ISO 27002 VS 27001
Included in ISO 27001
- Clause 0 – Introduction (not a formal clause but sets the context)
- Clause 1 – Scope
- Clause 2 – Normative References
- Clause 3 – Terms and Definitions
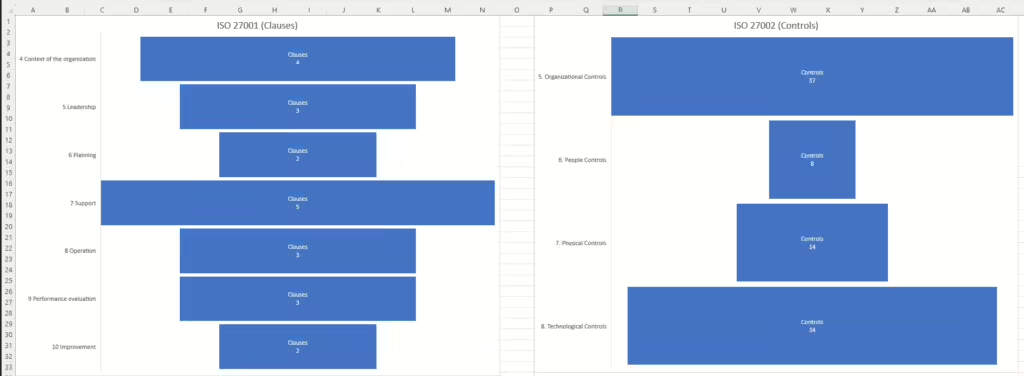
- Clause 4 – Context of the Organization
- Clause 5 – Leadership
- Clause 6 – Planning
- Clause 7 – Support
- Clause 8 – Operation
- Clause 9 – Performance Evaluation
- Clause 10 – Improvement
Included in ISO 27002
- Chapter 5: Organizational Controls
- 37 controls
- Chapter 6: People Controls
- 8 controls
- Chapter 7: Physical Controls
- 14 controls
- Chapter 8: Technological Controls
- 34 controls
The Two Most Talked-About ISO Standards: Why They Matter
Businesses might struggle to secure sensitive data, and we’d all feel less safe online. That’s where ISO standards come in. They’re the architects of cybersecurity, giving organizations a solid framework to protect their information assets and minimize risks.
But here’s the catch: ISO standards aren’t one-size-fits-all. They’re part of a family, each addressing specific aspects of security. Two of the most talked-about standards in this family are ISO 27001 and ISO 27002. While they’re closely linked, they serve very different purposes. Think of them as two sides of the same coin—one setting the foundation and the other fine-tuning the details.
Scope and Objectives
ISO 27001 focuses on establishing and maintaining an Information Security Management System (ISMS). Its main objective is to provide organizations with a framework to manage and mitigate security risks. It’s comprehensive, covering everything from identifying risks to implementing controls and auditing their effectiveness. If your organization seeks certification, ISO 27001 is the standard you’ll follow.
ISO 27002, on the other hand, isn’t about management systems or certification—it’s about implementation. Its purpose is to dive deeper into the controls listed in ISO 27001 and offer practical guidance on applying them effectively. Think of it as a companion manual that helps you answer the “how” behind the “what” outlined in ISO 27001.
If you’re looking for a practical tool to navigate these controls effectively, consider using an ISO 27002:2022 Controls Spreadsheet. It maps out all the updated controls, helping you stay organized and track implementation progress with ease.
| Aspect | ISO 27001 | ISO 27002 |
|---|---|---|
| Focus | ISMS framework | Control implementation guidance |
| Certification | Yes | No |
| Primary Objective | Risk management and governance | Practical application of controls |
Understanding the Core Framework and Controls
The ISO 27001 Clauses and ISO 27002 Controls form the cornerstone of effective information security management. Together, they guide organizations in establishing robust processes for managing risks and implementing security measures. While ISO 27001 provides the overarching framework through its structured clauses, ISO 27002 dives into practical, actionable controls that support implementation. These lists give you a clear roadmap to build, monitor, and enhance your organization’s security posture.
