Annex A 8.27 Compliance: ISO 27001 Secure Development Policy Template
The Secure Development Policy Template has been created to provide you with a framework for embedding security into every phase of the development lifecycle, from initial planning to ongoing maintenance.
This template offers the guidance and structure needed to protect your systems, data, and applications against potential vulnerabilities while ensuring full compliance with industry-leading standards like ISO 27001. Very useful when you’re developing new software or managing existing systems, this Secure Development Policy Template for ISO 27001 will help you maintain the integrity, confidentiality, and availability.
Why You Should Buy the ISO 27001 Secure Development Policy Template
- Ensure Comprehensive Security Across the SDLC
This template provides a step-by-step approach to incorporating security into your software development lifecycle (SDLC). By embedding security from the start, you can identify and address vulnerabilities early, rather than waiting until after deployment. The template covers everything from secure coding practices to vulnerability testing, ensuring that your development process is protected at every stage. - Achieve ISO 27001 Compliance
For organizations looking to align with ISO 27001, this secure development policy template ensures you meet the necessary requirements related to secure system architecture and engineering principles. This template simplifies the process of achieving and maintaining compliance, helping you avoid costly security incidents and regulatory penalties while ensuring your systems meet international standards. - Streamline Your Security Policies
The Secure Development Policy Template offers an easy-to-use, customizable solution for organizations looking to streamline their security policies. Instead of starting from scratch, you’ll receive a well-structured, detailed policy that can be tailored to your specific business needs. By using a pre-built template, you save time, reduce costs, and eliminate guesswork. - Protect Your Organization from Emerging Threats
Cyber threats are constantly evolving, and without strong security measures, your development processes are vulnerable to attack. This ISO 27001 Secure Development Policy is made to help you stay ahead of emerging threats, ensuring that your systems are resilient to the latest security risks. From encryption to incident response, the template includes proactive strategies that will safeguard your organization’s critical assets. - Tailored for Secure Outsourced Development
In many cases, development is outsourced to third-party vendors, making it crucial to ensure that external partners follow the same high standards of security as your internal teams. The secure development policy template includes dedicated sections on managing supplier and third-party security, helping you mitigate risks related to outsourced development. Ensure that your vendors and suppliers comply with your organization’s security standards, and maintain full control over their activities. - Boost Developer Productivity with Secure Automation
By automating security checks within the SDLC, developers can focus on innovation while ensuring that all security requirements are met. This template helps you integrate security automation tools—such as static and dynamic code analysis, vulnerability scanners, and penetration testing—into your development processes. Automation helps identify and fix vulnerabilities before they reach production, reducing the risk of costly security incidents later on. - Enhanced System Isolation with Secure Virtualization
As virtualization technology continues to transform the way businesses manage resources, it’s essential to implement secure virtualization techniques. The Secure Development Policy Template includes detailed guidance on how to create isolated and secure virtual environments, helping you minimize the risk of cross-VM attacks. By leveraging secure hypervisor management, network segmentation, and encrypted virtual machine configurations, your organization can ensure a secure virtual infrastructure. - Comprehensive Tamper Resistance Measures
Tamper resistance is a key feature of any robust security strategy. The template provides best practices for detecting and preventing tampering—both physical and logical—on critical systems. From hardware tamper detection to hashing and digital signatures, you’ll have the tools necessary to detect unauthorized modifications and respond promptly to prevent breaches or data theft. - Holistic Security Architecture Integration
Your secure development practices must integrate seamlessly with your existing security architecture. This secure software development lifecycle policy template ensures that your systems, applications, and infrastructure are fully aligned with your organization’s broader security infrastructure, including Identity and Access Management (IAM), Public Key Infrastructure (PKI), and Data Loss Prevention (DLP) solutions. With this alignment, you create a cohesive defense that spans every aspect of your IT environment. - Continuous Improvement and Monitoring
Security is never static—it’s an ongoing process that requires continuous monitoring and regular updates. This template incorporates a framework for continuous improvement, ensuring that your development processes evolve with new threats, industry standards, and business requirements. You’ll be able to monitor vulnerabilities, test systems regularly, and implement improvements to keep your security posture strong and adaptable.
