A Clear View to ISO 27001 Compliance
A clear, well-structured policy helps you define how data is handled, who is responsible for what and why.
Our ISO 27001 Information Security Policy Template makes this process manageable by providing a practical and customizable policy framework.
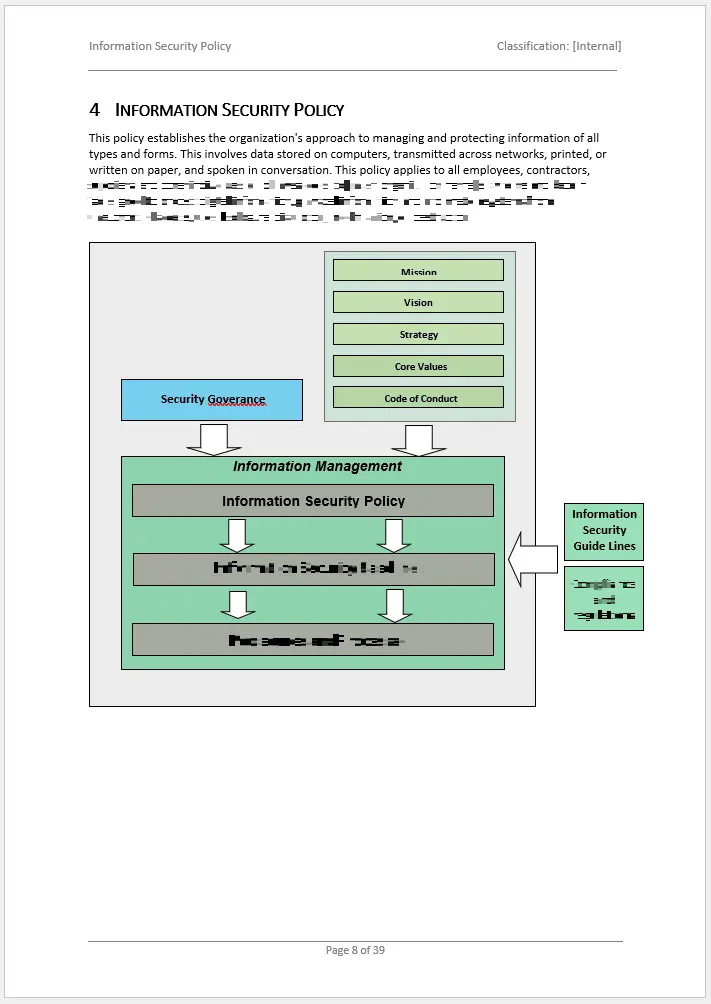
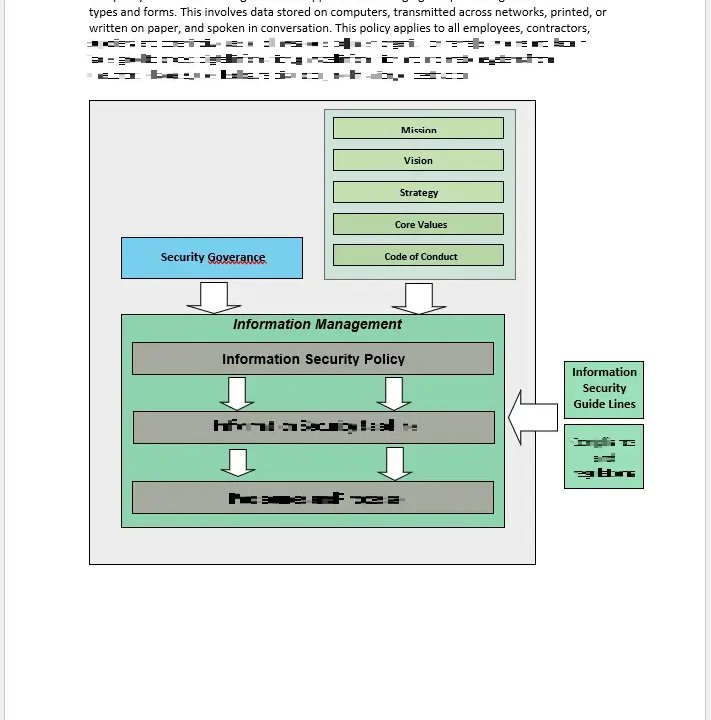
This Information Security Policy Template walks you through establishing a baseline for confidentiality, integrity, and availability—core principles at the heart of ISO 27001.
