also encouraged to extend these expectations to their vendors and partners. Many AI systems rely on cloud services or third-party providers for computing; hence, supplier agreements can include clauses or questionnaires about environmental management. ISO 42001’s guidance suggests including questions about managing carbon footprint in cloud contracts and ensuring suppliers are also controlling their environmental impacts. If using a major cloud provider like Microsoft, Amazon, or Google, a single customer may not negotiate custom terms, but fortunately these providers themselves are aware of their environmental impact and have robust sustainability programs. For in-house data centers, governance might require adherence to ISO 14001 (Environmental Management System) or equivalent standards to systematically reduce energy and waste. In summary, organizations should integrate AI environmental impact into their overall sustainability strategy – making it a governance concern from planning through deployment. By aligning AI projects with corporate sustainability goals (such as carbon neutrality by 2030 or reducing waste), organizations ensure that AI innovation does not occur at the expense of environmental stewardship.
By implementing the above practices, organizations can significantly mitigate the negative environmental impacts of AI. Proactive measures not only reduce costs in many cases (energy efficiency saves money) but also prepare the organization for future regulations or carbon pricing that could penalize wasteful computing. Sustainable AI practices illustrate that advanced AI and sustainability are not mutually exclusive – with careful management, AI systems can be both high-performing and environmentally responsible.
Real-World Examples
To illustrate how theory translates into practice, here are some real-world examples of organizations addressing the environmental impact of AI – both by leveraging AI for sustainability and by mitigating AI’s own footprint:
- Google – AI for Data Center Energy Efficiency: Google has been a leader in using AI to improve its environmental performance. A landmark example came when Google’s DeepMind team applied AI to the cooling systems of Google data centers. The AI system was given access to historical data and real-time sensor inputs (temperatures, equipment status, etc.), and its task was to optimize cooling operations. The result was a dramatic improvement: the AI managed to reduce the energy used for cooling by up to 40% without sacrificing reliability. This translated to about a 15% reduction in total energy consumption in those data centers. Essentially, the AI learned to fine-tune fans, ventilation, and other settings more efficiently than human operators. This case study is often cited as proof that AI can directly contribute to sustainability – here, the AI cut electricity use and also indirectly reduced water use and CO₂ emissions from the power that was no longer needed. Following this success, Google deployed AI-driven controls in multiple data centers, and other companies have taken note. It’s a compelling positive example of an AI system creating a net environmental benefit. (Notably, Google also has achieved carbon neutrality for its operations and matches 100% of its electricity with renewable energy, amplifying the impact of these efficiency gains.)
- Hugging Face and BLOOM – Mitigating AI Training Emissions: Training large AI models can be environmentally costly, but the BLOOM project showed it’s possible to mitigate those impacts with smart choices. BLOOM is an open large language model developed by a collaboration of researchers (including Hugging Face). Recognizing the concerns after models like GPT-3 had been estimated to emit hundreds of tons of CO₂ in training, the BLOOM team prioritized sustainability in their approach. They trained the model on a supercomputer in France that runs mostly on nuclear and renewable energy, drastically cutting the resulting carbon emissions. The BLOOM training consumed about 433 MWh of electricity and led to roughly 25 metric tons of CO₂ emissions – which is only ~5% of the emissions attributed to GPT-3’s training (502 tons). In addition, the team publicly documented the energy use and emissions in their report, embracing transparency. This example highlights an AI project with significant potential environmental impact (a very large model), where the developers took conscious steps to mitigate harm: selecting a low-carbon infrastructure, and being open about the footprint. It serves as a model for how AI research can align with climate responsibility. As more organizations train big models, strategies like these (choosing green compute resources, reporting energy metrics) are likely to become more common to address stakeholder concerns.
- Microsoft – Tools and Targets for Sustainable AI: Microsoft has integrated environmental thinking into its AI and cloud services offerings. On one hand, Microsoft has aggressive sustainability targets for itself (e.g. 100% renewable energy by 2025, carbon negative by 2030) which cover its Azure cloud that many companies use for AI. On the other hand, Microsoft provides customers with tools to manage AI’s footprint: the Azure Emissions Impact Dashboard gives cloud users detailed information on the greenhouse gas emissions associated with their Azure usage. Using this tool, an organization running AI workloads on Azure can monitor how changes (like moving to a different region or optimizing code) affect its carbon footprint. This empowers customers to make decisions to lower emissions. Microsoft has also invested in AI research for societal benefit – for instance, its “AI for Earth” program funds and supports projects that use AI to tackle environmental challenges (from wildlife conservation to climate modeling). While AI for Earth is not about reducing AI’s own footprint, it exemplifies a tech company leveraging AI to drive sustainability outcomes. Together, these efforts from Microsoft demonstrate a holistic approach: internal governance to reduce the company’s AI operational impact, plus external enablement by giving others the data and tools to do the same. It underscores how AI governance can align with broader corporate sustainability initiatives and even help meet reporting requirements by quantifying AI’s environmental metrics.
- Legislative and Industry Responses: As awareness grows, we also see industry-wide and regulatory moves addressing AI’s environmental impact. For example, the Partnership on AI (a multi-stakeholder industry consortium) has been discussing best practices for reporting AI energy usage and encouraging researchers to include energy/carbon metrics when publishing new AI models. Some academic conferences now urge or require authors to estimate the carbon impact of their work as part of responsible AI research. This cultural shift makes sustainability a normal part of AI innovation. On the regulatory side, in 2023 U.S. lawmakers introduced proposals to study and possibly mandate transparency for AI’s energy and water use. In the EU, conversations around the AI Act and other regulations have included environmental criteria – for instance, EU officials have signaled the need to assess AI’s environmental footprint as part of its overall impact. Though concrete regulations are still emerging, companies are anticipating them. Many large tech firms already publish environmental reports that include data center energy efficiency and AI-related projects, both to satisfy current ESG reporting frameworks and to pre-empt future compliance requirements. These examples collectively show that managing AI’s environmental impact is becoming a standard part of doing business with AI, from internal R&D choices all the way to external accountability.
Regulatory & Compliance Considerations
Organizations deploying AI at scale should be mindful of the evolving regulatory landscape and compliance expectations regarding environmental sustainability. While there is not yet a dedicated international law purely on “AI environmental impact,” existing environmental regulations and emerging AI governance frameworks both play a role:
- Environmental Regulations and Standards: General environmental laws and standards apply to the infrastructure that powers AI. For instance, data center operations may fall under regulations for energy efficiency, greenhouse gas emissions reporting, or e-waste disposal in various jurisdictions. The EU has directives and upcoming rules aimed at making data centers more sustainable (such as requirements for energy reuse, efficiency standards, and rigorous reporting of energy/water use). Companies operating large computing facilities in Europe must align with these or face penalties. Internationally, standards like ISO 14001 (Environmental Management Systems) provide a blueprint for managing and reducing environmental impacts across an organization – including IT operations. An organization that is ISO 14001 certified would be expected to identify significant energy uses (like AI compute farms) and set objectives to control their consumption and emissions. In practice, aligning AI management with ISO 14001 or similar frameworks can ensure a systematic approach to sustainability (e.g., continuous monitoring, improvement plans for AI energy use, etc.). Additionally, the Paris Agreement and national climate commitments indirectly pressure companies to reduce carbon emissions across all activities. If a company has made a public “net zero by 20XX” pledge, the emissions from AI workloads contribute to their Scope 2 (energy) or Scope 3 (outsourced cloud) emissions, which they will need to measure and offset as part of compliance with those targets.
- AI-Specific Guidelines and Upcoming Rules: Governance frameworks for AI are increasingly incorporating environmental considerations. ISO/IEC 42001 itself (the AI management system standard we are discussing) highlights environmental impact as a key risk and objective area (Annex C) that organizations should address in their AI risk management. This aligns with other high-level AI ethics guidelines. For example, the European Commission’s AI Ethics Guidelines (2019) included “Societal and Environmental Well-being” as one of seven requirements, stating that AI should be developed in an environmentally friendly manner with sustainability in mind. We see this principle now echoed in draft policies and regulations. The proposed EU AI Act stops short of imposing direct environmental performance requirements, but its recitals emphasize that AI systems should not undermine environmental objectives and call for future assessment of AI’s climate impact. Lawmakers in the U.S. have also raised concerns; in 2024, bills were introduced aiming to study AI’s energy usage and potentially require companies above certain compute thresholds to disclose their AI-related carbon and water footprint. These efforts signal that transparency and possibly limits or standards on AI’s environmental impact could become part of compliance. Organizations should stay abreast of such developments – for instance, requirements to perform an “AI environmental impact assessment” or include AI energy data in reports could emerge as part of AI governance regulations or updates to data center regulations.
- Corporate ESG Reporting: Even before any AI-specific law kicks in, many organizations are effectively regulated by stakeholder expectations through ESG (Environmental, Social, Governance) reporting. Investors and consumers increasingly demand disclosure of how companies are addressing climate change. In frameworks like the Global Reporting Initiative (GRI) or sustainability indices, companies often report their total energy consumption, renewable energy mix, and carbon emissions. If AI-driven activities form a significant part of operations, they will contribute to those numbers. For example, if a tech company dramatically increases compute for AI R&D, its Scope 2 electricity use may spike – something that must be reported and explained in sustainability reports. Thus, companies have a self-interest to manage AI’s footprint to keep their ESG metrics favorable. We are also seeing the inclusion of AI-related questions in sustainability audits: e.g. a data center provider might be asked by enterprise clients, “How do you ensure AI workloads in your facility are powered sustainably?” This ties into procurement as mentioned earlier. Furthermore, climate-conscious investors might inquire about how efficient a company’s AI strategy is, given the publicity around AI’s carbon footprint. All of this means that robust AI environmental governance is increasingly part of good corporate governance. Companies might integrate their AI environmental impact into their annual CSR (Corporate Social Responsibility) reports, showcasing initiatives like “we avoided X tons of CO₂ by optimizing our AI models” as positive achievements.
- Liability and Risk Management: From a compliance perspective, one should not overlook the risk of reputational or even legal liability. If a company’s AI project is found to be egregiously energy-inefficient or wasteful when better alternatives existed, it could face backlash or fail internal compliance checks. In the future, if carbon costs are internalized (through carbon taxes or cap-and-trade systems), an AI product that requires excessive compute might incur direct financial costs for the emissions it causes. Organizations should incorporate these considerations into risk assessments: Environmental impact is a material risk (both in terms of regulatory compliance and business continuity in a carbon-constrained world). ISO 42001’s risk management process encourages organizations to evaluate such risks – meaning a compliant AI Management System would include analysis of how environmental factors (e.g. energy price changes, carbon regulations) could affect AI system operation, and vice versa.
In summary, environmental impact and AI governance are converging. Forward-looking organizations are treating compliance with environmental standards as an integral part of AI deployment. This includes adhering to any current laws on energy use and e-waste, preparing to meet new transparency requirements regarding AI’s carbon footprint, and voluntarily aligning AI projects with global sustainability goals. By doing so, organizations not only reduce risk but often find efficiencies and innovation opportunities. They position themselves as responsible AI leaders – using AI to drive progress while safeguarding the environment, fully in line with the intent of ISO 42001’s Annex C on Environmental Impact.
C.2.5 Fairness
Fairness means ensuring AI outcomes are equitable and free from unjust bias or discrimination. In AI governance, this objective is crucial to prevent the system from systematically disadvantaging any group. Fairness encompasses equality and equity – AI decisions (like hiring recommendations, loan approvals, or criminal risk scores) should not reflect prejudices in data or design. Addressing fairness requires identifying and mitigating biases in training data, algorithms, and outputs so that the AI’s behavior aligns with ethical and legal standards of non-discrimination.
Real-World Examples
A well-known case is Amazon’s experimental AI hiring tool, which was found to discriminate against women. The model had learned from past résumés (mostly from male candidates) and began downgrading CVs that included the word “women’s,” among other biased patterns. Amazon had to scrap this AI system once the bias was discovered. Another example is image recognition software misidentifying individuals due to biased training data – famously, in 2015 Google Photos auto-tagged black individuals as “gorillas,” a shocking failure that drew attention to bias in AI algorithms. These incidents show how unfair AI systems can amplify discrimination at scale, harming certain groups and causing public backlash.
Implications for Organizations: Unfair AI can lead to legal liabilities (e.g. discrimination lawsuits or regulatory penalties), reputational damage, and loss of trust among customers and the public. Ensuring fairness means organizations must be proactive: include fairness as a key requirement in AI projects, and continuously assess AI outcomes for disparate impacts. In practice, this involves engaging diverse stakeholders in development, testing with various demographic data, and being prepared to adjust or disable AI systems that exhibit bias. Not addressing fairness can also mean missing out on the full benefits of AI – biased systems often perform suboptimally and “reduce AI’s potential” by alienating segments of users.
Best Practices
To integrate the fairness objective, organizations should implement bias management processes. This can include: conducting bias audits and ethical impact assessments for AI models, using techniques like bias metrics or disparate impact analysis on model outcomes, and improving training data representativeness (ensuring data isn’t skewed against any group). It’s also wise to set up governance structures like an AI ethics committee to review high-stakes AI decisions for fairness. Regular monitoring is key – for example, checking whether an AI’s decisions (hiring recommendations, loan rates, etc.) show any systematic bias against protected groups, and retraining or refining the model as needed. As NIST notes, managing fairness may involve trade-offs (e.g. between predictive accuracy and bias mitigation), so governance should include deliberation on these trade-offs in a transparent, principled way. Finally, clear accountability for fairness should be assigned (e.g. designating a responsible AI officer to oversee ethical compliance).
Connections to ISO/IEC 23894: The risk management guidance in ISO/IEC 23894 highlights bias as a major AI risk to address as part of fairness. ISO/IEC 23894’s Annex A explicitly lists fairness alongside safety, security, etc., as common objectives for AI risk management. It provides context on identifying bias (e.g. defining fairness criteria and what constitutes bias in an AI system) and suggests controls to manage it. Organizations implementing ISO 42001 can look to ISO 23894 for examples of effective bias mitigation throughout the AI lifecycle – for instance, it stresses involving domain experts and affected groups in defining fairness metrics. This alignment ensures that the fairness objective in an AI management system is supported by a robust risk assessment process for bias-related risks.
C.2.6 Maintainability
Maintainability refers to the ease with which an AI system can be kept up-to-date, fixed, and adapted over time. AI systems aren’t “fire and forget” – they require ongoing maintenance, such as model updates (retraining with new data), software patches for the code integrating the model, and recalibration as objectives or environments change. A maintainable AI system is one built with good software engineering practices (modularity, version control, documentation), and with operational processes for regular review and improvement. This objective recognizes that AI models can degrade (data drift), or new findings might necessitate changing the model (perhaps a new fairness metric emerges that you want to incorporate). If maintainability is poor – say the original development team leaves and no one else can understand the model – the system might become a black box that the organization is stuck with, afraid to change. That can lead to accumulating technical debt in AI, where future changes are increasingly costly or risky. Maintainability also means the AI can be efficiently tested and validated whenever changes are made (like deploying a new model version). Essentially, it’s about treating the AI lifecycle as continuous, not one-shot: ensuring the system can evolve safely and effectively. Good maintainability supports the continuous improvement ethos inherent in ISO management systems.
