ISO 27001 Access Control Policy Template Aligned With Control 5.15
Are you looking for a straightforward way to manage user access, secure your digital assets, and demonstrate compliance with ISO 27001 requirements? Our ISO 27001 Access Control Policy Template offers a solid, fully customizable framework made to facilitate achieving and maintaining compliance. This template helps organizations of all sizes implement best-practice access controls, making certain that only the right individuals access the right information at the right time.
Why You Need an ISO 27001 Access Control Policy Template
- Optimized Compliance
Utilizing our ISO 27001 access control policy template reduces guesswork when meeting the requirements of ISO 27001 (and the supporting guidance in ISO 27002). Demonstrate to auditors that your organization takes access control seriously. - Upgraded Security
A properly configured access control policy ensures that unauthorized users cannot view or manipulate sensitive information. This template helps you put the principle of “least privilege” into practice—granting the minimum level of access necessary for employees to fulfill their responsibilities. - Reduced Risk of Data Breaches
By defining detailed user access and authentication measures, you minimize the risk of internal and external threats. This includes managing user roles, monitoring access activities, and ensuring that terminated or transferred employees no longer have unwarranted privileges. - Time and Cost Savings
Crafting policies from scratch can be time-consuming and expensive. With our ISO 27001 access control policy template, you have an deployable document that can be specified to fit your organization’s unique context—saving valuable time and manpower.
