Breaking down ISO 27001:2022 Clause 10.2 Nonconformity and Corrective Action
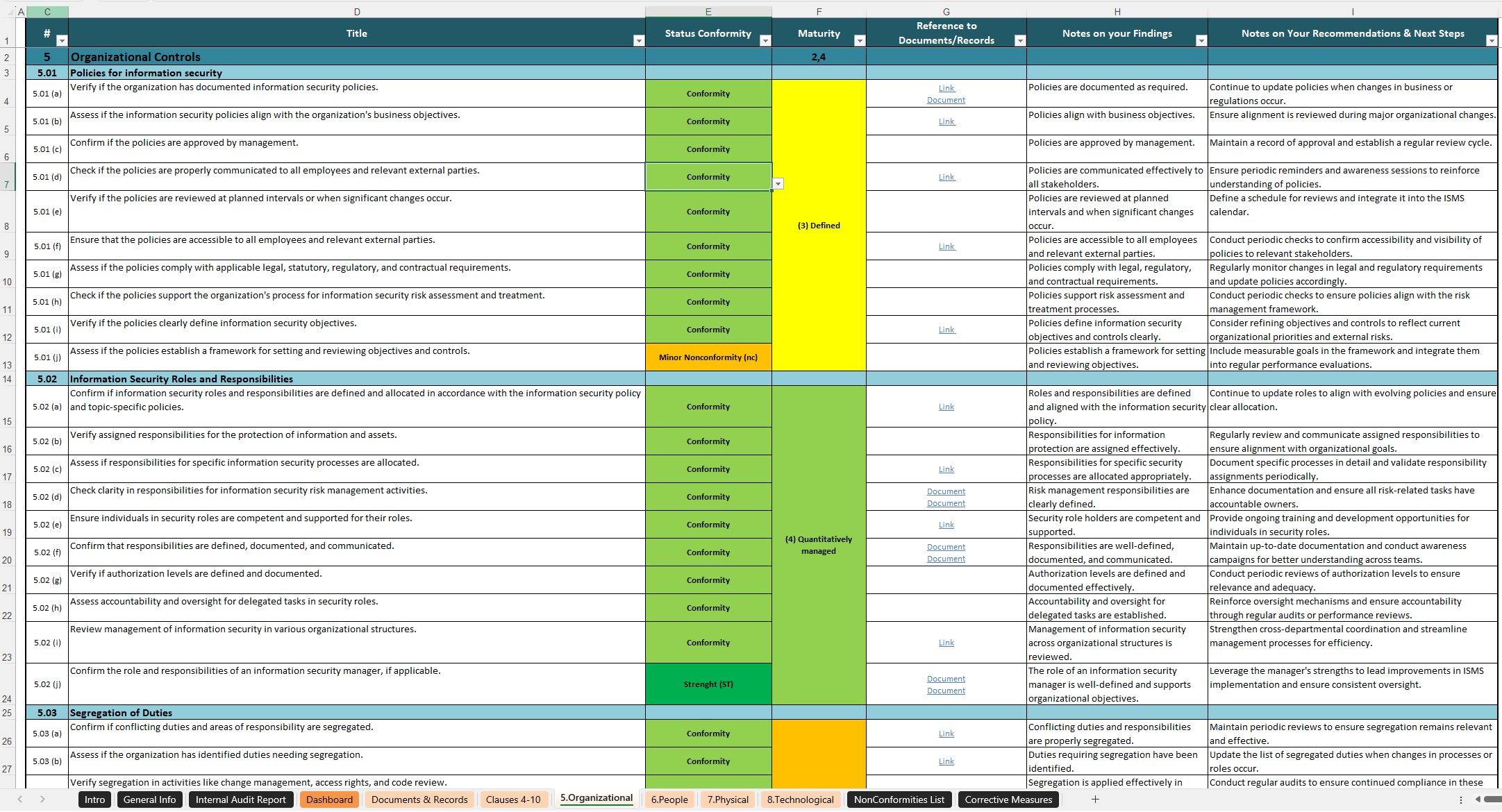
Clause 10.2 focuses on addressing nonconformities within your organization’s ISMS. It provides a systematic approach to identify, evaluate, and resolve issues to prevent their recurrence. Critical for maintaining compliance and continual improvement in information security practices.
