The Hardest Part of Cybersecurity: Tackling Cultural Resistance and Security Fatigue in 2024
Why Security Implementation Remains Challenging
Implementing security effectively remains challenging for cybersecurity professionals. They face a constant battle between enforcing strict policies and ensuring convenience for end-users. The dilemma often boils down to balancing robust security with user-friendly protocols—a feat that requires strategy, cooperation, and often a change in workplace culture. So, what are the hardest aspects of security to implement, and how can organizations overcome these challenges?
This article unpacks key hurdles in implementing effective cybersecurity measures and provides actionable insights into fostering a compliant and resilient culture.
In this Article
Main Challenges in Security Implementation
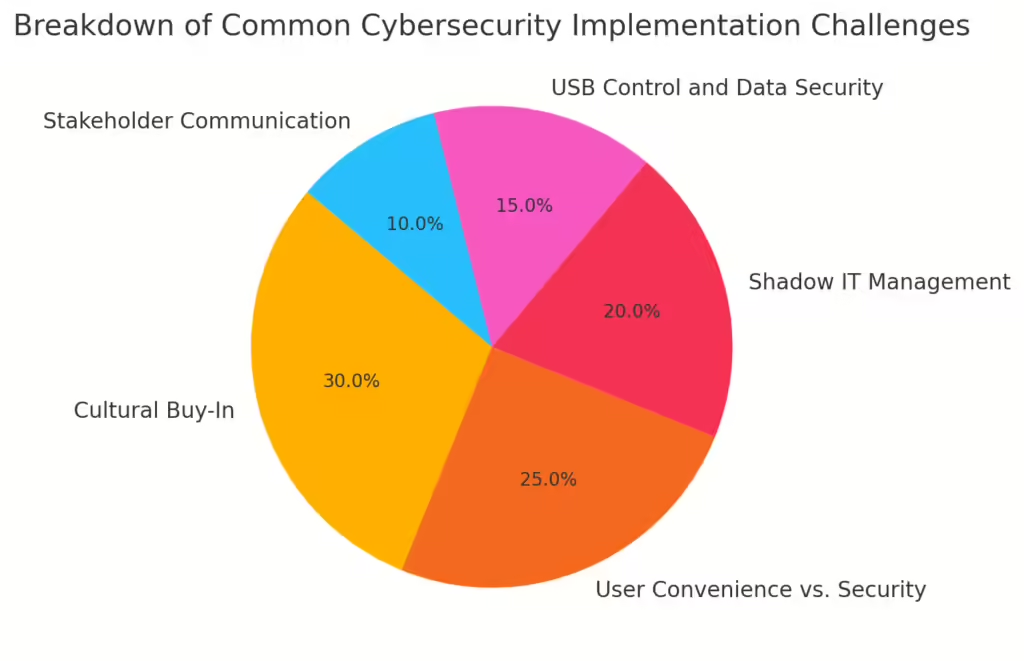
Security implementation in any organization faces a blend of technological, cultural, and procedural challenges. Below are some of the most commonly faced obstacles.
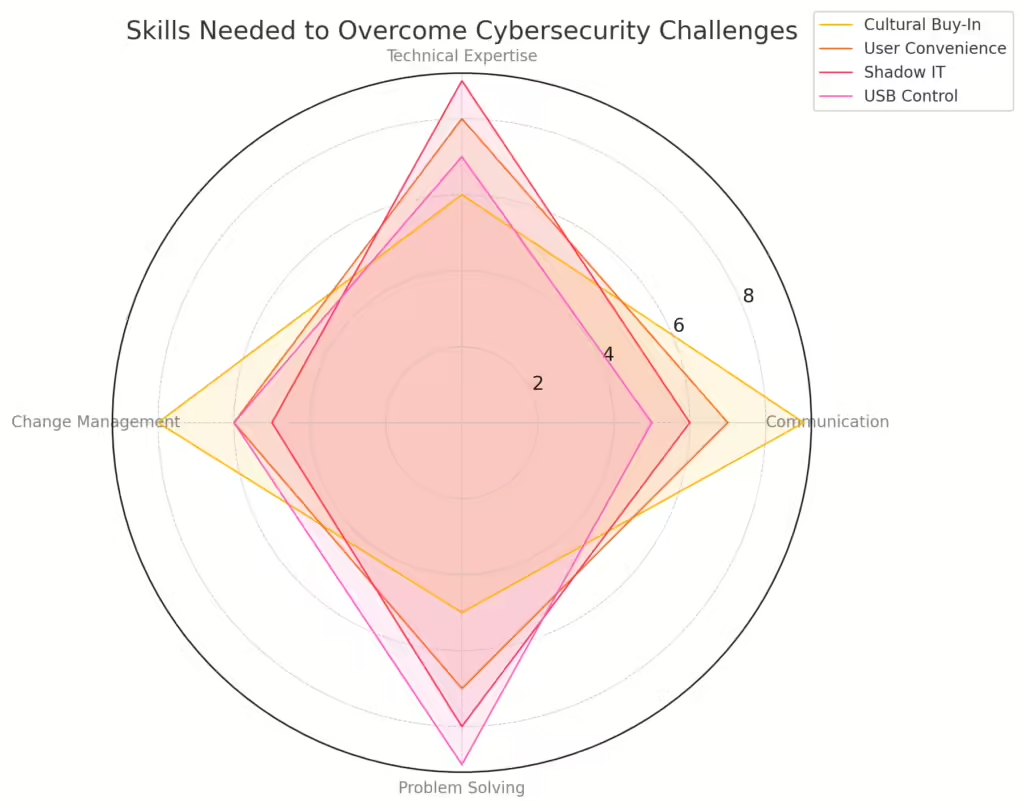
1. Cultural Buy-In: Building a Cyber-Resilient Culture
One of the biggest barriers in security implementation is achieving culture buy-in. Many organizations invest in high-quality tools and policies, but without the willingness of employees to adopt these measures, they fall flat. Resistance, often termed “change fatigue,” can occur when employees grow weary of constant shifts in protocol and security measures. When teams are reluctant to adapt, it becomes challenging for security measures to succeed. This gap between knowledge and buy-in highlights the need for a proactive approach to change management.