Real-World Examples
Many early AI projects in companies have failed or been abandoned due to maintainability issues. For example, a bank might develop a complex credit risk model with an external vendor; if the vendor contract ends or key data scientists leave, the bank might find itself with a model no one fully understands or can update – a maintainability crisis. A specific scenario: Netflix famously ran a public competition to improve its recommendation algorithm (the Netflix Prize), but ultimately did not deploy the winning algorithm in production largely because it was too complex to integrate and maintain relative to the business benefit. They opted for simpler, more maintainable approaches. Another anecdote: An e-commerce company had a pricing AI that worked well initially, but over time the market dynamics changed. The data science team that built it had moved on, and the code had little documentation. When the model’s performance started causing lost revenue, the company struggled for months to retrain or adjust it, essentially treating it as a black box. This shows maintainability issues leading to slow response to needed changes. On the flip side, one positive example: LinkedIn has a mature AI platform where they modularize components (like feature extraction, model serving) and maintain a “model zoo.” This standardized approach makes it easier for new engineers to pick up and improve existing models – illustrating good maintainability practices enabling continual improvement (LinkedIn regularly publishes improvements to its recommendation algorithms). Finally, consider regulatory changes: if a new law requires an AI to provide certain explainability or to exclude certain attributes, a maintainable system can be adjusted quickly to comply, whereas an unmaintainable one might force the organization to withdraw the system entirely. For instance, GDPR’s right to be forgotten meant search engine AI had to incorporate new logic – Google’s ability to update their algorithms for this indicates they had the infrastructure and maintainability to do so globally. Smaller companies with less maintainable systems might have had to turn off features if they couldn’t adapt in time.
Implications for Organizations
Poor maintainability can result in higher costs, slower time to respond to issues, and increased risk of failures. If an AI system is hard to maintain, it might not get security patches promptly, leaving vulnerabilities (tying to security objective). If it’s hard to update, it may fall out of alignment with business needs or data reality, leading to inaccurate outputs (risking quality and fairness). Organizations might find themselves in a position where they know an AI model is underperforming or behaving biasedly, but cannot easily fix it – a terrible position in terms of compliance and ethics. This also can breed a dependence on specific personnel or vendors (key-man risk). From a talent perspective, top engineers/data scientists prefer working in environments with modern, maintainable code; if your AI stack is a spaghetti mess of undocumented code, it’s harder to attract or keep talent to work on it. Also, regulators and auditors increasingly ask about not just the model at deployment but how you govern it through its life – being able to show a robust model management process (with maintenance cycles, re-validation, etc.) will inspire confidence. Maintainability also affects scalability: if each new model requires reinventing the wheel, you won’t efficiently scale AI use. Companies that industrialize AI (like with MLOps pipelines) can deploy many models swiftly; those with poor maintainability struggle to move beyond a few experiments. Thus, maintainability is key for future-proofing AI investments and staying agile in a landscape where data, technology, and regulations mature.
Best Practices
To ensure maintainability, adopt good MLOps (Machine Learning Operations) and software engineering practices for AI:
- Modular and reusable components: Build AI systems in a modular way. Separate data preprocessing, model training code, and deployment code. Use standard frameworks and patterns. For example, use a common feature store so that different models share the same well-maintained code for data processing. When models share components, maintenance in one place benefits many systems.
- Version control and reproducibility: Store model code, configuration, and even datasets in version control (like Git). This allows tracking changes over time and rolling back if needed. Also aim for reproducibility – someone else should be able to rerun the training process and get a similar model. This may involve using infrastructure-as-code for environment setup, fixing random seeds for experiments, and saving training data snapshots. When a model can be re-trained from scratch in a documented way, maintainability is high.
- Automated testing: Treat models like code – develop unit tests and integration tests. For instance, test that the data pipeline correctly handles edge cases, test that the model’s outputs on a validation set haven’t drastically changed from one version to the next (except where intended). If you update the model code or features, tests should catch if you broke something (like model now always outputs the same value – a regression). This gives confidence to maintainers that changes won’t silently ruin performance or fairness.
- Continuous integration/continuous deployment (CI/CD) for ML: Set up pipelines that automatically train and deploy models in a controlled manner. This includes validation steps and approvals. With CI/CD, pushing an update (like using a new algorithm) triggers retraining, testing, and can deploy to a staging environment. This automation makes maintenance (updates) less error-prone and faster. It also enforces discipline in how changes are made.
- Monitoring and feedback loops: Maintainability is aided by knowing when maintenance is needed. Implement monitoring for model performance drift (as discussed earlier). If an alert shows accuracy dropping or bias increasing, the team can proactively start maintenance (e.g., gather new training data or adjust hyperparameters). Essentially, use monitoring to schedule maintenance cycles (like “model retrain now” signals).
- Documentation and knowledge sharing: Keep documentation up to date – not just technical docs, but also rationale (why certain choices were made). Encourage the original developers to document assumptions and known limitations. If using complex techniques, include references or explanations in an internal wiki. For knowledge sharing, do code reviews (so multiple people understand the code) and pair programming occasionally. Rotate maintenance duties among team members so knowledge isn’t siloed.
- Simplify when possible: There’s a saying in engineering: “build the simplest thing that achieves the objective.” Overly complex models might slightly increase accuracy but at a cost to maintainability. Evaluate that trade-off. Sometimes using a simpler model or pipeline can drastically ease maintenance with minimal impact on results. Also, periodically refactor – if a system has grown unwieldy, invest time to clean up and simplify it. This prevents accruing too much technical debt.
- Lifecycle management: Plan the full lifecycle – from deployment to eventual retirement. If an AI model should be retrained every 3 months, put that on the calendar and allocate resources. If a model becomes obsolete (say, replaced by a new one), have a process to retire it cleanly (removing it from production, archiving its data, etc.). This kind of planned maintenance ensures you don’t have orphaned models running unattended.
By applying these practices, organizations treat AI systems like long-term products rather than one-off projects. This yields benefits such as easier onboarding of new team members (because they can get environments running quickly, understand code structure, etc.), quicker iteration (because pipelines and tests support change), and more reliable improvements (because you can safely try enhancements knowing you can validate them).
Connections to ISO/IEC 23894
ISO 23894’s risk management approach inherently considers lifecycle issues as a source of risk. It explicitly lists “system life cycle issues” as a risk source, indicating recognition that if you don’t manage the AI throughout its life, things can go wrong (e.g., model becomes outdated or incompatible). The standard likely recommends that organizations include maintenance and end-of-life in their risk assessments. For example, “What is the risk if we don’t update the model regularly?” – answer: performance may degrade and cause bad decisions. By highlighting that, ISO 23894 nudges organizations to allocate responsibility and processes for maintenance. It also probably aligns with existing system engineering standards on maintainability. Another insight from ISO 23894 is the idea of continual improvement (a principle from ISO management systems): it encourages learning from experience and improving processes. So, if maintenance of an AI system was problematic, ISO 23894 would suggest adjusting your framework (maybe improving documentation, or investing in better tools) as part of iterative improvement. In combination with ISO 42001, which requires organizations to plan for achieving objectives and to manage changes, ISO 23894 provides concrete guidance on how to implement a maintenance regime. It might mention having a model maintenance schedule or conducting periodic risk re-assessments for AI systems (which inherently brings up, “has anything changed? do we need to update the model or controls?”). Additionally, ISO 23894 references the AI system life cycle in Annex C, giving an example mapping – this would illustrate where maintenance (updates, monitoring, end-of-life) fits into the overall process of managing AI risk. By following that, an organization can systematically ensure maintainability. Essentially, ISO 23894 supports the maintainability objective by reminding that AI risk management doesn’t stop at deployment – it’s an ongoing process and offers best practices to integrate AI into your organization’s maintenance and improvement cycles.
C.2.7 Privacy
The privacy objective focuses on protecting personal data and respecting individuals’ privacy rights in the context of AI systems. AI often relies on large datasets, which may include sensitive personal information (e.g. patient records, user behavior logs, faces in images). Without proper safeguards, AI can become a vehicle for privacy invasions – by processing data in unauthorized ways, leaking personal information, or inferencing sensitive attributes about people. Privacy in AI governance means ensuring compliance with data protection laws (like GDPR, CCPA) and ethical norms in how data is collected, used, stored, and shared by AI systems. It also extends to concepts like data minimization (using the least data necessary), purpose limitation (using data only for stated purposes), and preserving anonymity when possible. With AI’s capability to re-identify or profile individuals, organizations must be extra cautious that their AI’s power is not misused to erode privacy.
Real-World Examples
A notorious example is Clearview AI, a company that built a facial recognition AI by scraping billions of images from social media and the internet without consent. Clearview’s database of faces (over 3 billion images) was used to identify individuals for law enforcement. This sparked global outrage and legal action – in 2024, the Dutch Data Protection Authority fined Clearview €30 million for GDPR violations, calling its mass collection of faces “illegal” and “highly intrusive”. Regulators warned that you “cannot simply unleash [facial recognition] on anyone in the world”. This case shows how AI capabilities (facial recognition at scale) can clash with privacy principles, and authorities are actively enforcing against such abuses. Another example: voice assistants (like Amazon Alexa or Google Assistant) have accidentally recorded private conversations and even sent those recordings to third parties, due to AI misactivation. One widely reported incident involved Alexa mistakenly sending a family’s private conversation to a random contact – a clear privacy breach and AI error. Additionally, targeted advertising AI has raised privacy concerns: Facebook’s algorithms, for instance, allow micro-targeting using personal data, which led to incidents like the Cambridge Analytica scandal where data on millions of users was harvested and used to influence elections. That scandal underscored how AI-driven profiling without user knowledge is a serious privacy issue. These examples illustrate that loss of privacy can occur in many ways – through the AI’s training data (Clearview), through AI’s operation and data logging (Alexa), or through AI’s inferential power (profiling sensitive traits).
Implications for Organizations
Breaching privacy can result in heavy fines, legal sanctions, and loss of customer trust. GDPR and other regulations have teeth – e.g., fines up to 4% of global turnover for serious violations. Beyond legal risk, users are increasingly privacy-conscious; an AI product perceived as “creepy” or invasive may face public backlash or market rejection. Thus, organizations need to bake privacy considerations (“privacy by design”) into their AI systems. This includes being transparent about data usage and giving users control where appropriate. If implementing ISO 42001, an organization is likely already aware of data protection obligations, but AI can introduce new challenges (like a model inadvertently memorizing personal data from training set and outputting it later, as happened with some early large language models). There’s also a risk of cross-border data issues – AI services often operate in the cloud, so data may flow internationally, triggering compliance needs (as seen with EU vs US data transfers). For employee data and customer data alike, trust is paramount: if people fear an AI is surveilling them or misusing their data, they won’t adopt it.
Best Practices
Achieving the privacy objective involves applying strong data governance and technical controls:
- Data inventory and minimization: Catalog all personal data used in AI projects and ensure each data element has a justified purpose. Avoid collecting or retaining data that isn’t needed for the AI’s function. For example, if age or gender isn’t necessary for a model’s performance, don’t include it in the dataset. This reduces risk exposure.
- Consent and transparency: Obtain informed consent from individuals when using their data for AI (unless you have another lawful basis). Be clear in privacy notices about AI processing (e.g. “Your data will be used to train a recommendation algorithm…”). If using data in new ways (secondary use), seek additional consent or anonymize the data. Transparency also means allow users to inquire or opt out of certain AI-driven decisions when feasible.
- Anonymization/Pseudonymization: Where possible, use anonymized data to train AI. Techniques like removing identifiers, aggregation, or differential privacy can allow AI to learn patterns without directly handling personal identifiers. Note, however, that truly anonymizing high-dimensional data is hard; governance should consider the risk of re-identification (AI can sometimes piece together identities from seemingly anonymous data).
- Access control and encryption: Restrict access to personal data within the organization (only the AI engineers who need it should handle raw data). Use encryption for data at rest and in transit, especially if data moves to cloud ML services. If using cloud AI providers, scrutinize their privacy and security measures – ensure no unintended sharing or ownership transfer of your data or models.
- Privacy-preserving ML techniques: Consider adopting techniques like federated learning (where raw data stays on users’ devices and only model updates are aggregated centrally) or encrypted computation (homomorphic encryption or secure enclaves) for sensitive data. These can allow building AI models without directly seeing all the raw personal data centrally. For instance, a healthcare consortium could train a joint AI model on patient data from multiple hospitals without the data ever leaving each hospital.
- Testing for privacy leaks: Just as one tests models for accuracy, test them for privacy. Language models have been found to sometimes regurgitate parts of their training data. One best practice is to prompt your model with queries to see if it reveals any personal info it shouldn’t (white-hat hacking for privacy). If it does, retrain with stricter data handling or remove problematic records.
- Compliance checks and documentation: Align your AI data practices with standards like ISO/IEC 27701 (privacy information management). Maintain documentation for regulatory compliance – e.g. records of processing, Data Protection Impact Assessments (DPIAs) specifically analyzing AI use cases as required by GDPR for high-risk processing. An AI system making automated decisions that significantly affect individuals might trigger legal rights (like GDPR Art.22) for human review, so be prepared to provide explanations or human intervention when individuals exercise those rights.
By following such practices, organizations can mitigate privacy risks. For example, after the uproar over Google Photos’ mislabeling incident, Google reportedly removed certain sensitive labels entirely and increased manual review, implicitly prioritizing privacy and ethics over a fully automated approach. Another example: Apple has tried to differentiate itself by doing more AI “on-device” (like facial recognition for unlocking phones) so that personal data stays local rather than on cloud servers – an architectural decision in favor of privacy.
Connections to ISO/IEC 23894
ISO/IEC 23894 underlines privacy as a key consideration in AI risk management, often linking it with ethical and societal impacts. It encourages organizations to incorporate privacy risk assessment into the AI lifecycle. For instance, if an AI system uses personal data, ISO 23894 would prompt the risk assessor to consider compliance risk, potential harm from data misuse, and controls needed (similar to a DPIA). The standard likely references ISO 27701 and other privacy guidelines, bridging them with AI management. Additionally, ISO 23894’s guidance on risk sources includes things like data quality and integrity – this is related to privacy because poor data governance can lead to both privacy breaches and flawed models. By using ISO 23894, organizations get examples of effective privacy controls in AI contexts (perhaps case studies of anonymization or federated learning in Annex C or the body text). It provides an international perspective on balancing data utility with privacy protection. Moreover, ISO 23894 reminds us that privacy isn’t just a legal duty but tied to human rights and ethical AI – it explicitly frames AI risks in terms of impacts on human rights and freedoms. So in conjunction with ISO 42001, it helps organizations go beyond checkbox compliance to truly embed privacy-respectful practices as part of AI trustworthiness objectives.
C.2.8 Robustness
Robustness refers to the AI system’s ability to behave reliably under a variety of conditions, including when facing errors, exceptions, or novel situations. A robust AI should handle noise or perturbations in input data, resist being easily fooled, and maintain performance even when operating circumstances change (within reason). It also implies that when the system does fail, it does so gracefully (e.g. not in a catastrophic or unpredictable manner). Robustness is crucial for trust – stakeholders need confidence that the AI won’t “break” when it encounters slight deviations from its training examples or malicious attempts to disrupt it. This objective overlaps with safety and security: a robust model is less likely to produce unsafe actions or be tricked by adversaries. However, even benign variations like sensor noise, missing data, or shifts in the environment (what’s called concept drift or distribution shift in ML) can degrade an AI if it’s not robust. Therefore, robustness in AI governance is about building resilient models and systems that can operate in the messy, dynamic real world. NIST’s AI framework captures this under attributes like reliability and resilience, noting that AI must perform as required without failure for a given period and withstand unexpected changes.
Real-World Examples
Adversarial examples are classic tests of robustness. For instance, a slight pixel-level modification to an image (imperceptible to humans) caused an AI vision model to misclassify a stop sign as a speed limit sign. This indicates a lack of robustness to small input perturbations. In one experiment, researchers placed small stickers on a stop sign and an otherwise high-performing image recognition AI consistently read it as a different sign. In another case, simply rotating or adding minor noise to images caused AI classifiers’ accuracy to plummet, even though humans could still recognize the objects easily. Outside of vision, consider voice recognition: speaking with an uncommon accent or in a noisy room might confuse a voice assistant – early voice AI systems struggled with accents or background noise, which is a robustness issue (they weren’t generalized enough). Another example of robustness (or lack thereof) is how AI chatbots or language models can produce nonsense or “hallucinations” when given inputs outside their training distribution. For instance, initial versions of GPT-3 sometimes gave obviously false statements or arithmetic errors – not because of malicious input, but because certain queries were effectively outside the scenarios it robustly handles. Model drift over time is another robustness challenge: a predictive model for retail demand might work well this year, but if consumer behavior changes next year (say, due to a pandemic or trend shift), the model’s predictions may become very wrong unless retrained – this happened during COVID-19, when many AI prediction systems failed as the world deviated wildly from historical patterns. These examples show that achieving robustness is non-trivial; AI that seems accurate in controlled tests can falter in real use due to unanticipated inputs or conditions.