Objective of Clause 10.2
Imagine you’re steering a ship through stormy seas. Nonconformities—those unexpected deviations from the plan—are like hidden icebergs. Clause 10.2 of ISO 27001 acts as your navigational guide, ensuring you identify and address these hazards before they cause irreversible damage. This clause emphasizes how organizations should react, evaluate, and learn from nonconformities to improve their Information Security Management System (ISMS). Let’s dive into what makes this clause so vital.
What Is a Nonconformity?
A nonconformity occurs when something doesn’t align with the standards, policies, or procedures outlined in your ISMS. It could be as simple as a missed log entry or as severe as a data breach caused by improper access controls.
Examples of Nonconformities
- Failure to conduct regular security audits.
- Improper handling of sensitive information.
- Ineffective password management policies.
Requirements of Clause 10.2
Clause 10.2 outlines a structured approach for managing nonconformities and implementing corrective actions. Here’s what’s required:
- Reacting to Nonconformities: Address the issue promptly to control and correct it. This might involve isolating affected systems or communicating with stakeholders.
- Evaluating the Need for Action: Dig deep to identify root causes and assess if similar issues exist elsewhere.
- Implementing Corrective Actions: Take decisive steps to eliminate root causes and prevent recurrence.
- Reviewing Effectiveness: Test and validate the success of your corrective measures.
- Making Necessary Changes to ISMS: Update your processes or policies to reflect lessons learned.
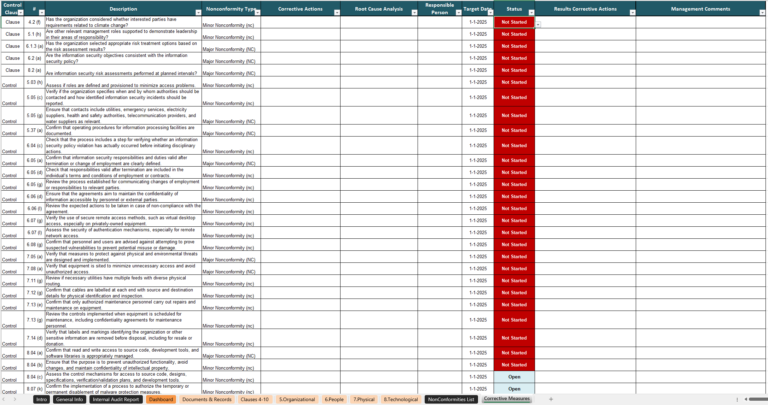
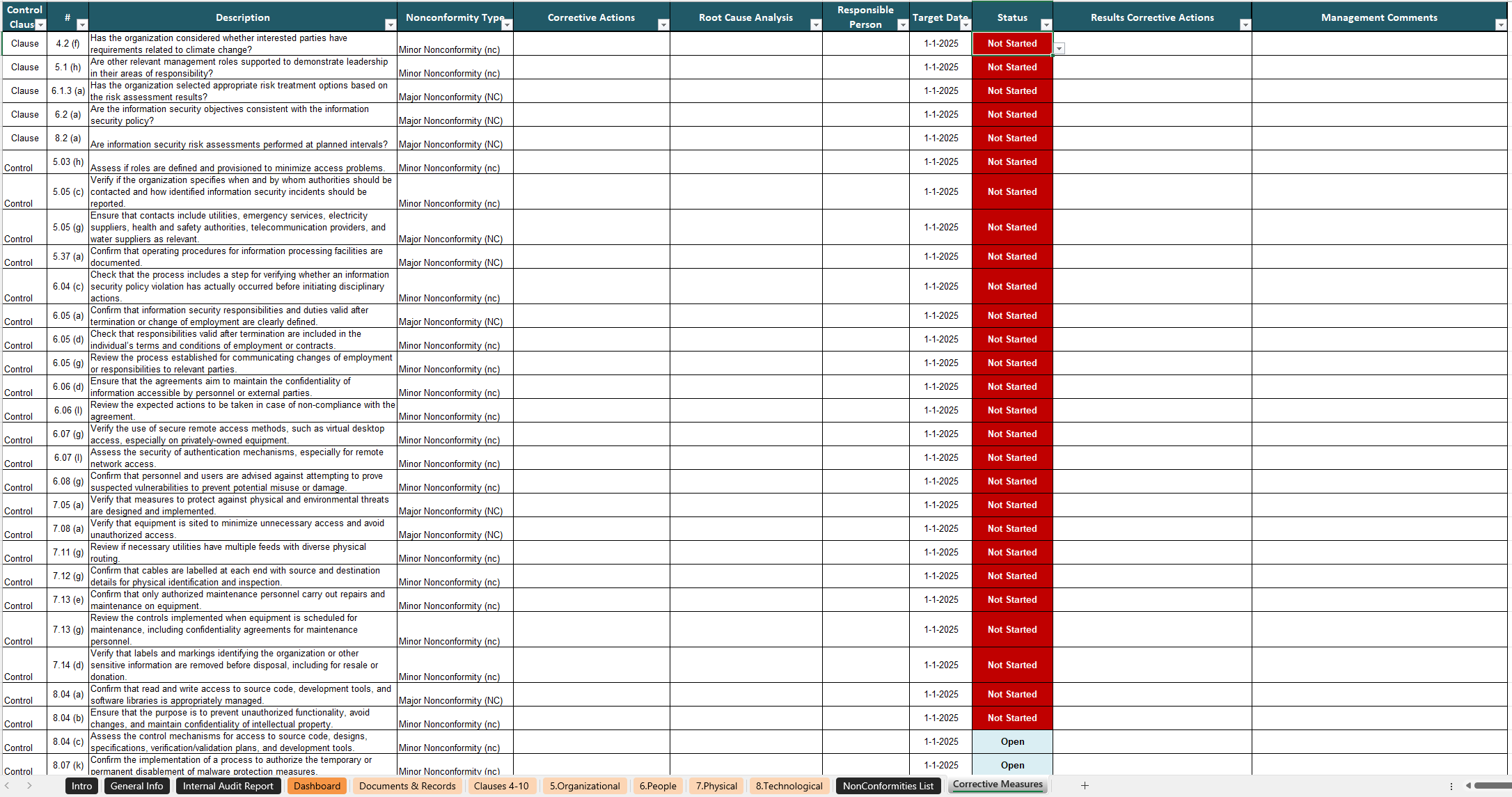
- Documenting Everything: Keep detailed records of nonconformities, actions taken, and results achieved.
The ISO 27001 Corrective Action Process
- Step 1: Identify and Document Nonconformities
Spotting a nonconformity is half the battle. Use tools like incident management systems to capture details, including:- Description of the issue.
- Time and location of occurrence.
- Potential impact.