Tips for Achieving Cultural Buy-In:
- Educate and Communicate: Regularly explain the “why” behind each security measure.
- Involve Users in Decision-Making: Engage employees in conversations about security protocols to promote ownership.
- Empower Security Ambassadors: Identify security-conscious employees to champion and reinforce security practices.
2. Strict Policies vs. User Convenience
Another common struggle is balancing strict security policies with user convenience. Stricter policies like Role-Based Access Control (RBAC), USB control, and network segmentation are essential but often disrupt workflow. For example, in critical infrastructure systems, segmenting networks or installing firewalls can cause significant friction as employees adapt to new, stringent protocols.
To combat this, companies may opt for incremental changes. Implementing gradual policy changes allows users to adjust, reducing the chance of major pushback and maintaining operational efficiency.
Addressing Common Security Issues Faced by Organizations
When implementing security measures, it’s crucial to recognize common pain points within organizations. Here are some primary issues:
1. Managing Shadow IT: Unapproved Software and Devices
Shadow IT, where employees use unapproved software or devices, introduces unmanaged risks. Security teams may be unaware of these tools, leaving the organization vulnerable to data breaches or security gaps. Overcoming this requires clear guidelines, regular audits, and awareness campaigns to highlight the risks of unregulated tools.
Effective Strategies for Managing Shadow IT:
- Regular Inventory Checks: Conduct periodic audits to detect and mitigate shadow IT risks.
- User Education: Educate employees on why certain software is restricted.
- Approval Processes: Set up a straightforward request system for adding new tools to the approved list.
2. USB Control and Data Security
USB controls and removable media policies often face resistance from employees who rely on these devices for legitimate work tasks. Tightening USB controls can be met with user pushback, especially when policies impact productivity. Companies should implement granular USB exceptions where necessary, allowing specific users access while maintaining a secure overall policy.
Effective Communication: Bridging the Gap with Business Stakeholders
Security implementations often suffer when communication breaks down between cybersecurity teams and business stakeholders. Many non-technical stakeholders may struggle to understand technical aspects, especially when decisions are based solely on graphs and figures. For security measures to succeed, it’s vital to bridge the gap with clear communication and collaborative decision-making.
Tips for Effective Stakeholder Communication:
- Use Business Language: Explain security risks and solutions in terms of business impact rather than technical jargon.
- Highlight Cost-Benefit Analysis: Present the financial and reputational costs of not investing in security measures.
- Showcase Case Studies: Share examples of companies that have benefited from proactive security investments to make your point resonate.
Long-Term Cybersecurity Strategies: Reducing Security Fatigue and Optimizing Implementation
Developing a long-term security strategy goes beyond policies and tools. To maintain momentum and avoid “security fatigue,” organizations need a plan that evolves with the changing cybersecurity landscape.
1. Implementing Zero Trust Network Architecture (ZTNA)
Adopting a Zero Trust approach can streamline security for end-users by creating a secure access model that assumes no implicit trust. This approach, while challenging to implement, reduces the risk of unauthorized access and simplifies security management by focusing on verifying users and devices continuously.
Advantages of Zero Trust:
- Enhanced Data Protection: By requiring verification at each access point, data remains safeguarded.
- User Transparency: Zero Trust measures can often run in the background, reducing interference with user workflows.
- Scalability: Zero Trust models are designed to grow with the organization, adapting to new users, devices, and services seamlessly.
2. Role-Based Access Control (RBAC): Limiting Permissions to Boost Security
RBAC is essential for ensuring that employees have access only to what they need. While straightforward in principle, implementing RBAC in established organizations where employees are used to broad access can lead to resistance. Developing a well-planned, step-by-step implementation can prevent disruption and reinforce security across the organization.
The Road Ahead in Security Implementation
In summary, security implementation requires more than just policies and tools. It demands a change in culture, a balance between convenience and control, and a strategic approach to managing risks like shadow IT. By focusing on cultural buy-in, effective communication, and long-term strategies like Zero Trust and RBAC, organizations can build a resilient and compliant security framework.
Key Takeaways
- Cultural Buy-In Is Crucial: Without employee engagement, security protocols are less effective.
- Balancing Strict Policies with Convenience: Stricter policies are essential but should be implemented incrementally to allow user adaptation.
- Zero Trust and RBAC for Long-Term Success: Adopting a Zero Trust model and RBAC can future-proof an organization’s cybersecurity posture.