With guidance on Clause 5.2 (Information Security Policy) and Clause 6.2 (Information Security Objectives), you’ll gain a clear roadmap for meeting compliance requirements.
Available as a Word template, easy to adjust policy statements, responsibilities and review schedules to fit your organization’s context.
Download this Information Security Policy Template and you equip your organization with a solid reference point for identifying and addressing potential security gaps.
It helps you focus on what matters: defining actionable objectives, aligning with regulatory demands, and staying ahead of emerging risks.
This template is a straightforward way to get started on ISO 27001 towards a secure ISMS.
Building a Strong Information Security Policy
Developing an effective information security policy can be challenging, but the right framework can make all the difference.
Our Information Security Policy Template ISO 27001 comes equipped with a set of key features that simplify policy creation, streamline compliance efforts, and help your organization prioritize security at every level.
Alignment with ISO 27001
This template is specifically developed to meet the requirements of ISO 27001 Clause 5.2, ensuring your policy:
- Reflects the purpose and objectives of your organization.
- Includes a framework for setting measurable security objectives, aligned with Clause 6.2.
- Demonstrates a commitment to satisfying legal, regulatory, and contractual requirements.
- Incorporates a continual improvement process for your ISMS.
Customization
Delivered as a Word file, this Information Security Policy Template Word document is fully customizable, allowing you to customize its contents to fit your organization’s specific needs.
You can modify sections, add unique organizational details, and integrate additional requirements based on your industry or regulatory landscape.
Comprehensive high-level Policy Coverage
The template provides a high-level policy framework supported by detailed guidance for creating and managing topic-specific policies. Key areas covered include:
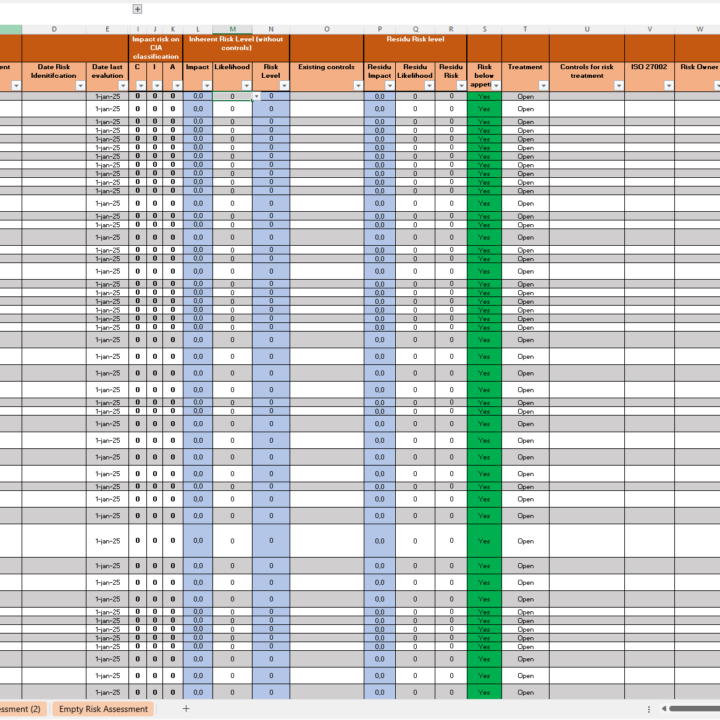
- Access Control: Defining roles, permissions, and procedures to secure sensitive information.
