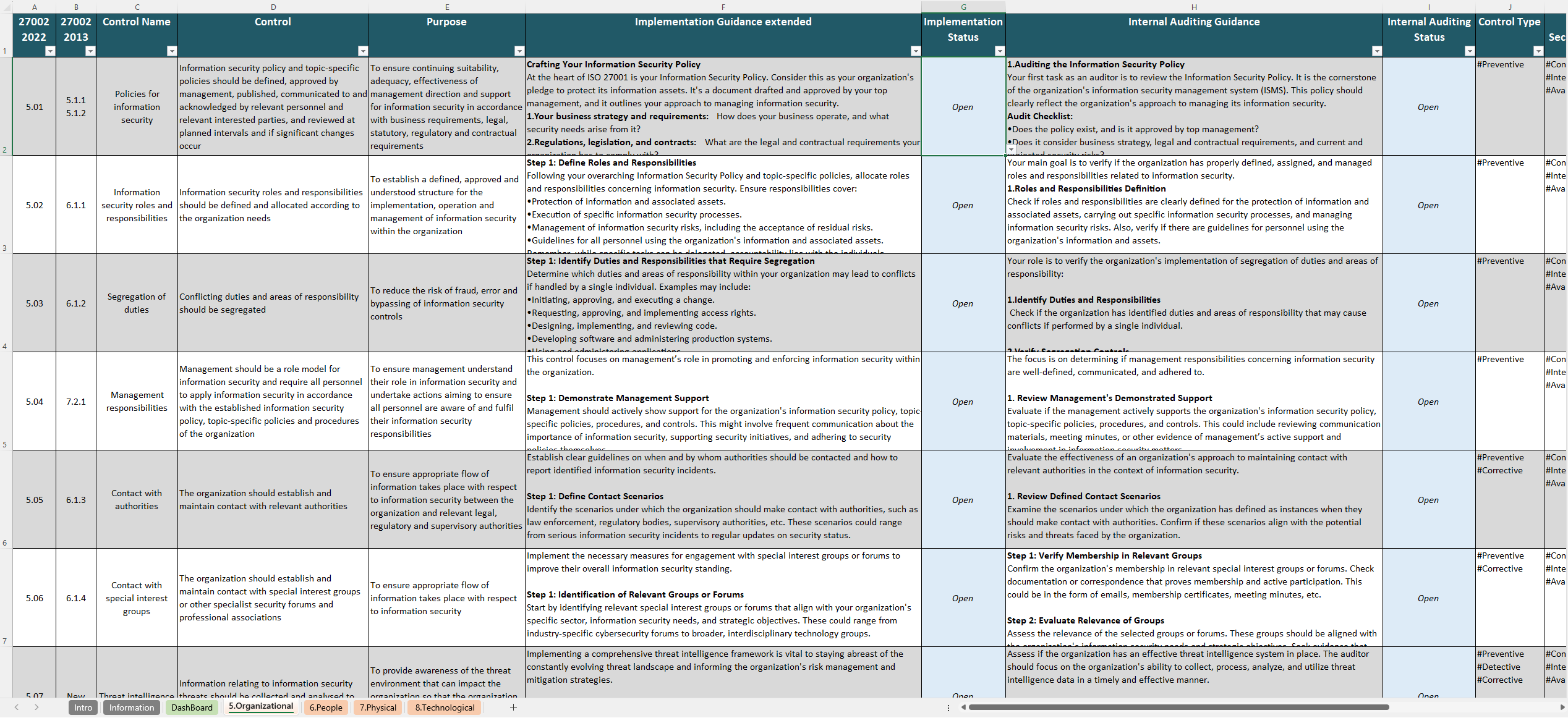
Thorough ISO 27001 Password Policy Template to Satisfy Control 5.17
Establishing secure and compliant password practices is crucial for any organization that handles sensitive information. Our ISO 27001 Password Policy Template offers a ready-made framework designed to align with the ISO 27001 (ISO 27002) standard, including specific guidance for Control 5.17. From password complexity requirements to user training recommendations, this resource covers every detail needed to strengthen authentication protocols while meeting international compliance benchmarks.