Implications for Organizations
A lack of robustness can lead to system failures, poor decisions, and vulnerability to manipulation. If an AI fraud detection system is not robust, fraudsters might easily find input patterns that evade detection. If an autonomous drone’s vision is not robust to lighting changes, it might crash when the sun angle changes. For organizations, this means potential costs from system downtime or malfunctions, safety incidents, or exploitation by malicious actors. It also affects user experience – a non-robust AI might frustrate users with erratic behavior (e.g. a chatbot that gives bizarre answers damages a company’s image). In critical applications, regulators or clients may require evidence of robustness (e.g. rigorous testing results). Failing to ensure robustness could halt an AI deployment if, for example, validation shows the model breaks on slightly noisy data. Additionally, robustness relates to maintainability – a robust system might be easier to maintain because it’s less sensitive to minor changes in environment or data. In contrast, a brittle system could require constant tweaking. Therefore, investing in robustness up front can save organizations from crises and expensive fixes later.
Best Practices
To enhance robustness, organizations can adopt several strategies:
- Diverse and extensive testing: Go beyond the “happy path” and test AI models on diverse inputs, including edge cases and stress conditions. For image AI, include various rotations, scales, backgrounds, etc. For an NLP model, test on misspellings, slang, code-mixed language. Create adversarial examples (if feasible) or use open-source adversarial attack tools to see how the model holds up. The goal is to identify brittle points before deployment.
- Adversarial training and data augmentation: One defense against adversarial or noisy inputs is to train the model with more variety. Data augmentation (randomly perturbing inputs during training – e.g. flipping images, adding noise) can make the model more invariant to those changes. Adversarial training explicitly includes some adversarial examples in the training set so the model learns to resist them. For example, an OCR AI might be trained on images with various distortions so it learns to read text even if the image is somewhat warped.
- Robust model architectures: Choose algorithms known for better robustness. Simpler models or those with built-in constraints can sometimes be more robust (there’s a trade-off with complexity/accuracy). Ensemble models (combining multiple models’ outputs) can improve robustness if each model has different failure modes. Also, incorporate validation checks within the system – e.g. a secondary rule-based check that flags if the AI’s output is outlandish (a sanity check layer).
- Graceful degradation: Design the system such that if the AI is uncertain or the inputs are far from what it knows, it either refrains from acting or calls for human assistance. For instance, a medical AI can have a threshold: if an X-ray image is very different from its training distribution, it could say “uncertain – refer to radiologist” rather than giving a possibly wrong diagnosis. This way the system doesn’t produce highly erratic outputs in unknown scenarios.
- Continuous monitoring and retraining: Robustness isn’t a one-and-done deal; it requires maintaining. Monitor the AI in production to detect distribution shifts – if new kinds of data are coming in (e.g. new slang on a social media platform the AI monitors), retrain or update the model to include those. Some organizations set up automated pipelines to periodically retrain models on fresh data, thereby adapting to change. Also monitor performance metrics: if they start degrading, that’s a sign robustness might be faltering due to something new.
- Validation in real conditions: If possible, pilot the AI in a controlled real-world environment before full rollout. For example, test a few autonomous cars on real roads with safety drivers, or A/B test a recommendation algorithm on a small user subset. Real-world use often reveals robustness issues that lab tests miss. Use the pilot to gather data on failure cases and improve the model.
- Documentation of boundaries: Clearly document the known limits of the AI. Developers and users should know the conditions under which the AI has been tested to be reliable. For instance, an AI may be robust for inputs within a certain range (like blood pressure values in a normal human range) but not outside it. By documenting this, you ensure the system is only used where it’s robust, or users know to be cautious beyond that.
In summary, treat robustness as an engineering requirement akin to durability in a physical product. It may require extra effort and computing resources (e.g. generating adversarial examples or running large test suites), but it pays off by preventing failures. A robust AI coupled with a plan for the unexpected will maintain integrity even when conditions aren’t perfect.
Connections to ISO/IEC 23894
ISO 23894 emphasizes technical robustness as a cornerstone of AI risk management. It likely lists “technical robustness and resilience” as an objective in line with other frameworks (similar to EU’s Trustworthy AI and NIST’s attributes). In its discussion of risk sources, ISO 23894 specifically calls out things like complexity of the IT environment and ML-specific risks (e.g. overfitting, adversarial examples), which directly relate to robustness. The standard provides detailed guidance on identifying these risk sources – for example, noting that the dynamic and complex environments AI operates in can produce a wide range of situations the AI must handle. It suggests that organizations need to factor in “the range of potential situations an AI system can face while in operation” when managing risk– essentially advising on robustness. ISO 23894 also bridges to reliability engineering by referencing best practices (it might, for instance, mention redundancy or the importance of validation data). In using ISO 23894 with ISO 42001, an organization would be guided to integrate robustness checks into their risk assessment (e.g. “what if input data is corrupted?”), and it would find internationally vetted controls to strengthen robustness. For example, ISO 23894 might reference adversarial training as a control or stress testing as part of risk treatment, giving implementers concrete actions. Therefore, ISO 23894 provides the “how” to achieve robustness that ISO 42001 requires: it frames robustness in the language of risk (likelihood of model failure under X condition and impact Y) and helps organizations prioritize and address those risks systematically.
C.2.9 Safety
Safety is about preventing physical or psychological harm that could be caused by AI system behavior. This objective is especially critical for AI that controls systems in the physical world (e.g. autonomous vehicles, medical devices, industrial robots) or that makes decisions affecting human welfare (e.g. healthcare diagnostics or emergency response systems). Ensuring safety means the AI should operate within well-defined bounds and fail gracefully (or revert to human control) if it encounters a situation outside its scope. It also means anticipating how misuse or malfunctions could lead to harm. Safety overlaps with robustness and security but specifically focuses on hazard prevention – making sure the AI doesn’t accidentally or intentionally cause injury, damage, or unsafe conditions. In AI governance, safety is fundamental to trust: users and regulators need confidence that AI will not endanger lives or property.
Real-World Examples
One dramatic example underscoring AI safety is the case of IBM Watson for Oncology. Watson, an AI system designed to recommend cancer treatments, was found in some instances to give “unsafe or incorrect” treatment advice. Internal documents revealed that the system, trained on hypothetical data, sometimes suggested treatments that doctors deemed likely to harm patients. This not only eroded trust but could have been dangerous if used without human oversight. Another high-profile example is the 2018 Uber self-driving car crash in Tempe, Arizona. Uber’s experimental autonomous vehicle struck and killed a pedestrian. Investigations found the AI’s object recognition system detected the person but did not correctly classify her or plan a safe stop in time. The tragedy sparked debate about whether the technology was deployed unsafely and who was accountable (the safety driver or the company). It highlighted that immature AI can pose direct safety risks on the road. Similarly, Tesla’s Autopilot (a driver-assist AI) has been involved in crashes where the system did not recognize obstacles or disengaged too late – for instance, an Autopilot failure in 2016 led to a fatal crash when the AI didn’t “see” a white truck against a bright sky. These cases illustrate how AI errors or blind spots can translate into real-world harm. Even outside of physical systems, consider content recommendation AIs that inadvertently promote dangerous challenges or misinformation – they can indirectly put people in harm’s way. Thus, safety is a broad concern, from “no harm” principles in AI ethics to concrete functional safety in engineering.
Implications for Organizations
Unsafe AI can have catastrophic consequences – loss of life or severe injuries will result in legal action, regulatory bans, and irreparable reputational damage. Even “near misses” erode stakeholder confidence. Therefore, organizations must integrate safety considerations from the very start (design phase) and treat AI with the same rigor as they would other safety-critical systems. There may also be industry-specific regulations: e.g. the FDA will scrutinize AI in medical devices, aviation authorities will regulate autonomous drones, etc. Non-compliance can stop a product from going to market. Organizations implementing AI should perform thorough risk assessments for potential harms (“What’s the worst case if this AI goes wrong?”) and incorporate human oversight in high-risk operations. Importantly, clear accountability must be established for safety (more on that in Accountability objective). A safety incident involving AI could also set back AI adoption across the whole industry due to public fear, so each organization’s practices contribute to broader societal trust in AI.
Best Practices
To achieve safety, organizations can borrow from systems safety engineering approaches and adapt them to AI:
- Hazard identification and analysis: Before deployment, systematically identify how the AI could cause harm. Use techniques like Failure Mode and Effects Analysis (FMEA) or hazard and operability studies (HAZOP) but include AI-specific failure modes (e.g. misclassification of critical objects, extreme out-of-distribution outputs). For example, in an autonomous driving AI, list hazards like “fails to detect pedestrian”, “emergency stop fails to trigger”, etc., and address each.
- Safe design and testing: Implement safety constraints in the AI’s design. This could mean adding rules or guardrails that override the AI if it proposes an action that violates safety (for instance, an autonomous robot that will not exert more than a certain force, even if the AI policy says to). Testing should include extensive simulations of rare or dangerous scenarios. For an AI medical diagnosis system, test it on edge cases and ensure it flags uncertainty or defers to doctors when out of scope.
- Human-in-the-loop / human-on-the-loop: Especially during initial deployment, keep a human supervisor in the loop for critical decisions. A human pilot or driver should be able to take control from an AI autopilot; a doctor should review AI-generated treatment plans before they’re applied. Design interfaces that make it easy for humans to understand when the AI might be faltering (e.g. alerts when the AI has low confidence or when sensor anomalies are detected).
- Redundancy and fail-safes: Don’t rely on a single input or component for safety. The Boeing 737 MAX case is instructive: MCAS (an automated system) relied on one sensor and became dangerous when that sensor was faulty. The fix was to use multiple sensors and give pilots more control. Similarly, AI systems should have redundant sensors or checks. If an AI in a factory thinks a situation is safe but a simpler rule-based system disagrees, it should err on the side of caution (fail-safe state).
- Monitoring and incident response: Once deployed, continuously monitor the AI’s performance in the field for any near misses or anomalies. Establish an incident reporting system for AI (like how aviation has incident reports) to learn from mistakes that didn’t result in harm. And have the ability to issue updates or recalls for AI models if a safety issue is discovered (just as you would recall a faulty product).
- Training and culture: Train employees and end-users on the limitations of the AI. In many crashes, part of the fault was human operators over-trusting the AI. Make sure users know what the AI can and cannot do reliably, so they remain vigilant. Cultivating a safety culture means encouraging team members to question AI decisions and not blindly defer to automation – “trust but verify.”
Regulatory frameworks are also emerging (e.g. the EU AI Act classifies “high-risk AI” which will have strict safety obligations). Adopting ISO 42001 helps demonstrate an organization is systematically managing AI safety. Adherence to related standards like ISO 61508 (functional safety) or industry-specific safety standards can be mapped to AI contexts as well.
Connections to ISO/IEC 23894
ISO/IEC 23894 gives guidance on assessing AI-related safety risks and integrating with general risk management. It references ISO Guide 51’s definition of risk as harm probability & severity, showing alignment with classical safety risk thinking. Annex B of ISO 23894 likely enumerates “safety risk sources” such as technology immaturity or complexity (which can lead to unsafe behavior). One valuable insight from ISO 23894 is its mapping of AI risk to the AI system lifecycle (Annex C). For safety, this means it encourages organizations to consider safety at each lifecycle stage – from data acquisition (ensure data doesn’t omit critical rare events) to model design (ensure it meets safety requirements) to deployment (monitor real-world performance). ISO 23894, being a guidance document, may also provide examples of risk treatment for safety: e.g. case studies of how a healthcare AI company managed patient safety risk by extensive clinical validation. By following ISO 23894 alongside ISO 42001, organizations can ensure that safety objectives are not just set, but actively achieved through risk-informed controls and continuous improvement. In summary, ISO 23894 deepens the treatment of safety by showing how to identify hazards, assess risks, and implement controls in a structured way.
C.2.10 Security
Security in the AI context refers to protecting AI systems from unauthorized access, malicious attacks, and data breaches. AI systems often introduce new security challenges: they might expose additional attack surfaces (e.g. machine learning model parameters or APIs), handle sensitive data, or make automated decisions that attackers may seek to manipulate. Thus, the security objective is about ensuring confidentiality, integrity, and availability of AI systems and their data. This includes guarding against traditional cybersecurity threats and AI-specific threats like adversarial attacks (inputs designed to fool the model) and data poisoning (tampering with training data). A secure AI is one that resists manipulation and theft – both of the model itself and the data it processes. Achieving this is vital for AI governance because an insecure AI can undermine all other objectives (for example, a safety or fairness measure can be nullified by a successful attack).
Real-World Examples
There have been striking demonstrations of adversarial attacks on AI, underscoring the security risks. For example, researchers at Duke University hacked an autonomous vehicle’s AI-based radar, making the car’s system hallucinate phantom cars that weren’t there. In a scenario where such an attack were carried out maliciously, the car could take unsafe actions (swerving or braking unnecessarily), potentially causing accidents. This shows how AI vulnerabilities can translate into physical danger. Another example: adversarial patches on traffic signs – researchers showed that placing innocuous-looking stickers on a stop sign could cause a computer vision model to misread it as a speed-limit sign. In effect, an attacker could trick an AI driver-assistance system into ignoring a stop sign, a serious safety hazard. Beyond adversarial AI, AI systems are targets for data breaches as well. Consider large language model APIs (like a cloud AI service): if not secured, an attacker might exfiltrate confidential data or steal the model (through model extraction attacks). These examples illustrate that AI security is not hypothetical – threat actors are actively probing AI systems to exploit weaknesses, and even benign errors (bugs) can expose AI systems to compromise.
Implications for Organizations
If an AI system is compromised, the consequences can range from financial loss and IP theft (e.g. a stolen model or algorithm) to safety incidents and compliance violations (think of privacy breaches). For instance, an attacker who manipulates an AI that manages sensitive decisions (like credit scoring or medical diagnoses) could cause harmful outcomes for individuals and liability for the organization. Moreover, a data breach involving AI (such as exposing personal data used by the AI) can trigger regulatory penalties under laws like GDPR. Organizations must treat AI systems as critical assets within their information security management. An insecure AI undermines trust – users will be reluctant to adopt AI-driven services if they fear those are easily hacked or leak data. Therefore, integrating robust security controls into every phase of AI development and deployment is essential.
Best Practices
To fulfill the security objective, organizations should apply both traditional IT security and AI-specific safeguards. Best practices include:
- Securing the AI supply chain: ensure that machine learning libraries, pre-trained models, and third-party AI services are from trusted sources and up-to-date (to avoid known vulnerabilities).
- Implementing access controls and encryption for AI models and datasets, just as one would for sensitive databases. Limit who can access training data, model parameters, and output in production.
- Conducting threat modeling for AI systems: Identify how an adversary might attack (e.g. feeding malicious input, tampering with data pipelines) and build controls against those methods. For example, if the AI is public-facing (like a chatbot), rate-limit inputs and use anomaly detection to spot adversarial patterns.
- Adversarial testing and red-teaming: Before deployment, test the AI with adversarial examples to gauge its robustness. Some organizations hire “red teams” to actively try to break their AI systems – revealing weaknesses that can be fixed (similar to penetration testing for software).
- Ensuring end-to-end security: If an AI is part of a larger system, secure the environment (servers, networks, sensors). A complex AI system might fail if a sensor is hacked or if the data pipeline is compromised. So, for an AI-based sensor system, one might add encryption/authentication on sensor data and fail-safes if data looks anomalous.
