ISO 27002 controls spreadsheet
- Excel document
- Guide to implementing ISO 27002 2022 controls
- Streamline control implementation aligned with ISO 27002.
- Prioritize, document, and assess security controls.
- Gain full oversight of control deployment.
- Supports a layered security strategy.
What is the ISO 27002 Controls Spreadsheet?
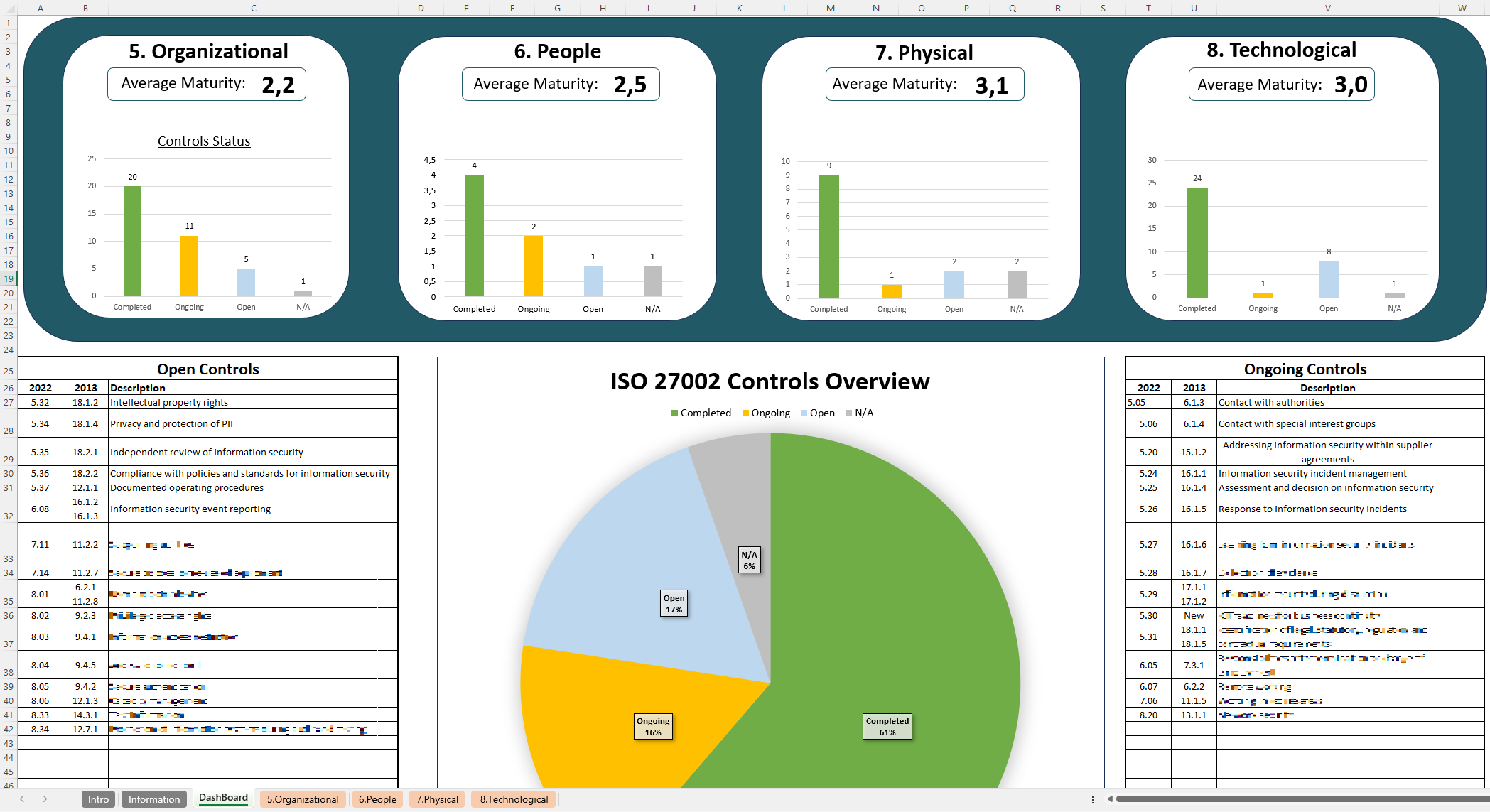
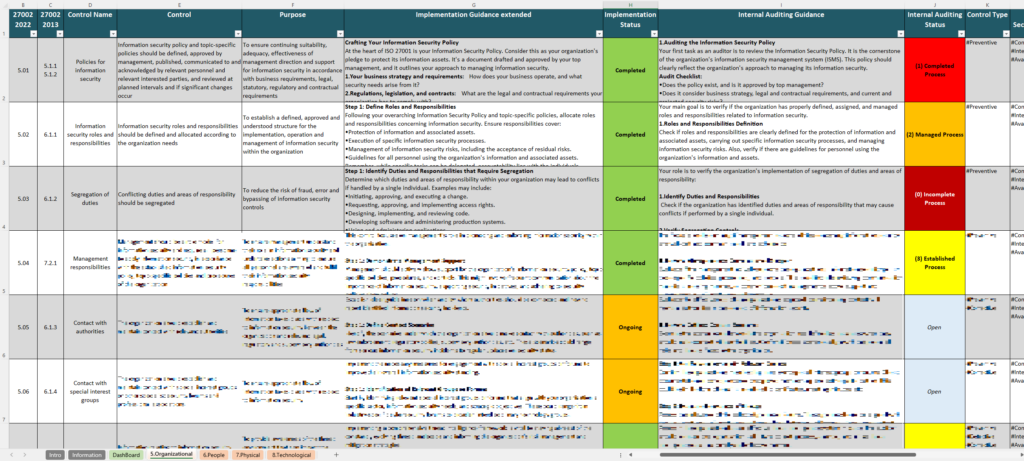
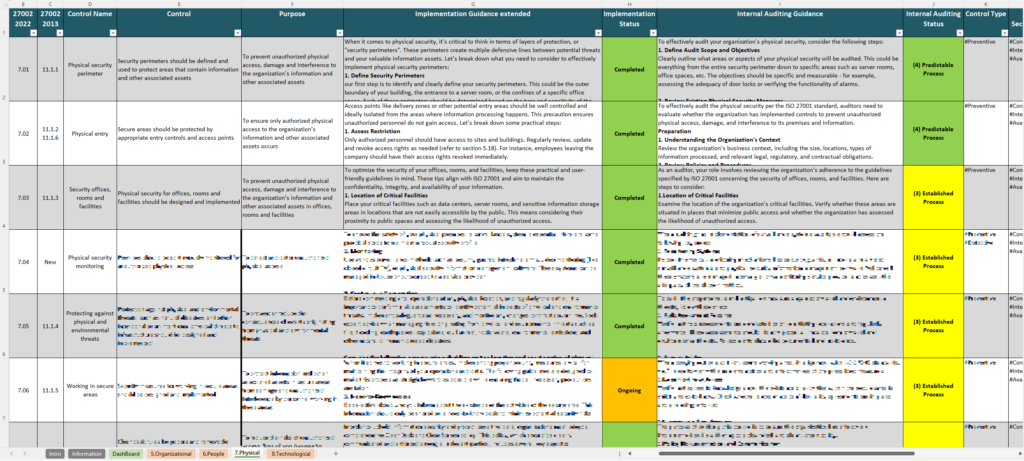
With a user-friendly format, the ISO 27002 Controls spreadsheet breaks down all ISO 27002 controls—recently updated to include 93 controls in four categories: Organizational, People, Physical, and Technological. Each control is presented with space for documentation and tracking, enabling users to map, assign responsibilities, and record audit findings with ease. This tool is valuable for organizations seeking ISO 27001 certification or aiming to align their security practices with global standards, offering a clear way to organize and demonstrate compliance
What is ISO 27002?
ISO 27002 is an internationally recognized standard providing guidelines for implementing information security controls. ISO 27002 offers detailed recommendations on selecting and applying specific controls to manage information security risks. It focuses on the practical side of security management by suggesting specific measures to protect assets.
