Data Security in Project Management
Early consideration of data security requirements for the product or service (e.g. at the planning and design stages), can lead to more effective and cost-efficient solutions for quality and data security.
In this Article
What is Data Security in Project Management?
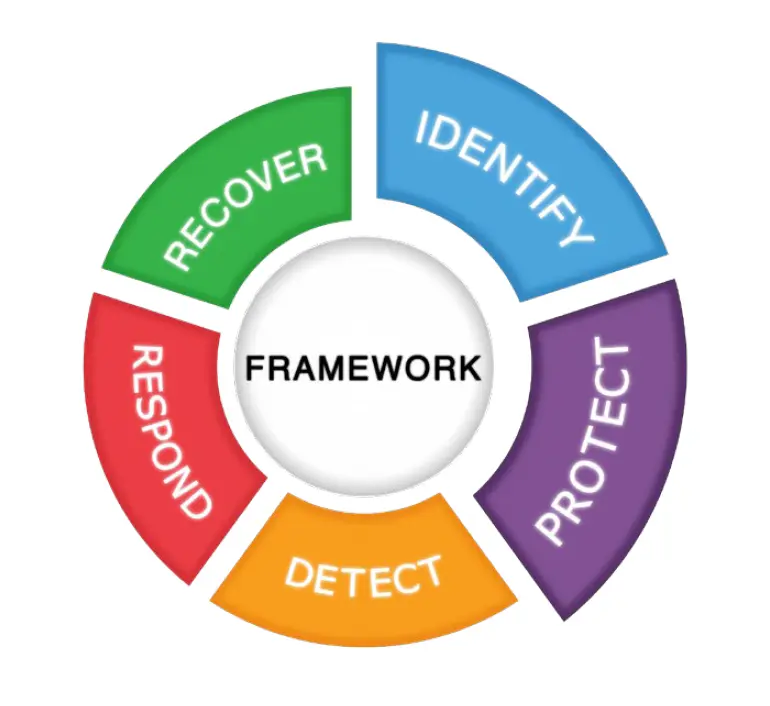
Data security in project management refers to the protection of sensitive information involved in project activities from unauthorized access, breaches, and data corruption. This includes ensuring the confidentiality, integrity, and availability of project-related data throughout its lifecycle.
Project managers are responsible for implementing data security measures that safeguard critical assets, such as client information, project documentation, and financial data. Some essential security practices include encryption, access controls, secure file sharing, and backup strategies. The integration of these practices into project management minimizes the risk of data breaches and ensures compliance with industry standards like ISO 27001 and NIST’s cybersecurity frameworks.
ISO 27001 Control 5.8 Information Security in Project Management
Implementing ISO 27001 Control 5.8 Information Security in Project Management can be a highly effective security measure. Control 5.8 Information Security in Project Management, emphasizes the integration of information security into project management across all stages of the project lifecycle. This control aims to ensure that security risks are identified early, treated consistently, and monitored throughout the project. It applies to all types of projects, from business processes to IT and facility management, and stresses the importance of addressing confidentiality, integrity, and availability concerns.
MITRE ATT&CK
Utilizing frameworks like MITRE ATT&CK can further strengthen data security by identifying potential vulnerabilities and threats early in the project lifecycle. By mapping out potential attack vectors using a structured approach, project managers can proactively address data security concerns, ensuring that countermeasures are in place to protect sensitive information.
Why is data security important in project management?
Project data often includes sensitive information such as intellectual property, financial details, customer data, and strategic plans. Ensuring the confidentiality, integrity, and availability of this information is essential for several reasons:
- Protecting Sensitive Information: Project management often involves handling confidential business information or proprietary technology. Breaches or unauthorized access to this data could lead to significant financial losses, reputational damage, and potential legal consequences.
- Compliance with Regulations: Many projects must comply with industry regulations, such as the General Data Protection Regulation (GDPR) or NIST’s data security standards. Failing to meet these requirements could result in hefty fines and other legal repercussions.
- Minimizing Business Risks: A breach or data loss during a project could disrupt operations, delay deliverables, and negatively impact stakeholder trust.
- Maintaining Competitive Advantage: Projects often involve strategic initiatives, new product developments, or partnerships. Unauthorized exposure of project-related data could give competitors an edge or diminish the value of the company’s innovations.
How does project management software help with data security?
Key ways in which project management software contributes to data security include:
- Access Control and Permissions: Project management software allows administrators to set role-based access controls.
- Data Encryption: Many project management platforms offer encryption for data both at rest and in transit. This ensures that sensitive information, such as financial records or client details, is protected from interception or unauthorized access during communication between team members. Encryption also helps maintain the integrity of the data, preventing unauthorized modifications.
- Secure Collaboration: Project management software often includes secure file sharing and communication tools, which ensure that all exchanges within the platform remain encrypted and protected from external threats. These tools help project teams collaborate efficiently while maintaining strict security protocols.