- Maintain monitoring and incident response for AI: Logging the AI’s inputs and outputs can help detect if it’s under attack (e.g. a sudden spike in bizarre inputs). Have a plan to quickly patch or shut down an AI model if a new vulnerability is discovered.
By integrating these measures, an organization can mitigate risks like data poisoning or model theft. For example, Facebook reportedly “watermarks” and monitors its AI models to detect if someone is trying to steal them via repeated queries. Organizations should also align their AI security with existing standards – ISO 27001 (information security) and NIST cybersecurity framework practices can be extended to AI contexts. This might involve updating security policies to explicitly cover AI assets and training security teams about AI-specific issues.
Connections to ISO/IEC 23894
ISO/IEC 23894 provides deeper insight into AI security risks by detailing AI-specific risk sources related to security (many of which overlap with general IT security). It notes that while AI shares some risks with traditional software, new threats (like adversarial inputs) require special attention. The standard encourages using ISO 31000 risk management principles to tackle these – for security, that means systematically identifying threats, evaluating their likelihood/impact, and treating them (through controls as above). For instance, ISO 23894 might guide an organization to consider the level of autonomy and complexity (risk factors that can exacerbate security issues) when analyzing vulnerabilities. It also stresses integration of AI risk management into broader enterprise risk management, which means security governance for AI should not be siloed. In summary, ISO 23894 reinforces that security is a paramount objective and provides examples (in Annex B or case studies) of managing adversarial risk, thereby complementing ISO 42001’s requirements with practical guidance.
C.2.11 Transparency and explainability
Transparency and explainability refer to making the AI system’s workings understandable and open to stakeholders. Transparency can mean access to information about the AI – such as its purpose, training data, algorithms, and decision logic – and explainability usually means the ability to provide meaningful explanations for specific outputs or decisions of the AI (especially to those affected by them). These concepts are crucial in AI governance as they enable accountability, trust, and compliance. If an AI is a “black box” that even its creators struggle to interpret, it’s hard to ensure it’s behaving correctly or to contest its decisions. Explainability is particularly important in regulated domains – e.g., a person denied a loan by an algorithm may have a right to know why. It’s also key for debugging and improvement: understanding why the AI made an error helps fix it. Transparency can be categorized into different levels (to developers, to auditors, to end-users) – for instance, internal transparency for audit trails and external transparency for user communication. Achieving this objective means building AI systems that are not just accurate, but also intelligible and open enough to be scrutinized. This ties directly to ethical principles of respect for users and trustworthiness – people tend to trust a system more if they can comprehend its rationale or at least trust that someone can audit it.
Real-World Examples
A telling example comes from healthcare: Many doctors are wary of AI diagnostic tools that operate as black boxes. In one case, a sepsis detection AI was deployed in hospitals but clinicians often ignored its alerts, partly because it gave no explanation for its predictions. The result was that the AI had little impact on patient outcomes – an example of how non-explainable AI can fail to be adopted on the ground. A broader illustration: the American Medical Association noted that AI’s growth in healthcare “could stall if physicians aren’t told what the technology is doing and how it’s doing it”. This sentiment reflects a general truth: lack of explainability hinders user acceptance. Another example is the Apple Card credit limit controversy in 2019. Apple’s credit card, managed by an AI algorithm at Goldman Sachs, was criticized when several high-profile individuals observed that women (even with similar or better financial credentials) got significantly lower credit limits than their husbands. The algorithm was essentially a black box, and neither Apple nor Goldman could initially provide a clear explanation, simply saying it wasn’t intentionally biased. This opacity led to an investigation by regulators and public distrust – illustrating that when an algorithm’s decisions have big impacts (like creditworthiness), the demand for explainability is high. In the criminal justice system, the COMPAS algorithm used for risk assessment was challenged in the Wisconsin Supreme Court (Loomis case) because the defendant argued he couldn’t challenge the score without knowing how it worked. COMPAS was proprietary (a “trade secret” algorithm), meaning its internal workings were not transparent; the court upheld its use but advised caution. This case, along with ProPublica’s investigation showing COMPAS’s racial bias, fueled calls for transparency in criminal AI tools. Overall, these examples underscore that when AI affects human lives, lack of transparency/explanation leads to pushback – whether from professionals, consumers, or regulators.
Implications for Organizations
If AI systems are not transparent or explainable, organizations face several risks. First, regulatory non-compliance: laws like GDPR already have provisions (the so-called “right to explanation” or at least a right to meaningful information about automated decisions). The upcoming EU AI Act also places transparency obligations on AI, especially high-risk systems (e.g. requiring documentation, user information, etc.). Non-compliance could mean the AI cannot be used legally or heavy fines if it is. Second, operational and legal risk: if a decision is challenged (say, someone sues for discrimination or harm), the organization will need to produce reasoning for that decision. Without explainability, the organization might be unable to defend its AI’s actions in court, or even to detect that something was wrong. Third, reputational risk and user rejection: as seen, customers and partners may distrust AI they don’t understand. For example, an HR department might reject a recruitment AI if it can’t provide clear reasons for rejecting candidates, out of fear it might be unfair. Internally, a lack of transparency can hamper debugging and improvement – engineers may spend enormous time trying to figure out why a model is making odd decisions if it’s a complex black box. On the flip side, building reputation for transparency can be a competitive advantage – e.g., an AI-enabled bank that provides clear loan decision explanations might attract customers over one that gives cryptic rejections. In summary, failing on this objective can lead to misuse, misunderstanding, or mistrust of AI, undermining its benefits.
Best Practices
To promote transparency and explainability, organizations can:
- Documentation and disclosure: Maintain thorough documentation of AI systems – the data sources, how they were collected, the model architecture, training processes, and known limitations. Internally, this creates a knowledge base so that anyone reviewing later (or an auditor/regulator) can follow the trail. Externally, decide what information can be shared: e.g., publish model cards or fact sheets for your AI services that describe in plain language what the model does, what data it was trained on, and appropriate uses. Many companies now produce “AI transparency reports” or at least summaries for customers.
- Explainable AI techniques: Utilize algorithms and methods that provide explanations. This could mean using inherently interpretable models (like decision trees or rule-based systems) when possible, or using post-hoc explanation tools (like SHAP values, LIME, or counterfactual explanations) for more complex models. For example, if you use a neural network for loan decisions, you can implement a system that for each decision outputs the top factors that influenced it (“loan denied because income was below threshold and credit history length was short”). These techniques can often be integrated into the AI pipeline. Researchers are also developing explainable AI dashboards to help humans interact with model reasoning.
- User-friendly explanations: Tailor explanations to the audience. A data scientist might want a detailed feature importance chart, whereas an end-customer wants a simple reason (“You were denied insurance because you have had 3 accidents in the last 5 years, which is above our risk threshold.”). Make sure the explanation is truthful and not misleading – it should reflect what the model actually used. Also, avoid overly technical jargon in end-user explanations. The goal is to empower users and stakeholders to understand decisions enough to accept them or contest them appropriately.
- Transparency in design: Encourage a culture of openness in AI development. For instance, conduct model design reviews where cross-functional teams (including legal/ethics) question how the model works. Open source or peer review your AI components when possible – sometimes having external eyes (academics, third-party auditors) can validate that the system is fair and working as intended. If full open-sourcing isn’t feasible, consider third-party audits: having an independent firm or group examine your AI for bias, fairness, and explainability, and publish a summary report.
- Interactive explanations: In some applications, it’s useful to let users query the system about a decision. For instance, a credit platform might allow a declined applicant to submit additional information or scenarios (“Would a higher income have changed the outcome?”) and the AI (or a hybrid human-AI system) can respond. This kind of interactivity can enhance perceived fairness and understanding. It’s a form of counterfactual explanation (“If X were different, the decision would be Y”), which is often recommended in ethical AI guidelines.
- Limit use of black-box models in high-stakes decisions: If an AI model is completely unexplainable yet very high impact, consider whether it’s appropriate. Sometimes a slightly less accurate but more interpretable model is preferable for accountability. For example, some medical AI projects choose simpler predictive models that doctors can validate, rather than inscrutable deep learning, if it means doctors will trust and use it. It’s about finding the right balance for the context – this principle is echoed in many guidelines (the EU suggests a “right to explanation” in high-risk AI). If a complex model is necessary, then augment it with explainability tools and rigorous validation so that it doesn’t operate as a mysterious oracle.
Organizations should also train their staff on interpreting AI results. It’s one thing to generate an explanation; it’s another for the recipient to understand it. So, part of operational measures could include educating decision recipients (like loan officers, doctors, or customers) on how to interpret model explanations provided to them.
Connections to ISO/IEC 23894
ISO 23894 lists “lack of transparency and explainability” as a key risk source to consider, which directly ties to this objective. The guidance would advise organizations that if an AI is too opaque, that increases risk (e.g. risk of bias undetected, risk of user mistrust). ISO 23894 likely provides examples of how to integrate transparency into the risk management process, maybe suggesting documentation practices or assessment of explainability methods. It also aligns with ISO/IEC 22989 (AI terminology) which defines transparency-related terms. By using ISO 23894, an organization can get a deeper understanding of what types of information about AI should be communicated to stakeholders (perhaps referencing frameworks like the ones from IEEE or EU for algorithmic transparency). Moreover, ISO 23894 emphasizes that transparency enables accountability – one of its risk management principles is the need to have evidence and records for decisions. In fact, ISO 23894’s integration with ISO 31000 means it supports “risk communication”: being transparent about AI risks and decisions is part of effective risk management. So for an ISO 42001 implementer, ISO 23894 serves as a companion that fleshes out how to achieve and evaluate transparency. For instance, it may recommend maintaining an AI risk register that includes for each identified risk the explanation of how the AI might cause it – which is a practice that doubles as documentation and transparency internally. In summary, ISO 23894 provides the playbook for making AI less of a black box: it encourages detailed descriptions of AI systems (Annex C mapping to lifecycle might show where to insert transparency, e.g. during design and testing, ensure traceability of why certain model decisions were made in training). Together, the standards push organizations to prioritize explainability as a first-class requirement, not an afterthought.
ISO 42001 Annex C.3 – Risk Sources
C.3.1 Complexity of environment
The complexity of an AI system’s operating environment refers to how dynamic, unpredictable, and varied the conditions are. In highly complex environments, the range of possible situations is extremely broad, making it hard to anticipate every scenario. This can introduce significant uncertainty in an AI’s performance, since the system may encounter inputs or situations it was never trained or programmed to handle. Unlike a closed, controlled setting, a complex real-world environment (e.g. busy streets or hospitals) presents “open, nonlinear, random, dynamic” conditions with high uncertainty. In such environments, even a well-designed AI might misbehave or fail when faced with rare or unforeseen circumstances. The risk arises because complexity increases the likelihood of edge cases – situations at the fringe of the AI’s competence – which can lead to errors or unsafe outcomes.
Real-World Examples
A classic example is autonomous driving. Self-driving cars must navigate roads with unpredictable traffic patterns, weather changes, pedestrians, and obstacles. The road traffic environment is essentially an open system with countless possible situations, making it “unpredictable and inexhaustible”, which poses a huge challenge for autonomous driving systems. Indeed, autonomous vehicle tests have shown that unusual combinations of events (e.g. a truck ahead partially obscured by glare) can confound the AI, leading to accidents. In healthcare, an AI diagnostic system might perform well in a controlled research lab but struggle in the complexity of a real hospital. For example, a pathology AI trained on ideal laboratory images may not achieve the same accuracy on noisy, varied clinical data – one study noted an AI that matched expert performance in lab settings did not guarantee similar success under actual clinical conditions. This gap occurs because hospitals present diverse patient populations, comorbidities, and unforeseen usage conditions that the AI may not fully understand. Smart city environments are also highly complex: AI systems managing traffic or utilities in a smart city must contend with numerous interconnected factors (vehicles, infrastructure, human behaviors, weather, etc.). A smart traffic control AI might face anomalies like public events or accidents that create patterns it hasn’t seen, potentially leading to gridlock if not properly handled. Each of these scenarios illustrates how operating in a complex environment amplifies risk by exposing AI to unknown unknowns.
An autonomous Lexus RX450h test vehicle (Google/Waymo) operating in the real world. AI systems in open environments like public roads must handle unpredictable events and a wide variety of conditions, which increases risk.
Technical Implications
In complex environments, AI systems require robust generalization and the ability to handle out-of-distribution inputs. If the environment presents conditions outside the AI’s training data or rules, the system may produce erroneous decisions. For instance, an autonomous car’s vision system might misclassify an object if lighting or weather differs greatly from training conditions. Complexity also makes verification and validation difficult – it’s infeasible to test every possible scenario. This uncertainty can impact safety (e.g. an undetected edge case causing a crash), reliability (AI might have inconsistent behavior in new situations), and even security (unexpected inputs could be exploited by malicious actors). Moreover, complex, open-world environments often lead to feedback effects: the AI’s actions change the environment, which in turn creates new situations. This dynamic can lead to emergent behaviors that designers didn’t predict. Overall, the technical challenge is ensuring the AI remains robust under a broad spectrum of conditions.
Risk Mitigation Strategies
To mitigate environment complexity risks, organizations should employ a combination of extensive testing, simulation, and design safeguards. Key strategies include:
- Scenario-Based Testing: Go beyond static test cases by using simulations and real-world trials that cover a wide range of scenarios. For example, autonomous vehicle developers run millions of miles in simulation to expose the AI to rare events (wild animals crossing, unusual driver behavior, etc.). The goal is to achieve greater coverage of possible states, reducing the “unknowns” at deployment.
- Robust Model Design: Use algorithms that can handle noise and variability. Techniques like domain randomization (training on highly varied data) help the AI generalize better to new situations. In robotics and driving, engineers also incorporate adaptive algorithms that can estimate their own uncertainty – if the AI detects high uncertainty (e.g. sensors are confused), it can trigger a safe fallback.
- Human or Fallback Interventions: For complex settings, a human-in-the-loop or fallback system can improve safety. An autonomous drone, for instance, might have a remote pilot on standby or an automatic “safe mode” landing routine if it encounters conditions outside its parameters. This ensures that when the environment overwhelms the AI, it fails safely rather than catastrophically.
- Environment Constraints: Sometimes the best mitigation is limiting the operating domain. Companies may initially deploy AI only in semi-controlled environments. For example, a self-driving shuttle might be limited to a defined route in good weather (geo-fencing and weather-fencing) until the technology matures for broader use. By reducing environmental complexity (at least in early phases), organizations can manage risk while still benefiting from AI.
- Continuous Learning and Monitoring: Complex environments evolve, so AI systems should too. Implement processes to continuously collect performance data in the field and retrain or update the AI to handle new scenarios (while avoiding catastrophic forgetting of previous knowledge). Monitoring systems can flag when the AI encounters a novel scenario or its performance dips, prompting a review or model update. Over time, this adaptive approach expands the range of environments the AI can safely handle.
In summary, dealing with environmental complexity requires acknowledging that complete prediction is impossible. Thus, risk management focuses on making the AI as robust and failsafe as feasible, expanding testing to include as many real-world situations as possible, and planning interventions for the inevitable surprises.
C.3.2 Lack of transparency and explainability
“Why did the AI make that decision?” If this question can’t be answered, it signals a lack of transparency or explainability in the system. Transparency refers to openness about how an AI system works – its mechanisms, data sources, and decision processes are made understandable to stakeholders. Explainability is related, meaning the ability to describe the reasoning behind specific AI outputs in human-understandable terms. These qualities are critical because without them, users and affected persons have no insight into the AI’s behavior. A lack of transparency turns the AI into a “black box”, which can erode trust and make it difficult to detect or correct problems. For instance, if a credit approval AI denies a loan and neither the applicant nor the bank officer can understand why, it’s impossible to know if the decision was fair or if an error occurred. In high-stakes domains – finance, healthcare, criminal justice – unexplainable AI decisions are risky: they may mask biases, prevent accountability, and even violate regulations that require justification of decisions. Transparency is also vital for debugging and improvement; if developers can’t interpret the model’s workings, addressing errors or biases becomes guesswork. In short, explainability is essential for trust, accountability, and effective oversight of AI systems.