- Incident Management: Establishing protocols for identifying, responding to, and recovering from security incidents.
- Cryptography and Key Management: Setting standards for the secure use and management of encryption technologies.
- Secure Development: Outlining requirements for developing and maintaining secure systems and applications.
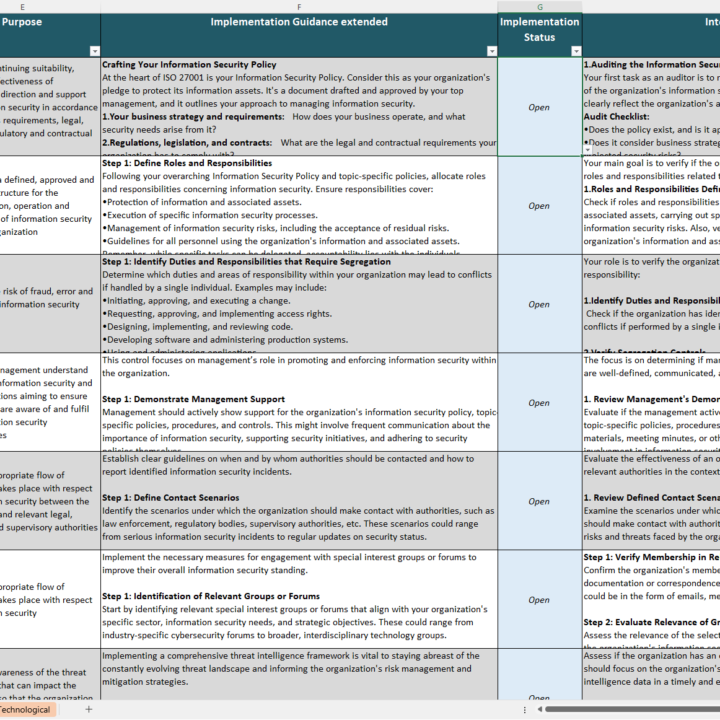
Guidance for Policy Review and Updates
The template includes guidance for periodic review and updates, a critical aspect emphasized in ISO 27001 Control 5.1. Your organization can establish processes to:
- Regularly assess the policy’s effectiveness in light of evolving business strategies, threats, and regulatory changes.
- Ensure alignment between high-level policies and specific operational requirements.
- Communicate updates to relevant personnel and external stakeholders effectively.
Support for Documentation and Communication
To comply with ISO 27001 requirements, your information security policy must be documented, communicated within the organization, and made available to relevant interested parties.
This template provides pre-written sections that make it easy to:
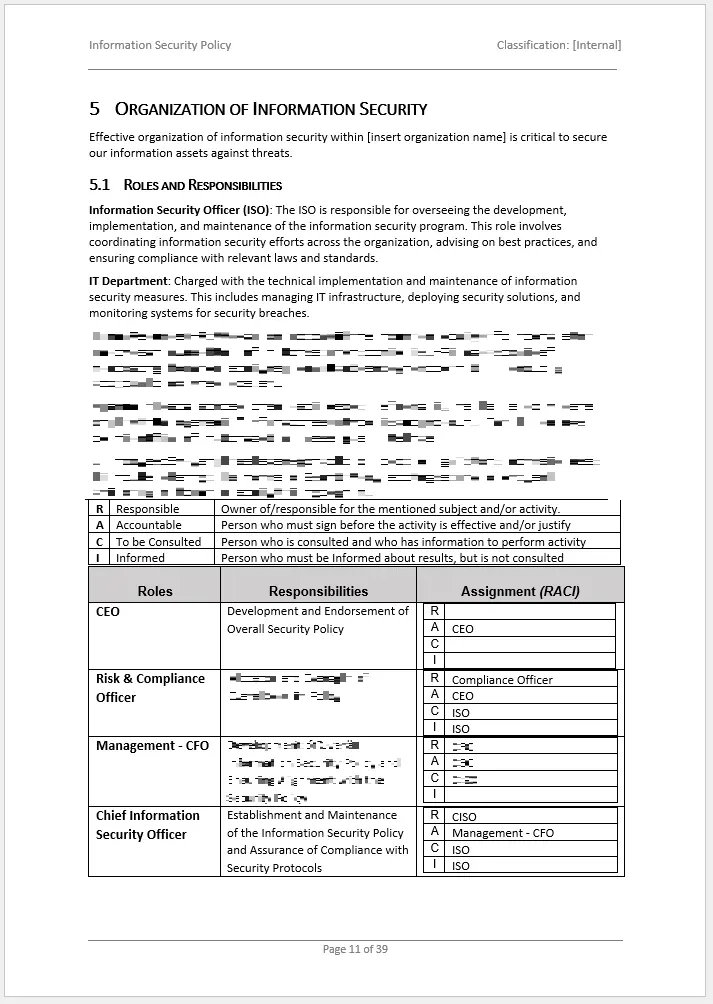
- Define roles and responsibilities for managing information security.