- Audit Trails and Monitoring: Most modern project management software includes audit trails and activity logs, allowing administrators to track who accessed what data and when. This feature is vital for detecting suspicious behavior and responding quickly to potential security incidents. It also aids in compliance by providing a clear record of data handling throughout the project.
What are the most important security features of project management software?
Project management software is a critical tool for ensuring the secure handling of sensitive project data. Some of the most important security features that effective project management software offers include:
- Role-Based Access Control (RBAC): One of the most crucial features is role-based access control, which allows administrators to define specific user roles and permissions. This ensures that only authorized individuals can access, edit, or manage sensitive data, reducing the risk of unauthorized access and potential breaches.
- Data Encryption (In-Transit and At-Rest): Data encryption is fundamental to securing sensitive information. Many project management tools use encryption protocols like SSL/TLS for data in transit, and AES encryption for data at rest, ensuring that even if data is intercepted or compromised, it remains unreadable to unauthorized parties.
- Two-Factor Authentication (2FA): Two-factor authentication adds an extra layer of security by requiring users to verify their identity through an additional method beyond just a password (e.g., a one-time code sent to a mobile device). This significantly reduces the risk of unauthorized access, even if a password is compromised.
- Audit Logs and Activity Tracking: Comprehensive audit trails and logs allow project managers and security teams to monitor user activity within the system. These logs track who accessed or modified data and when, making it easier to detect and investigate suspicious activities or potential breaches.
- Data Backup and Recovery: Many project management platforms provide automated backups and disaster recovery options. This ensures that project data can be quickly restored in the event of data loss, ransomware attacks, or other disruptive incidents.
- Compliance Management: Leading project management tools offer built-in features that help organizations stay compliant with various data protection regulations, such as GDPR, HIPAA, and NIST guidelines. These compliance features ensure that sensitive data is managed according to legal standards, reducing the risk of regulatory penalties.
Tips/advice for keeping project data safe
Keeping project data safe requires a comprehensive approach that includes both technical and procedural safeguards. Below are some key tips and best practices for ensuring project data security:
- Implement Strong Access Controls: One of the most effective ways to secure project data is to limit access to only those who need it. Use role-based access controls (RBAC) to ensure team members have appropriate levels of access based on their roles. Regularly review and update these permissions to reflect any changes in the team.
- Use Data Encryption: Encrypt all sensitive data both in transit and at rest. This ensures that even if data is intercepted or compromised, it cannot be read without the proper decryption keys. Modern encryption protocols such as SSL/TLS should be used for data in transit, while AES encryption is common for data at rest.
- Conduct Regular Security Audits and Monitoring: Regularly monitor and audit access to project data using built-in activity logs or third-party tools. Security audits help identify unauthorized access attempts or unusual activity, allowing you to address vulnerabilities before they can be exploited.
- Ensure Regular Data Backups: Maintain frequent backups of critical project data to protect against data loss caused by accidents, ransomware, or system failures. Ensure that these backups are stored securely and test recovery processes regularly to verify the integrity of the backups.
- Train Your Team on Data Security Practices: One of the most significant vulnerabilities in data security comes from human error. Regularly train your team on best practices, such as recognizing phishing attacks, using strong passwords, and securely sharing data. A well-informed team can act as a first line of defense against security threats.
- Use Secure File Sharing and Collaboration Tools: Avoid sharing sensitive project data via unsecured methods, such as email. Instead, use project management tools that offer secure file sharing features, which ensure that files are encrypted and only accessible by authorized team members.
Tips/advice for small businesses choosing project management software who want to protect data
When small businesses select project management software, data security should be a top priority. Below are some practical tips for ensuring that the chosen platform offers strong data protection:
- Prioritize Platforms with Strong Encryption: Ensure the software encrypts data both at rest and in transit. Look for platforms that use industry-standard encryption protocols, such as AES for data at rest and SSL/TLS for data in transit. This ensures that sensitive data is protected from interception and unauthorized access.
- Choose Software with Role-Based Access Controls (RBAC): Look for project management tools that offer fine-grained access controls, allowing you to assign specific roles and permissions. This limits access to sensitive information to only those who need it, reducing the risk of internal data breaches.
- Ensure Regular Updates and Patch Management: Security vulnerabilities can arise if software is not regularly updated. Choose a vendor that provides regular security updates and patches to protect against emerging threats and vulnerabilities.
- Check for Compliance with Security Standards: Verify that the software complies with industry security standards and regulations like GDPR, HIPAA, or NIST. Platforms that adhere to these standards are more likely to have robust security features in place.
- Look for Audit Logs and Monitoring Features: Small businesses should select software that offers detailed audit logs and monitoring features. These logs track user activity and data access, allowing you to monitor for suspicious behavior and quickly respond to potential breaches.
- Ensure Backup and Recovery Capabilities: Choose project management software with built-in data backup and recovery features. This ensures that in the event of data loss—due to cyberattacks, human error, or technical failure—data can be quickly restored with minimal downtime.