Examples of AI Failures from Opaqueness
There have been notable real-world incidents underscoring this risk. One famous case is the COMPAS recidivism prediction algorithm used in US courts to assess defendants’ likelihood of reoffending. This algorithm was proprietary and its inner workings were not disclosed. An investigative report by ProPublica revealed that COMPAS appeared to be biased against black defendants (falsely flagging them as higher risk at disproportionately higher rates). Because the tool lacked transparency – “the company does not publicly disclose the calculations used to arrive at defendants’ risk scores” – neither defendants nor the public could understand or challenge its decisions. This is a stark example of how opacity can hide bias and hinder justice. Another well-known incident is Amazon’s recruiting AI that the company developed to screen resumes. It was later found that the AI was downgrading female applicants – effectively learning a gender bias from historical hiring data. Amazon eventually scrapped this tool. Part of the problem was that the model’s complex machine learning process was not explainable; it wasn’t obvious it was discriminating until engineers noticed the pattern in outputs. The lack of transparency delayed the discovery of this bias. In finance, opaque AI models have led to trouble as well. For example, some banks deployed black-box credit scoring models that inadvertently learned to discriminate against certain groups or made lending decisions that nobody could interpret when they went awry. This not only causes reputational and legal risks, but also practical risk – if an AI-driven investment or lending model fails, the inability to explain its reasoning makes it harder to prevent repeat mistakes. These cases show that when AI operates with a lack of explainability, undesirable outcomes like bias and errors can go unnoticed until damage is done, and it’s hard to hold anyone accountable.
Impacts on Safety, Fairness, Accountability
When an AI’s logic is opaque, it undermines fairness and accountability. Individuals affected by the AI (a job applicant rejected, a patient denied treatment by an AI diagnosis tool, etc.) cannot ascertain whether the decision was justified or the result of flawed logic. This can embed hidden discrimination – as seen in the hiring and judicial examples – or simply errors that are not corrected. Safety can also be compromised. Consider an autonomous vehicle that makes a split-second decision that leads to an accident; if the decision process is inscrutable, engineers might not learn the right lessons to fix the system. Moreover, lack of transparency makes regulatory compliance challenging. Frameworks like the EU’s GDPR emphasize a “right to explanation” for automated decisions, and upcoming AI regulations demand some level of interpretability for high-risk AI. An opaque system risks non-compliance with such laws, compounding legal risk for organizations. Finally, from an ethical standpoint, opacity in AI can erode public trust in AI solutions generally – people may be less willing to accept or use AI if they feel it’s a mysterious black box making unchecked decisions.
Methods to Improve Transparency & Accountability
Achieving explainable AI (XAI) is a active area of research and practice. Some effective strategies include:
- Interpretable Model Design: Where possible, use simpler or inherently interpretable models. Not every AI needs to be a complex neural network; for many tasks, a decision tree or rule-based system might achieve the goal and can be directly inspected. Choosing an interpretable approach when stakes are high is a proactive way to ensure explainability. For example, a healthcare triage system might use a transparent scoring formula rather than a black-box model, so that doctors understand the basis for risk scores.
- Post-hoc Explanation Tools: When complex models are necessary, employ explanation techniques to open the black box. Tools like LIME or SHAP can generate human-readable explanations for individual AI decisions (e.g. highlighting which features of a loan application most influenced a denial). Similarly, saliency maps in computer vision show which pixels or regions influenced an image recognition result. While these techniques have limits, they provide insight into model behavior without altering the model.
- Transparency in Data and Development: Document and communicate how the AI was developed. This includes publishing datasheets/model cards that describe what data the model was trained on, its intended use, and known limitations. For instance, a model card might reveal that a facial recognition AI was trained mostly on lighter-skinned faces – a transparency measure that flags a potential bias issue to downstream users. Openly sharing such information builds trust and allows others to account for shortcomings. Indeed, a “transparent AI system is one where its mechanisms, data sources, and decision-making processes are openly available and understandable.”
- Governance and Oversight: Establish processes to review AI decisions regularly, especially in high-impact applications. Human oversight committees or audit teams can examine samples of AI decisions for fairness and consistency. If the AI is making unexplainable choices, those should be investigated and possibly used to improve the model or add constraints. In regulated sectors, this oversight aligns with compliance (e.g. validating that credit models don’t systematically disadvantage protected groups).
- User-Friendly Explanations: Provide affected users with explanations at an appropriate level of detail. For example, if an AI declines an insurance claim, the customer should receive a basic explanation (“Claim denied because damage was assessed below deductible and policy excludes item X”), even if internally the AI’s reasoning is more complex. This maintains a sense of procedural justice and allows users to contest or provide additional info if needed. Such “full disclosure” and communication about how the AI works and its purpose fosters accountability.
- Algorithmic Transparency by Design: Adopt a “Responsible AI by Design” approach where transparency isn’t an afterthought but a key requirement from the start . This could mean selecting algorithms known for interpretability, simplifying model architecture to what is necessary, and avoiding unnecessarily convoluted ensembling that would impede understanding. Techniques like model distillation (approximating a complex model with a simpler one for explanation) can also be used if one must deploy a complex model but still want a transparent proxy.
By implementing these measures, organizations can greatly reduce the risks associated with opacity. In essence, making AI transparent, explainable, and interpretable wherever possible helps ensure errors or biases are caught and corrected, users and regulators maintain trust, and the AI’s decisions can be justified in the light of day.
C.3.3 Level of automation
AI systems can operate with varying degrees of autonomy – from decision-support tools that a human oversees, up to fully autonomous systems that act on their own with no human input. This level of automation has a direct impact on risk. When an AI is fully autonomous, it means human operators are not in the loop for real-time decisions, so the system must handle all situations – including emergencies – by itself. Any failure in a fully automated system can have immediate, uncontrolled consequences because there’s no human backup to catch mistakes. On the other hand, when a human is “in-the-loop” or on standby (semi-autonomous systems), there’s an opportunity for oversight and intervention, but this introduces different risks like human complacency or confusion about when to step in. Each gradation – often discussed in contexts like autonomous vehicles (SAE Level 0 to 5) or industrial automation – presents a trade-off between efficiency and control. As automation increases, safety and security concerns intensify because the AI is granted more authority over actions, and any lack of judgment or flaw in the AI isn’t easily corrected in the moment. Additionally, higher automation raises ethical and fairness questions – e.g. should a completely autonomous system be allowed to make life-and-death decisions (as in autonomous weapons or medical AI) without human review?
Human-in-the-Loop vs. Full Autonomy
A human-in-the-loop system (low or moderate automation) often allows better control over risk in complex or value-sensitive decisions. For instance, many hospitals use AI to assist diagnoses, but final decisions are made by human doctors. This can improve outcomes by combining AI’s speed with human judgment. However, partial automation comes with the issue of automation bias and human complacency: operators might become over-reliant on the AI and fail to stay vigilant. A known phenomenon is that pilots or drivers can become too trusting of automated systems and may react too slowly when the system hands control back in an emergency. On the flip side, in a fully autonomous system, the response time can be faster (no waiting for human input) and processes more efficient, but the accountability shifts entirely to the AI logic. If the AI encounters a scenario it can’t handle, there is no immediate fail-safe unless pre-engineered. Therefore, fully automated systems require extremely rigorous validation and often additional fail-safes (like emergency shutdown mechanisms).
Safety Concerns & Case Studies
The impact of automation level on safety is evident in domains like aviation and transportation. A tragic example is the Boeing 737 Max’s MCAS automated system involved in two crashes. The aircraft’s MCAS was a software automation that pushed the nose down under certain conditions without pilot command. Pilots were not fully aware of this new system behavior. The result was catastrophic: “The two Boeing 737 Max plane crashes that killed 346 people have been attributed to a faulty automated system that pilots say they were not aware of.”
In this case, increasing the level of automation (and not adequately informing or training humans) introduced a deadly risk – the automation made a critical error (triggered by a single faulty sensor) and the human pilots were out of the loop, unable to correct in time due to lack of knowledge and the rapid onset of the problem. This underscores that with higher automation, design flaws or sensor failures can directly translate to accidents if human intervention is not feasible. Another example is from finance: algorithmic trading systems that operate with minimal human oversight. In 2012, Knight Capital deployed automated high-frequency trading software that went rogue due to a bug, executing millions of trades in minutes. In just 45 minutes, Knight’s algorithms created erratic trades that lost the company $460 million before humans could intervene. Here, the automation (program trading bots) acted far faster than any human could, which is beneficial when working correctly, but when an error occurred, the lack of a human checkpoint caused a massive loss. This illustrates the operational risk of full automation in fast-paced domains – there’s no “pause” for a sanity check. In robotics, consider a manufacturing robot working autonomously on an assembly line. If a safety interlock fails and the robot goes out of its programmed bounds, a fully automated robot could strike a human worker, as happened in the first recorded robot-related factory death in 1979. Modern factories mitigate this with cages and emergency stop buttons – effectively acknowledging that some human control or fail-safe must wrap around the autonomous robot to manage risk. As AI-driven automation expands to things like warehouse robots, delivery drones, and beyond, ensuring that their level of autonomy does not exceed what the safety measures can support is vital.
Fairness and Ethics with High Automation
Another angle is how fairness and ethical considerations play out. In a human-in-the-loop scenario, a human can inject ethical judgment or contextual understanding that an AI might lack. For example, a judge using an AI recommendation for sentencing can choose to override it based on circumstances the AI didn’t consider. In a fully automated decision (like an AI automatically rejecting loan applicants), there’s a risk that the decisions consistently disadvantage certain groups and no human is actively noticing or correcting those biases in real time. This was the fear with fully automated HR systems or college admissions algorithms – hence many organizations keep a human review step to ensure fairness. Furthermore, full automation in lethal systems (like military drones) raises ethical alarms because it removes human agency from applying deadly force. Many governance frameworks insist on meaningful human control in such cases for moral and legal accountability.
Security Implications
From a security standpoint, greater automation can mean a single breach or hack has more extreme consequences. If an AI is fully controlling a process, a malicious actor who manipulates the AI’s input or logic could cause harm without needing to trick any human. For instance, a fully autonomous vehicle could be misled by a tampered road sign (an adversarial attack) to behave unsafely with no driver to correct it. Or autonomous trading algorithms could be manipulated by feeding false market data, causing them to make huge damaging trades. With a human in the loop, there might be a chance to detect “something looks off” before disaster. So security controls often need to be stronger as automation increases.
Mitigation Strategies by Automation Level
Managing risks related to automation level involves both technical and procedural measures:
- Define Appropriate Automation Boundaries: Organizations should carefully decide which decisions to fully automate and which to keep a human involved in. A risk assessment can identify decisions that are too sensitive or complex to leave entirely to AI. For example, a bank might use AI to flag transactions as potentially fraudulent (automation), but have a human analyst review the flagged cases rather than automatically freezing accounts, to avoid false positives harming customers.
- Human-Centered Design: Even in automated systems, design for human override and situational awareness. In semi-autonomous vehicles, for instance, there are driver monitoring systems that ensure the human is ready to take over. Similarly, AI-operated machinery is often equipped with big red emergency stop buttons accessible to humans. These design choices acknowledge that automation can fail and provides a manual fallback. It’s also crucial to clearly inform humans about the automation’s limits (as Boeing failed to do for pilots). Training and transparency about what the AI will or won’t handle keeps human supervisors effective.
- Gradual Automation & Testing: Do not jump from manual to fully autonomous in one leap. Gradually increase autonomy as confidence and safety measures grow. Use extensive simulations and pilot programs at each level. The aviation industry, for example, incrementally introduced autopilot features over decades, learning how humans and automation interact (though the 737 Max showed even incremental steps can backfire without proper process). Each increase in autonomy should come with exhaustive testing of failure modes – what happens if the AI makes a wrong move? Ensuring the system degrades gracefully (fails safe) is key.
- Automation Bias Training: For systems where humans and AI co-operate, train the human operators about automation bias and how to remain engaged. Pilots, for example, are trained to understand what the autopilot can/can’t do and to practice takeover scenarios. In medical AI tools, doctors should be reminded that the AI is an aid, not an oracle, and be trained in when to question or override AI suggestions. Organizational culture should reinforce that the human’s role is still critical even when AI is doing the routine work.
- Rigorous Validation for Full Autonomy: If full automation is deployed, it necessitates very rigorous validation and monitoring. This might include formal verification of critical algorithms, redundancy (e.g. an independent parallel system monitoring the primary AI for anomalies), and real-time diagnostics. An autonomous system might have a secondary “sanity-check” AI that evaluates the primary AI’s actions and can intervene or alert if something seems off (a technique used in some high-end autonomous driving systems). Essentially, safety engineering like what’s used in aerospace (multiple independent systems cross-checking each other) becomes important when a human isn’t in the loop as a safety net.
- Maintaining Human Accountability: Even with full automation, assign clear human accountability for the system’s operation. There should be designated individuals or teams responsible for the outcomes of the AI system, who regularly review logs and decisions. This governance ensures that the AI’s performance is tracked and there is someone empowered to adjust or halt the system if it’s trending in an unsafe or unfair direction. For example, a bank using an automated trading AI might have a risk officer who gets alerts if the AI’s trading deviates from expected patterns, with the authority to suspend trading if needed (essentially acting as a human circuit-breaker).
- Policy and Regulation Compliance: Keep automation aligned with regulations that may require human judgment. In some domains, laws intentionally require a human decision-maker (for instance, GDPR’s Article 22 gives individuals the right to demand human review of automated decisions). An organization should design its AI use to respect these constraints, perhaps by offering appeals processes or oversight boards for decisions made by AI.
In summary, as the level of automation increases, the nature of risks shifts – moving from “human error in using AI” towards “AI error with no human catch”. A balanced approach often works best: automate what you can safely automate, but maintain human insight and control where needed. Importantly, build organizational competency to manage human-AI interaction, so that neither the human nor the AI becomes a single point of failure.
C.3.4 Risk sources related to machine learning
Machine learning (ML) introduces unique risks because of its data-driven, statistical nature. Unlike deterministic software, an ML model’s behavior is learned from data, which means data quality and biases directly influence outcomes. Key risk sources in ML include: poor training data quality, bias in data or model, vulnerabilities to malicious inputs (like data poisoning and adversarial examples), overfitting or lack of generalization, and concept drift over time. Additionally, the complexity of ML models (especially deep neural networks) can make their failures non-intuitive and hard to debug, compounding the risk.
Data Quality & Bias Risks
The maxim “garbage in, garbage out” is very apt for ML. If the training data is flawed – containing errors, noise, or unrepresentative samples – the model will learn those flaws. For example, if an ML model for hiring is trained on past hiring decisions that favored a certain demographic, the model can learn to perpetuate that bias, as happened with Amazon’s recruiting AI which learned to penalize resumes containing the word “women’s” due to biased historical data. This is a data bias issue leading to discriminatory outcomes. ML systems have shown racial and gender biases in many settings: a prominent study by Buolamwini and Gebru found that commercial facial recognition models were significantly less accurate for darker-skinned women than for lighter-skinned men
– a direct result of imbalanced training data that had fewer examples of darker-skinned female faces. These biases are not always obvious until the model is deployed and causes harm. The risk is that ML can amplify societal biases under the veneer of algorithmic objectivity. Data quality issues beyond bias include mislabeled data (leading to incorrect model behavior), or training data that doesn’t cover important scenarios (leading to blind spots in model knowledge). For instance, if an autonomous drone’s ML vision system was never trained on birds, it might misidentify a bird as something else, causing odd behavior. Robustness of an ML model heavily depends on comprehensive, high-quality data; any shortcomings here manifest as performance errors or unfair decisions.
