ISO 27001 Audit Process: A Complete Certification Guide
Achieving ISO 27001 certification is a significant milestone in showcasing your commitment to information security. This guide breaks down the certification audit process into its two stages, providing a clear understanding of what auditors look for, how they assess your Information Security Management System (ISMS), and tips to ensure a smooth audit experience.
In this Article
What is the ISO 27001 Audit Process for Certification ?
The certification audit is a formal assessment by an accredited auditor to determine if your ISMS aligns with ISO 27001 standards. It’s a two-part process involving Stage 1 and Stage 2 audits, designed to review your documentation and practical implementations.
Ultimately, much of this depends on the auditor. Some auditors may focus on minor, insignificant issues, like “missing a column in your risk assessment sheet” of this paper is not signed (but is approved digitally), and raise unnecessary nonconformities. Others, take a more holistic approach, focusing on understanding your ISMS and the intent of the standard, rather than nitpicking over small and irrelevant details.
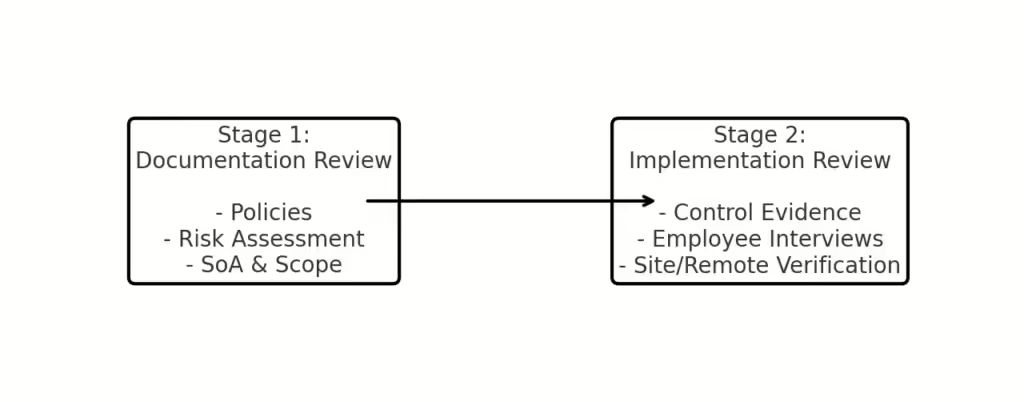
Stage 1: Documentation Review
In the first stage, auditors conduct an in-depth review of your company’s ISMS documentation. They look at:
- Policies and Procedures: Essential ISMS policies, Statement of Applicability (SoA), and scope documentation.
- Risk Assessment and Objectives: Ensuring all risks are identified and managed appropriately.
- Management Review: Evidence of top management commitment to the ISMS, a critical component for certification.
Stage 1 can often be done remotely, making it a convenient way for auditors to verify the design of your ISMS. They also review internal audit findings and management’s response to any non-conformities, as well as the overall scope and context of the organization.
Key Tip: Emphasize Top Management Involvement
Management’s active role in supporting information security is crucial in Stage 1. Demonstrating top management’s commitment, often referred to as the “C-suite buy-in”, is a mandatory requirement that assures auditors your ISMS aligns with ISO 27001’s core principles.
Stage 2: Implementation Review
Stage 2 takes place 1-2 weeks after Stage 1, focusing on how well your ISMS is implemented in practice. During this stage, auditors examine evidence of ISMS operations, interviewing employees and reviewing records to verify compliance with ISO 27001 requirements.
Common Areas Auditors Review in Stage 2
- Sample-Based Controls Review: Auditors typically review a sample of implemented controls to ensure they match your policies. For instance, if your ISMS requires HDD encryption on laptops, the auditor may check a few devices for compliance.
- Supplier and HR Security: Auditors assess your processes for managing supplier relationships and HR security controls, like NDAs and employee onboarding/offboarding.
- Physical and Operational Security: If an on-site audit is necessary, auditors inspect physical security measures, such as building access controls, equipment security, and business continuity plans.
Handling Non-Conformities
When non-conformities are identified, they fall into two categories:
- Minor Non-Conformities: These are issues you can address by the next surveillance audit, allowing certification to proceed.
- Major Non-Conformities: These need immediate correction to issue the certificate. Without resolution, certification may be delayed until remediation is verified.
What to Expect from the Auditor
Auditors are trained to ask targeted questions to assess the effectiveness of your ISMS. They might inquire about recent system changes, staff training, or the management of specific risks. If you’re unsure of a question or need time to gather information, it’s perfectly acceptable to ask for clarification.
Common Audit Focus Areas
- Risk Treatment and Management: Auditors expect a thorough review and treatment plan for identified risks.
- Training and Awareness: Records of training programs and their effectiveness are a common audit focus.
- Compliance with ISO/IEC 27001:2022: This latest update emphasizes criteria for interested parties, process criteria, and new Annex A controls, including Threat Intelligence, Data Loss Prevention (DLP), and Configuration Management.
Geographic Trends in Audits
From experiences across regions, it’s clear that focus areas may vary by country:
- Eastern Europe: Strict adherence to ISO standards, with attention to Annex A controls.
- Northern Europe: Emphasis on risk-based measures.
- Southern Europe: Often focuses on “quick win” controls like HR and physical security.
Key Tips for a Successful ISO 27001 Audit
- Prioritize Documentation: Ensure all ISMS documentation is current and accurate.
- Showcase Management Support: Evidence of top management’s involvement is essential.
- Prepare for Sample-Based Evaluations: Know which controls might be sampled, such as IT asset security or supplier agreements.
- Address Non-Conformities Proactively: Document and plan for any minor issues ahead of Stage 2 to avoid delays.
- Stay Updated on ISO 27001 Changes: Familiarize yourself with updates in the ISO/IEC 27001:2022 standard.
Wrapping Up
The ISO 27001 audit process is a journey toward demonstrating your organization’s commitment to protecting information. With careful preparation, transparency, and engagement from management, the certification process can become a straightforward and rewarding experience.