Main Features of Our ISO 27001 Access Control Policy Template
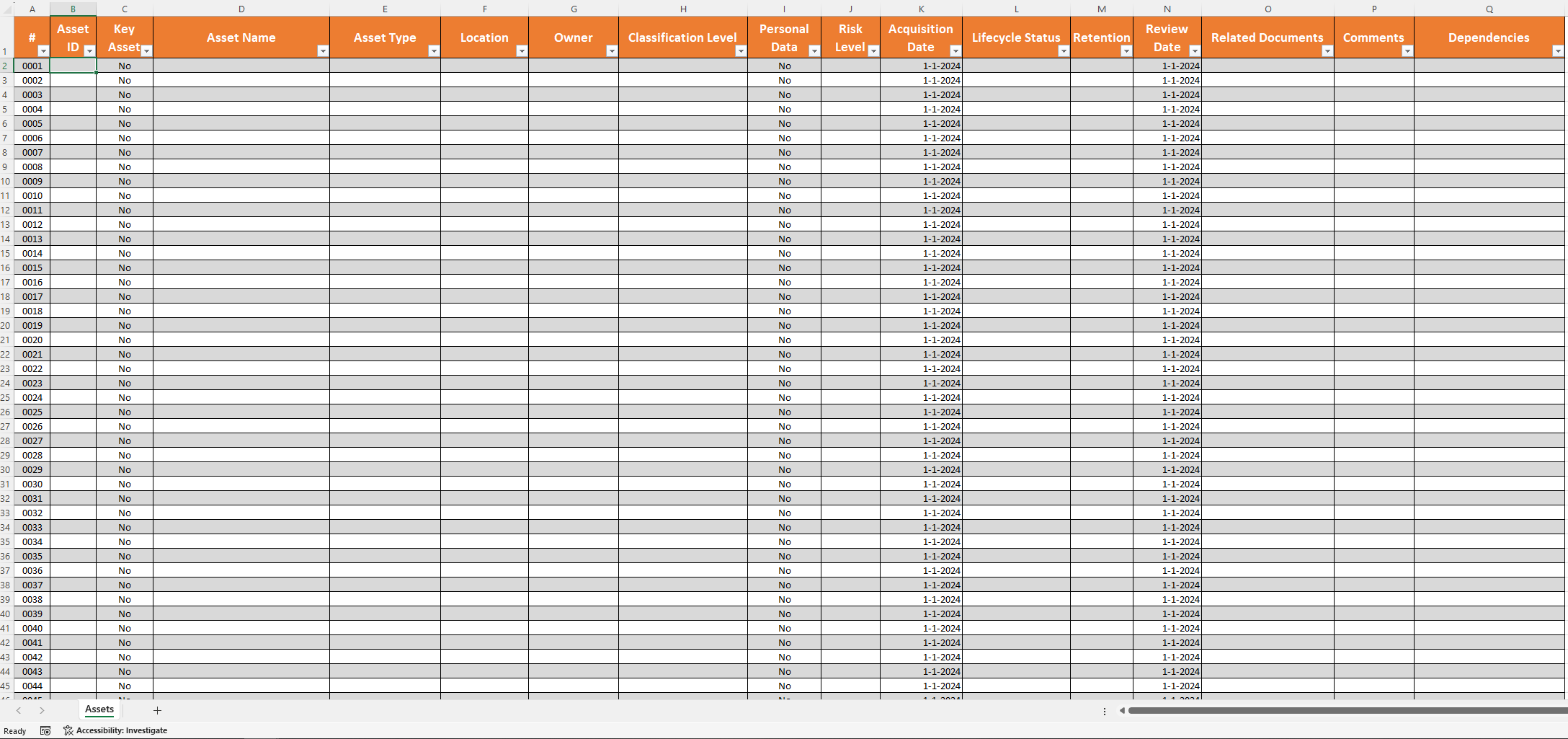
- Role-Based Access Management
Assign and manage privileges based on job responsibilities. This section clarifies how to classify user roles, ensuring everyone has the correct level of access. - Clear Approval Workflows
Define the process for granting, modifying, and revoking user access. This ensures a consistent, traceable, and auditable approach. - Monitoring and Review Framework
Track access logs, review user privileges periodically, and detect suspicious activity early. Proper monitoring and review help maintain continuous compliance. - Incident Response and Escalation
Outline actions to take if unauthorized access is detected. Clearly defined escalation procedures keep your team prepared and minimize damage in critical situations. - Alignment with ISO 27002 Control 5.15
Our template is specifically aligned with ISO 27002 Control 5.15, which focuses on managing access rights and enforcing the principle of least privilege. This alignment ensures that your policy is not just compliant, but also robust and effective against evolving security risks. - Customizable Sections
Every organization has different structures, technologies, and risk appetites. Our ISO 27001 access control policy template includes placeholders and optional sections so you can adapt it seamlessly to your business.
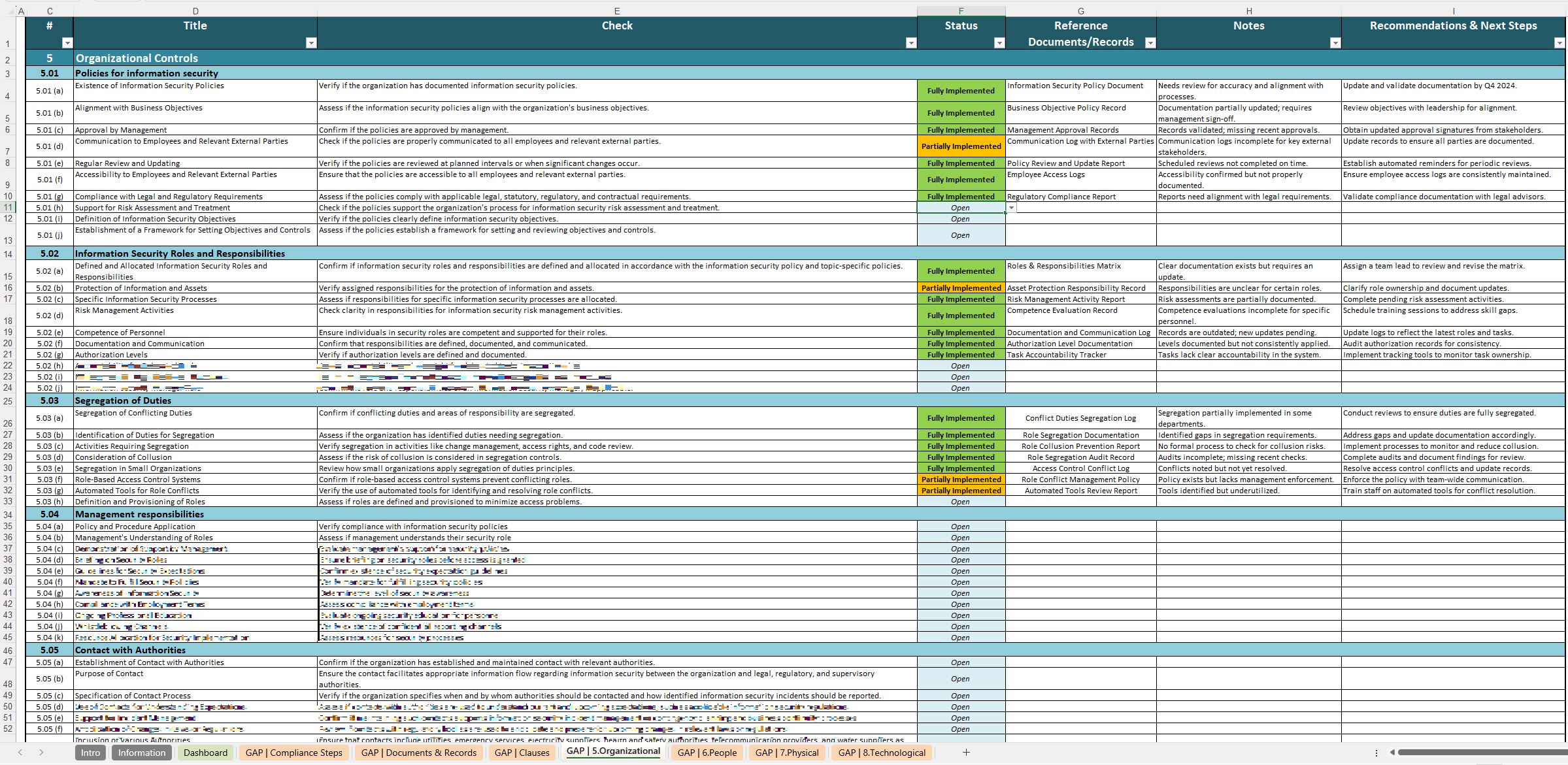
Detailed Alignment with ISO 27001 (ISO 27002) Control 5.15