Training Process & Overfitting
The way an ML model is developed can introduce risk. If a model is overfit to its training set (i.e. it memorizes training examples instead of generalizing), it may perform well in testing but fail in real-world use with slightly different data. This often isn’t discovered until deployment. There’s also risk in hyperparameter selection – an improperly tuned model might be unstable. Moreover, if the objective function in training doesn’t align with real-world goals, the model may optimize the wrong thing. A famous anecdote: a military image classifier trained to distinguish tanks vs. trees accidentally learned to recognize differences in photo lighting (since tank photos were taken on cloudy days, trees on sunny days) – it “solved” the training objective but in a meaningless way, failing on new data. This type of spurious correlation risk is endemic in ML.
Adversarial Attacks (Evasion)
Adversaries can exploit ML models through adversarial examples – specially crafted inputs that fool the model while looking normal to humans. For instance, researchers showed that by placing small stickers on a stop sign, a vision model could be tricked into “seeing” it as a speed-limit sign. Imagine the risk if a self-driving car’s perception ML system is vulnerable to such attacks: an attacker could cause the car to ignore real stop signs or misread traffic signals, potentially leading to accidents. Adversarial examples represent a risk source because they reveal how fragile ML decision boundaries can be – a slight perturbation, imperceptible to people, can lead the model to make a drastically wrong prediction. This is particularly concerning for security-sensitive applications (facial recognition can be fooled by patterned glasses, malware detectors fooled by adding benign code, etc.). Unlike traditional software, where inputs that cause failure are usually obvious, ML models might fail on inputs that look entirely benign due to these adversarial vulnerabilities.
Data Poisoning (Training-time attacks)
If an attacker can influence the training data (or retraining process), they might introduce “poisoned” examples that cause the model to learn incorrect behavior. For example, an attacker might add some fake records to a fraud detection training set so that transactions from a certain fraud scheme are always labeled as non-fraud. The trained model might then consistently fail to catch that scheme. Data poisoning can be hard to detect because it hides in the learning process. One real incident akin to online poisoning was Microsoft’s chatbot Tay: trolls on Twitter taught Tay to output hateful messages by feeding it malicious inputs, in essence poisoning its online learning process. In less interactive settings, poisoning could be subtle – e.g. corrupting a few sensor readings in an autonomous vehicle’s dataset so it learns a slight miscalibration.
Concept Drift
After deployment, ML models face the issue that the world may change in ways that invalidate the patterns they learned. This is called concept drift – the statistical properties of the input or the relationship between inputs and outputs evolve over time. For instance, a model predicting stock prices might perform poorly when market dynamics change significantly from the training period, or a recommendation system’s predictions might become stale as user preferences shift. An example in medicine: an AI diagnosing diseases might become less accurate if a new strain of virus emerges (making past data less relevant). Concept drift means models can degrade silently if not monitored. A predictive model might continue to output results with high confidence while its error rate creeps up because the environment changed. Without processes to detect and address drift, organizations may rely on increasingly inaccurate models, which is a significant risk source.
Real-world Consequence Examples
We already saw fairness failures (biased hiring, biased face recognition) and safety/security issues (adversarial stop sign). Another notable example of ML risk is IBM Watson for Oncology. Touted as a cutting-edge AI for recommending cancer treatments, it faced serious criticism when deployed. It was found that Watson often suggested treatments that were incorrect or unsafe – in one case, recommending a drug for a patient with severe bleeding where that drug was explicitly contraindicated. The root cause was that Watson’s model was trained largely on hypothetical synthetic cases created by doctors, not on real patient data, leading it to learn patterns that didn’t hold in reality. This highlights multiple ML risk sources: limited/bias training data and lack of rigorous validation, resulting in a system that could have harmed patients. The outcome was loss of trust and eventual discontinuation of that product. Another example: “Concept drift” in credit risk models during an economic crisis. A bank’s ML model for credit scoring might be built on data from stable economic times; when a recession hits (a different data regime), the model’s predictions of who will default can become very wrong, exposing the bank to far more risk than anticipated. If the bank doesn’t update the model or catch this drift, it could lead to many bad loans or unjustly denying credit to qualified borrowers because the model’s implicit assumptions no longer hold.
Strategies for Robust & Safe ML:
- Data Governance & Bias Mitigation: Ensure training data is as accurate, representative, and unbiased as possible. This involves diversifying data sources, cleaning data rigorously, and using techniques like re-sampling or re-weighting to address known biases. For fairness, conduct bias audits on the model outputs (e.g. test the model on subpopulations to see if error rates differ) and use bias mitigation algorithms if needed. Domain experts should review whether the features the model uses are appropriate or encode any sensitive attributes inadvertently.
- Secure Training Practices: Treat training data as a potential attack surface. Use data provenance and validation to prevent unauthorized or suspicious data from influencing the model (especially in online learning systems). If the model is updated continuously (e.g. recommendation systems), put guardrails to detect anomalies in new training data. Research techniques like robust training and poisoning-resistant algorithms can help, as can simply having a human-in-the-loop to review training data additions.
- Adversarial Robustness: Improve model resilience to adversarial inputs by methods such as adversarial training (where you train the model on perturbed examples so it learns to resist them) and input sanitization. For vision systems, for instance, one can implement filters that detect odd patterns or warnings if a critical sign detection is uncertain. It’s also important to physically test AI systems in realistic adversarial conditions; e.g. test an autonomous car with graffiti on signs, weirdly colored objects, etc., to see how the ML handles them. Additionally, monitoring systems can flag if inputs to the ML model have characteristics of known adversarial patterns (for example, an intrusion detection system for images).
- Validation & Testing (ML-specific): Go beyond standard train/test splits. Use extensive cross-validation, and test the model on out-of-sample and stress scenarios. For critical systems, consider formal verification on simpler surrogate models to get guarantees on certain properties. Conduct “red team” exercises where an internal team deliberately tries to break the model or find scenarios where it fails. For example, challenge a loan approval model with edge-case applicant profiles, or challenge a vision model with unusual environmental conditions, to discover weaknesses. The NIST AI Risk Management Framework suggests evaluating trustworthiness characteristics like robustness, which involves testing a model under a range of conditions.
- Monitoring and Maintenance: Once deployed, monitor model performance in real time. Implement drift detection algorithms that compare new input data distributions to the training data distribution; if they diverge beyond a threshold, alert that concept drift may be occurring. Also track the accuracy or error rates over time via ground truth feedback if available. Many organizations now practice MLOps – an analogue of DevOps for ML – which emphasizes continuous monitoring, data/model versioning, and periodic retraining. If performance degradation is detected, have a process to retrain the model on more recent data or revisit feature engineering. Essentially, plan for the model’s lifecycle: an ML model is not a one-and-done deliverable but requires ongoing care to remain valid.
- Robust Model Architecture: Employ architectures known for better generalization when possible. Simpler models can sometimes generalize more reliably and are easier to troubleshoot (aligning with the transparency point earlier). Where complex models are necessary, use ensemble methods – multiple models whose results are combined – which can provide more stability (one model may correct another’s odd mistake). However, ensembling should be done carefully to avoid just enshrining the same bias multiple times.
- Fail-safes and Human Oversight in ML Decisions: For critical applications, do not rely solely on the ML output. Use the ML to assist or flag issues, and keep a human decision-maker for the final call until you have extremely high confidence in the model. For instance, if an ML model scans medical images for cancer, it could mark suspicious regions but a radiologist should confirm before diagnosis. If an autonomous system’s ML is uncertain (low confidence prediction), it should have logic to either not act or to default to a safe mode. Designing the system to know when it doesn’t know (and hand control to a human or a safe state) is an important safety mechanism.
- Privacy and Security Measures: Some ML risks are indirect – e.g. privacy issues (personal data in training sets) or intellectual property (model theft). Techniques like federated learning, differential privacy, or secure multi-party computation can reduce those risks by protecting training data or the model from exposure. While these are more about privacy/security, they ultimately contribute to the trustworthiness of the ML system and prevent incidents (like a data breach altering training data = poisoning).
Addressing these areas, organizations can significantly reduce the risk profile of ML systems. It’s about making the ML pipeline – from data to model to deployment – as robust, secure, and well-monitored as possible. As one source summarizes: “the outputs of machine learning systems depend on the quality of the training data”and on the assumptions remaining valid, so continuous diligence is needed to ensure those conditions hold true in practice.
C.3.5 System hardware issues
Hardware-Related Risks Overview
AI systems ultimately run on hardware – from sensors that perceive the environment, to processors (CPUs, GPUs, AI accelerators) that compute the algorithms, to actuators that may execute decisions in the physical world. Hardware issues can therefore directly impact AI behavior. The risk sources include hardware failures (sudden crashes or malfunctions), degraded performance due to aging or environmental factors, compatibility or transfer issues (when moving AI software to a new hardware platform), and security vulnerabilities at the hardware level. Unlike purely software issues, hardware problems can be nondeterministic (e.g. a rare memory bit flip) and may not be caught by traditional software testing. This makes them a subtle but important source of risk.
Failures and Aging Components
Hardware, like any equipment, can fail. In an AI context, a failing sensor feeding incorrect data to the AI could cause bad decisions. For example, if a LIDAR on a self-driving car fails or gets occluded, the AI’s perception of obstacles will be wrong. If not designed to handle sensor failures, the car could make unsafe moves. Redundancy is often used to mitigate this (multiple sensors cross-check), but not all systems have that. Aging is another factor – over time, sensors may drift (a camera’s color calibration might shift, or a physical component might wear out, causing data noise). This can slowly degrade an AI’s performance. A classic case is calibration drift: many IoT sensors (temperature, pressure, etc.) require periodic recalibration; if an AI relies on them and they drift, the AI’s inputs become systematically biased. For hardware like robotic actuators, wear-and-tear could lead to less precise movements, so an AI controller might start overshooting or not achieving desired outcomes reliably. Additionally, hardware environments (temperature, vibration) can affect electronics. An AI chip running too hot might throttle and thus not provide results in real-time, causing latency in a safety-critical system. All these failure modes need consideration: a robot that should apply 10N of force but due to a motor issue applies 30N could damage its environment or humans around.
Infrastructure and Power
AI systems often depend on broader infrastructure – e.g. cloud servers, network connectivity, power supply. Hardware risk includes outages or constraints in these. If an AI is running in the cloud and the data center has a power failure or network partition, the AI service might become unavailable or only partially available. For instance, an AI-powered surveillance system might go down if network hardware fails, leading to a security blind spot. Or if a power surge damages an edge computing device running an AI, its functionality is lost. Even something as mundane as a low battery in a drone or autonomous vehicle is a hardware risk – if the system doesn’t handle it gracefully, the AI could literally drop out of the sky or stall in traffic.
Transferring ML Models Between Hardware
Organizations often develop AI models on one hardware setup (say, high-end GPUs in a lab) and then deploy on different hardware (say, an embedded device or specialized AI chip). This transfer can introduce issues. One is differences in numeric precision – for example, a model trained in 32-bit floating point might be quantized to 8-bit integers to run on a small device. If not done carefully, this can significantly change the model’s outputs. It may introduce small errors that cascade into big decision changes. Developers need to validate that the model’s accuracy remains acceptable post-porting. Another issue is compatibility: certain model operations might not be supported or might run in a limited way on the target hardware, leading to using approximations or suboptimal execution which could affect timing. There’s also a risk that hardware-specific bugs or quirks (like a particular GPU model’s driver bug) surface only in deployment. Ensuring consistency of AI behavior across hardware is important but not trivial – differences in computation order or parallelism can cause nondeterministic outcomes in some cases. For example, two GPUs might sum floating-point numbers in different orders, leading to tiny numerical differences; usually negligible, but in sensitive algorithms it might lead to divergent paths over time. This is often managed by thorough testing on the target hardware and sometimes retraining or fine-tuning the model on the target device.
Security Vulnerabilities in AI Hardware
The hardware that runs AI can be a target for attackers. A few notable vulnerability types:
- Side-Channel Attacks: Attackers can exploit physical emissions (like electromagnetic radiation or power usage patterns) of AI hardware to infer secrets about the model or data. For instance, researchers demonstrated the “BarraCUDA” attack where they used electromagnetic signals from an NVIDIA Jetson AI module to extract the neural network’s weights and biases. This means an attacker with the right equipment near a device could potentially steal a proprietary model (IP theft) or even sensitive data the model was trained on (if the model parameters encode such info). Side-channel attacks on AI accelerators are a real concern as reported by industry – even OpenAI has raised flags about securing AI chips.
- Fault Injection: Attackers may induce faults in hardware (via techniques like voltage glitching, clock glitching, or even exposing memory to cosmic rays artificially) to make the hardware miscompute. One scary scenario: by flipping certain bits in an AI model’s memory (through a Rowhammer attack or similar), an attacker might induce the model to misclassify. If an autonomous car’s brain is attacked this way, a stop sign might be seen as a speed sign, similar to an adversarial example but achieved through hardware manipulation. Meta (Facebook) published that even unintentional hardware faults like random bit flips can cause **“AI model parameters to be corrupted and produce inaccurate or weird outputs”*. If done intentionally by an attacker, they could aim flips to cause maximum disruption or specific wrong outcomes.
- Hardware Trojans: During the manufacturing of AI chips or devices, if an adversary inserts a backdoor (a malicious circuit or code in firmware), it could be triggered later. For instance, an AI accelerator could have a hidden mode that, when it sees a specific trigger input, bypasses normal computations and outputs an attacker-chosen result. This is a sophisticated risk, more applicable in critical national security or military AI hardware, but it is a concern in supply chain security discussions.
- Firmware/Software Vulnerabilities: Many AI hardware systems (like GPUs running drivers, or IoT devices running firmware) have software components that can be exploited (buffer overflows, etc.). Once compromised, an attacker might manipulate the AI computations or use the hardware access to further infiltrate the system. For example, an exploitable bug in a Tesla’s autopilot hardware firmware could, in theory, allow an attacker to send fake sensor readings to the driving AI.
Mitigation Strategies for Hardware Risks
- Redundancy and Fault Tolerance: For critical sensors and processors, provide redundancy. Airplanes, for example, have multiple redundant sensors and computers voting on outcomes. Similarly, a self-driving car might use radar as well as camera as a backup if LIDAR fails. On the compute side, error-correcting memory (ECC) can greatly reduce the risk of bit flip errors by detecting and correcting single-bit memory errors on the fly. Redundant power supplies or backup batteries can help systems safely shut down or continue briefly during outages. The system should be designed to fail safe if hardware fails – e.g. if sensor input is lost, an autonomous car should slow and stop rather than operate blindly.
- Preventive Maintenance and Monitoring: For hardware that can degrade, schedule regular maintenance or calibration. For instance, periodically calibrate sensors against known references. Many industrial AI systems include self-diagnostic routines – a robot might periodically check if its actuators are responding within expected parameters and flag if not. Condition monitoring (tracking sensor noise levels, drift over time) can predict when a component is likely to go out of spec so it can be replaced proactively. Essentially, treat the hardware like an integral part of the AI system lifecycle: track its health like you track model accuracy.
- Robust Deployment & Testing on Target Hardware: Always test AI systems on the actual hardware they will run on (or an accurate simulation of it) before full deployment. This testing should include edge cases and stress conditions: e.g. run the device at high temperature, low voltage, maximum throughput, etc., to see if any failures or timing issues emerge. If a model is ported to new hardware, do a regression test to ensure its outputs match the original within acceptable tolerance on a large suite of test inputs. If differences are found, consider retraining or recalibrating the model on that hardware. Some organizations use techniques like quantization-aware training (training the model while simulating lower precision) to avoid surprises when deploying on specialized chips.
