ISO 27001 Clause 6.1.2 Information security risk assessment
Explaining ISO 27001:2022 Clause 6.1.2 Information security risk assessment
Clause 6.1.2 of ISO 27001 focuses on conducting a structured information security risk assessment within your organization’s ISMS. It requires defining clear criteria for assessing risks, identifying potential threats to confidentiality, integrity, and availability, and analyzing their impact and likelihood.

Introduction to Clause 6.1.2 General
When we first approached Clause 6.1.2 Information Security Risk Assessment in ISO 27001, we thought, “How complicated can it really be? Identify risks, check, move on.” But as we dug deeper, we realized there’s so much more to it.
Why Clause 6.1.2
Sure, you can install firewalls and monitor traffic, but how do you know which risks are worth your immediate attention? Clause 6.1.2 helped us step back and create a clear picture of the threats to information security and the opportunities to strengthen our ISMS.
Where Clause 6.1.2 Fits in the ISO 27001 Framework
Clause 6.1.2 is part of a bigger process. Think of it as the bridge between Clause 6.1.1 General, where risks and opportunities are broadly identified, and Clause 6.1.3 Risk Treatment, where actions are taken to address them. This is where we:
- Establish criteria for assessing risks (spoiler alert: this part is critical and comes in the next chapter).
- Identify and analyze risks to understand their potential impact and likelihood.
- Prioritize risks so we can focus our efforts where they matter most.
How We Approached It
When we started, it was easy to feel overwhelmed. Risks seemed to pop up everywhere, and without a clear structure, it felt impossible to know where to start. That’s where templates became our secret weapon. A well-designed ISO 27001 Risk Assessment Template helped us simplify the process, ensuring consistency and reducing the guesswork.
With a structured template, we could focus on what really mattered—evaluating risks systematically and making informed decisions.
Establishing Risk Assessment Criteria – Setting the Foundation
When it comes to Clause 6.1.2, setting up risk assessment criteria is like building the rules of the game. Without clear criteria, the process of identifying, analyzing, and prioritizing risks can feel chaotic. But with well-defined standards in place, you create a structured, repeatable process that ensures consistency and clarity.
Why Risk Assessment Criteria Matter
Think of the criteria as the lens through which you evaluate risks. They help ensure that:
- Everyone in the organization assesses risks the same way.
- Risk levels are comparable across different processes or departments.
- Your assessments align with your organization’s overall risk appetite and goals.
Key Components of Risk Assessment Criteria
Clause 6.1.2 specifies two main areas to focus on:
Risk Acceptance Criteria
This defines the threshold for what your organization considers an acceptable level of risk.- What risks can you tolerate without action?
- What risks require immediate attention?
Example:
- Low risk: A minor website defacement with no customer data involved.
- High risk: Unauthorized access to sensitive financial records.
- Criteria for Performing Risk Assessments
These guidelines define how you’ll identify, analyze, and evaluate risks.
- What information assets will you assess?
- What methodologies will you use (e.g., qualitative vs. quantitative analysis)?
- What will you measure—impact, likelihood, or both?
Our Approach to Setting Criteria
When we worked on establishing criteria, we found that collaboration was key. We brought together stakeholders from IT, compliance, and operations to define what mattered most. This ensured that the criteria reflected real-world priorities and not just theoretical ideals.
We also used a simple framework to structure our criteria:
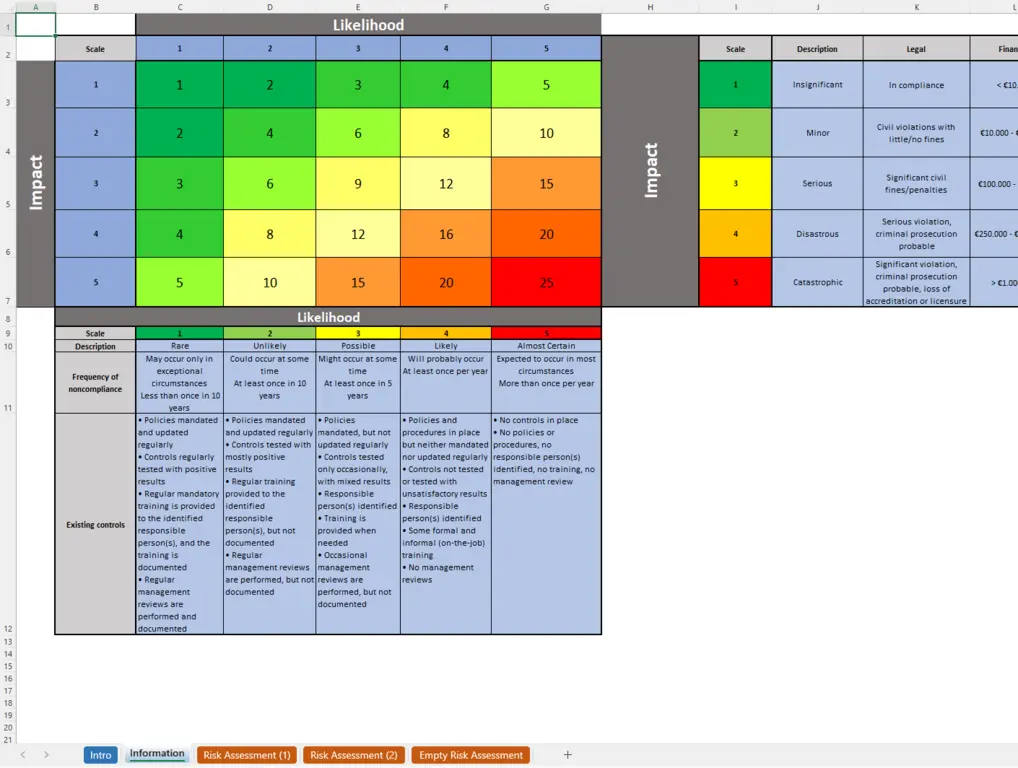
- Impact Scale: Insignificant, Minor, Serious, Disastrous, Catastrophic (e.g., financial loss, reputation damage).