- Communicate the policy to employees and third parties in a clear and understandable manner.
- Document acknowledgments to ensure recipients understand and comply with the policy.
ISO 27001 Clauses and Controls
Building a dependable information security policy requires a clear understanding of ISO 27001’s core principles.
This Information Security Policy Template is structured to help your organization address key clauses and controls with minimal complexity, ensuring that your security measures remain both comprehensive and effective.
Clause 5.2: Clear Policy Objectives
ISO 27001 emphasizes the importance of defining a policy that aligns with your organization’s overall objectives. By using this template, you can:
- Ensure the policy reflects your mission, business goals, and regulatory commitments.
- Include clear statements on confidentiality, integrity, and availability.
- Document how these objectives are communicated, monitored, and reviewed across all operational levels.
Clause 6.2: Measurable Security Objectives
Establishing specific, actionable objectives is one of the main ISO 27001’s requirements. This template guides you through:
- Setting measurable goals tied directly to risk assessments and organizational priorities.
- Outlining responsibilities for tracking progress and adjusting objectives as needed.
- Demonstrating continual improvement by regularly reviewing performance against set targets.
Control 5.1: Formalizing Policies for Information Security
Control 5.1 focuses on formalizing your organization’s commitment to safeguarding information. Within this template, you’ll find:
- Structured guidelines for defining high-level information security policies.
- Clear processes for obtaining management approval and distributing the policy.
- Instructions for periodic reviews, ensuring the policy remains relevant in light of evolving threats or regulatory changes.
Benefits of Using This ISO 27001 Information Security Policy Template
Developing a comprehensive information security policy can seem daunting, but having a structured, ISO 27001-aligned template simplifies the process.
How this Information Security Policy Template can benefit you.
- Streamlined Compliance Efforts
Meeting ISO 27001 requirements often involves multiple steps, from defining objectives to conducting risk assessments.
This template helps you map those tasks into a single, cohesive policy framework, reducing confusion and duplication of effort. - Improved Clarity and Consistency
Using this template, you can maintain consistent language, roles, and responsibilities across various departments.
This unified approach makes it easier for teams to understand their obligations and for leadership to monitor compliance. - Enhanced Risk Management
This template integrates naturally with risk assessments, helping your organization prioritize vulnerabilities and plan remediation. - Reduced Administrative Overhead
Having a pre-structured policy document saves you from reinventing the wheel.
You can allocate resources to more pressing tasks—like refining your incident response strategies or enhancing employee training—rather than drafting basic policy sections. - Ongoing Adaptability
This template’s layout includes prompts for regular reviews and updates.
What’s Included
When you use this ISO 27001 Information Security Policy Template, you get a structured, easy-to-follow set of resources designed to guide your organization toward a fully compliant and actionable policy.