- Security Hardening of Hardware: Employ hardware security best practices. This includes using Trusted Platform Modules (TPMs) or secure enclaves to protect sensitive model parameters or computations from exposure. Devices should authenticate firmware updates to prevent tampering. Side-channel attack mitigation can involve adding noise to power consumption, shielding electromagnetic emissions, or using constant-time execution techniques so that operations don’t vary with secret data. For example, if deploying an AI model that is highly sensitive IP, one might use an encrypted model format that only decrypts inside a secure enclave in the CPU, so even if someone has the device, they can’t easily dump the model weights. To counter fault injection, sensors like voltage and clock monitors can detect abnormal fluctuations and reset or shut down the device if an attack is suspected. In environments where physical access is possible, physical tamper-detection mechanisms can be in place (like the device erases sensitive info if opened).
- Diverse Sensing and Cross-Validation: In robotics and autonomous systems, combining different types of sensors mitigates individual weaknesses. For instance, camera-based AI might fail in darkness but an infrared sensor or radar still works – fusing their data provides robustness. If one sensor disagrees wildly with another, the system can recognize something’s wrong with one of them. Similarly, if an AI has multiple hardware outputs, cross-check if they remain consistent. A practical example: a medical monitoring AI might use two different brands of sensors for critical vitals; if one readings diverges, it alerts staff to check the patient manually – this reduces risk of a single sensor fault causing a missed alarm.
- Environment Control: In critical deployments, sometimes the environment can be controlled to reduce hardware risk. For example, AI servers can be kept in temperature-controlled, filtered environments to minimize overheating or dust-related failures. If an AI device must operate in harsh conditions (extreme cold, heat, vibration), choose industrial-grade hardware rated for those conditions or add protective housings (for instance, shock absorbers for vibration, cooling systems for heat). By aligning hardware specs with the operating environment, unexpected failures are less likely.
- Logging and Alerting: Implement comprehensive logging for hardware-related events. Many systems can log if they had to correct a memory error, or if a sensor had a momentary dropout. If such events become frequent, it indicates a brewing hardware issue. Alerts can be sent so maintenance can be scheduled before a catastrophic failure. For AI, also log when the system falls back to a redundant component, or when an internal check fails – this can pinpoint hardware issues. Think of an autonomous drone that has dual cameras: if one camera feed goes black and it switches to the other, it should log that and perhaps notify ground control on landing that Camera A is dead.
- Supply Chain and Procurement Caution: Reduce the use of untrusted or unknown hardware components in critical AI systems. Source hardware from reputable manufacturers with good security track records. If AI accelerators or boards are sourced from third parties, ensure they are vetted or certified (some industries have certification processes for hardware used in safety-critical systems). For extremely sensitive uses, custom-designed chips with formal verification might be warranted to ensure no hidden surprises. While this is not feasible for most commercial uses, being aware of where hardware comes from and any known issues (checking errata sheets for CPUs/GPUs for known bugs, etc.) is part of risk management.
In essence, hardware is the foundation of any AI system: if it cracks, the whole system can fail regardless of how good the software is. Thus, anticipating hardware failures, securing the hardware against threats, and engineering tolerance and graceful degradation into the system are all critical to managing AI risk at the hardware level. As Meta’s research noted, even a tiny bit flip can cause “weird or bad output” from an AI model, so both preventing such faults and handling them when they occur is an important part of trustworthy AI engineering.
C.3.6 System life cycle issues
An AI system’s risks are not static; they can emerge at any stage of its life cycle – from initial design and development, through deployment and operation, to ultimately decommissioning. System life cycle issues refer to problems that arise due to how the AI is managed (or mismanaged) over time. This includes design flaws from the outset, inadequate testing before deployment, poor change management during updates, lack of maintenance and monitoring in operation, and improper end-of-life handling. Each phase has its pitfalls: decisions or omissions early on can bake in future failures, while neglect later on can let an initially good system become unsafe or obsolete. Ensuring a robust AI governance process across the entire life cycle is key to mitigating these risks.
Design & Development Flaws
In the design phase, if requirements are incomplete or the context of use is misunderstood, the AI might be built with wrong objectives or constraints. For example, if designers focus solely on accuracy and neglect fairness requirements, the resulting system might be very accurate on average but systematically biased. A real case: the UK’s 2020 A-level exam algorithm was designed to standardize grades when exams were canceled (due to COVID-19) using historical school data. The designers failed to account for individual student merit sufficiently, and the result was perceived as unfair (bright students from historically underperforming schools were harshly downgraded). This design choice – valuing one kind of consistency over individual fairness – caused a huge controversy and the system had to be scrapped. Another design flaw example is not incorporating security from the start (no threat modeling) – e.g., an AI assistant might inadvertently be triggerable by anyone’s voice because designers didn’t plan authentication. If ethical, security, and domain experts are not involved in design, critical scenarios and requirements can be missed. During development, inadequate testing is a common issue. Perhaps the AI model was only tested on clean lab data and not on messy real-world data (leading to failure upon deployment, as seen with some medical AI that worked in the lab but not on real hospital patients). Integration testing is also crucial: the AI may work fine in isolation, but when integrated into a larger system it could behave unexpectedly (maybe the input data pre-processing in the pipeline had a bug, or unit conversions were handled differently, etc.).
Deployment & Transition to Operation
How an AI system is introduced can be risky. If users (or operators) are not properly trained on the new AI tool, they might misuse it or mistrust it. For instance, rolling out a decision support AI to loan officers without guidance could lead to inconsistent use – some might follow it blindly (even when it’s wrong), others might ignore it completely. Another deployment risk is the lack of a phased rollout or pilot. Launching system-wide in one go means any undiscovered issue hits all users at once. Best practice is often to do a limited deployment, observe, fix issues, then expand. Skipping that due to time pressure or overconfidence is risky. Also, transitioning from an old system to a new AI system must be handled carefully – both might need to run in parallel for a while to verify the AI’s outputs align with expectations. If the old system is shut off prematurely, there’s no fallback if the AI has issues.
Maintenance and Monitoring Gaps
Once the AI is live, if it’s treated with a “set and forget” mentality, problems will accumulate. AI models are not static; they need continuous updates and maintenance to stay relevant. Many organizations fail to plan for this ongoing effort. For example, if an AI model in e-commerce isn’t retrained as product ranges and consumer behavior evolve, it will start giving poor recommendations – a minor issue. But in critical systems, like a fraud detection AI, if new fraud patterns emerge and the model isn’t updated, the organization could suffer major losses. Lack of monitoring is another lifecycle issue: you need to watch how the AI is performing in the real world (accuracy, errors, feedback, etc.). If no one is tracking key metrics or user complaints, the AI could be making flawed decisions for a long time before anyone realizes. In one case, an automated translation system was unknowingly producing sexist translations (e.g. always translating “doctor” as “he” in a target language), and it took public criticism to spur the maintainers to correct those biases – indicating that internal monitoring hadn’t caught it. Additionally, software environment changes (like an OS upgrade or a library update) can affect the AI. If maintenance doesn’t include re-testing the AI after infrastructure changes, there’s risk of sudden failures. Consider an AI chemical process controller that worked in version 1 of an API, but version 2 changed a function’s behavior – without lifecycle management, this could lead to a plant incident.
Evolution and Change Management
AI systems might undergo improvements or changes (new training data, new features, model upgrades). Each update is a potential risk if not managed well. There have been instances where a model update, meant to improve performance, ended up causing a drop in a different aspect (like improving overall accuracy but significantly worse on a subgroup). Without proper A/B testing or rollback plans, pushing a bad update can degrade system performance or user trust. The “shadow mode” approach – running the new model in parallel without affecting decisions, to compare outputs – is wise, but if skipped, the first sign of trouble might be user complaints or incidents after the new model is live. Moreover, documentation is a life cycle aspect: if the rationale for certain design choices or model parameters isn’t documented, when new team members join or an incident occurs later, it’s hard to understand the system. Lack of documentation and knowledge transfer is a risk to continuity and consistent improvement.
Decommissioning and End-of-Life
Eventually, an AI system may need to be retired or replaced. Risks here include data and model remnants. For example, if a healthcare AI system is decommissioned, it likely has learned from patient data – that data and the model might be sensitive. Properly archiving or destroying models in line with data retention policies and privacy laws is important. If not, there’s a risk of data breaches or misuse of an obsolete model that’s floating around. Another risk is a gap in functionality: if the AI provided an important safety function and it’s turned off before a new solution is in place, you have a window of vulnerability. Even migrating to a new AI can be risky if not overlapped – the new AI might behave differently, surprising users or not integrating well with legacy components.
Examples of Lifecycle Mismanagement
Aside from the earlier examples, consider the scenario of “AI project failure” in organizations: studies find a large percentage of AI projects fail to deliver value, often due to issues in lifecycle management (like deploying without clear business alignment, or no one to maintain them). A concrete story: a large bank developed an AI tool to evaluate legal documents. It worked in the pilot but after deployment, no one updated its knowledge base; as laws changed, it became less accurate, lawyers lost confidence in it, and it eventually was shelved – essentially a failure of ongoing maintenance and alignment with changing requirements. Another example is the Tesla “Autopilot” evolution: Tesla frequently updates its car AI via over-the-air updates. In one instance, an update intended to improve performance in certain scenarios caused new issues in others (some users reported more false braking events). Tesla quickly had to patch it. The lesson is that without rapid monitoring and patching (which Tesla does have in place), such updates can pose safety risks; Tesla’s agile approach to life cycle management mitigates it, but not all industries can move that fast or have that direct of an update pipeline.
Best Practices for Lifecycle Governance:
- Incorporate Risk Management from Day 1: During design, perform risk assessments (akin to FMEA – Failure Modes and Effects Analysis) specifically for the AI features. Identify what could go wrong and build in safeguards or at least monitoring for those scenarios. For example, foresee if an AI could be used outside its intended scope and how to prevent that. Treat ethical and security considerations as first-class design goals, not afterthoughts.
- Cross-Functional Design Review: Engage stakeholders from various domains (security, domain experts, end-users, ethicists) in design and development. They can catch issues early that the core AI developers might miss. This can prevent obvious misalignments like the UK exam algorithm’s oversight or Watson for Oncology’s training approach, by questioning “What if…?” at the requirements stage.
- Rigorous Testing & Validation Plan: Establish a multi-stage testing pipeline: simulation, sandbox environment, pilot program. Use real-world data in testing as much as possible. Include adversarial testing and stress testing as mentioned. Importantly, test the integration of the AI within the whole system (hardware, other software, user workflows). Certification processes (like FDA approval for medical AI or ISO safety certifications) often provide good frameworks for validation – following those even if not mandatory can strengthen confidence in the system before full release.
- Change Management Processes: Any update to the AI (model retrain, software update, hardware change) should go through a change management flow: testing of the change, impact analysis, documentation of what changed and why. Maintain a “version history” of models and be able to roll back to a previous model if an update underperforms. Tools from software engineering (like Git for code, and emerging ML model versioning tools) help track this. As a rule, avoid abrupt changes – prefer gradual rollout or shadow mode verification for major changes.
- Continuous Monitoring and Ownership: Assign clear ownership for the AI system in production. This could be an AI operations team or a product manager, etc., who continuously monitors performance metrics and user feedback. Define Key Performance Indicators (KPIs) and thresholds that, if breached, trigger an investigation. For example, if an anomaly detection AI suddenly starts flagging 30% more events than usual, the owner team should be alerted to investigate whether it’s a true increase in anomalies or a model issue. Use dashboards and automated alerts for things like data drift, unusual output patterns, or system downtime. Essentially, treat the AI like a service that requires uptime monitoring and incident response procedures.
- Regular Maintenance and Updates: Plan periodic review cycles for the AI. This might mean retraining the model on new data every X months, or recalibrating it. Even if concept drift isn’t evident, regular refresh can keep performance optimal (assuming new ground truth data is available). Also update the AI to incorporate new knowledge – e.g., if a medical AI is in use, periodically updating it with the latest medical research or guidelines ensures it doesn’t become outdated in its recommendations. Document these maintenance actions in a log.
- User Training and Feedback Loop: Ensure users (or operators) are trained on the AI system’s proper use, limitations, and how to report issues. Establish an easy feedback mechanism – e.g., a doctor using an AI diagnosis tool can press a button if they think the AI made an incorrect suggestion, which gets logged for the developers to review. Users often are the first to notice subtle issues (“the AI seems less accurate with pediatric cases”) – capturing that information is gold for lifecycle improvement. An organization might even formally survey or audit user satisfaction with the AI system regularly.
- Incident Response Plan: Despite best efforts, things can go wrong. Having a plan for AI incidents is crucial. For instance, if the AI in a factory starts behaving oddly (say a robot making unusual motions), there should be a clear procedure to safely shut it down and revert to manual process. If an AI-driven service produces an incorrect result that causes harm (like a bad financial decision), have a plan to compensate or remediate. Basically, apply principles from IT disaster recovery to AI: backups (maybe keep the last stable model version), failover (hand off to human control), and communication plans (inform stakeholders, users about the issue openly and what’s being done).
In summary, managing AI risk is not a one-time task but a continuous process throughout the system’s life. From conception to decommissioning, each phase needs attention to ensure the AI remains safe, effective, and aligned with objectives. Organizations following standards like ISO 42001 or ISO 23894 are guided to consider the entire life cycle – this includes setting up an AI management system that enforces these practices. The payoff is that the AI system will be far less likely to produce nasty surprises and far more likely to deliver sustained value.
C.3.7 Technology readiness
The concept of technology readiness refers to how mature (or immature) a technology is for real-world use. Using cutting-edge, immature AI tech can be risky because its limitations and failure modes are not well understood – essentially, you’re venturing into the unknown. On the other hand, even widely adopted “mature” AI technologies can breed over-reliance and complacency, which is risky if edge cases haven’t been fully eliminated. This risk source is about gauging whether the AI technology is sufficiently proven and understanding the challenges at both ends of the spectrum: the bleeding edge vs. the stable but possibly unchallenged plateau.
Challenges with Immature AI Technologies
New AI methods (e.g. a novel deep learning architecture, or AI in a domain that hasn’t used it before) often come with unknown unknowns. There may be hidden flaws that only surface when applied at scale or in diverse environments. For example, early generative AI language models (like initial GPT versions) surprised users by producing hallucinations (confidently incorrect statements) or leaking private training data – behaviors not fully anticipated by creators because the tech was so new. Immature tech may also lack tooling, guidelines, and community knowledge for best practices. This means organizations adopting it might not have frameworks to ensure safety. Performance drift is another issue: an immature AI might perform well in demo scenarios but degrade in prolonged use. Consider an experimental reinforcement learning algorithm from research – it might solve a game in the lab but fail to adapt to slight rule changes or increased complexity in the real world. Regulatory gaps compound this: when a technology is new, regulations might not exist yet (or are very outdated), so there’s less external oversight. For instance, early facial recognition deployments happened with very little regulatory guidance, leading to public backlash and moratoria once issues of bias and privacy came to light. Companies that jump on immature tech might face reputational or legal risk once society catches up with the implications.
There’s also the scaling risk – something that works in a small trial might hit unexpected bottlenecks at scale (maybe computational intensity, or unanticipated costs). Immature AI often requires specialized hardware or huge data; an organization might struggle to support that at production scale, causing failures or unmet performance in deployment. Additionally, lack of standards for a new tech means interoperability issues; if you adopt a unique AI solution that later doesn’t align with emerging standards, you may have to do costly reworks.
Over-reliance on “Mature” AI Tech
Conversely, when an AI technology is considered mature, people might treat it as infallible when it’s not. A good example is the decades-old automated trading algorithms on Wall Street – by 2010, they were standard (mature) but then events like the “Flash Crash” happened, partly because too much trust was placed in automated trading and not enough safeguards for unusual situations. Another example is autopilot systems in aviation – extremely mature and generally reliable. However, this maturity led to pilots being less engaged or skilled in manual flying, which became a factor in some accidents where autopilot handed control back in an emergency and pilots were rusty (this was noted in the Air France 447 crash analysis). So the risk is complacency: assuming the AI can handle everything, organizations might neglect training humans or updating contingency plans. Mature AI tech can also get embedded into infrastructure without frequent re-validation. If an edge case or vulnerability is later discovered, it may be widespread. For instance, suppose a popular open-source AI library has a subtle bug that no one noticed for years; once discovered, it might reveal that many deployed systems have a flaw (like a random number generator bug impacting cryptographic security or similar).