ISO 27001 Clauses List
Clauses 4 - 10
4 Context of the organization
| Clause 4.1 – Understanding the organization and its context |
| Clause 4.2 – Understanding the needs and expectations of interested parties |
| Clause 4.3 – Determining the scope of the information security management system |
| Clause 4.4 – Information security management system |
5 Leadership
| Clause 5.1 – Leadership and commitment |
| Clause 5.2 – Policy |
| Clause 5.3 – Organizational roles, responsibilities and authorities |
6 Planning
| Clause 6.1 – Actions to address risks and opportunities |
| Clause 6.1.1 – General |
| Clause 6.1.2 – Information security risk assessment |
| Clause 6.1.3 – Information security risk treatment |
| Clause 6.2 – Information security objectives and planning to achieve them |
| Clause 6.3 – Planning of changes |
7 Support
| Clause 7.1 – Resources |
| Clause 7.2 – Competence |
| Clause 7.3 – Awareness |
| Clause 7.4 – Communication |
| Clause 7.5 – Documented information |
| Clause 7.5.1 – General |
| Clause 7.5.2 – Creating and updating |
| Clause 7.5.3 – Control of documented information |
8 Operation
| Clause 8.1 – Operational planning and control |
| Clause 8.2 – Information security risk assessment |
| Clause 8.3 – Information security risk treatment |
9 Performance Evaluation
| Clause 9.1 – Monitoring, measurement, analysis and evaluation |
| Clause 9.2 – Internal audit |
| Clause 9.2.1 – General |
| Clause 9.2.2 – Internal audit programme |
| Clause 9.3 – Management review |
| Clause 9.3.1 – General |
| Clause 9.3.2 – Management review inputs |
| Clause 9.3.3 – Management review results |
10 Improvement
| Clause 10.1 – Continual improvement |
| Clause 10.2 – Nonconformity and corrective action |
ISO 27002 Controls List
Annex A - Contols
5 Organizational Controls
| Control 5.1 – Policies for Information Security |
| Control 5.2 – Information Security Roles and Responsibilities |
| Control 5.3 – Segregation of Duties |
| Control 5.4 – Management Responsibilities |
| Control 5.5 – Contact with Authorities |
| Control 5.6 – Contact with Special Interest Groups |
| Control 5.7 – Threat Intelligence |
| Control 5.8 – Information Security in Project Management |
| Control 5.9 – Inventory of Information and other Associated Assets |
| Control 5.10 – Acceptable use of Information and Other Associated Assets |
| Control 5.11 – Return of Assets |
| Control 5.12 – Classification of Information |
| Control 5.13 – Labelling of Information |
| Control 5.14 – Information Transfer |
| Control 5.15 – Access Control |
| Control 5.16 – Identity Management |
| Control 5.17 – Authentication Information |
| Control 5.18 – Access Rights |
| Control 5.19 – Information security in supplier relationships |
| Control 5.20 – Addressing information security within supplier agreements |
| Control 5.21 – Managing information security in the ICT supply chain |
| Control 5.22 – Monitoring, review and change management of supplier services |
| Control 5.23 – Information security for use of cloud services |
| Control 5.24 – Information security incident management planning and preparation |
| Control 5.25 – Assessment and decision on information security events |
| Control 5.26 – Response to information security incidents |
| Control 5.27 – Learning from information security incidents |
| Control 5.28 – Collection of evidence |
| Control 5.29 – Information security during disruption |
| Control 5.30 – ICT readiness for business continuity |
| Control 5.31 – Legal, statutory, regulatory and contractual requirements |
| Control 5.32 – Intellectual property rights |
| Control 5.33 – Protection of records |
| Control 5.34 – Privacy and protection of PII |
| Control 5.35 – Independent review of information security |
| Control 5.36 – Compliance with policies, rules and standards for information security |
| Control 5.37 – Documented operating procedures |
6 People Controls
| Control 6.1 – Screening |
| Control 6.2 – Terms and conditions of employment |
| Control 6.3 – Information security awareness, education and training |
| Control 6.4 – Disciplinary process |
| Control 6.5 – Responsibilities after termination or change of employment |
| Control 6.6 – Confidentiality or non-disclosure agreements |
| Control 6.7 – Remote working |
| Control 6.8 – Information security event reporting |
7 Physical Controls
| Control 7.1 – Physical security perimeters |
| Control 7.2 – Physical entry |
| Control 7.3 – Securing offices, rooms and facilities |
| Control 7.4 – Physical security monitoring |
| Control 7.5 – Protecting against physical and environmental threats |
| Control 7.6 – Working in secure areas |
| Control 7.7 – Clear desk and clear screen |
| Control 7.8 – Equipment siting and protection |
| Control 7.9 – Security of assets off-premises |
| Control 7.10 – Storage media |
| Control 7.11 – Supporting utilities |
| Control 7.12 – Cabling security |
| Control 7.13 – Equipment maintenance |
| Control 7.14 – Secure disposal or re-use of equipment |
8 Technological Controls
| Control 8.1 – User endpoint devices |
| Control 8.2 – Privileged access rights |
| Control 8.3 – Information access restriction |
| Control 8.4 – Access to source code |
| Control 8.5 – Secure authentication |
| Control 8.6 – Capacity management |
| Control 8.7 – Protection against malware |
| Control 8.8 – Management of technical vulnerabilities |
| Control 8.9 – Configuration management |
| Control 8.10 – Information deletion |
| Control 8.11 – Data masking |
| Control 8.12 – Data leakage prevention |
| Control 8.13 – Information backup |
| Control 8.14 – Redundancy of information processing facilities |
| Control 8.15 – Logging |
| Control 8.16 – Monitoring activities |
| Control 8.17 – Clock synchronization |
| Control 8.18 – Use of privileged utility programs |
| Control 8.19 – Installation of software on operational systems |
| Control 8.20 – Networks security |
| Control 8.21 – Security of network services |
| Control 8.22 – Segregation of networks |
| Control 8.23 – Web filtering |
| Control 8.24 – Use of cryptography |
| Control 8.25 – Secure development life cycle |
| Control 8.26 – Application security requirements |
| Control 8.27 – Secure system architecture and engineering principles |
| Control 8.28 – Secure coding |
| Control 8.29 – Security testing in development and acceptance |
| Control 8.30 – Outsourced development |
| Control 8.31 – Separation of development, test and production environments |
| Control 8.32 – Change management |
| Control 8.33 – Test information |
| Control 8.34 – Protection of information systems during audit testing |
Breaking Down the Key Differences
ISO 27002 vs 27001, the distinction becomes clear in their purpose and how they’re applied. ISO 27001 gives us the framework to build and manage a robust ISMS, while ISO 27002 provides the detailed guidance we need to put those security controls into action. This table offers a side-by-side comparison, helping us see how these two standards align and complement each other.