Need a structured approach to documenting nonconformities? Check out our ISO 27001 Internal Audit Template
- Step 2: React Quickly
Control the situation immediately to minimize harm. For instance, if sensitive data is exposed, restrict access and notify relevant authorities. - Step 3: Analyze the Root Cause
Dive beneath the surface using techniques like the 5 Whys or Fishbone Diagrams. For example:- Why did the firewall fail? It wasn’t configured correctly.
- Why wasn’t it configured correctly? There was no updated policy.
- Step 4: Plan Corrective Actions
Develop a clear roadmap to eliminate root causes. Include specific tasks, deadlines, and accountability. - Step 5: Implement and Monitor
Put your plan into action. Monitor progress and adjust if needed. - Step 6: Review and Verify
Assess whether the corrective actions resolved the issue effectively. Conduct follow-up audits to ensure compliance. - Step 7: Update ISMS Policies
Incorporate findings into your ISMS to prevent similar nonconformities in the future.
Tools for Managing Nonconformities
Root Cause Analysis Tools
- The 5 Whys: Simple and effective for uncovering the root cause.
- Fishbone Diagram: Visualizes relationships between causes and effects.
- Failure Mode and Effects Analysis (FMEA): Identifies potential failure points.
Document Management Systems
These tools help maintain records of nonconformities and corrective actions, ensuring traceability and compliance.
Documentation Best Practices
Ensure your records include:
- Detailed descriptions of nonconformities.
- Steps taken to address them.
- Outcomes and lessons learned.
Common Implementation Challenges
Lack of Awareness
Many organizations struggle to identify nonconformities because employees are unaware of ISO 27001 requirements.
Tip: Provide regular training on nonconformity identification and reporting.
Inadequate Root Cause Analysis
Jumping to conclusions without thorough analysis leads to ineffective corrective actions.
Tip: Use structured methodologies like the 5 Whys or Fishbone Diagram.
Poor Documentation
Failing to document actions makes it difficult to demonstrate compliance during audits.
Tip: Implement a centralized documentation system.