- Likelihood Scale: Rare, Unlikely, Possible, Likely, Almost Certain.
- Risk Levels: Combine impact and likelihood to prioritize actions (e.g., Critical, Major, Minor).
How to Document Your Criteria
ISO 27001 requires you to maintain documented information about your risk assessment process. Ensure your criteria are well-documented, including:
- Definitions for impact and likelihood scales.
- Risk levels and their corresponding actions.
- Any assumptions or methodologies used in the process.
What’s Next?
Now that we’ve defined the rules of the game, it’s time to play. In the next chapter, we’ll dive into the process of identifying and analyzing risks, turning your criteria into actionable insights.
Identifying and Analyzing Risks – Turning Criteria into Action
With your risk assessment criteria established, the next step is to put them into practice. Clause 6.1.2 emphasizes the importance of systematically identifying and analyzing risks to your information assets. This is where theory meets action, and you begin uncovering vulnerabilities and opportunities for improvement.
Step 1: Identifying Risks
Identifying risks is the foundation of your risk assessment process. The goal here is to uncover potential threats to the confidentiality, integrity, and availability (CIA) of your information assets.
How to Identify Risks:
- Define the Scope: Focus on assets within the ISMS’s defined scope, such as systems, networks, processes, or even people.
- Use Your Criteria: Refer to your risk assessment criteria to ensure a consistent approach.
- Engage Stakeholders: Collaborate with IT, compliance, and other teams to identify risks they encounter regularly.
- Review Past Incidents: Analyze past security breaches, audit findings, or near misses to identify recurring risks.
- Perform Threat Modeling: Consider how potential attackers could exploit vulnerabilities, whether they’re internal, external, or environmental.
Example:
- Asset: Customer database
- Risk: Unauthorized access due to weak password policies
Step 2: Assigning Risk Owners
Once you’ve identified risks, it’s essential to assign ownership. A risk owner is the individual or team responsible for managing the risk. This accountability ensures that every risk is actively monitored and addressed.
Tips for Assigning Risk Owners:
- Choose individuals with authority over the impacted asset or process.
- Clearly define their responsibilities, including monitoring, mitigation, and reporting.
- Document ownership in your risk register for transparency.
Step 3: Analyzing Risks
Identifying risks is only half the battle; analyzing them is where you understand their potential impact and likelihood. This helps prioritize risks based on their severity.
How to Analyze Risks:
- Assess Impact: Determine the consequences if a risk materializes. Consider financial loss, operational disruption, reputational damage, and legal implications.
- Assess Likelihood: Estimate how likely the risk is to occur based on historical data, current threats, and vulnerabilities.
- Calculate Risk Levels: Combine impact and likelihood to determine the overall severity of each risk. Use a scale (e.g., Low, Medium, High) or a numerical score.
Example Analysis:
- Risk: Unauthorized access to the customer database
- Impact: High (leakage of sensitive customer data)
- Likelihood: Medium (password policies are weak, but no breach has occurred yet)
- Overall Risk Level: High
Step 4: Prioritize Risks
With risk levels calculated, the next step is prioritization. Focus first on high-risk items that pose immediate threats, then address lower risks as resources allow.
Tip: Maintain a risk register to track all identified risks, their owners, and their current status. This document serves as a living record for your risk management process.
Bridging the Gap – From Risk Assessment to Risk Treatment
By this stage, we’ve worked through the process of identifying, analyzing, and evaluating risks under Clause 6.1.2. But risk assessment is only part of the story. The real value lies in how you act on those insights to safeguard your organization’s information assets. That’s where Clause 6.1.3: Information Security Risk Treatment comes into play.
Why Risk Treatment is the Next Logical Step
Risk treatment is about turning analysis into action. Clause 6.1.3 focuses on selecting and implementing controls to manage the risks you’ve prioritized in Clause 6.1.2. Without this step, your ISMS would be incomplete, leaving identified vulnerabilities unaddressed and your organization exposed.
Let’s quickly recap the flow:
- Clause 6.1.1 (General): This clause set the stage for everything.
- Clause 6.1.2 (Risk Assessment): You identified risks, analyzed their severity, and prioritized them.
- Clause 6.1.3 (Risk Treatment): You’ll now decide how to handle each risk—whether to reduce, transfer, avoid, or accept it—and plan actions to implement those decisions.