The standard has been updated in 2022. This latest version simplifies the control structure, reducing the total number of controls from 114 to 93 and organizing them into four main categories: Organizational, People, Physical, and Technological.
Difference Between ISO 27002 and ISO 27001
ISO 27001 and ISO 27002 are complementary standards within the ISO 27000 family, both focused on information security. However, they serve distinct roles within an Information Security Management System (ISMS). Understanding their differences is essential for organizations aiming to implement or certify their security frameworks effectively.
ISO 27001: Framework for an ISMS
ISO 27001 is the primary standard for establishing, implementing, maintaining, and continuously improving an ISMS. It outlines a high-level management system based on risk assessment and management, helping organizations protect their information assets systematically. ISO 27001 sets specific requirements and mandates regular internal audits and management reviews to ensure ongoing compliance. Additionally, organizations can achieve formal certification for ISO 27001, demonstrating their commitment to security to clients and partners.
ISO 27002: Guidelines for Security Controls
While ISO 27001 defines “what” needs to be achieved for information security, ISO 27002 provides the “how.” It offers detailed guidance on implementing specific security controls to support the objectives in ISO 27001’s Annex A. These controls range from access management and cryptography to incident response. Unlike ISO 27001, ISO 27002 is not a certifiable standard; instead, it serves as a best-practice guide that organizations can adapt to their needs.