Unanticipated Edge Cases Even in Mature Tech
Any AI system, no matter how polished, can face a scenario outside its design. A quote from a Stanford expert on autonomous cars summarizes it: “With an autonomous car operating in an urban environment, you can always find some pathological situation that’s going to cause a crash.” – meaning no matter how mature, there will be some scenario (perhaps extremely rare) that breaks it. If people assume a mature AI has no edge cases, they won’t be prepared when one happens. The Tesla Autopilot (considered fairly advanced) not detecting a white truck against bright sky in a 2016 crash is a perfect illustration: a corner case fooled a well-established system, resulting in a fatal accident. Thus, “mature” doesn’t mean “perfect,” and thinking otherwise is risky.
Assessing Technology Readiness
To systematically evaluate how ready an AI technology is, one approach borrowed from engineering is using Technology Readiness Levels (TRLs). TRLs provide a scale (usually 1 through 9) that rates how tested and proven a tech is – from basic principles observed (TRL 1) up to actual system proven in operational environment (TRL 9). For AI, a TRL assessment might consider if the algorithm has been validated in lab only or in real-world pilots, whether it’s been integrated with real users, if it’s faced regulatory review, etc. For example, an AI method fresh from research paper might be TRL 3 or 4 (validated in lab), whereas a well-established machine learning method used in many products (like convolutional neural networks for image recognition) might be TRL 8 or 9 for certain domains. TRLs help in decision-making – if an AI component is TRL 5, you know more development and testing are needed to reach deployment-ready maturity. It brings consistency to how teams discuss readiness and risk.
Another framework is pilot/prototype evaluation: essentially testing the AI in increasingly realistic settings to gauge readiness. Sandboxing new AI tech in a small area or with a subset of users can reveal practical issues. Some organizations also use exit criteria – a set of conditions that must be met to declare the tech ready (e.g. must achieve X accuracy on a wide validation set, must run for Y hours without failure, etc.). If those are not met, the tech is deemed not ready for wider deployment.
Ensuring Safe Deployment of New AI Tech
When deploying immature tech, certain precautions can manage risk: very controlled environments (as mentioned, geofenced areas for self-driving car trials), extensive human oversight initially, and a gradual ramp-up. It’s also wise to have a kill-switch or fallback when trying out new tech – e.g., if an AI driving mode misbehaves, the human can instantly take over (as Tesla’s design intends, though human factors make it tricky). Organizations should also stay aware of regulatory developments. For example, if using AI in healthcare, even if laws aren’t in place yet, looking at draft guidelines or industry best practices (like FDA proposed rules or ethics guidelines) can preemptively ensure the tech meets a level of rigor that likely will be required. This is part of being ready not just technologically, but also in compliance and governance.
For mature tech, ensuring safe ongoing use might involve stress-testing it periodically. Just because it’s been stable for 5 years doesn’t mean you shouldn’t challenge it with new scenarios or pen-test it for vulnerabilities (sometimes, attackers find new ways to exploit old systems – e.g., using machine learning to guess inputs that cause worst-case behavior).
Over-reliance Mitigation
To combat complacency with mature tech, organizations can institute periodic reviews and drills. For example, if an AI handles 99% of cases, ensure the team practices handling the 1% manually or when AI is off (like fire drills). Encourage a culture of continued skepticism – treat the AI as an assistant, not an omniscient oracle, even if it’s worked well historically. This mindset ensures people remain vigilant and are watching for any sign of the AI going off-track rather than assuming it never will.
Frameworks and Practices:
- TRL Assessments and Gates: As mentioned, use TRLs or a similar readiness assessment. Some government and industry bodies provide AI-specific readiness checklists (for example, the US Department of Defense might have guidelines on when an AI is mission-ready). Before moving an AI project from R&D to production, hold a review that explicitly evaluates if the technology is at an acceptable readiness level. If not, identify what further development or evidence is needed.
- Prototype in Controlled Settings: For novel AI, start with small-scale pilots. For instance, before a hospital uses a new AI diagnostic tool hospital-wide, they might run it in one department as a trial. Gather results and feedback. This can uncover if the technology meets its promise and if staff are comfortable with it. Only after success in the pilot, expand usage. This phased approach is essentially a practical readiness test.
- Independent Audits and Benchmarking: For both new and established AI, getting an independent evaluation can be valuable. An external audit might test an AI system against known standards or challenge problems. For example, there are robustness benchmarks where multiple AI systems are subjected to adversarial conditions or rare scenarios; seeing how a technology stacks up can tell you if it’s truly ready. If your AI fails badly in these benchmarks compared to others, it indicates immaturity or at least areas to improve before real deployment.
- Fallback Plans: When deploying a new AI-driven process, always have a way to revert to the previous system or a manual process if things go wrong. This might mean keeping the legacy system running in parallel for a while (hot backup) or having manual procedures that can be enacted. This ensures that if the technology doesn’t perform as expected, operations and safety aren’t compromised. It also gives confidence to regulators or management that you’re not all-in without safety nets.
- User Education on Technology Limits: If introducing an immature tech to users, be upfront about its experimental status and proper use. For example, a beta feature in software can carry a disclaimer. In more critical scenarios like a driver-assist AI, educating the driver that “this is not full self-driving, you must keep attention” is crucial (Tesla’s documentation does this, though user behavior doesn’t always follow). When people know a technology is not fully proven, they are more likely to use it cautiously and report issues, which actually helps maturation.
- Continual Improvement and Updates: As the technology matures, update the deployment. For instance, early versions might require heavy human oversight, but if over time the AI proves itself, you can gradually relax constraints (with evidence to back that decision). Always incorporate lessons learned into the next version – this sounds obvious, but it requires capturing the data and feedback systematically. Many AI projects fail to loop back real-world data for improvement. Having a pipeline to retrain models with new data, or to tune rules based on observed usage, progressively increases the technology’s readiness for broader, more autonomous use.
- Staying Current with Research and Standards: For mature systems, ensure you’re aware of any new findings that might affect them. Sometimes a technique long thought safe is found to have a blind spot by researchers. By monitoring academic and industry research, one can pro-actively update an AI system. Also, as standards emerge (like IEEE or ISO standards for specific AI applications), align the system with them. For example, if a standard for AI transparency in credit scoring is published, even a mature credit AI can be reviewed and updated to comply, reducing risk of future regulatory issues or trust erosion.
In essence, technology readiness risk is about knowing where on the innovation curve you are and acting accordingly. If you’re on the cutting edge, apply extra caution, testing, and oversight. If you’re on the well-trodden path, don’t fall asleep at the wheel – continue to evaluate and prepare for the rare bump on the road. A balanced, informed approach ensures that when an AI technology is deployed, it’s truly ready – meaning it’s been proven to the degree needed, and everyone involved knows its limits and how to deal with them. As a structured approach, organizations that use readiness frameworks and maintain a culture of due diligence will navigate the introduction of AI technologies much more safely, aligning with the risk-based approach advocated by standards like ISO 42001.
Connecting to ISO/IEC 23894 for Deeper Insights
ISO/IEC 23894:2023 (Guidance on AI risk management) is a valuable companion to ISO 42001, offering detailed guidance that can enhance understanding and implementation of Annex C topics:
Comprehensive Risk Catalog
ISO 23894 provides a catalog of common AI-related objectives and risk sources in its Annexes A and B that mirrors ISO 42001 Annex C. This catalog delves into each item – for example, it expounds on what “fairness” entails and lists types of bias to consider, and it breaks down “risks related to ML” into specific challenges like data drift, overfitting, adversarial examples, etc. Organizations can use these detailed descriptions to inform their risk assessments and controls. Essentially, ISO 23894 turns the one-word bullets of Annex C into multi-faceted guidance – serving as a reference manual for understanding each objective/risk in depth.
Risk Management Process Alignment
ISO 23894 follows ISO 31000’s risk management process, mapping it to AI. It guides organizations to identify, analyze, evaluate, and treat AI risks at each stage of the AI system life cycle. For instance, it recommends identifying risks like lack of transparency or data bias during the design phase, evaluating their likelihood and impact (perhaps suggesting qualitative or quantitative methods), and then treating them with appropriate controls. By using ISO 23894, organizations implementing ISO 42001 can ensure they’re not just ticking off objectives, but actively managing the underlying risks in a structured way. It provides practical examples – e.g., how to integrate risk considerations when selecting training data or deploying a model – which can be directly adopted as best practices.
Best Practice Examples
Throughout ISO 23894, numerous examples and case studies illustrate effective risk management. These often highlight the very objectives and risks of Annex C. For example, ISO 23894 might describe a case of a financial firm ensuring fairness by conducting bias testing at multiple points (aligning with our fairness best practices), or a scenario of addressing “level of automation” by introducing human oversight in an autonomous process. It also likely includes tables or annex content mapping risk sources to possible controls. Organizations can learn from these examples to inform their own governance measures. Essentially, ISO 23894 functions as a knowledge repository of what works in AI risk management, derived from international consensus – leveraging this can shortcut the learning curve and provide confidence that your approach aligns with global best practices.
Focus on Organizational Capability
ISO 23894 emphasizes that managing AI risk is not just about the technology; it’s about having the right organizational structures and competencies . It likely advises on roles (e.g., risk owners for AI, oversight committees) and the importance of training – reinforcing the “AI expertise” objective. For instance, ISO 23894 might suggest that interdisciplinary teams evaluate risks, ensuring AI experts and domain experts collaborate. It might also highlight the need for awareness training so that staff can identify and escalate AI-related issues. By following these pointers, an organization builds the internal muscle (expertise and process) to sustain its AI management system. This directly complements ISO 42001, which requires resources and competence (Clause 7) – ISO 23894 gives guidance on what competencies and resources are needed specifically for AI risk.
Ethical and Societal Context
ISO 23894 frames AI risks in terms of potential impacts on individuals and society (e.g., fairness, human rights, environmental impact). It provides an internationally accepted perspective on ethical AI considerations. This can help organizations interpret Annex C objectives in light of broader values. For example, it links fairness to human rights and non-discrimination principles, or safety to harm definitions in ISO Guide 51. Thus, using ISO 23894 can deepen an organization’s appreciation of why these objectives matter and how regulators or society might view them. It might also reference relevant regulations or frameworks (OECD AI Principles, etc.), guiding organizations to ensure their governance is in line with emerging legal norms – which is especially useful as laws like the EU AI Act come into play.
Continuous Improvement Guidance
ISO 23894 encourages monitoring and improvement of the risk management process itself. For organizations implementing ISO 42001, this means they can use ISO 23894’s advice to periodically review if their handling of Annex C objectives is effective. Are risk controls for transparency actually reducing lack-of-explainability incidents? Are new risk sources emerging? ISO 23894 provides a mindset and possibly tools (like maturity models or checklists) to evaluate and upgrade the AI governance framework over time, ensuring ongoing alignment with best practices.
In summary, ISO/IEC 23894 offers the “how-to” details and international consensus wisdom that bolster each objective and risk consideration in ISO 42001 Annex C. By consulting ISO 23894, organizations can validate that their interpretation of, say, “robustness” or “transparency” is comprehensive and not missing important facets. It helps translate the high-level goals of ISO 42001 into actionable steps and metrics. Where ISO 42001 asks “Have you considered fairness?”, ISO 23894 might enumerate “the types of bias to look for, methods to measure fairness, and example mitigation techniques”. This makes it easier for practitioners to implement ISO 42001 in a rigorous way.
We strongly recommend organizations use ISO 23894 as a guidebook alongside ISO 42001. For each Annex C objective and risk:
- Refer to ISO 23894’s relevant section or annex entry.
- Extract key insights or recommendations.
- Apply those to your context (perhaps documented in your risk assessment or controls design).
This will ensure your AI governance framework not only meets ISO 42001 requirements on paper but is enriched with proven practices and global expertise, leading to more effective management of AI risks.
FAQ
What is ISO 42001 Annex C?
ISO 42001 Annex C is an informative annex in the ISO/IEC 42001 standard (the AI Management System standard) that outlines potential AI-related organizational objectives and risk sources. It offers guidance on what goals an organization might set for responsible AI use (e.g., fairness, transparency) and what risks to watch for (e.g., lack of explainability, system lifecycle issues) when managing AI.
Why is Annex C important for organizations using AI?
Annex C helps organizations bridge the gap between broad AI principles and concrete risk management actions. It identifies key goals and risks specific to AI, which many traditional IT governance frameworks don’t fully address.
How does Annex C relate to ISO/IEC 23894 and other AI-related standards?
ISO/IEC 23894:2023 is a guidance standard on AI risk management. Annex C of ISO 42001 complements ISO/IEC 23894 by listing AI-specific risk sources and objectives – effectively providing a checklist of what 23894’s risk guidance should cover.
What are the key organizational objectives outlined in Annex C?
Annex C suggests 11 potential AI governance objectives for organizations. These include:
- Accountability: Maintaining clear responsibility for AI outcomes even when AI aids or automates decisions.
- AI Expertise: Building internal expertise with interdisciplinary AI specialists to effectively assess and deploy AI.
- Availability & Quality of Data: Ensuring high-quality training, validation, and test data for AI (critical for ML-based systems).
- Environmental Impact: Recognizing AI’s environmental footprint (energy use, etc.) and striving for positive or minimized impact.
- Fairness: Preventing unfair bias or discrimination in AI-driven decisions.
- Maintainability: Keeping AI systems maintainable, so they can be updated or fixed as needed.
- Privacy: Protecting personal and sensitive data used by AI from misuse or improper disclosure.
- Robustness: Designing AI to be resilient and perform reliably even on new or evolving data.
- Safety: Ensuring AI systems do not endanger human life, health, property, or the environment (especially relevant for autonomous systems).
- Security: Addressing new security issues AI brings (e.g., adversarial attacks, data poisoning) beyond traditional IT security.
- Transparency & Explainability: Making both the AI system and the organization’s use of AI transparent. Providing explanations for AI decisions in human-understandable terms.
What are the major risk sources associated with AI systems in Annex C?
Annex C lists seven major AI risk sources that organizations should consider:
C.3.1 – Complexity of Environment
C.3.2 – Lack of Transparency and Explainability
C.3.3 – Level of Automation
C.3.4 – Risks Related to Machine Learning
C.3.5 – System Hardware Issues
C.3.6 – System Life Cycle Issues
C.3.7 – Technology Readiness
Conclusion
Implementing ISO 42001 with a deep understanding of Annex C objectives and risk sources – and using ISO 23894 for additional guidance – equips an organization to deploy AI responsibly and successfully. It creates a proactive governance culture that anticipates risks (from bias to system failures) and addresses them through design, controls, and continuous oversight. By prioritizing fairness, security, safety, privacy, robustness, transparency, accountability, reliability (availability/maintainability), data quality, and building internal AI competency, organizations can confidently harness AI’s benefits while mitigating its pitfalls. This comprehensive approach not only ensures compliance with emerging AI regulations and standards, but also builds trust with customers, regulators, and society – ultimately enabling sustainable and innovative use of AI in line with the principles of trustworthy AI.
Each step taken – whether it’s bias auditing, adversarial testing, thorough documentation, or staff training – contributes to an AI management system where risks are well-managed and objectives are consistently met. By following the structured guidance of ISO 42001 and ISO 23894, organizations can transform Annex C from an informative list into a living practice, thereby operationalizing ethical and effective AI governance. This alignment of people, process, and technology towards common AI objectives will be a key differentiator in the coming years, as those who manage AI well will deliver superior results and trustworthiness.