Control 5.15 within ISO 27002 centers on the importance of establishing, documenting, and enforcing clear guidelines for user access. Our template ensures you:
- Define Roles and Responsibilities: Clearly assign access management tasks (e.g., administrators, HR, line managers) to ensure accountability.
- Implement Principle of Least Privilege: Enforce minimal access for staff and third parties to reduce the chance of data leaks or unauthorized actions.
- Maintain Clear Audit Trails: Track who has accessed what, when, and why. Comprehensive audit logs help maintain transparency and demonstrate compliance.
- Regularly Review Access Rights: Schedule audits to confirm privileges remain aligned with each user’s current role and responsibilities.
How our ISO 27001 Access Control Policy Template Helps You
- Accelerated Audit Readiness
By covering the key compliance points laid out in ISO 27001 and ISO 27002, this template positions you for successful certification audits. Demonstrate immediate compliance with minimal customization. - Fully Editable Microsoft Word Format
Customize every section to align with your organization’s brand, structure, and security protocols. Update content on the fly and effortlessly track changes to maintain version control. - Integration with Existing Frameworks
Already have parts of an ISMS in place? The template complements your existing policies, aligning seamlessly with common frameworks and procedures. - Supports Continuous Improvement
Built-in review cycles, version control tables, and distribution tracking make it easy to update your policy in response to new security threats or organizational changes.