What Makes Our ISO 27001 Password Policy Template Stand Out?
- Ready-to-Use Structure
Our ISO 27001 Password Policy Template is fully developed, enabling you to insert your organization’s details and roll out a secure password strategy much faster. - Aligned with International Standards
The template provides explicit alignment with ISO 27001 and ISO 27002 recommendations, ensuring that you meet the key criteria auditors look for in an ISMS. - Designed for Control 5.17
Control 5.17 (in ISO 27001 / ISO 27002) details the necessity for reliable password management. This template includes all relevant points—such as defining secure authentication methods and ongoing monitoring—to help you address Control 5.17. - Provided in a Completely Editable Word Format
Our ISO 27001 Password Policy Template allows you to customize its contents in Microsoft Word, facilitating easy alignment with your brand or organizational structure.
Example Elements of the ISO 27001 Password Policy Template
- Password Creation and Complexity
- Minimum length specifications
- Mandatory mix of letters, numbers and symbols
- Guidelines to prevent overly simple or repeated credentials
Adherence to these principles deters brute-force attacks and enforces uniformity in password strength.
- Protection and Storage
- Recommended encryption for password databases
- Methods for safeguarding credentials during transmission
- Guidance on access controls to prevent unauthorized retrieval
Following these steps helps prevent intercepts and breaches from compromised databases.
- Lifecycle and Maintenance
- Frequency and triggers for password resets
- Deactivation protocols for dormant accounts
- Automated notifications to encourage timely updates
A well-structured lifecycle routine minimizes vulnerabilities from outdated or unused credentials.
- Monitoring and Compliance
- Audit logs for login attempts
- Procedures for addressing suspicious access activities
- Regular reviews to keep pace with emerging threats
Continual observation and timely updates are essential for maintaining an effective, ISO-aligned password strategy.
Direct Connection to Control 5.17
Control 5.17 prioritizes the establishment of secure, well-defined authentication mechanisms. Key points include:
- Thorough Definition of Access Needs: Identify which roles require specific levels of system access to optimize password rigor accordingly.
- Structured Password Policy Management: Introduce encrypted storage, reliable reset procedures and strong verification steps to protect credentials effectively.
- Ongoing Improvement: Continuously revisit and refine policy elements to counteract newly discovered vulnerabilities.
Who Can Benefit from This Template?
- Startups and Mid-Sized Companies: Quickly formalize password regulations and avoid common cybersecurity pitfalls.
- Large Enterprises: Enforce uniform, enterprise-wide password rules while simplifying compliance audits.
- Public Sector Entities: Strengthen public trust by implementing recognized ISO 27001 standard of protective measures.
- Highly Regulated Industries (Finance, Healthcare, etc.): Minimize legal exposure by adhering to strict security requirements.
Implementation and Customization
- Review the Sections
Each segment of the template mirrors an ISO 27001 requirement and clarifies how to fulfill it. - Adapt to Organizational Context
Personalize content around your existing workflows, access levels and risk landscape. - Deploy and Educate
Introduce the updated policy throughout the company and use the included training outlines for effective employee onboarding. - Monitor Progress
Conduct frequent audits and policy reviews, reflecting ISO 27001’s focus on continuous improvement and risk management.
Advantages of Using the ISO 27001 Password Policy Template
- Compliance
Implementing a policy that’s already mapped to ISO 27001 standard—particularly Control 5.17—you prepare your organization’s audit readiness and credibility. - Increased Security
Enforcing carefully defined password rules cuts down on attacks like credential stuffing and guesswork-based intrusions. - Clarify Onboarding
A clearly written template lays out expectations, assisting both new and existing staff in maintaining best practices. - Structured Documentation
Properly organized policy documents make it easier to demonstrate diligence during certifications or external examinations.
Takeaways
This ISO 27001 Password Policy Template provides the guidelines—covering everything from password composition to training methods—while pinpointing the requirements of Control 5.17. Adopting these practices, your organization can meet the ISO 27001 standard, increase cybersecurity defenses and demonstrate commitment.
Secure your future and maintain compliance by integrating this template into your governance framework.