The standard has been updated in 2022. This latest version simplifies the control structure, reducing the total number of controls from 114 to 93 and organizing them into four main categories: Organizational, People, Physical, and Technological.
Understanding the Controls in ISO 27002
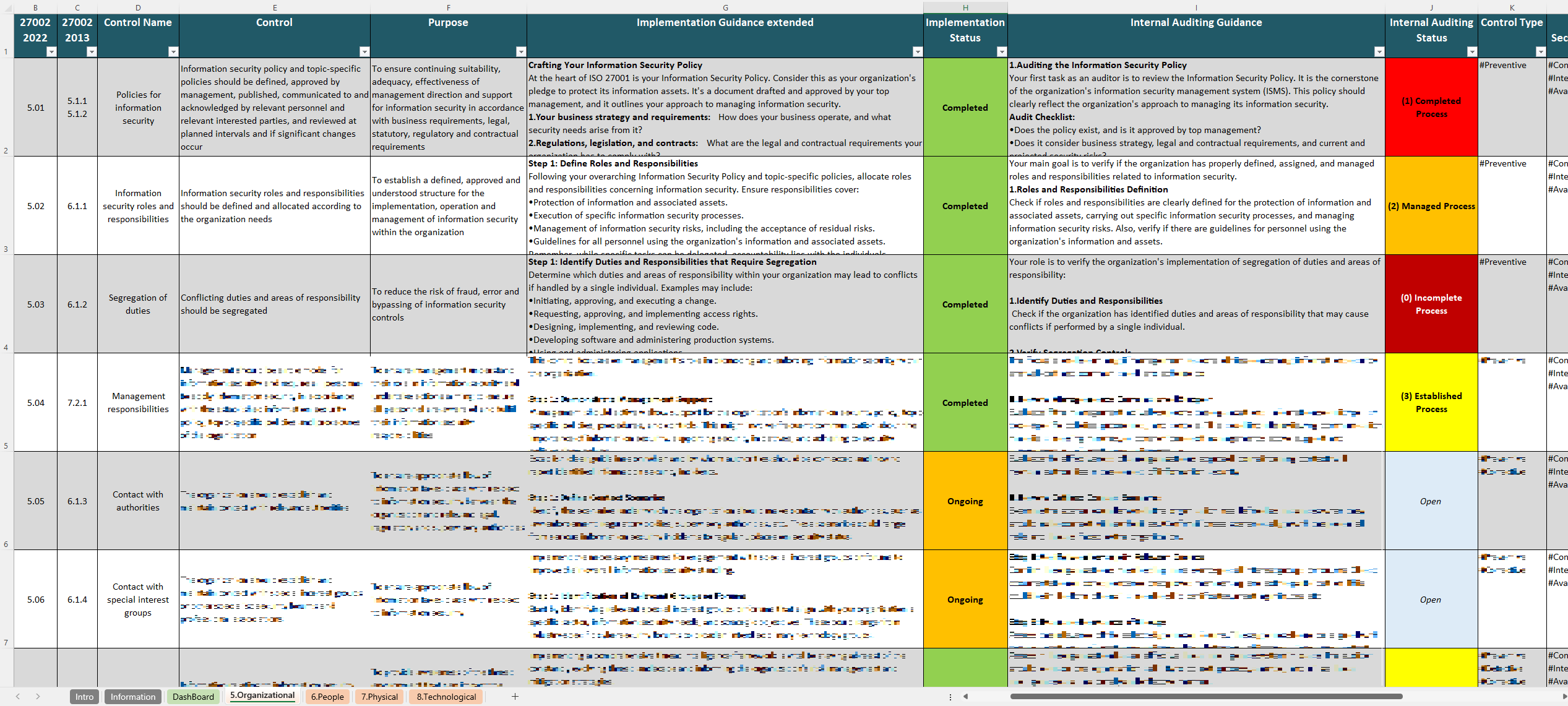
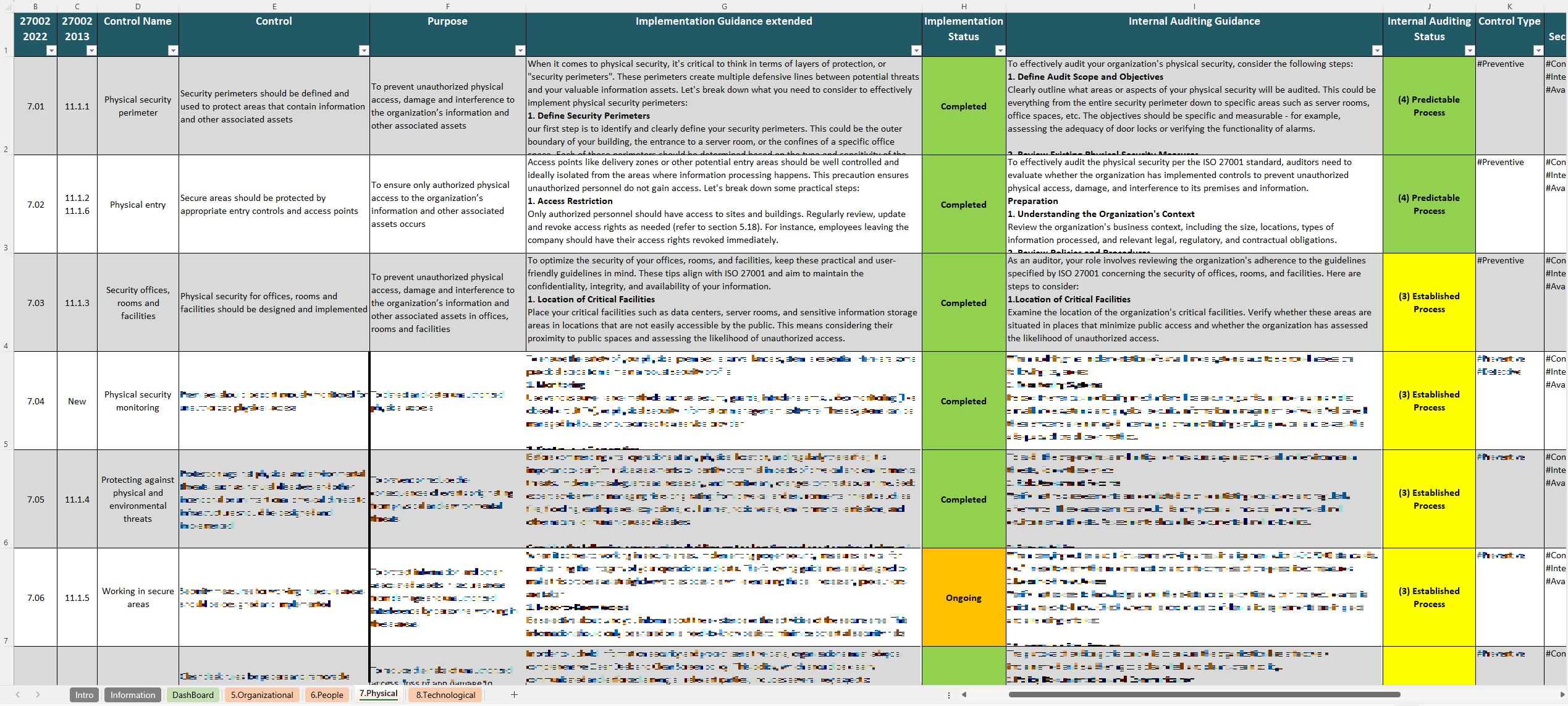
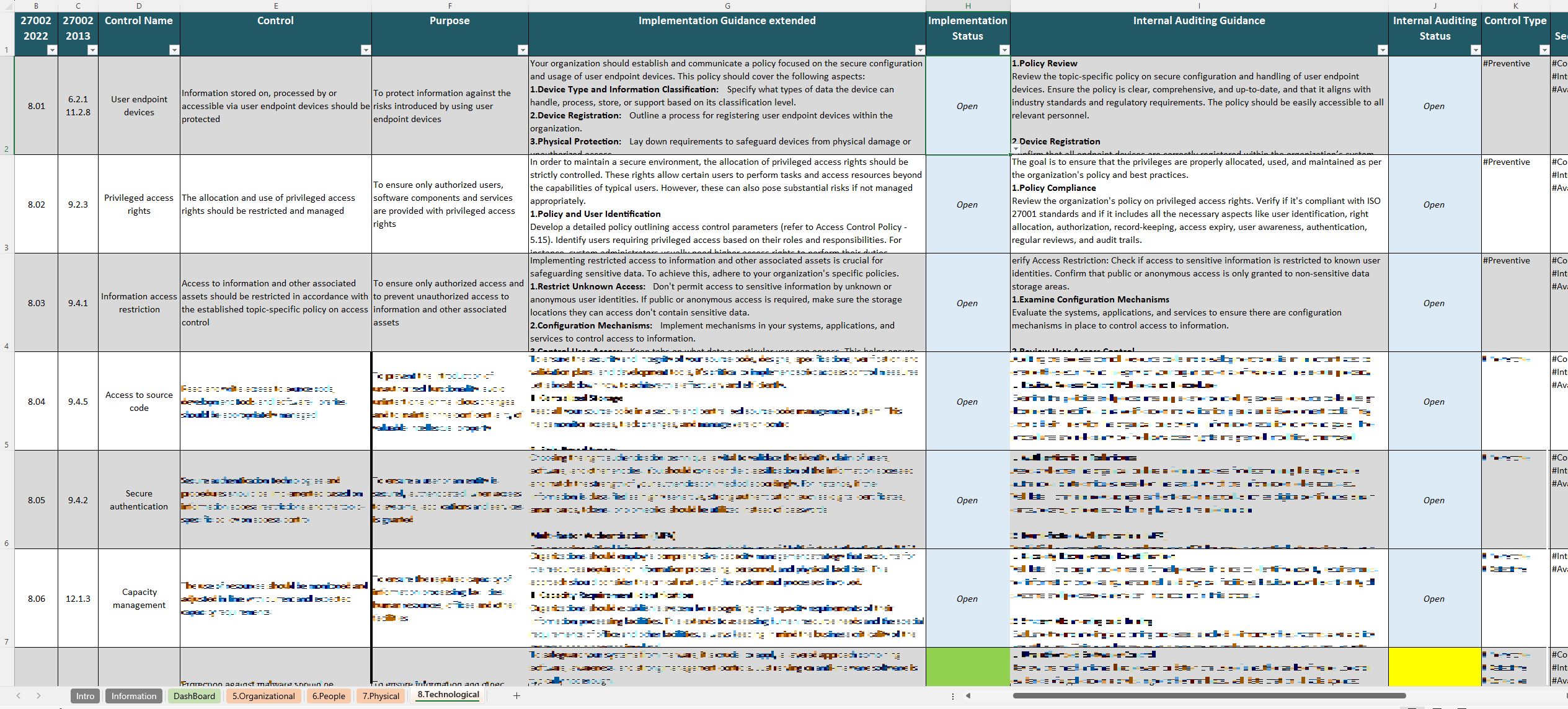
The controls in ISO 27002 are the core of the standard, providing the specific security practices organizations can adopt to protect their information assets and support their Information Security Management System (ISMS). The ISO 27002 Controls Spreadsheet is a great tool for tracking and managing these controls, allowing users to systematically implement each one as part of their security strategy.