| Aspect | ISO 27001 | ISO 27002 (Annex A) |
|---|---|---|
| Purpose | Establishes requirements for creating, implementing, maintaining, and improving an ISMS (Information Security Management System). It enables organizations to manage risks to their information security effectively. | Provides detailed implementation guidelines for the controls listed in ISO 27001 Annex A. It serves as a best-practice guide to strengthen information security without being certifiable itself. |
| Core Objective | Focuses on setting up an ISMS framework for continual improvement in information security, ensuring alignment with the organization’s strategic objectives. | Supports ISO 27001 by detailing control implementation to address identified security risks practically. |
| Certification | Certifiable by accredited third-party certification bodies, proving that an organization meets information security management standards. | Not certifiable on its own; intended to be a guidance document supporting ISO 27001 implementation. |
| Structure | Organized into 10 main clauses, each specifying requirements for an ISMS, and includes Annex A, listing 93 security controls grouped into 4 themes (people, technology, processes, physical security). | Contains 93 controls aligned with ISO 27001 Annex A, organized by categories like organizational, people, physical, and technical security. Each control includes a purpose, guidelines, and implementation tips. |
| Primary Focus | Focuses on “what” organizations must do to establish, manage, and improve an ISMS systematically, based on risk management principles. | Focuses on “how” to effectively implement security controls. Emphasis is on operationalizing controls to enhance security practices. |
| Risk Management | Requires organizations to conduct a comprehensive risk assessment to identify, evaluate, and manage risks to information security, followed by a risk treatment plan. | Offers guidance on selecting and implementing controls based on risk assessment outcomes performed as per ISO 27001 requirements. |
| Document Requirements | Requires formal documentation for policies, procedures, risk assessments, and statements of applicability. Emphasis on documented evidence for audits. | Provides flexible guidance on documentation without strict requirements, although documentation aids in consistent control implementation. |
| Scope Flexibility | Scope is determined by the organization based on risk assessment, legal, regulatory, and contractual requirements. Organizations can focus on specific areas or enterprise-wide certification. | Non-restrictive scope; guidance can be applied as per organization needs, making it suitable for organizations of all types and sizes. |
| Target Audience | Suited for organizations aiming for ISMS certification and compliance with information security standards, particularly useful for those under regulatory or customer pressure. | Intended for information security managers, technical teams, and other professionals seeking detailed implementation guidance to improve security practices. |
| Implementation | Requires organizations to define and document processes for establishing an ISMS, including security objectives, risk treatment, and ISMS maintenance. | Recommends best practices for implementing each control to meet the requirements of ISO 27001, with flexibility to adapt to organizational context. |
| Compliance and Audits | Sets clear requirements for regular internal audits, management reviews, and continuous improvement to maintain certification. External audits are conducted by certification bodies. | Does not require audits, but encourages monitoring and reviewing control effectiveness to ensure continuous security improvement. |
| Continual Improvement | Emphasizes the Plan-Do-Check-Act (PDCA) cycle to ensure ongoing improvement of the ISMS. Organizational changes, new threats, or incidents require updating the ISMS. | Provides recommendations for control adjustments to align with changes in organizational security needs or emerging threats. |
| Update Cycle | Periodically updated to ensure alignment with evolving information security standards and threats (latest: 2022). | Updated in sync with ISO 27001 revisions to maintain consistency in control requirements and implementation practices. |
| Applicability to Non-Certified Organizations | Primarily beneficial to organizations seeking formal certification; however, it can also guide non-certified organizations looking for a structured ISMS approach. | Valuable for any organization seeking robust security practices, whether pursuing certification or not, as it offers in-depth, practical control insights. |
| Control Details | Lists controls at a high level in Annex A, organized into categories but without implementation specifics. | Describes each control in detail, including purpose, control application, and practical examples, making it more user-friendly for implementation. |