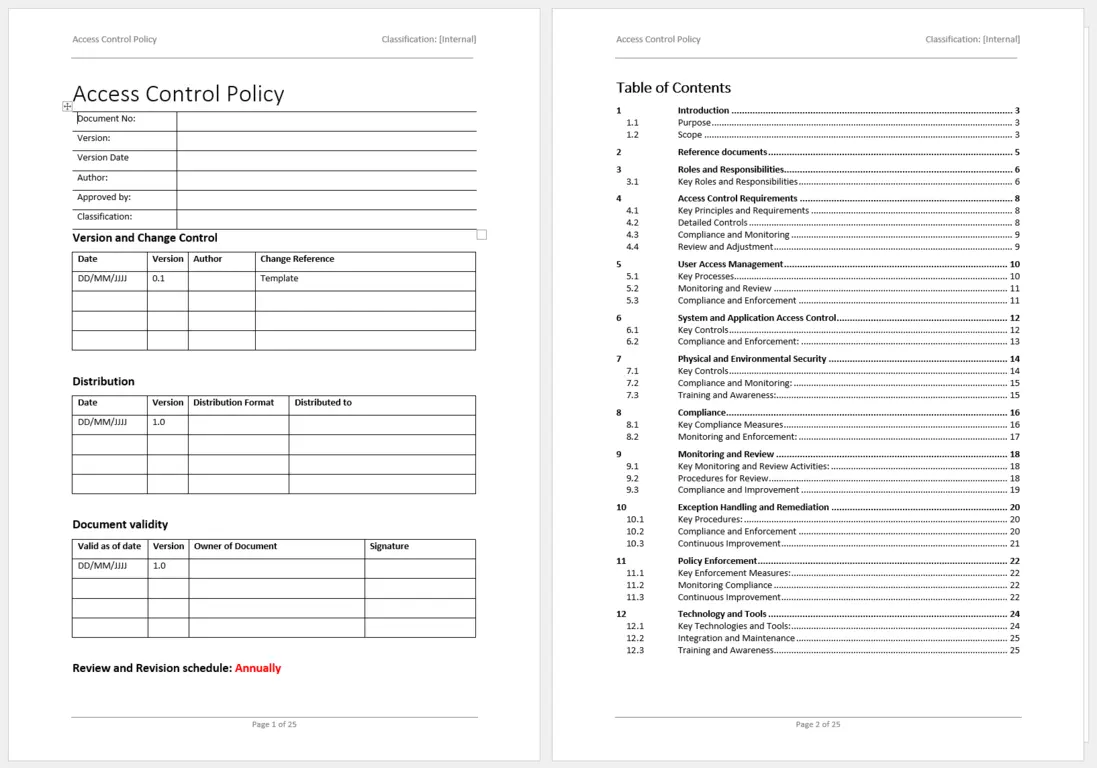
ISO 27001 Access Control Policy Template Contents At a Glance
- Title Page and Document Information
Identify key details such as version number, authors, and approval date. - Table of Contents
Quickly navigate policy sections—from overview and definitions to compliance and enforcement measures. - Policy Overview
Clarify purpose, scope, and responsibilities within your organization. - Roles and Responsibilities
Spell out who manages user accounts, approves new access, and oversees annual reviews. - Detailed Controls
Provide granular guidance on user authentication methods, password policies, and privilege assignments. - Monitoring and Review
Outline how you track system access, generate logs, and conduct periodic access rights reviews. - Incident Reporting and Escalation
Define the steps to take if access control measures fail or malicious activity is suspected. - Policy Enforcement and Exceptions
Clarify disciplinary actions for non-compliance and processes for granting policy exceptions. - Appendices and Reference Documents
Keep references to ISO 27001 and ISO 27002 readily available for quick correlation during audits.
Who Should Use our ISO 27001 Access Control Policy Template?
- IT and Security Managers: Implement user access and IT control measures aligned with ISO best practices.
- Compliance Officers and Auditors: Validate your organization’s security posture and streamline audit preparations.
- HR and Department Heads: Understand how new hires, role changes, and terminations affect system access.
- Small and Medium Businesses: Adopt industry-leading access control standards without the complexity of creating policies from scratch.
- Enterprises: Maintain consistent security frameworks across multiple departments and jurisdictions.
Getting Started
- Download the word Template
Receive a professionally formatted Microsoft Word document. - Customize for Your Organization
Tailor roles, responsibilities, and technical controls to fit your existing environment. - Obtain Management Approval
Share the final policy with executive stakeholders for endorsement. - Communicate and Train
Ensure every team member understands the policy and their responsibilities. - Monitor, Review, and Update
Schedule periodic reviews, track changes, and update the policy as new threats emerge or organizational changes occur.
In Summary
Take the stress out of developing an access control policy from scratch. Our ISO 27001 Access Control Policy Template is a thorough, customizable word document that aligns with ISO 27002 Control 5.15. With this template you’ll strengthen your security posture, streamline compliance efforts, and pave the way for successful ISO 27001 certification.
Stay on track and stay secure—make ISO 27001 compliance manageable with our ISO 27001 Access Control Policy Template!