In the 2022 update, ISO 27002 reorganized the 114 controls from the previous version into 93 streamlined controls across four categories: Organizational, People, Physical, and Technological. This restructuring reflects modern security needs, addressing new areas like cloud security and threat intelligence to help organizations stay resilient in today’s cyber landscape.
ISO 27002 Control Categories:
- Organizational Controls: These controls focus on governance, policy development, and procedural aspects. They include risk management, supplier relationships, and roles and responsibilities, making it easier for organizations to structure their approach to information security.
- People Controls: Centered around staff and user behavior, these controls include training, security awareness, and background checks. The ISO 27002 Controls Spreadsheet can be used to monitor compliance with these requirements, helping organizations reduce human risk factors.
- Physical Controls: Addressing the protection of physical assets, these controls cover areas like facility security and physical access restrictions. They are crucial for preventing unauthorized physical access to sensitive systems and locations.
- Technological Controls: This category includes controls for managing technology, such as cryptography, network security, and access control. With the ISO 27002 Controls Spreadsheet, organizations can keep track of these technical implementations and monitor their status across departments.
Benefits of Using an ISO 27002 Controls Spreadsheet
The ISO 27002 Controls Spreadsheet enables organizations to centralize all information security controls in one accessible document, simplifying the management process. With all controls in a single, organized location, teams can easily assign responsibilities, monitor status, and record updates. This centralized approach streamlines collaboration across departments and ensures that everyone involved in information security has access to the same up-to-date information.
This spreadsheet is particularly useful for organizations working toward ISO 27001 certification, as it aligns directly with the Annex A controls listed in ISO 27001. By using this spreadsheet, organizations can prepare thoroughly for both internal and external audits. The tool facilitates the documentation of control implementation, providing auditors with a clear and detailed record of compliance efforts.
Implementing and tracking ISO 27002 controls can be complex and time-consuming without the right resources. The ISO 27002 Controls Spreadsheet helps streamline this process by providing a ready-to-use template that reduces the need for manual tracking. This efficiency allows security teams to focus on optimizing controls and responding to potential risks, rather than managing extensive documentation.
Organizations can easily edit the ISO 27002 Controls Spreadsheet to their specific needs. Controls can be adjusted to reflect different levels of risk, industry requirements, or organizational policies. This flexibility ensures that the controls implemented are both relevant and effective, enhancing the overall impact of the security framework.
The spreadsheet helps with compliance and also strengthens an organization’s overall security by supporting risk management efforts. By tracking and reviewing controls regularly, organizations can proactively identify gaps, evaluate risk levels, and implement necessary changes. This structured approach to risk management helps build a resilient ISMS that adapts to security challenges.
Why Choose This ISO 27002 Controls Spreadsheet?
The ISO 27002 Controls Spreadsheet is designed to make managing ISO 27002 controls straightforward and effective. Here’s why it stands out:
- User-Friendly Design: The spreadsheet offers a clear, organized format to track and update controls, saving time and reducing complexity for security teams.
- Built for Compliance: It aligns directly with ISO 27001 Annex A, making it a great data resource for organizations aiming to achieve or maintain ISO 27001.
- Editable Controls: Adapt controls to fit your specific security needs and industry requirements. This flexibility ensures the tool remains relevant and practical across different security contexts.
- Audit-Ready: The spreadsheet simplifies audit preparation by keeping all control documentation in one place, allowing for quick, accurate compliance verification.
Protect Your Business with CyberZoni
- Virtual CISO
- Vulnerability Scanning
- Control Design and Implementation