Key Features of the ISO 27001 Secure Development Policy Template:
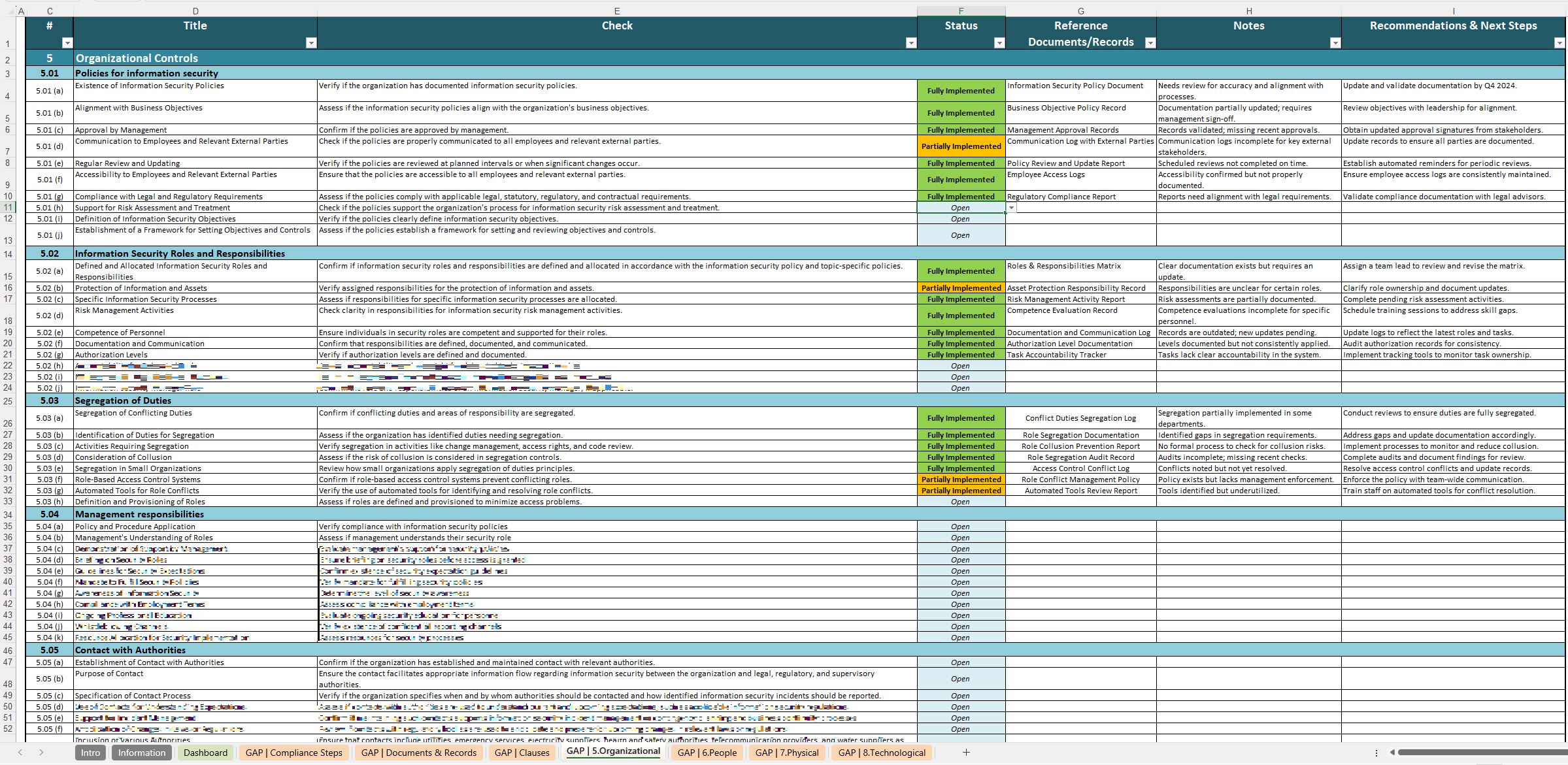
- ISO 27001 Compliance: Aligns with ISO 27001 Control 8.27 requirements for secure system architecture, making compliance easier to achieve and maintain.
- Customizable: Tailor the template to meet your organization’s specific development needs, regardless of industry or project scale.
- Security Best Practices: Includes best practices for secure coding, vulnerability management, encryption, incident response, and more.
- Supplier and Outsourced Development Management: Ensures that third-party partners follow your security guidelines, reducing risks related to outsourced development.
- Virtualization Security: Offers detailed guidance on secure virtualization techniques, providing system isolation and robust hypervisor security.
- Tamper Resistance: Covers physical and logical tamper resistance strategies, from hardware protections to integrity checks and monitoring.
- Automation of Security Testing: Streamlines secure development processes by integrating automated security testing tools, ensuring vulnerabilities are identified early in the development cycle.
- Continuous Monitoring and Improvement: Facilitates the ongoing monitoring of security measures, helping you stay ahead of evolving threats.
Who Is This Template For?
The Secure Development Policy Template is designed for:
- Software development teams looking to implement secure coding and development practices across their projects.
- IT security professionals responsible for safeguarding systems and ensuring compliance with security standards.
- CISOs and IT managers aiming to align development processes with industry standards like ISO 27001 while mitigating risks related to third-party suppliers.
- Organizations of any size that need a ready-to-use solution for securing their development activities without having to build policies from scratch.
Benefits of Purchasing the Secure Development Policy Template:
- Save Time and Resources: No need to spend countless hours creating policies from the ground up. This ready-made template gets you up and running quickly.
- Boost Security Across All Projects: Ensure that security is built into every project, reducing vulnerabilities and safeguarding your organization’s data.
- Ensure Compliance and Avoid Penalties: Avoid regulatory penalties by ensuring your development processes comply with international standards like ISO 27001.
- Protect Against Future Threats: Stay ahead of emerging cyber threats with a policy that is designed to adapt and evolve with new security challenges.