- High-Level Policy Framework
A ready-made format for defining your organization’s stance on confidentiality, integrity, and availability.
This section lays out the fundamentals of an effective information security policy, aligning closely with ISO 27001 Clause 5.2. - Measurable Objectives Section
Document your security goals in line with Clause 6.2, ensuring each objective is clearly stated, monitored, and updated as risks and business needs change. - Security Domains
Covering topics like access control, incident management, and cryptography.
These sections help you shape topic-specific policies that align with Control 5.1 and standard best practices. - Periodic Review and Update Framework
Clear instructions for reviewing and revising the policy at set intervals or when major changes occur.
This ensures your organization maintains compliance with ISO 27001 requirements. - Editable Word Format
Delivered as an information security policy template Word file, you can adjust text, headings, and structure to match your organization’s unique context.
This flexibility saves time and allows for easy incorporation of additional requirements.
Who Should Use This Template?
The Information Security Policy Template is made to help a professionals and organizations looking to strengthen their security posture and align with ISO 27001 standard.
Whether you’re building a new security framework from scratch or refining existing policies, this template can streamline your efforts.
Particularly useful for:
- Small to Mid-Sized Businesses
If you’re operating with limited resources but still need to protect sensitive data, this template provides a clear approach that helps you establish a solid baseline. - Growing Enterprises
As your organization expands, the need for consistent and well-documented security measures becomes more pressing. - Compliance Officers and Risk Managers
Achieving and maintaining compliance with ISO 27001 often falls under the remit of these roles.
The template offers a straightforward way to document policies, track compliance requirements, and prepare for audits more efficiently. - IT Managers and Security Teams
Technical staff benefit from a clear policy framework that outlines responsibilities, communication channels, and escalation procedures. - Organizations Pursuing ISO 27001 Certification
For those aiming to become ISO 27001 certified, this ISO 27001 information security policy template acts as a foundational document.
How to Access and Use
Implementing a new information security policy doesn’t have to be complicated.
This Information Security Policy Template is designed to streamline the process, giving you a straightforward roadmap for integrating its contents into your organization’s operations.
- Download the Template
Access the Information Security Policy Template download and open it in Word or another compatible word processor. - Review and Customize
Start by reading through each section, focusing on how the pre-written content aligns with your organization’s goals.
Update any sections that need refining, add details relevant to your industry, and remove any elements that don’t apply to your operational context. - Define Roles and Responsibilities
Assign clear tasks and accountabilities for key security functions.
This involves stating who oversees policy governance, manages risk assessments, and coordinates incident response.
Clarity in this step ensures efficient communication and faster decision-making. - Obtain Management Approval
Present the finalized policy to top management for review and endorsement.
ISO 27001 emphasizes the importance of leadership buy-in, so ensure decision-makers understand how the policy aligns with business objectives and regulatory obligations. - Communicate Organization-Wide
Distribute the policy to all relevant personnel in a format that’s accessible and easily understood.
Offer brief training sessions or internal FAQs if needed, so everyone knows their responsibilities and how to comply with the new guidelines. - Implement and Monitor
Put the policy into action by integrating it with existing processes, such as onboarding procedures, vendor management, or IT administration tasks.
Continually monitor adherence, gather feedback, and address any issues that arise during day-to-day operations. - Schedule Regular Reviews
Set up a review timeline to ensure your policy remains up-to-date.
ISO 27001 recommends reviewing policies when business objectives shift, new regulations emerge, or your risk landscape evolves.
Regular updates help maintain effectiveness and relevance.
Improve Your Security Posture
Download the template to provide your organization with straightforward guidelines, objectives, and a consistent policy structure that aligns with ISO 27001 requirements.
Reduce the risk of data breaches, integrate compliance efforts, and establish ongoing security improvements.
Use the Information Security Policy Template download to drive change in how your organization approaches confidentiality, integrity, and availability.